In recent lawsuits, you can see how illegal, and awful, the government can be to you if you compete with the stock ownerships of certain U.S. Senators or report their corruption crimes. Here are some of the revealing text sections from those legal filings:
“…The charges are filed against Defendant, THE UNITED STATES OF AMERICA, a representative entity which has a 1.) command-and-control, 2.) financing, 3.) legal authority and 4.) management influence over the actions and claims of harm described herein and has been proven, in thousands of past court cases, to use reprisal attacks against A.) whistle-blowers and B.) the competitors to political campaign financiers of high-level government officials.
SILICON VALLEY STOCK CRASH
On May 5, 2022 all of the stock values of all of the Big Tech companies that had assisted the corrupt United States Officials in stealing Victims’s intellectual property and attacking Victims, ironically, crashed into the ultimate stock market valuation pit from hell. It was probably just ultimate KARMA for a bunch of sinister corporations that Government politicians protect in Silicon Valley and allow them to keep producing child suicides, racism, misogyny, child mental health threats, domestic spying, data harvesting, sex trafficking, election manipulation, tax evasion, Fusion GPS/Media Matters/ Black Cube hit jobs on competitors, censorship, contrived market monopolization, intellectual property theft, political bribery and many other crimes! Why? Because crime pays…for corrupt U.S. Senators!
This is a case regarding the harms to the Victims by organized criminal activity that has been masquerading under corrupt governmental officials. Victims have been attacked with defamatory actions and attacks by governmental officials and they been seriously harmed. Victims has used due diligence to report criminal activity to law enforcement. However, Victims’s actions have been totally disregarded. Victims has been grievously harmed and seeks to recover the damages that have been incurred.
-
This complaint covers issues which the Court has the power to decide, such as RICO, Anti-trust monopoly violations, 28 U.S.C. &1331; 18 U.S.C. §§ 1961(5), 1962(c), 18 U.S.C. §§ 1961(5), 1962(d) 773. ; and many other matters which attorney-less, pro-se, low-income, senior, disabled Victims is not skilled enough to properly cite, at this time, but could cite, with perfection, with a great court-appointed lawyer. Court has subject matter jurisdiction over this action pursuant to 28 U.S.C. § 1331, as Victims’s claims arise under the Constitution and laws of the United States. This Court has jurisdiction to grant relief in this action pursuant to 28 U.S.C. § 1346(b), as Victims brings claims under the Federal Tort Claims Act. This case also presents a federal matter within this Court’s jurisdiction under Article III of the United States Constitution, 28 U.S.C. § 1331, and the Administrative Procedure Act, 5 U.S.C. § 702, and under other related law acts and precedents.
This Court has authority to grant declaratory relief under the Declaratory Judgment Act, 28 U.S.C. § 2201 et seq., and to award damages, costs, and attorneys’ fees under 28 U.S.C. § 2412, and under other related acts and precedents. Venue is proper in this district under 28 U.S.C. § 1391(e), and under other related acts and precedents. The venue is proper in this district pursuant to 28 U.S.C. § 1391(b), because a substantial part of the acts or omissions that give rise to the Victims’ claim occurred or will occur in the area. RICO charges by Victims, against Defendant are verified as valid by Victims and by reviewing third parties. Victims is also requesting relief under the United States Constitution, the Federal Tort Claims Act (“FTCA”), 28 U.S.C. §§ 1346(b), 2672 and related jurisdictions and applicable rights.
- On information and belief, always relevant herein, the UNITED STATES OF AMERICA (which includes those entities that are financier/beneficiary oligarchs that have been illicitly incorporated into the government as “White House Advisors” and “Special Staff”).
“… This case is about hit-jobs and attacks on Victims via the operators of a profiteering organized crime activity in government offices. Racketeering-motivated political ‘mobsters’, in Government offices, attacked and harmed Victims, using taxpayer-paid resources because they did not cooperate with their crimes, which were based out of government offices, and because Victims reported those crimes to law enforcement when Victims witnessed those crimes.
Victims’s income, housing, brand and businesses were attacked and cut-off in reprisal for his aid to the government in criminal ‘stimulus’ scam investigations involving profiteering with foreign rare earth mining schemes, the energy and internet industries and the stock market. Defendants spent over $60+ million dollars (proven by their own banking records, comps from Presidential campaigns, and opposition research group’s past billings as shown in provided EXHIBITS) using spy agency-type dirty tricks contracted from such attack services as Cardinal & Pine; Pacronym, Acronym; The Americano; Investing in US; Shadow Inc; Courier Newsroom; IN-Q-Tel; Gawker Media; Jalopnik; Gizmodo Media; K2 Intelligence; WikiStrat; Podesta Group; Fusion GPS; Clearview AI Face Tracking, Google; YouTube; Alphabet; Facebook; Twitter; Think Progress; Media Matters); Black Cube; Correct The Record; Orbis Business Intelligence, Undercover Global Ltd; Stratfor; Jigsaw; ShareBlue/Acronym; Versa LLC; American Ledger; Supermajority News; New Venture Fund; Sixteen Thirty Fund; Cambridge Analytica; Sid Blumenthal; States Newsroom; Hopewell Fund; Open Society.; Palantir, Kroll, David Brock; AmpliFire News; American Bridge; Plouffe Consulting; Pantsuit Nation; MotiveAI; American Bridge 21st Century Foundation; Priorities USA; PR Firm Sunshine Sachs; The American Independent Foundation; Covington and Burling; Buzzfeed; The American Independent; Perkins Coie; Secondary Infektion; Wilson Sonsini and thousands more are hired to scan EVERY database, every hour to run hit-jobs, character assassinations, dirty tricks and economic reprisal attacks on Victims, and any targets who reported the crimes. Defendants used former intelligence agency (ie: See Ronan Farrow’s Book: CATCH AND KILL) personnel to harm Victims as revenge/vendetta/reprisal because Victims was a whistle-blower, a direct competitor and the inventor of technologies that Defendants financiers had not, themselves, invented….”
“These public official racketeer ‘mobsters’ run part of the United States Government and used government resources, that Victims tax dollars paid for, to operate their crimes and to attack Victims for whistle-blowing. These racketeering officials rely on schemes they operate with Elon Musk, Jeff Bezos, Bill Gates, Lauren Powell Jobs, Tim Draper, Steve Jurvetson, Larry Page, Eric Schmidt, The Zuckerbergs and other windfall profiteers, coordinated by private banks such as Goldman Sachs, corrupt CPA firms like Mossack and dirty law firms like Perkins Coie as consigliere-type coordinators of the schemes.
Some of the most famous politicians in the world covertly joined together to engage in a profiteering and racketeering ‘enterprise’ (not unlike the ‘Mafia’) in order to optimize bribes based around stock market manipulation of securities assets owned by politicians and their family members. The many thousands of news articles about the reasons for the STOCK ACT, in Congress, detail the harms of this via massive public documentation. White House and Congressional staff (ie: Plouffe, Axelrod, Mcdonough, Carney, Spinner, Emanual, Rattner, Schmidt, Westly, et al) advised them on how to set-up and prosper in these illegal machinations in exchange for political campaign financing and percentages of said financing.
“…The Patent Office has awarded Victims dozens of issued federal patents as first-to-invent the core products that run Silicon Valley. Victims, and his partners, spent decades of their lives and millions of dollars creating those inventions. A patent is a fight with the U.S. Government over who invented a thing. You file a paper saying: “I invented this thing” and the Government generally sends you a letter saying: “We aren’t sure you were the first: PROVE IT!” You go back and forth with the Patent Office in a federal investigation that can last years, and spend vast amounts of money on lawyers, until you have absolutely proven to the Patent Office that you were the first to invent something. Then the Patent Office awards you the patent. In Victims case, the patent office said that they invented the things that Google, YouTube, Netflix, Tesla and Facebook – Meta are based on. The Patent Office, Victims emails, contracts, NDA’s and other evidence; including leaks and whistle-blowers from Silicon Valley, proves that Victims invented those things, and launched the companies offering those products and services, years before those competing companies even existed.
At the same time, federal and news media investigators discovered that Google, YouTube, Netflix, Tesla and Facebook – Meta.et al, are the LARGEST PROVIDERS OF BRIBES TO U.S. SENATORS AND WHITE HOUSE STAFF. It is impossible for the Court or the Victims to argue otherwise because the public documentation confirming this fact is so vast.
Victims discovered, later, that those competitors hired moles to spy on their companies and their technologies and engage in RICO-violating anti-competitive attacks. Even worse: Victims found out that later after a number of broadcast 60 Minutes CBS News reports and Congressional tips from U.S. Senators family members, that their government officials covertly owned those companies!!! Yes, the victims elected officials turned out to be either financed by, friends, with, sleeping with, dating the staff of, holding stock market assets in, promised a revolving door job or government service contracts from, partying with, personal friends with, photographed at private events with, exchanging emails with, business associates of or directed by; our business adversaries, or the Senators and politicians that those business adversaries pay campaign finances to, or supply political digital search manipulation services to. Criminal U.S. Senators and White House staff coordinated and profited in these schemes.
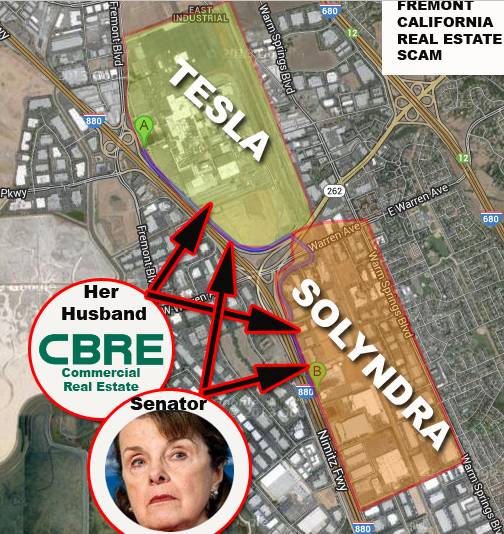
For example; One California Senator’s family (Feinstein) owned and controlled A.) Government trained attack ‘spies’ formerly with the CIA, NSA, etc., B.) The leasing contracts for Tesla and Solyndra, C.) Their office staff that threatened Victims in writing and in-person to Victims’s Washington DC staff, D.) the financing for Tesla and Solyndra, E.) The construction services for Tesla and Solyndra, F.) The staffing company for Tesla and Solyndra, G.) The adjacent railroad services for Tesla and Solyndra, H.) Key suppliers for Tesla and Solyndra, I.) Goldman Sachs cooperative relationships for Tesla and Solyndra, J.) Transitions from their own Senate Office staff to revolving door jobs at Tesla and Solyndra, K.) Government decisions for Tesla and Solyndra, L.) The relationship incentives between Google, Tesla and Solyndra and that Senator’s campaign financing to that Senator; and other illicit conflicts of interest. Victims owned the competing electric car company and technology that would have obsoleted Tesla, Google and Solyndra and was the first to begin negotiations with the factory that Tesla later took over at the insistence of that Senator, even though Elon Musk appears in news reports, previously stating that they saw no use for the building for Tesla.
Silicon Valley Big Tech has had the largest number of Congressional hearings against it for abuse of the public, BUT the least number of regulations imposed on it. Why? You can look no further than the covert ownership of Silicon Valley by elected officials. Our politicians get paid bribes, by Silicon Valley, to keep the political corruption alive and well while they operate, with impunity, as the biggest threats to society ever manifested.
Government politicians protect Silicon Valley and allow it to keep producing child suicides, racism, misogyny, child mental health threats, domestic spying, data harvesting, sex trafficking, election manipulation, tax evasion, censorship, intellectual property theft, political bribery and many other crimes! Why? Because crime pays…for U.S. Government officials!
Certain Government officials, listed by name in the evidence documents, have knowingly formed a RICO-law violating ‘criminal enterprise’ in order to operate monopolies against the public, including Victims and his companies, that place criminal greed over ethical governance. The highest levels of DOJ, FEC, OSC, and other enforcement agencies have been proven, BY CONGRESS, to have been blockaded by cronyism and corruption in their required duties to arrest these officials.
Victims’s letter to Senator Bingham and the Energy and Commerce Committee began the Solyndra and Cleantech Crash investigations as shown on the referenced CBS NEWS 60 MINUTES segments (Victims worked with Bob Simon at 60 Minutes) and other documents in the attached and linked EXHIBITS, and created the ‘The Stop Trading on Congressional Knowledge (STOCK) Act’ which Senator Bingham and Victims both aggressively pushed to create.
There are 8 billion people in the world and over 5 million companies in the world. Why are the same 20 people; from the same 6 companies; that are all within 10 blocks of each other; that all went to the same frat houses; that all go to each other’s parties; that control the same crooked ‘Panama Papers’-type CPA’s, Law Firms, Media Attackers and Lobbyists; that operate all this felonious larceny connected in this way unless it is a “criminal enterprise” in violation of RICO laws?
-
-
-
-
-
-
On top of that, Defendants confided to Victims (Later proven in their leaked emails) that “they are the new Mafia” and produced Mafia documents and Mafia photo tributes to themselves (attached herein). They said that they “…sought to control The White House and Sacramento Government offices so they could steer all the taxpayers public funds and power to their personal pockets…” , an act they fully accomplished! A deep state is a type of governance made up of potentially secret and unauthorized networks of power operating independently of a state‘s political leadership in pursuit of their own agenda and goals. In popular usage, the term carries overwhelmingly negative connotations.[2] The range of possible uses of the term is similar to that for shadow government. The expression state within a state is an older and similar concept. Historically, it designated a well-defined organization which seeks to function independently,[3] whereas the deep state refers more to a hidden organization seeking to manipulate the public state. Congressional and other government officials have confirmed that a portion of the UNITED STATES OF AMERICA is operated by and organized as this Deep State operation including the administrators of this section of the government, listed by name, in the related EXHIBITS.
-
-
-
-
-
The United States Patent Office (https://uspto.gov) has awarded Victims dozens of seminal issued patents as first-to-invent the core technologies, of modern Silicon Valley, years before Defendants sinister company partners even existed. Billions of people use Victims’s technologies worldwide.
Who has hasn’t dreamed of an electric car that can solve all of America’s energy problems, gets all of it’s fuel from clean sources INSIDE of America, is the safest car ever made, is affordable to the average person and relies on no foreign sourcing? The United States Patent Office and public records say one of Victims’s company’s did it first! …AND, on top of that, Victims was awarded nearly a billion dollars of issued patents in commendation by the government. …AND on top of that, Congress awarded Victims a Congressional award for it in The Iraq War Bill …AND The United States Government contracted Victims to build it….. BUT then the U.S. Government sabotaged the whole thing, including all the patents and the rest of Victims’s funding because it was about to obsolete their insider’s car: The deadly, stock market pump-and-dumped and contrived “Tesla”. Law enforcement and news investigators then informed Victims they had been defrauded by a government scam and insider crony slush-fund.
There are a vast volume of other similar examples of “Firsts” created and placed on the market by Victims and then spied-on, stolen and copied By Defendants who then launched harms against because Victims refused to participate in their protection rackets.
Defendants broke RICO and Antitrust laws by, in part, attacking and destroying Victims’s companies because they did not participate in Defendants protection rackets and because his products and technologies obsoleted theirs.
Defendants spied on Victims companies (with honey-traps, listening devices that were found, hacked servers, Microsoft Outlook email re-directs, moles who actually worked for the Defendants and other tricks), copied the patents, technologies and trade secrets and made hundreds of billions of dollars from them.
Defendants blockaded Victims from getting a law firm, as detailed in the attached and hot-linked EXHIBITS and blockade his litigation attempts to get to Jury Trial against him. There is even a New York Times expose’ article about how Google boss: Larry Page (‘boyfriend’ of Elon Musk – They share an apartment, lobbyists and own the same Senators), skulks around at tech events stealing ideas for Google/Alphabet. Page stole many of Google’s technologies from Victims. It is difficult for Victims to watch Defendants buy mutiple homes, race cars, private islands, private jets, celebrity parties, exotic resort vacations and other fine things, based on profits from Victims’s inventions, while Victims is allowed to have none of these things, and is blockaded from even getting a single home, because Defendants Cartel ‘Enterprise’ won’t allow him to. In full compliance with RICO requirements, Defendants attacked Victims A.) Record-breaking Global Televsion Network, B.) Energy Processing Company, C.) Electric Vehicle Manufacturing Company, D.) Social Media company and harrassed, black-listed, and put them out of business because they had products that Defendants copied and Victims had them years Before Defendants efforts even existed.
In the CASE X matter, the United States agencies, university and news reports have stated that the United States and it’s taxpayers lost tens of billions of dollars.
THE UNITED STATES OF AMERICA OWES PLAINTIFF MONEY FOR SAVING THE UNITED STATES OF AMERICA MONEY – If not for the actions of Victims, taxpayers would have lost tens of billions of dollars more. Victims are OWED some consideration for serving their nation, overtly and covertly, and getting attcked and harmed for it by reprisal-oriented corrupt government officials who got caught! Verifications and proofs of all assertions are provided in the attached EXHIBITS.
Victims, and their co-investors, previously sued the U.S. for political reprisal and won their (massivly media covered) case under (Supreme Court nominee) Judge Ketanji Brown Jackson, wherein Victims and his peers proved that political reprisal hit-jobs had been ordered against Victims by Executives in The White House, The Department of Energy and via West Coast U.S. Senators, all of whom had hundreds of millions of dollars of ‘unjust gains’ expected from their illicit participations in CASE X and the stock market gains they sought therefrom. The Secretary of Energy, Mutiple Attorney General’s and the Director of the FBI were fired for corruption during the CASE X timeframe and according to law-firm Covington And Burling, who claims (in emails to Victims) to have placed those appointees in office, they were all connected to CASE X ill-gotten gains. Victims’s exposure of the crimes, notifications to the perpetrators that they had been caught, lock-down of the loop-holes used to engage in the crimes, creation of massive press coverage of the corruptions, creation of legal precedents, mass posting of the evidence to citizens world-wide, and other efforts, is said to have saved the United States Of America over $200 Billion dollars in losses from future and ongoing versions of these crimes.
Victims alleges reprisal, vendetta, and revenge by government officials as retribution for reporting violations of RICO laws, Anti-Trust Laws and other crimes, in a criminal program involving U.S. public officials. Victims also alleges RICO-organized business harms to his companies and issued patents.
Victims’s losses from said state-sponsored vendetta reprisal attacks operated The White House, government agencies and Congress wherein those bodies were infected by corruption as reported by the FBI, DOJ, SEC, OSC, FEC, FINCEN, INTERPOL, ICIJ, WIKILEAKS, CBS NEWS, CONGRESSIONAL ETHICS COMMITTEES AND hundreds of other government bodies. Victims in no way aserts that the U.S. government is “bad”. Victims simply asserts that there are some bad people, with criminal intentions, working in the government.
Victims asks the Court to re-consider Victims’s request for protection via the more detailed threat explanations, below, which proves that Victims have threats of death, were attacked, have extreme vulnerability to retaliation, have already had their lives destroyed by Defendants attacks and that it is in the public’s interest for Victims to stay alive and unharmed so that they can continue to protect taxpayers from corruption. Plaintffs attacks are now detailed in the body of the complaint as well as the attached EXHIBITS which are part and parcel of this filing.
Actual evidence of harassemet, shadow-bans and cyberstalking are provided. Victims has over 3 million pages of evidence and many hours of video evidence posted online. Any appearance of Victims’s name on any server, dating site, government site or other electronic location damages Victims because these hired attack companies use computerized cyber-assassin software: Cardinal & Pine; Pacronym, Acronym; The Americano; Investing in US; Shadow Inc; Courier Newsroom; IN-Q-Tel; Gawker Media; Jalopnik; Gizmodo Media; K2 Intelligence; WikiStrat; Podesta Group; Fusion GPS; Clearview AI Face Tracking, Google; YouTube; Alphabet; Facebook; Twitter; Think Progress; Media Matters); Black Cube; Correct The Record; Orbis Business Intelligence, Undercover Global Ltd; Stratfor; Jigsaw; ShareBlue/Acronym; Versa LLC; American Ledger; Supermajority News; New Venture Fund; Sixteen Thirty Fund; Cambridge Analytica; Sid Blumenthal; States Newsroom; Hopewell Fund; Open Society.; Palantir, Kroll, David Brock; AmpliFire News; American Bridge; Plouffe Consulting; Pantsuit Nation; MotiveAI; American Bridge 21st Century Foundation; Priorities USA; PR Firm Sunshine Sachs; The American Independent Foundation; Covington and Burling; Buzzfeed; The American Independent; Perkins Coie; Secondary Infektion; Wilson Sonsini and thousands more are hired to scan EVERY database, every hour to run hit-jobs, character assassinations, dirty tricks and economic reprisal attacks on Victims, and any targets who reported the crimes. For his own security, Victims has helped to place an “insurance” policy data set on servers around the globe, on in-orbit satellites launched by others and in torrent files that look like movie files but are actually encrypted data sets, residing around the globe. Agents for Victims will release those data sets upon the untimely death, coma-state harm or severe interdiction harm to Victims.
Victims still maintain it is in the best interest of the Court and the public to appoint a qualified lawyer, equitable to the legal counsel used by Defendants, for Victims. Victims can’t understand “legalese’, can’t make a logical trial hearing sound as good as a real lawyer could, to the Jury, when the emotional stress of this case has devastated Victims and Defendant has billions of dollars at their disposal while Victims has none.
Government officials no longer have the immunity they once thought they had. Victims’s STOCK ACT in Congress proves part of that assertion as the STOCK ACT punishes most government officials for doing the crimes Victims asserts. Also, Victims created a legal Precedent by suing the Acting Secretary of Energy. Steven Chu and Lachlan Seward said they had “Qualified immunity”, yet Victims got them kicked to the curb. That’s a “win” for Victims AND the taxpayers! He and his investors sued Steven Chu, The Secretay of Energy, The U.S. and other government officials and got them fired for corruption. Other recent cases prove that dirty politicians will always, now be taken down, either in, or around the Court. To dismiss Victims case may discourage the public that nobody can get justice and may make the world say: “See, they ran another reprisal on him…it’s Seth Rich all over again”. ..”there is no justice..” “Everybody that tries to DO THE RIGHT THING gets screwed by Uncle Sam..” etc. Give the people some hope and don’t let this case get dismissed. EVERYBODY said: “You can’t sue the Secretary of Energy personally and get him kicked out” Victims did it! There are hundreds of things Victims was told were “IMPOSSIBLE..” and Victims still pulled them off. Look at Victims resume website, who else do you know that has been so productive against such impossible odds? It would be a crime to dismiss a public-interest lawsuit designed to stop corruption against the public! Victims set new legal precedents which make it easier to sue public officials and hundreds of public service groups are now doing the same thing.
Did you notice that 35+ Congressional members just decided to up and quit Congress just prior to the upcoming election? That is from these new “immunity reduction” efforts targeting crooks working in Victims’s government. Crooked officials can no longer put their dirty eggs in the “but I’m immune..” basket. Google-Alphabet-YouTube will, likely, trot out their old ploy: “…but we work for the CIA, see all these secret wire trasnfers we get from the government..and…. and, the CIA funded us.. We are IMMUNE” BS!! Micheal Painter can testify about who paid for Google Maps and the Google spy satelitte system: The American Taxpayer! Nearly 500 ex-employes are prepared to come forward and testify to what Google REALLY is. The one thing that Google, and the other co-conspirators, are NOT is immune! Eric Schmidt, Larry Page and Elon Musk, as covert operators of the deep state within the U.S., have no such immunity. The FBI AND Victims both have the evidence, training, credentialing and rapid ability to produce arrest documents for any party listed herein and those Defendant bad actors MUST be arrested and charged. Mobsters in the U.S. government engaged in RICO violations and organized crime are NOT immune from prosecution!
Related cases confirming Victims’s assertions include: Criminal Case No. 21-582 (CRC); Task Force cases known as: “Durham Investigations”; “The Solyndra Investigation”; “The Afghanistan Rare Earth Minng Corruption Investigations”;SFPD Case # 150528148 ( – Company E (Northern District) Per Officer Liu – Badge # 4742 ) is relevant. Police incident report # 25119268 is relevant. OSC Case File No. MA-19-002006 is relevant. OSC Case File DI-15-4541 is relevant. California Victim Compensation & Government Claims Board Claim # G628261 is relevant. Also relevant are: Case No. 1:20-cv-03010 ( Google monopoly and competitor attacks case); Case No. 11-CV-2509 ( https://www.cand.uscourts.gov/judges/koh-lucy-h-lhk/in-re-high-tech-employee-antitrust-litigation/ ); Task force Case No. 20-xyz2020a ( http://www.case-xyz2020a.com/ ); Case No. 20-03664 ( https://www.insurancejournal.com/app/uploads/2020/06/brown-v-google.pdf ); Case No. 1:12-CV-00774-mms and related cases. ( https://thehill.com/blogs/congress-blog/the-administration/250109-a-case-study-in-pay-to-play-cronyism. Criminal referrals against the attackers have been filed with the FBI, DOJ, SEC, FEC, FTC ); Case No. 18-cv-8865 (S.D.N.Y.)(SEC v. Elon Musk for lies and scams ); Case No. 18-cv-8947 (S.D.N.Y.)( SEC v. Tesla, Inc. for lies and scams ); Case No. 1:14-cv-270143 ( Google racketeering charges – https://artistrightswatch.com/2017/10/08/googles-racketeering-challenge/ ); Case No. 1:19-cr-00490 ( United States v. Epstein – Big tech sex cult crimes case ); Case No. 129 So.3d 1196 (Fla. 2d DCA 2014); 170 So.3d 125 (Fla. 2d DCA 2015) ( Gawker Media, LLC v. Bollea in which Gawker, Deadspin, Gizmodo, Jalopnik, Jezebel, Kotaku and Lifehacker were exposed as character assassination and money-laundering fronts working for notorious third parties); Case No. 19-cv-343672 James Martin (on behalf of ALPHABET INC) v Larry Page et al (Sex Cults In Silicon Valley ); Case No. CGC-11-508414, California Superior Court, San Francisco (Victims v Google ); Case No. 3:16-cv-03061 U.S. DISTRICT COURT, NORTHERN DISTRICT OF CALIFORNIA, San Francisco Division ( Victims V. Google/Alphabet/YouTube); Case No. 18-CIV05380 Rubin Vs. Rubin (Google sex cult and sex slave charges ); Case No. : 1:17 – cv – 06404 Vs. Rubin (Organized crime sex trafficking stock market manipulators ); Case No. D.C. No. 3:17-cv-05369 – VC (Big tech harassment of outsiders);Case No. 3:21-cv-00077 (Another of many lawsuits proving that the Silicon Valley Cartel conspires to manipulate media and markets) and the SFPD Roger Boas case records. David Drummond, Elon Musk, Larry Page, Eric Schmidt, David Rubin, and other, oligarchs advised and, lierally, ran the White House, were charged with sex trafficking by their spouses, tax evasion by the IRS, money laundering by FINCEN, DOJ, INTERPOL, or other agencies. They ran the White House to such a degree that many news reports stated that “you couldn’t swing a cat at the White House without hitting a Google or Facebook insider.” ( ie: The Intercept – The Google Administration) The U.S. sought, solicited, encouraged, paid, traded influence and web services with these known mobsters of the tech industry and gave these sociopaths full credentials and authority under the U.S.
For over a decade, the U.S. had full and complete evidence to arrest the Cartel members referenced herein yet the U.S. did not arrest them because they were “friends of the White House” and they kept the pig trough of insider trading and crony capitalism flowing like a tsunami of skull-duggery. Thus the U.S. is responsible for all harms and damages to Victims in addition to the other reasons mentioned, herein, as to why the U. S. must pay Victims. On top of that, The U.S. sponsored, operated, financed and provided the taxpayer-paid resources to harm Victims.
The government argument that “…oh, that was just all that crazy Eric Schmidt, Elon Musk and Larry Page and Zuckerberg doing all that stuff.. they are just insane little frat house boyfriends that are out-of-control…” , does not hold water based on the facts herein.
The U.S. had direct financing and command-and-control executive management over all of the harms against Victims. In fact, top FBI, DOJ, SEC, FTC, CIA and other investigative officers have quit their agencies over this crony favoratism and failure to arrest. On March 22, 2022 in a related case, # 1:21-mc-00813-AT in U.S. District Court, Southern Division New York; Paul A. Calli and Charles P. Short, lawyers for the Victims filed a letter of the same date, provided in the EXHIBITS. In that letter to Honorable Judge Analisa Torres and in related national news articles, it has been revealed that the DOJ lied to, and concealed facts and evidence form the Judge.
This is of concern as Victims, is also a reporter and nationally published news publisher. On the same day, and at nearly the same time DOJ leaked government exhibit #3217 (GX 3217) which was admitted under seal, This leaked evidence provided the names of 121 famous sex cult partipants in the U.S. v. Ray sex cult case. The news organizations of the world have now published that list. It seems that someone at DOJ is trying to help Victims’s case, while others at DOJ are trying to harm Victims. Further, in the Project Veritas Vs. FBI case, it has been shown that the White House uses the FBI for personal retribution efforts. These two recent occurences further prove two of Victims’s claims:
1. That government officials hack citizens simply in reprisal and lie to Judges about it. In that other case, simply because some girl lost her diary.
2. That an active and ‘Deep State’ sex cult exists nationwide. That affiliated insiders operate and sex traffick in it and the government is fully aware of it.
The Defendants are 100% liable for the charges herein and for the harms to Victims listed herein.
LIST OF HARMS TO PLAINTIFF BY DEFENDANTS
HARM #1: MANIPULATION AND BLOCKADE OF PLAINTIFFS EARNED GOVERNMENT FUNDS
Victims applied for SSDI and a HUD home certificate. Contractors from The White House and California Senators, all of whom have vast documented court and news report records of hiring attackers from spy agencies for reprisal attacks on whistle-blowers, used their resources to stop all funding in Victims SSDI funding as reprisal for whistle-blowing. Dianne Feinsteins own staff and family confessed to these ‘dirty-tricks’ actions as reprisal for Victims’s testimony.. Her staff have been exposed by CIA staff as “the masters of dirty tricks reprisals…even as good as the ones we (THE CIA) pull off..” City and County officials have stated that they have “never seen it take so long”. According to all experts, the only way it could have been stone-walled this long is if a public official had ordered it slow-walked as part of the politial reprisal attacks on Victims. Three different counties have checked on this and said that Victims records ‘went missing” in a Lois Lerner type of error set.
The cut-off of Victims’s finances and benefits coincides, exactly, with his whistle-blower testimony AND to the reprisal threats and promises by THE ONLY PEOPLE IN THE WORLD capable of accomplishing such state-sponsored attacks. Defendants were the only entity with the means, the motivation and the proven history of such actions on a regular historical basis.
Feinstein’s current and former staff members (See the Dossier on Daniel Jones) (See the fact that Victims lived with, dined with and partied with her family and senior staff) have stated that the Feinstein and Pelosi offices commonly order citizens government funding to be cut off as political reprisal. The White does it almost every other day. In this case they did it to Victims at least three times.
Victims, had an industry standard pay rate of $10,000.00 per month, based on Salary.com, his patent issuances and accomplishment records in Silicon Valley contrasted with the salaries of less experienced executives at Google, Facebook, Netflix and Tesla. The U.S. Government states, via all of its agencies, that the minimum survivable cost-of-living in the Bay Area is $3200.00 per month. By intentional actions of government officers, in reprisal, Victims income was reduced to $300.00 per month for most of the past decades. Two SSA officials confessed to assisting in hit jobs on him including Mario U from the San Mateo SSA office and an official who worked at the San Francisco SSA office and who then went to work for a Senator who assisted in the attacks on Victims. When asked for Victims’s medical records SSA sent a huge number of medical records for two strange women in massive violation of federal medical privacy rights. The SSA Inspector General has shown Victims thousands of cases of politicians using SSA for political reprisal punishments. FBI IT experts and ‘Black Hat’ hackers can hack into every SSA server in minutes and change records, files and decisions. Rahm Emanual, Nancy Pelosi and Dianne Feinstein can do it with a single phone call. It should be noted by the Court that EVERY background check file in AMERICA was hacked and stolen by China within a few hours and that every hacking tool of the NSA and CIA was hacked by Russia and posted on the internet. It is IMPOSSIBLE for anyone to ever assert that “nobody can hack SSA”. That would be a remarkable lie. In fact, Victims has agency confimation that 95% of the Silicon Valley oligarchs entire family tax records, stock accounts, political payments and payola and pretty much everything that would destroy them, has been hacked and is in the hands of ICIJ (Panama Papers investigators), Propublica, FINCEN and pretty much everybody they would not want to have it.
Victims demands that the Court order SSA to award Victims his full SSDI backpay from 2007 to today, with interest, based on the fact that SSA was used to harm Plantiff as a reprisal tool. The Inspector General has proven this happens regularly and hundreds of other whistle-blowers are prepared to confirm this fact.
Victims has received multiple threats of death, personal, resource or physical harm.
HARM #2: THREATS OF DEATH AND ACTUAL MURDERS OF PEERS
Victims has actually been attacked as enumerated below and has active cases with SFPD, FBI, OSC and other agencies. Twice Victims car was rammed. The first time the attacker performed a PIT maneuver, flipping Victims car onto the concrete median wall on the Freeway across from Marin Joe’s restaurant in Marin County, causing massive damage. The attacker sped away. A car next rammed Victims parked car on Wildomar in Mill Valley and, at the same location, a man tried to drive has car through the fence into Victims’s cottage. Two other times, strangers pulled up along Victims, pointed at him and yelled “you are dead”. Victims has received threats by email and voicemail and had dead animals tossed over his fence. Further proving the at-risk claims of Victims. Victims, and his peers, had contact with the following persons in CASE X: Rajeev Motwani; Gary D. Conley; Seth Rich; Philip Haney; David Bird; Doug Bourn; Misti Epstein; Joshua Brown; Kenneth Bellando; Moritz Erhardt; Imran Aliev; Kate Matrosova; David Drye; Vincent Foster; Kathy Ferguson; Duane Garrett; Eric S. Fox; Judi Gibbs; Berta Caceres; Suzanne Coleman; L.J. Davis; John Hillyer; Stanley Huggins; Sandy Hume; Shawn Lucas; Gary Johnson; John Jones; John F. Kennedy, Jr.; Stephen Ivens; Mary ‘Caity’ Mahoney; Eric Butera; Danny Casolara; John Ashe; Tony Moser; Larry Nichols; Joseph Rago; Ron Brown; Bob Simon; Don Adams; Peter Smith; Victor Thorn; Lori Klausutis; Gareth Williams; Daphne Caruana Galizia; James D Johnston; Dave Goldberg; Loretta Fuddy; Paul Wilcher; Gary Webb; Beranton J. Whisenant Jr; Stanley Meyer; Jon Parnell Walker; Tyler Drumheller; Barnaby Jack; Dominic Di-Natale; Barbara Wise; Ilya Zhitomirskiy; Jeff Joe Black; Robin Copeland; John Wheeler; Ashley Turton; Michael Hastings; Antonin Scalia; David Koschman; David Werner; Alex Okrent; Kam Kuwata; Larry Frankel; And hundreds more connected to this case who suddenly, and strangely, turned up dead in this case and, ironically, their deaths all benefit the suspects in this case….Rajeev Motwani taught Google how to Google. Suddenly, in perfect health, they was found floating face-down, dead, in his Silicon Valley swimming pool. It helps certain people that they can no longer talk. Gary D. Conley was the CleanTech competitor to, and whistle-blower on, the suspects. He was suddenly found with a bullet in his head behind Beale Air Force base. It helps certain people that they can no longer talk. He TOLD Victims that someone from Google was going to kill him. Google programmer Forrest Hayes, who worked on Google search engine rigging, was suddenly found dead with the story that “they was overdosed by a Google hooker on his sex yacht”. Google associate and Tesla Investments founder Ravi Kumar was also killed by his hooker. Deep Google investor VC liason and husband of Facebook executive Cheryl Sandberg was suddenly found dead with a hole is his head. The “official” story is that they was the first person in history to be killed by his treadmill. David Bird was the Wall Street Journal energy reporter who was working on a story that involved Cleantech energy connections of some of the suspects. He was working on a story about who controlled the modern energy industry and cleantech. He went for a walk and was found a long time later, dead, floating in a pond. It helps certain people that they can no longer talk. One Mr. Breitbart was a famous blogger, who railed on the web about the political manipulations of the suspects. Suddenly, they had a “heart attack” in his shower and died. It helps certain people that they can no longer talk on the blogs. Mr. Karl Slym , with Tata Motors was involved in a car deal with some of the suspects for one of the biggest Indian auto-makers. Suddenly they was a stain on the sidewalk, accomplished by his fall from the top of a skyscraper hotel. It helps certain people that they can no longer talk. Doug Bourn, The senior electrical engineer at Tesla (Google’s covert partner), Andrew Ingram of Palo Alto, a top systems electrical engineer at Tesla; and Brian M. Finn the senior manager of interactive electronics, at Tesla, had deep knowledge of financial misdeeds and technical cover-ups at Tesla Motors. They were key parts of the Tesla operation. For some reason, they all got into a private airplane, in perfect health, and then the airplane plowed into the ground, killing all three at once. It helps certain people that they can no longer talk. They wrote, and helped describe, in Tesla’s own federal patent filings, the fact that Tesla’s batteries would kill you, maim you and/or burn your house down. Tesla did not realize this when they paid the federal patent filing fees. When Tesla, later realized this, they were forced to give all of their patents away for free. These three senior engineers had deep inside knowledge of the Tesla Motors operations. Their aircraft suffered an “Engineering failure”. This case involves potential crimes by two Presidents of The United States, their staffs, U.S. Senators and the Silicon Valley oligarchs that financed and controlled them, two wars and trillions of dollars of manipulated U.S. Treasury monies and stock marke monies. How could anyone think this was NOT a life-endanging situation for the Victims?
The other attacks, which only state-sponsored attackers would seem to be capable of, were:
HARM #3: THE GOVERNMENT DEFRAUDED PLAINTIFF OVER AND OVER:
Government agency bosses solicited Victims with false promises of future loans, carbon credit sales, billions of dollars of stock market valuation profits, contracts and/or grants from their agencies and caused the Victims and his associates to expend millions of dollars and years of their time for projects which those government bosses had covertly promised to their friends. They used Victims’s ‘nice guy’ brand as a “smokescreen” to cover their illegal government slush-funds for Victims competitors and personal enemies who were OWNED by government officials. By using this tactic, the attackers drained the Victims’s funds and forced Victims into an economic disaster, without the government bosses fearing any reprisal for their scam. The crony insiders made hundreds of billions of dollars in profit in the notorious Solyndra-type scandals as seen in the CBS 60 Minutes episode: “The Cleantech Crash”, thousands of TV news segments and the related GAO and Congressional corruption reports.
HARM #4: THE PLACING OF MOLES AND SPYING ON PLAINTIFF:
White House financier Kleiner Perkins placed moles inside of Victims’s companies in order to sabotage, delay and misdirect operations. The moles were discovered to be staff of Kleiner Perkins. The main offices of Kleiner Perkins were broken into, per San Mateo County police reports, and records of corruption copied or duplicated by a state-sponsored intelligence agency entity, which provided further proof that Kleiner Perkins and the White House were exchanging Quid Pro Quo. Tom Perkins, one of the founders of Kleiner Perkins told Victims that they was on “A government hit-list” for exposure the corruption of Silicon Valley titans and government executives. John Doerr, another partner, told Scott at a, VC conference, that they will make sure the government kills of any effort to support fuel cells (which compete with his and Elon Musk’s lithium batteries)
HARM #5: BLOCKADES OF PLAINTIFF ACCESS TO LEGAL COUNSEL:
– Detailed further in the EXHIBITS, below, Defendants used every trick in the book to keep Victims from gaining equitable legal justice or representation because exposure of Defendants crimes would shame them Government officials and the federal agency: Legal Services Corporation (LSC corporation -A federal agency dedicated to providing legal services to citizens) blockaded Victims rights to legal representation in order to prevent Victims from personally suing the attackers because such a lawsuit would have embarrassed corrupt public officials. High tech law firms that were discussing a services agreement with Victims were threatened and ordered to not help Victims or “they would be black-listed or be cut-off from tens of millions of dollars of Google, Netflix, Facebook and government contracts”. Individual lawyers were threatened with black-listing and getting “flooded with more filings than you could ever respond to in your life-time...” LSC officials, who were almost entirely Obama Administration associates, refused to assist with lawyer referrals. That is a violation of their federal contract with The U.S. Government .
HARM #6: HIRED CHARACTER ASSASSINATION AND DEFAMATION SERVICES THAT DEFENDANTS USED TO DESTROY PLAINTIFF’S LIFE
Defendants purchased over $30 Million dollars of attacks against Victims with Media Matters, The Gawker/Gizmodo Tabloid empire and Google. This attack is detailed in the attached EXHIBITS. It was equal in scope and cost to an attack on a Presidential candidate by another Presidental candidates opposition research task force.A sophisticated animated attack film was produced by Google/Youtube and Nicholas Denton attacking Victims. An animated film is an expensive effort involving considerable time and expense. An attacker must be well financed to undertake such an effort. The film was published on YouTube and locked onto the very top search result line on every YouTube search in front of 7.5 billion internet users for over a decade. The damage to Victims reputation is estimated in the tens of millions of dollars. YouTube steadfastly refused to remove or adjust the search results even though YouTube executives knew Victims and knew that the video represented a character assassination attempt against Victims because YouTube owners finance the political campaigns of the public officials who ordered the attacks. While Google/YouTube stated to Congress that all of it’s search results are arbitrary, the never-moving search result of this attack video proved that Google’s and YouTube’s search results are manually manipulated by human maintained black-lists. The corrupt officials hired Nicholas Guido Denton and his character-assassination-for-hire sleazy tabloid publication empire known as Gawker Media AKA Gizmodo Media. They own Gawker, Gizmodo, Jalopnik and a number of fake news sites based in the USA and near-Russian regions. The offshore sites are used for money laundering and tax evasion.
The FBI has been asked to interview and financially trace the payments and command-and-control orders back and forth between Nicholas Guido Denton and his attacker/operatives: Ian Fette, Adrian Covert, Nick Cook, Gabrielle Darbyshire, John Hermann, Patrick George, et al and Google. All of whom transferred payments and communications between each other to conspire, operate, produce and publish the articles, videos, blogs and server manipulations for the attacks against the victims around the world. These attacks resulted in billions of dollars of damages to the victims.
The orders for these attacks can be traced back to The White House. This ended Victims’s life but created an enemy for the DOES and ROES that has lots of of investigator contacts and nothing to lose. The Defendents have caused the deaths of more children than any other entities. Harassment is harassment – whether it happens at school, at the playground, on the job, or on the internet. But online bullying is downplayed. Victims are stigmatized, mocked as oversensitive snowflakes who can’t take a joke. Plenty of people are unwilling to accept that victims can be seriously hurt by this behavior. Internet harassment is not only real and damaging, it represents a threat to the most vulnerable among us: children. Cyberbullying statistics show the high cost of online harassment. From increased depression and suicide rates to social anxiety and alienation, the pain and consequences of online harassment are as severe as they are undeniable. Imagine every new friend, potential date, your fiance’, your bank, anybody.. typing your name on the internet and seeing that Google says that you are a scumbag. Nobody will ever talk to you, hire you or help you ever again. Google, Gawker and Gizmodo are now known to partner together on character assassination efforts. One of their bloggers hired to “kill” Victims even advertises himself on Facebook, globally, as an assassin-for-hire. Victims has acquired the banking records of these Co-conspirators showing that they, and the U.S. government wired millions and millions of dollars between each other for these “spy agency” dirty tricks hit jobs.
Google knows Victims personally. Victims went to school and events with the founders. It was a lie for Google and YouTube to say over-and-over that they never heard of Victims so they “can’t remove the attacks because it is ‘just how their algorithm works’…” The founder’s teacher: Rajeev Motwani, revealed to Victims that Google manually sets all of their key search results BY HAND. Rajeev died was murdered for telling the truth about Google’s insidious plans and internet manipulations. Investigators suspect shell fish toxin or a reverse taser-like electronic heart-attack inducing defib device was used to kill him.
Victims charges proved that Google manually rigs search results based on cronyism and that Google/YouTube lied to Congress about not doing so. This allowed Victims to drive U.S. agencies and State AG’s to sue Google/Alphabet/Youtube for being lying, manipulate, society-abusing, child-killing, monopolistic monsters.
Take note of this letter from one of Victims’s past lawyers to those attackers that were hired by THE WHITE HOUSE to produce fake articles, animated videos and fake blogger comments, all tracked back to the same servers and attackers:
Even though the Google/Gawker/Gizmodo produced and hosted attack articles and animated videos were completely discredited as a “character assassination hatchet job paid for by politicians”; by every known expert, Defendants still post them on their servers with hidden “P8” codes covertly embedded in the search engines to trick the public, in front of 7 billion internet readers as “payback”, in order to operate their reprisal attacks. No other servers or publishers in the world host and lock this attack media on their search results EXCEPT DEFENDANTS MEDIA COMPANIES. This ALONE would seem to prove that Defendants did the harms that they are charged with doing as Defendants are the only ones running, hosting and operating the attacks on Victims on all of Earth!
Victims has, over and over, demanded that the FBI, POLICE, FINCEN and other enforcement investigators reveal what they discovered when they traced the compensation routes and command-and-control management of these attackers. Victims demands that this Court order the FBI, FINCEN and the NSA to reveal those compensation path records on the attackers from their investigations.
One might wonder why it has been so hard to get this information from the authorities. If the FBI reveals that the path-of-compensation goes from Adrian Covert, Nicholas Guido Denton and John Herrman right to the Oval Office in the White House, then the question is asked and answered. White House staff members Jay Carney, David Axelrod and Robert Gibbs have said “maybe”. White House staff insider Jofi Joseph has said “without a doubt”. Rahm Emanual’s White House staff say that, while in the White House, Rahm ordered all kinds of hit-jobs on whistle-blowers.
Gawker Media and Gizmodo Media have engaged in the origination of, production of and global broadcast of compensated character assassination videos and articles as a reprisal-service-for-hire (like Fusion GPS, Black Cube, Black Water and other related services) because we were FBI and GAO witnesses against Gawker and Gizmodo financiers. As 1.) the only publishing group on Earth to have engaged in such attacks and 2.) since the attacks were financed by complainants business competitors and 3.) since adversaries own staff have admitted to the scheme and 4.) since communications, FBI records and previous litigation records prove complainants assertions, complainants are justified in their demands.
The attacks and broadcast of multiple defamation attack articles and videos by Gawker Media, Google, YouTube and Gizmodo Media has been operating as recently as this today, thus the statutes of limitations are not exceeded. Well known U.S. government political figures and political financiers hired Gawker Media, Gizmodo Media and “Nick” Denton to undertake these ongoing attacks and to manipulate web servers to operate those attacks globally and permanently. The attackers hired Gawker Media, Gizmodo Media, “Nick Guido Denton”, Univision/Unimoda, Google and YouTube (essentially all the same people) to engage in reprisals because of the Victims’s testimony against the Cartel in federal investigations and because the plaintiff had superior technologies that the attackers could not compete with. Transaction documents showing payments between the “bad guys” in this case, were recently uncovered in other court cases.
Defendant adversaries produced a series of videos and defamation articles and used internet server technology tricks to place those attack materials in front of 7.5+ billion people day after day, year after year, refreshing the attack daily. This is, essentially, a “hit-job” service that Univision provides as a side gig through it’s TV networks and it’s offensive tabloid brands of: Gizmodo, Jalopnik, Jezebel, Gawker and other Univision/Unimoda assets along with it’s partnership with Google for the operation of such attacks. “Univision uses this service as a political-payback tool for politicians as well as an anti-trust violating anti- competition tool for its clients”, claim Victims. The Victims are informed and believe and, based on that information and belief, allege that the named Defendants herein and each of the parties designated as a “DOE” and every one of them, are legally responsible jointly and severally for the Federal RICO Statute violating events and happenings referred to in the within Complaint for Intentional Interference with Contractual Relations, Intentional Interference with Prospective Economic Advantage, Cyberstalking, Fraud, Invasion of Privacy, Unfair Competition and Theft of Intellectual Property and RICO statute violations.
In particular, Defendants took compensation for, and engaged in, malicious and coordinated tactics to seek to destroy, damage, harm and ruin Victims via an illicit media “hit-job” service which Defendants regularly offered in covert commerce and engaged in regularly against targets that Defendants were hired to seek to ruin as part of reprisal, vendetta, retribution programs operated for business and political competitors of the targets. Historical facts and other history-making lawsuits by third parties, has proven Defendants to be the single largest core violator of human rights, in this manner, in the world. Defendants offer the service of creating and publishing contrived “hatchet job” movies, fake news articles, faked comments and repercussion backlinks describing the Victims in horrific descriptors. Defendants media holdings manipulate national elections.
Let’s be clear on this: Victims does swear, warrant and certify that Google, Facebook, YouTube, The Elon Musk Group, Twitter and Linkedin plan and operate the conscious and manual manipulation of national American elections and international elections.
The attack material is reposted, “impression accelerated”, “click-farm fertilized” and Streisand array cloned over-and-over by Defendants massive character assassination technology via servers, algorithms and technical internet manipulation, daily, as recently as yesterday. Defendants also embed the article in job hiring databases on Axciom, Palantir, Taleo and other databases used by all hiring and recruiting services in order to prevent Victims from ever receiving income for W2 or 1099 work ever again. Defendants own staff then post thousands of fake comments, below each attack item, under fake names, designed to make it appear as if a broad consensus of the public agreed with the defamation messages by Defendants. Almost all of the fake comments were created by a handful of Defendants own staff pretending to be a variety of outside voices. Defendants provide the service of delivering “weaponized text and media to corporate clients”. Defendants replicated various versions of these attack items across all of their different brands and facade front publications and addedadditional fake comments to each on a regular basis.
A. Defendants have formed a business and political and industry manipulation “Cartel” intended to inflict corruption upon the United States Federal Government, The State Government and the California State authorities, as defined by law under RICO Racketeering Statutes for the purpose of manipulating the value of stock market holdings and controlling political policy decisions.
B. In exchange for financing, Defendants Clients gave Defendants Associates business monopolies and government contract monopolies and media distribution exclusives worth trillions of dollars. This was an illegal quid-pro-quo arrangement. Victims designed, produced, received patent awards on, received federal commendations for, received federal funding for and first marketed the very products which Defendants copied and made billions of dollars on and which Defendants felt might beat them in hundreds of billions of dollars of competitive market positions and stock market trades. Companies operated by Victims included automobile design and manufacturing companies, global television broadcasting companies and energy companies which are commonly known to have generated hundreds of billions of dollars in profits, revenue and stock market transactions for Defendants competing holdings at Victims expense. Defendants operated a criminal CARTEL as defined by RICO LAWS and that Cartel ran an an anti-trust market rigging and crony political payola operation. Defendants spent tens of millions of dollars attacking Victims because Defendants were not clever enough to build better products. Defendants chose to “CHEAT RATHER THAN COMPETE” and to try to kill Victims lives, careers, brands, revenues, assets, businesses and efforts via malicious and ongoing efforts.
C. The U.S. Attorney General has been informed, in writing, of these charges and Victims understand that DOJ officials have an ongoing investigation into these matters.Under investigation for these crimes, New York State attorney general Eric Schniderman was recently forcedto quit over corruption and sexual cult charges involving the NXIUM group and related matters.
D. Due to Defendants fears of the loss of up a trillion dollars of crony payola from their illegal abuse of taxpayer funds, Defendants engaged in felonious actions in order seek to intimidate others.
E. Just as, over time, the Watergate crimes are now intimately documented and detailed; over time The “Cleantech Crash Scandal” as featured on CBS News 60 MINUTES TV Show, has been detailed and exposed in numerous federal, news media and public investigations. Significant barriers to justice were illicitly placed in front of Victims by Defendants.
F. Defendants organized and operated a series of malicious attacks and thefts against Victims as reprisals and competitive vendettas. Defendants report to the FBI, GAO, FTC, SEC, Congressional Ethics Committees, The White House and other entities on a regular basis.
G. Defendants and their associates Elon Musk, Jon Doerr, Eric Schmidt, Larry Page, Steve Jurvetson, Vinod Khosla and other members of the “Silicon Valley Cartel” are documented in tens of thousands of news reports, federal law enforcement reports and Congressional reports in their attempts to infiltrate and corrupt the U.S. Government in an attempt to route trillions of tax dollars to Defendants private accounts. Defendants perceived Victims as a threat to their crimes. Federal investigators, news investigators and whistle-blowers have reported to Victims that Defendants were the financiers and/or beneficiaries and/or command and control operatives for the crimes and corruption disclosed in the CBS NEWS 60 Minutes investigative reports entitled: “The Cleantech Crash”, “The Lobbyists Playbook” and “Congress Trading on Insider Information”; The Feature Film: “The Car and the Senator” Federal lawsuits with case numbers of: USCA Case #16-5279; and over 50 other cases including the ongoing “Solyndra” investigation and federal and Congressional investigations detailed at:
http://greencorruption.blogspot.com
and
https://theintercept.com/2016/04/22/googles-remarkably-close-relationship-with-the-obama-white-house-in-two-charts/
… and thousands of other documentation sites. Victims are charged withengaging in these crimes and corruptions against Victims and financing and ordering attacks on Victims. Victims engaged in U.S. commerce and did everything properly and legally. Unlike Defendants, Victims did not steal technology. Unlike Defendants, Victims did not bribe elected officials in order to get market exclusives. Unlike Defendants, Victims did not poach Defendants staff. Unlike Defendants, Victims were the original inventors of their products. Unlike Defendants, Victims did not operate “AngelGate Collusion” schemes and “High Tech No Poaching Secret Agreements” and a Mafia-like Silicon Valley exclusionary Cartel. Unlike Defendants, Victims did not place their employees in the U.S. Government, The California Government, The U.S. Patent Office and The U.S. Department of Energy in order to control government contracts to Defendants exclusive advantage. Unlike Defendants, Victims did not place moles inside of competitors companies. Unlike Defendants, Victims did not hire Gawker Media and Think Progress to seek to kill Victims careers, lives and brands. Unlike Defendants, Victims did not rig the stock market with “pump-and-dump”, “Flash Boy” and “Google-stock/PR-pump” schemes. Victims engaged in hard work every day of their lives for the time-frame in question under the belief that the good old American work ethic and just rewards for your creations was still in effect in the U.S.A., and that the thieves and criminals that attempted to interdict Victims would face Justice. In a number of circumstances Defendants took advantages of Victims hard work via come-ons; Defendants then made billions of dollars from Plainiffs work at Victims expense and attacked Victims in order to reduce Victims competitive and legal recovery options.
H. Defendants exchanged payments for services via cash, stock warrants, illicit personal services, media control and a technology known as a “Streisand Effect Massive Server Array” which can control public impressions for, or against a person, party, ideology or issue. Defendants StreisandEffect internet system was used to destroy Victims in reprisal, retribution, and vendetta for Victims help with law enf ment efforts in the case and because Victims companies competed with Defendants companies with superior technologies.
I. Defendants have used their Streisand Effect technology to build a character assassination ring of bloggers and hired shill “reporters” who engage in a process called a “Shiva”. This process is named after a Victims in a similar case named: Shiva Ayyadurai, the husband of Actress Fran Drescher. Shiva Ayyadurai holds intellectual property rights to part of Defendants email technology. In fact, the people most threatened by the Shiva Ayyadurai patent right claims, ironically turn out to be Defendants and, in particular, Defendants associates Elon Musk, Jon Doerr, Eric Schmidt, Larry Page, Steve Jurvetson, Vinod Khosla and other members of the “Silicon Mafia” who own most of the main companies exploiting email technology. Were Shiva Ayyadurai to prevail in his claims, Defendants would owe him billions of dollars. “Running A Shiva” involves the production of a series of Defamation articles by bloggers who act asif they are independent from Defendants but are in fact, not. Defendants used “the Shiva” to attack and seek to destroy Donald Trump, Shiva Ayyadurai, Victims, and numerous political figures. Univision, Unimoda,Jalo pnik, Gawker Media, Gizmodo and over a hundred stealth-ed, and overt, assets of Defendants have been using “The Shiva” network to attack Donald Trump, Shiva Ayyadurai, Victims, and numerous political figures as recently as this morning, thus, the time bar restarts every day. Victims have pleaded with Defendants to cease their attacks but Defendants have refused to comply. Even with Fran Drescher’s ongoing royalty payments from her popular television series, friends have reported that the attacks on the Ayyadurai family have been devastating and have caused massive damages and personal and emotional devastation.
J. Defendants produced animated movies, attack articles, fake blog comments, DNS routes, “Shiva” Campaigns, and other attack media against Victims and expended over $30 million dollars in value, as quantified by Defendants partner: Google, in placing the attack material in front of 7.5 billion people on the planet for the rest of Victims lifetime. No person could survive such an attack and in the case of Victims, lives were destroyed and multiple companies invested into by Victims, which Defendants made over $50B off of the copies of, were destroyed because they competed with Defendants.
8. The Victims are informed and believe, and based on that information and belief allege that at all times mentioned in the within Complaint, all Defendants were the agents, owners and employees of their affiliated insiders and, in doing the things alleged in this Complaint, were acting within the course and scope of such agency and employment.
9. As to any corporate employer specifically named, or named as a “DOE” herein, the Victims are informed and believe and therefore allege that any act, conduct, course of conduct or omission, alleged herein to have been undertaken with sufficient, malice, fraud and oppression to justify an award of punitive damages, was, in fact, completed with the advance knowledge and conscious disregard, authorization, or ratification of and by an officer, director, or managing agent of such corporation. The Statute of Limitations and time bar on this case has not expired. Victims only became aware of all of the facts recently due to the FBI, Congressional and hacker-exposed investigation data on Defendants operating and receiving cash, rewards and assets from an illegal and illicit set of political slush-funds established to compensate them for financing political campaigns. The Sony, Clinton, DNC, HSBC, Panama Papers and other hacks and publication of all of the relevant files and the Congressional investigation of illicit activities and the continuing issuance of federal documents to Victims confirming Victims intellectual property areall vastly WITHIN the statutes of limitations to allow this case to proceed to Jury Trial. Victims has had a long, ongoing and high-level interaction with Defendant in both the work effort and the monetization and collection effort. Victims has been continually interactive with Defendant in order to try to collect his money. Attacks and interference with Victims has occurred as recently as this week by Defendants. The Victims, whose multiple businesses ventures had already suffered significant damage as the result of the online attacks of the Defendants, contacted renowned experts, and especially Search Engine Optimization and forensic internet technology (IT) experts, to clear and clean the internet of the false, defamatory, misleading and manufactured information belittling the Victims, attacking them and discrediting their reputation as an inventor, product developer and project director from their websites.
None of the technology experts hired by the Victims, at substantial expense, were successful in their attempts to clear, manage or even modify the false, defamatory, misleading and manufactured information belittling the Victims, attacking him and discrediting their reputation as an inventor, product developer and project director which only Defendants, the controlling entity of the internet, refused to remove. In fact, those experts were able to even more deeply confirm, via technical forensic internet analysis and criminology technology examination techniques that Defendants was rigging internet search results for its own purposes and anti-trust goals.
All efforts, including efforts to suppress or de-rank the results of a name search for “Victims” failed, and even though tests on other brands and names, for other unrelated parties did achieve balance, the SEO and IT tests clearly proved that Defendants was consciously, manually, maliciously and intentionally rigging its search engine and adjacent results in order to “mood manipulate” an attack on Victims.
In fact, the experts and all of them, instead, informed the Victims, that, not only had Defendants locked the false, defamatory, misleading and manufactured information belittling the Victims, attacking them and discrediting their reputation as an inventor, project developer and project director into its search engine so that the information could never be cleared, managed or even modified, Defendants had assigned the false, defamatory, misleading and manufactured information belittling the Victims, attacking them and discrediting their reputation as an inventor, project developer and project director “PR8” algorithmic internet search engine coding embedded in the internet information-set programmed into Defendantsinternet architecture. [See, Information received from one of over 30 IT, forensic network investigators and forensic SEO test analysts, a true and correct copy of which is attached hereto in the Exhibits.]
Per the many world-wide search engine results forensic analysis experts Victims hired – They had never seen search engines results that were locked so maliciously, manually and unmovably into Google’s and YouTube’s search results. “It was as if the CIA, or Larry Page himself, was doing this”, said one. Victims placed associates inside of Google and, among other things, acquired bank records proving Google and the attackers were exchanging millions of dollar with each other.
Victims even went to the effort of placing nearly a thousand virtual forensic test servers around the globe, using empty space on third-party existing servers owned by hundreds of other people, in order to monitor and metricize the manipulations of search results of examples of the
Victims name in comparison to the manipulations for PR hype for Defendants financial partners, for example: the occurrence of the phrase ”Elon Musk”, Defendants business partner and beneficiary, over a five year period. The EU, China, Russia, and numerous research groups (ie:
http://www.politico.com/magazine/story/2015/08/how-google-could-rig-the-2016-election-121548 By Robert Epstein ) have validated these forensic studies of Defendants architect-ed character assassination and partner hype system .
The “PR8” codes are hidden codes within the Defendants software and internet architecture which profess to state that a link is a “fact” or is an authoritative factual document per Defendants research. By placing “PR8” codes in the defamatory links that Defendants was manipulating about Victims, Defendants was seeking to tell the world that the links pointed to “Facts” and not “Opinions”. Defendants embedded many covert codes in their architecture which marketing the material in the attack links and video as “facts” according to Defendants.
The “PR8” codes are a set of codes assigned and programmed into the internet, by the Defendants to matters it designates as dependable and true, thereby attributing primary status as the most Defendants is known to have provided tens of millions of dollars to this tabloid chain per Defendants financial staff, SEC filings and disclosures in other legal cases.
Victims also used CIA technology call “Steganography” to embed text-based messages and codes into photos and videos in order track Google and YouTube’s global impression manipulations and create a significant and important link to be viewed by online researchers regarding the subject of their search.
Defendants were fully aware that all of the information in the attack articles against Victims was false, Defendants promo ted these attacks as vindictive vendetta-like retribution against Victims.
At all times Defendants maintained it had no subjective control or input into the rankings of links obtained by online researchers as the result of a search on its search engines and that its search engine algorithms and the functions of its media assets were entirely “arbitrary” according to the owners and founders of Defendants.
In or about April 15, 2015, The European Union Commission took direct aim at Defendants charging the their Internet-search giant with skewing and rigging search engine results in order to damage those who competed with Defendants business and ideological interests.
In those proceedings, although Defendants continued to maintain that it has no subjective control or input into the rankings of links obtained by online researchers as the result of a searchon its sear ch engines and that its staff had no ability to reset, target, mood manipulate, arrange adjacent text or links, up-rank, down-rank or otherwise engage in human input which would change algorithm, search results, perceptions or subliminal perspectives of consumers, voters, or any other class of users of the worldwide web, also known as The Internet, the court, in accord with evidence submitted, determined that Defendants, does in fact have and does in fact exercise, subjective control over the results of information revealed by searches on its search engine.
Defendants has a variety of such hidden codes and has various internal names for such codes besides, and in addition to, “PR8”. Defendants has been proven to use these fact vs. fiction rankings to affect elections, competitors rankings, ie: removing the company: NEXTAG from competing with Defendants on-line; or removing political candidates from superior internet exposure and it is believed by investigators and journalists, that Defendants are being protected from criminal prosecution by public officials who Defendants have compensated with un-reported campaign funding. As a result of receiving this information, the Victims became convinced of the strength and veracity of their original opinion that the Defendants, had, in fact posted the false, defamatory, misleading and manufactured information belittling the Victims, attacking them and discrediting Victims reputation as inventor, project developer and project designer had been intentionally designed, published, orchestrated and posted by them in retaliation to the true testimony provided by the Victims, to the Government Office of Accountability of the United States in May of 2005, and to the Securities and Exchange Commission, The Federal Bureau of Investigation, The United States Senate Ethics Committeeand other investigating parties, and had been disseminated maliciously and intentionally by them in an effort to do damage to their reputation and to their business prospects and to cause him severe and irremediable emotional distress.
In fact, the Victims, has suffered significant and irremediable damage to their reputation and to their financial and business interests. As a natural result of this damage, as intended by the Defendants, Plaintiffshas also suffered severe and irremediable emotional distress.
To this day, despite the age of the false, defamatory, misleading and manufactured information belittling the Victims, attacking him and discrediting their reputation as an inventor, project developer and project director, in the event any online researcher searches for information regarding the Victims, the same information appears at the top of any list of resulting links.
In addition, due to their control of all major internet database interfaces, Defendants have helped to load negative information about Victims on every major HR and employment database that Victims might be searched on, thus denying Victims all reasonable rights to income around the globe by linking every internal job, hiring, recruiter, employment, consulting, contracting or other revenue engagement opportunity for Victims back to false “red flag” or negative false background data which is designed to prevent Victims from future income in retribution for Victims assistance to federal investigators.
HARM #7: DEFENDANTS USED FACTORY-PROCESSED SOCIAL MEDIA ATTACKS AGAINST PLAINTIFF:
In the attached book: “ATTACKED”, the Court will see the CIA, FSB and MI6 tactics and techniques that are trained and practiced, illicitly, by political officials. Social networking sites including MeetUp, Match, Facebook, etc. and all other IAC-owned, or similar, sites (IAC is managed by Hillary Clinton’s daughter, whose Mother knew Victims) have had their profiles, texts, and inter-member communications, since those companies were started, hacked or purchased. The financiers of almost everyone of these sites are also the financiers of the suspects. The attack service providers use Palantir, Acronym, In-Q-Tel financed data analysis software to analyze every activity in those services in order to find honey-trap, blackmail and social conflict exploitation opportunities. Your social life will, essentially, end. Every photo on every social site is cross checked with every other photo on the internet in order to cull your Facebook, Linkedin, Snapchat and other social media together to create a total manipulation profile data file on you. New contacts on these sites were contacted by the attackers and told to “avoid” the Victims in order to damage Victims. These attacks were all documented and operated against Victims as detailed in the EXHIBITS and evidence repositories. Defendants bought these services from Eastern Bloc nations, China and South America. “The Agency”, in Russia does much of this work. They are hard at work, even as recently as today according to the CIA, pushing a “positive spin” on Russia’s invasion of the Ukraine based on Hunter Biden’s computer leaks.
HARM #8: GOVERNMENT OFFICIALS CAUSED SSA AND HUD BENEFITS BLOCKADES AND MANIPULATIONS AS REPRISAL AGAINST PLAINTIFF:
Social Security, SSI, SDI, Disability and other earned benefits were stone-walled. Applications for benefits for the Victims were intentionally “lost” like a “Lois Lerner hard drive”. Files in the application process “disappeared”. A U.S. Senator ordered Victims benefits to “never be approved” even though Victims worked 60 hour+ weeks for decades in service to their nation and their community. A SSA official in the local SSA office, who had a devout expressed hatred against one United States President ordered a benefits blockade against Victims because they found out that Victims ex-lawyer now worked in the White House. Forensic evidence and backgrounders on every person who worked on, or had access to, Applicants files, records, benefits decisions and related data sets shows that a number of those employees and contractors were members, financiers, web promoters or supporters of ANTIFA anarchy groups or KKK or Proud Boys related political activist-type groups. In San Francisco and Marin Counties SSA offices, in employees workspaces and on their Facebook and MySpace sites, many employees proudly display pictures of themselves wearing their pink “pussy hats”, black riot gear and sporting political tattoos. FBI records and IG investigations show that SSA has the highest percentage of political activist employees of any federal agency. Such persons are inclined to become drunk with power when allowed access to the trillions of dollars of government technology on the SSA file and decisions systems.
A number of these persons have worked for, or with, U.S. Senators and other politicians who targeted Applicant in political reprisal. At least 3 persons in the San Francisco SSA office, at least 2 persons in the San Mateo SSA office and at least 2 persons in Marin SSA office are known to have engaged in such actions. Applicants funding and benefits were manipulated, so as to harm Applicant, as political reprisal as vendetta for his provision of testimony to federal investigators in a trillion dollar political corruption matter involving famous political figures featured in global news coverage. A vast number of agency abuse cases and lawsuits are now on public record in the Inspector General’s offices and federal courts. It is an indisputable fact that some government agencies run “hit-jobs” on citizens on orders from certain corrupt politicians.
These actions are felony violations of the law. Federal and State Agencies including SSA, FEC, GOVT, HHS, VA, CIA, HUD, SA, SEC, FBI, DOJ and many others, have been charged, and found guilty, in these crimes against citizens. In the Congressional investigation published by the United States Congress in review of the U.S. Department of Energy LGP/ATVM programs, it is clearly proven that the U.S. Department of Energy was used as a slush-fund by some GOVT executives in order to pay off campaign financiers by attacking and sabotaging their competitors. The GOVT Paducah Gaseous Diffusion Plant under contracts with The U.S. Government and the government-owned U.S. Enrichment Corp paid $5M whistle-blower awards to those whistle-blowers who were attacked, using government agency resources, for reporting a crime. Dept. of Energy Hanford URS has agreed to settle a lawsuit brought by former employee Walter Tamosaitis for $4.1 million.
The settlement in the whistle-blower case comes almost one year before the case was set for a jury trial in federal court in Richland and compensates Tamosaitis for attacks against him, by GOVT officials, in retribution for reporting a crime. VA officials attacked hundreds of citizens who reported corruption, ie: https://www.thenewamerican.com/usnews/health-care/item/18610-va-whistleblowers-facing-retribution. As shown in this report: https://www.pogo.org/analysis/2018/08/new-report-confirms-whistleblower-retaliation-is-alive-and-well-at-department-of-veterans-affairs/, Agencies attack often and harshly. CIA and NSA executives have been widely shown to use spy tools to attack domestic citizens they don’t like, ie: https://www.dailymail.co.uk/news/article-2435011/NSA-employees-used-phone-tapping-tools-spy-girlfriends-cheating-husbands.html , and hundreds of other news links that can be provided. Elon Musk and Tesla, as well as Eric Schmidt and Larry Page at Google, have been proven to use the CIA group: IN-Q-TEL, to run government sponsored/financed attacks on business competitors. In Civil Action No. 1:13-cv-00777-RBW GOVERNMENT AGENCIES WERE CAUGHT BEING USED FOR ATTACKS AGAINST CITIZENS AND PUNISHED IN THE COURT AND THE MEDIA! The IRS, and hordes of other government agencies have been caught and proven, IN COURT, to target and attack people for presumed political differences.
Why should we assume that the Social Security Administration is not ALSO doing this too to harm citizens who speak out? The Lois Lerner IRS attacks took many years to resolve. In an unprecedented victorious conclusion to a four year-long legal battle against the IRS, the bureaucratic agency admitted in federal court that it wrongfully targeted citizens, during the Obama Administration, because of their political viewpoints and issued an apology to those people for doing so. In addition, the IRS is consenting to a court order that would prohibit it from ever engaging in this form of unconstitutional discrimination in the future. In a proposed Consent Order filed with the Court, the IRS has apologized for its treatment of U.S. citizens including organizations from 20 states that applied for 501(c)(3) and (c)(4) tax-exempt status with the IRS between 2009 and 2012 — during the tax-exempt determinations process. Crucially, following years of denial by the IRS and blame-shifting by IRS officials, the agency now expressly admits that its treatment of our clients was wrong and a total violation of our Democracy. As set forth in the proposed Order: “The IRS admits that its treatment of Victims during the tax-exempt determinations process, including screening their applications based on their names or policy positions, subjecting those applications to heightened scrutiny and inordinate delays, and demanding of some Victims’ information that TIGTA determined was unnecessary to the agency’s determination of their tax-exempt status, was wrong.
For such treatment, the IRS expresses its sincere apology.” Throughout litigation of this case, activists have remained committed to protecting the rights of the public who faced unlawful and discriminatory action by the IRS and other agencies. The objective from the very beginning has been to hold agencies accountable for corrupt practices.
This Consent Order represents a historic victory for the public and sends the unequivocal message that a government agency’s targeting of citizens organizations, or any organization, on the basis of political viewpoints, will never be tolerated and that revenge will be swift and vast. The Order will put an end, once and for all, to the abhorrent practices utilized against citizens, as the agreement includes the IRS’s express acknowledgment of – and apology for – its wrongful treatment of the public. While this agreement is designed to prevent any such practices from occurring again, rest assured that all public interest lawyers will remain vigilant to ensure that the IRS, SSA, DOJ or SEC does not resort to such tactics in the future. Per detailed reports, in March of 2012 lawyers began being contacted by literally dozens of citizens and groups who were being harassed by the Obama IRS after submitting applications for tax-exempt status. Their tax-exempt applications were held up for years (over seven years in some cases), and they began receiving obtrusive and unconstitutional requests for donor and member information. That began a now more than five and a half year fight with the burgeoning bureaucracy at the IRS. Then on May 10, 2013, Lois Lerner, the then head of the IRS Tax Exempt Organizations Division, publicly implicated the IRS in one of the worst political targeting scandals of the century.
This is an extraordinary victory against government agency abuse. It sends a powerful warning to the deep state bureaucracy that it will not be allowed to violate the Constitution in order to silence and shut down the whistle-blowers. In addition to the IRS’s admissions of and apology for its wrongful conduct, the Consent Order would specifically award Victims the following: – A declaration by the Court that it is wrong to apply the United States tax code to any tax-exempt applicant or entity based solely on such entity’s name, any lawful positions it espouses on any issues, or its associations or perceived associations with a particular political movement, position or viewpoint; – A declaration by the Court that any action or inaction taken by the IRS must be applied evenhandedly and not based solely on a tax-exempt applicant or entity’s name, political viewpoint, or associations or perceived associations with a particular political movement, position or viewpoint; and – A declaration by the Court that discrimination on the basis of political viewpoint in administering the United States tax code violates fundamental First Amendment rights.
Disparate treatment of taxpayers based solely on the taxpayers’ names, any lawful positions the taxpayers espouse on any issues, or the taxpayers’ associations or perceived associations with a particular political movement, position or viewpoint is unlawful. In the Order, the IRS has also agreed that (unless expressly required by law) certain actions against the Victims– i.e. the sharing, dissemination, or other use of information unnecessarily obtained by the IRS during the determinations process (such as donor names, the names of volunteers, political affiliations of an organization’s officers, etc.) – would be unlawful. In addition, the IRS promises not to take any retaliatory action against our clients for exposing the targeting scheme. Finally, and of crucial significance, the IRS admits it targeted persons and groups based on their viewpoints (i.e., “policy positions”) and that such viewpoint discrimination violates fundamental First Amendment rights. This is the first time the IRS has admitted that its targeting scheme was not just “inappropriate” – as TIGTA found – but, as alleged, blatantly unconstitutional. To ensure consistency and uniformity within the agency’s operations going forward, the IRS is required, pursuant to the Order, to inform all employees within the Exempt Organizations Division, as well as the Commissioners and Deputy Commissioners within other divisions, of the Order’s terms. This Order not only validates allegations about their treatment at the hands of the corrupt Obama-era IRS but also provides important assurances to the American public that the agency understands its obligation to refrain from further such discriminatory conduct. As Attorney General Sessions acknowledged in this regard, “[t]here is no excuse for [the IRS’s] conduct,” as it is “without question” that the First Amendment prohibits the conduct that occurred here, i.e., subjecting American citizens to disparate treatment “based solely on their viewpoint or ideology.” Sessions further confirmed his Department’s commitment to ensuring that the “abuse of power” in which the IRS engaged here “will not be tolerated.” It is impossible to overstate the importance of this victory.
This marks a years-long fight for justice in defense of the constitutional rights of the public. This is an extraordinary victory against abuse of power and corruption. It sends a powerful warning to the deep state bureaucracy that it will not be allowed to violate the Constitution and manipulate the IRS, SSA and other agencies in order to silence and shut down those who speak out about political corruption crimes. In the wake of Wisconsin Watchdog’s investigation into SSA staff allegations of incompetence, misconduct, and retaliation in Social Security disability appeals offices, several employees have taken their complaints to a Senate committee led by Wisconsin Sen. Ron Johnson.
An official with knowledge of the complaints said the Senate Homeland Security and Governmental Affairs Committee, chaired by the Oshkosh Republican, has received emails and other contacts from “certain people” inside the Social Security Administration’s Office of Disability Adjudication and Review. The initial complaints came from an employee inside the Milwaukee office following Wisconsin Watchdog’s opening investigative report that found some claimants waiting more than 1,000 days for an appeals decision on their disability benefits claim. Following Wednesday’s story of a whistle-blower in the Madison ODAR office, the committee has received more specific complaints about retaliation against employees, the source said. Committee staff members sent the latest Watchdog piece to SSA administrators hoping they will “cooperate,” the source said. To date, the agency has been less than cooperative. “This is an ongoing process, and they are not always as forthcoming as we’d like them to be,” the source said. “Hopefully with your continued reporting, this is an issue they can’t duck.” A Senate committee member said officials there are working with the Office of Special Counsel on “multiple whistle-blower retaliation claims.” The committee continues to request information from the SSA. The whistle-blower in the Madison office claims management retaliated against her after she was called to testify in a misconduct case.
The incident involved “inappropriate behavior” by an administrative law judge, she said. “They are so corrupt. It’s absolutely horrible,” said the woman, a lead case technician in the Madison Office of Disability Adjudication and Review. She spoke on condition of anonymity, fearing more retribution from her supervisors. While she said recounting her particular experiences will more than likely betray her identity anyway, the ODAR case worker insisted she has had enough. “I’m at point where they don’t care about me, I don’t see why I’m protecting them. This is my last resort,” she said. “I want to do my work without fear of retaliation.” She said she has contacted the Senate committee. “I forwarded my information to them and I got an email back from them. See these reports:
-
WSJ: 131 Federal Judges Broke Law by Hearing Cases Where They Had Financial Interest...
https://www.wsj.com/articles/hidden-interest-judges-financial-conflicts-graphic-11632834079
-
They said people are coming out of the woodwork with their complaints (about ODAR) following your story,” the whistle-blower said. Ronald Klym, a long-time senior legal assistant in the Milwaukee ODAR office, alleges they has been retaliated against by supervisors for going public with his charges of incompetence and misconduct in the agency. The federal employee, who has worked for SSA for 16 years, provided Wisconsin Watchdog with documents showing extremely long wait times for claimants appealing their denied applications for benefits. Doug Nguyen, SSA regional spokesman, in a previous story said the agency acknowledges that Milwaukee ODAR has a “high average processing time for disability appeal hearings, and we are working to address the issue.” Beyond the delays is what Klym calls the “shell game,” the wholesale transferring of cases to other parts of the country by administrators to make the Milwaukee office’s numbers look better than they are. The Madison office whistle-blower confirmed Klym’s allegations, saying at one point she saw 2,000 cases from the Milwaukee office handed off to the Oak Brook operation. There are over 10,000 SSA disability manipulation charges against SSA executives and staff.
HARM #9: DEFENDANTS USED BLACKLISTING AGAINST PLAINTIFF:
ie: The U.S. Stops Silicon Valley’s ‘No Poaching’ Deals. . . a …
![]() https://www.aol.com › 2010 › 09 › 26 › doj-stops-silicon-valleys-no-poaching-deals-a-few-years-t
https://www.aol.com › 2010 › 09 › 26 › doj-stops-silicon-valleys-no-poaching-deals-a-few-years-t
DOJ Stops Silicon Valley’s ‘No Poaching’ Deals. … But anyone on the ground in Silicon Valley knows that a full-blown war for talent is under way, with checkbooks blazin.
-
Government officials and tech oligarchs contacted members of the National Venture Capital association (NVCA) and created national “black-lists” to blockade Victims from receiving investor funding. This was also confirmed in a widely published disclosure by Tesla Motors Daryl Siry and in published testimony. If Silicon Valley political campaign finance oligarchs black-list you (see the “AngelGate” Scandal and the “High Tech No Poaching Class Action Lawsuit” cases) you will never get investor funding again.
HARM #10: DEFENDANTS ORDERED FOIA OBFUSCATION OF PLAINTIFF’S FOIA AND STILL HAVE NOT RESPONDED TO MANY FOR YEARS BECAUSE THEY SHAME DEFENDANTS:
Federal FOIA requests were hidden, frozen, stone-walled, delayed, lied about and only partially responded to in order to seek to hide information and run cover-ups. In once instance, even though GOVT FOIA staff had the requested FOIA files in their top desk drawers, they delayed handing the FOIA copies over for nearly a decade in order to run a cover-up.
HARM #11: DEFENDANTS ENGAGED IN ARBITRARY DEADLINE MANIPULATION:
Crony state and federal officials play an endless game of Catch-22 by arbitrarily determining that deadlines had passed that they, the government officials, had stonewalled and obfuscated applications for, in order to force these deadlines that they set, to appear to be missed.
HARM #12: POLITICAL POISONING & TOXIC EXPOSURE BY DEFENDANTS HARMED PLAINTIFF:
Victims were found to be strangely poisoned, not unlike the Alexander Litvenko case, The Salisbury Case and hundreds of other political poisoning cases. Heavy metals and toxic materials were found right after Victims work with The U.S. Government weapons and energy facilities. Many wonder if Victims was intentionally exposed to toxins in retribution for their testimony. The federal MSDS documents clearly show that a number of Victims were exposed to deadly compounds and radiations, via GOVT, without being provided with proper HazMat suits which GOVT officials knew were required. Victims was awarded an exceptional number of issued patents on the energy technologies they had developed for the Dept of Energy. 3rd Party outside legal valuation experts appriased the value of these patents at over $200,000.000.00. The patents, clearly visible in full detail, on the US Patent office website, list many of the chemicals and compounds Victims was working with without adequate hazmat resources of Sandia, Argonne or other National Labs safety oversight.
HARM #13: WORKPLACE SABOTAGE AND OBSTRUCTION OF PLAINTIFFS RIGHT TO WORK:
Victims contacts at ARTECH and KAISER PERMANENTE were called, and faxed, and ordered to fire target Victims from their places of employment, in the middle of the day, with no notice, as a retribution tactic.
HARM #14: MEDIA ASSASSINATION PROGRAMS WERE CONTRACTED BY DEFENDANTS TO HARM PLAINTIFF:
On orders from Obama White House officials Google, YouTube, Gawker Media and Gizmodo Media produced attack articles. Google locked these contrived attack articles from the Nicholas Guido Denton tabloid empire on the top line, of the front page of all Google searches for a decade in front of 7.5 billion people, around the world. This attack-type uses over $40 million dollars in server farms, production costs and internet rigging. The forensic data acquired from tracking some of these attacks proves that Google rigged these attacks against Victims on the internet and that all of Google’s “impressions” are manually controlled by Google’s executives who are also the main financiers and policy directors of the Obama Administration. This data was provided to the European Union for it’s ongoing prosecution of Google’s political manipulation of public perceptions. Hired attackers Nicholas Guido Denton, John Herman, Adrian Covert, Ian Fette, Patrick George, Gabrielle Darbyshire and John Cook have been referred to the FBI for surveillance, tracking and interview relative to the command, control and compensation for those attacks.
HARM #15: COMMERCIAL EMPLOYMENT DATABASE POISONING AND RED-FLAGGING OF PLAINTIFFS HR DATABASE REFERENCES WERE CREATED TO HARM PLAINTIFF’S INCOME POTENTIAL:
Victims HR and employment records, on Taleo, Palantir and EVERY recruiting and hiring database, was embedded with negative keywords and “flags” in order to prevent the Victims from ever gaining future employment.
HARM #16: ATTEMPTS ON THE LIVES OF WHISTLE-BLOWERS BY DEFENDANTS WERE MEANT TO FRIGHTEN PLAINTIFF:
Gary D. Conley, Seth Rich, Rajeev Motwani who Victims knew, and many other whistle-blowers in these matters, turned up dead under strange circumstances. Victims has received ongoing death threats for his help to federal investigations in the larger organized crime investigation relative to this matter. See the list of over 120 dead victims, lower down in this document, 1/3 of whom worked with Victims and were threatened in advance of their deaths.
HARM #17: DEFENDANTS ENGAGED IN REVENUE BLOCKADES AND INTERNET INCOME RE-DIRECTION TO MINIMIZE PLAINTIFF RESOURCES SO HE COULD NOT FIGHT BACK:
Paypal, and other on-line payments for on-line sales by Victims are de-platformed, delayed, hidden, or re-directed in order to terminate income potential for target who competed with the attackers interests and holdings. This further denied Victims income. As a test, Victims built an online store with hundreds of thousands of products and marketed it globally. Trackers, placed by Victims technicians, on servers, discovered that Paypal and an outside “Virgina-based system” were DNS and payment re-directed all traffic away from the store so that Victims received no traffic and no income. In DNS redirection, “website spoofing” sends target Victims websites to dead ends where no sales orders or customer inquiries actually get back to the target. These internet revenue activity manipulations are conducted using outside covert servers operated by the attackers and revealed in the Snowden Leaks. All commercial storefronts and on-line sales attempts by target Victims, had their sites hidden, or search engine de-linked by a massively resourced facility located in Virginia, Texas or Palo Alto, California in order to terminate revenue potentials for the Victims.
HARM #18: DEFENDANTS USED THE TROLL FARM DEPLOYMENTS AGAINST PLAINTIFF THAT THEY USE AGAINST PRESIDENTIAL OPPOSITION CANDIDATES:
Contracted trolls, shills, botnets and synth-blog deployments are deployed to place defamatory statements and disinformation about Victims in front of 7.5 billion people around the world on the internet in order to seek to damage their federal testimony credibility by a massively resourced facility. Some of these troll farms were uncovered in Russia, Ukraine, Israel and Brazil. Renown author Farrow writes about this technique in his book: “Catch And Kill”. FUSION GPS, BLACK CUBE and MEDIA MATTERS Brand, Reputation and Credibiity “KILL” CONTRACTS were executed by Defendants targeting Victims. Campaign finance dirty tricks contractors were hired by campaign financiers to attack the friends and family members of the target Victims in order to create low morale for the target Victims psyche and motivation. The Fusion GPS Scandal implicates Gawker and Gizmodo Media In Pay-To-Publish Scheme. A court filing from the U.S. district court for DC shows that Fusion GPS paid several journalist to run hit jobs on political adversaries and was paid by a media organization. All of those players were attackers hired to attack Victims. FBI interviews can verify this.
HARM #19: MANUAL SEARCH ENGINE LOCK-IN ATTACKS WERE CONTRACTED FROM GOOGLE AND YOUTUBE, BY DEFENDANTS, TO HARM PLAINTIFF:
In one case covert political partner: Google, transferred large sums of cash to dirty tricks contractors and then manually locked the media portion of the attacks into the top lines of the top pages of all Google searches globally, for years, with hidden embedded codes in the links and web-pages which multiplied the attacks on Victims by many magnitudes.
HARM #20: THE U.S. PATENT OFFICE MANIPULATION WAS USED TO BLOCKADE REVENUE FROM PLAINTIFF’S INVENTIONS:
Facebook and Google executives sit on the boards and run The United States Patent Office. That fact alone says it all. For details see https://www.usinventor.org
-
Covert Cartel financier: Google, placed Google’s lawyer: Michelle Lee, in charge of the U.S. Patent Office and she, in turn, stacked all of the U.S. Patent Office IPR and ALICE review boards and offices with Google-supporting employees in order to rig the U.S. Patent Office to protect Google from being prosecuted for the vast patent thefts that Google engages in. Google has hundreds of patent lawsuits for technology theft and a number of those lawsuits refer to Google’s operations as “Racketeering”, “Monopolistic Cartel” and “Government Coup-like” behaviors. Thousands of articles and investigations detail the fact that Google, “essentially” ran the Obama White House and provided over 80% of the key White House staff. A conflict-of-interest unlike any in American history. Google’s investors personally told Victims they would “kill him”. Google and the Obama Administration were “the same entity”. Victims testified in the review that got Michelle Lee terminated and uncovered a tactical political and social warfare group inside Google who were financed by Federal and State funds. For additional proof, SEE THE VIDEO at: The_Battle_to_Save_Inventing.m4v
Silicon Valley has taken over the U.S. Patent Office with lobbyists and influence payments. Per Randy Landreneau, the President the U.S. Inventor guild: “ Independence Day is that special time when we Americans remember and celebrate our country’s freedom. While it may mean different things to many people, suffice to say, it is the reason we are Free, we have Liberty. Founder, writer, statesman and inventor Benjamin Franklin wrote, “On Historical occasions, Questions of Right and Wrong, Justice and Injustice, will naturally arise.” Here, on this honored day, we take a quick look at Invention and our Independence. Towards the beginning of the Declaration of Independence, whose principal author was our eventual third president, Thomas Jefferson, the very purpose of our Founders’ quest was established. It is stated: “We hold these truths to be self-evident, that all men are created equal, that they are endowed by their Creator with certain unalienable Rights, that among these are Life, Liberty and the pursuit of Happiness.” These were men and women of incredible vision, of intense courage, and they succeeded in accomplishing their seemingly insurmountable task, rising up and defeating perhaps the most powerful global Empire of the time, Great Britain. The United States of America eventually became the beacon of hope and individual freedom around the world. People from virtually every land came to this country to seek the American Dream, which ideals include individual and property rights, religious freedom, liberty, equality and the opportunity for upward mobility, achieved through dedication and hard work. One of the reasons America became the world leader in nearly all categories is due, in no small part, to how our Founders recognized and encouraged invention and innovation. They understood what builders, creators and designers could mean to a small, fledgling country with such a noble purpose. After declaring our independence and fighting a long and bloody war to establish it, our Founders gathered once again in Philadelphia for the Constitutional Convention to form a government that would embody those ideals embodied in our Declaration of Independence. The Father of our Constitution and eventual fourth President, James Madison wrote, in Federalist 43 (January 23, 1788): “A power ‘to promote the progress of science and useful arts, by securing, for a limited time, to authors and inventors, the exclusive right to their respective writings and discoveries.’ “The utility of this power will scarcely be questioned. The copyright of authors has been solemnly adjudged, in Great Britain, to be a right of common law. The right to useful inventions seems with equal reason to belong to the inventors. The public good fully coincides in both cases with the claims of individuals. The States cannot separately make effectual provisions for either of the cases, and most of them have anticipated the decision of this point, by laws passed at the instance of Congress.” Thus, within our U.S. Constitution is that short item, located in Article I Section 8 as Clause 8: “To promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries.” That clause is, in reality, a significant and powerful part of the American Dream, allowing people from all walks of life who have a bright and useful idea to capitalize on their innovations and creations. For more than two centuries that which our Founders established for inventors and patent holders held true, for the most part. However, the biggest blow to true Independence for Inventors came with passage of the America Invents Act of 2011 (AIA). Due to ambiguous language and loopholes in that piece of legislation, multinational conglomerates and Big Tech have all but wiped out what our Founders had set up, which they hoped would endure – patent holder property rights. When any form of poor legislation is passed and enacted we are reminded of what Samuel Adams, Sons of Liberty founder and a leader of the Boston Tea Party, said; “The grand end of civil government, from the very nature of its institution, is for the support, protection, and defense of those very rights; the principal of which, as is before observed, are Life, Liberty, and Property.”
Indeed, Jefferson states it quite succinctly, “Our legislators are not sufficiently apprized of the rightful limits of their power; that their true office is to declare and enforce only our natural rights and duties, and to take none of them from us.” Madison adds to that, “A Government is instituted to protect property of every sort…This being the end of government, that alone is a just government, which impartially secures to every man, whatever is his own.” As we celebrate Independence Day, and all that our Founders provided for our great country, we at US Inventor are working to correct the wrongs and injustices that have befallen inventors, particularly since the AIA was enacted, by revitalizing the spirit of our Declaration of Independence (“…Life, Liberty and the pursuit of Happiness.”) through restoration of patent rights and protection as guaranteed in Article I Section 8 Clause 8 of our United States Constitution (“securing, for a limited time, to … inventors, the exclusive right to their respective … discoveries.”). We will not rest until the rights of inventors have been restored. We’re gaining ground, but our enemies are powerful. We need your help in forwarding our cause and becoming involved when it matters. This isn’t just for us, it’s for our children, our grandchildren, and the future existence of the American Dream.”
Silcon Valley oligarchs have spent billions of dollars to put their people inside the United States Patent Office and to manipulate patent rulings in order to harm WITNESS and his peers for the purposes of: 1.) cheating instead of competing by stealing technologies and not paying for them and, 2.) operating reprisal, vendetta, retaliation campaigns against competitors and political enemies. Victims was awarded an exceptional number of issued patents on the energy technologies they had developed for the Dept of Energy. 3rd Party outside legal valuation experts appriased the value of these patents at over $200,000.000.00. By it’s actions, The U.S. Government made Victims’s patents unusuable for monetization by causing black-listing of those patents with NVCA investors and by using online trolls to make the marketing for those patents close off. Victims demands that the U.S. Government now purchase ALL of Victims’s patents at fair market value to partially offset his loss.
HARM #21: HONEY-TRAPS WERE PLACED ON SOCIAL MEDA SITES BY DEFENDANTS SPY OPERATIVES TO HARM PLAINTIFF:
“Honeytraps” and moles were employed by the attackers. In this tactic, people who covertly worked for the attackers were employed to approach the “target” in order to spy on and misdirect the subject. Match.com and other dating sites are owned by famous politicians and election campaign financier involved with Jeffrey Epstein and those sites were used to source girls for Epstein and Honey-traps to lure political adversaries.
HARM #22: A FAKE NEWS TABLOID EMPIRE WAS CREATED JUST FOR DEFAMATION ATTACKS, BY DEFENDANTS, AND USED TO HARM PLAINTIFF:
Gawker Media, Gizmodo Media, Snopes, SPLC and other hired media assassins were retained to produce “hatchet job” character assassination articles about Victims. Then those articles were faxed, mailed and emailed to Kaiser Permanente and investors with a note saying: “You don’t want to have anything to do with this person, do you..?” in order to get Victims fired from their job and get Victims loans or financing pulled. The attackers use their round one attack media, that they authored, to create a round two second wave attack designed to end Victims life status via economic warfare. All of the other attack victims received between $100,000.00 to $75,000,000.00 but Victims received ZERO DOLLARS because the Judge was friends with the Defendants.
HARM #23: HOUSING BLOCKADES WERE DEPLOYED BY DEFENDANTS TO HARM PLAINTIFF:
Mortgage and rental applications had red flags added to them in databases to prevent the targets from getting homes or apartments. HUD applications were manipulated or stalled from 2007 to today, as reprisal.
HARM #24: HACKING OF PLAINTIFFS DEVICES OCCURRED ON ORDERS OF DEFENDANTS:
Krebs On Security, Wired, Ars Technica, The Wall Street Journal and most major IT publications have reported that hundreds of spy “back-doors” have been found on every Intel, AMD, Apple, Xfinity, Cisco, Microsoft, Juniper Networks motherboard, chip-set and hardware component set. This means that the attackers used a “key” code can open any of Victims computer, server, router, cloud-network or other network connected device and read every file, photo, video, your calendar and email on devices at any time from any location on Earth. This has been widely reported on by Glenn Greenwald, Edward Snowden, Scahill, Cheryl K of CBS News and others. Victims was hacked at least 10 times. In a number of instances, people, who Victims had been communicating with online, were mysteriously contacted by a third party who sent them the Gizmodo attack article or phoned them with warnings to avoid Victims. These kinds of Man-In-The-Middle interceptions would only have been possible from hacking and MITM surveillance tactics.
HARM #25: TECH INDUSTRY BLACK-LIST COORDINATION AGAINST PLAINTIFF HAD COMMAND-AND-CONTROL OUT OF DEFENDANTS OFFICES:
McCarthy-Era “Black-lists” were created and employed against target Victims who competed with Obama Administration executives and their campaign financiers to prevent them from getting funding and future employment. This White House process is known as “RatFucking”, a tactic that is documented in a variety of published reports and on Wikipedia. Using Gust, Google Docs, Dropbox and secret meetings, a black-list has been maintained to attack Victims for whistle-blowing. Victims has named specific individuals to this court and demanded that the Court request the FBI 302 reports on those individuals. Additional, Victims demands the FINCEN financial mapping records for those Defendant parties. That data, cross referenced in the XKEYSCORE database, provides indisputable, fully incriminating, follow-the-money evidence about every single party mentioned in this complaint.
HARM #26: HUD AND USDA MORTGAGE RIGHTS BLOCKADES TO HARM PLAINTIFF HOUSING IN REPRISAL AS DIRECTED BY DEFENDANTS VIA THEIR ‘DIRTY TRICKS’ TEAM:
The housing rights of Victims were stalled in reprisal. Public records show that tens of thousands of other Victims were moved ahead of Victims even though Victims validation metrics exceeded those of almost every other Victims. Victims was “black-listed”.
-
Additional ‘dirty tricks’ efforts were used per:
https://www.justice-integrity.org/634-intelligence-agencies-use-social-media-for-dirty-tricks-propaganda-new-report -
https://www.salon.com/2011/02/11/threats_against_glenn_greenwald_wikileaks/
-
https://www.theguardian.com/commentisfree/2013/jun/24/surveillance-us-national-security
-
http://federal-report.com/public/The_Political_Reprisal_Vendetta_Playbook.pdf
-
https://www.cia.gov/library/readingroom/docs/CIA-RDP89-01258R000100010002-4.pdf
-
…and thousands of additional reports proving the attacker assertions.
Victims is aware of the FBI procedure of the filing of FBI ‘302’ Reports on subjects.
Victims has, on multiple occasions, via the DC and SFO FBI offices, requested that the FBI interview, observe and track the attackers and confirm the command and control communications authority authorizing, managing and financing their attacks and the paths of compensation of those attacks. The FBI has had the full capacity and resources to easily confirm who ordered and operated the attacks on Victims via an interview and investigation of the Defendants hired attackers, specifically Nicholas Guido Denton, John Herrman, Gabrial Darbyshire, Patrick George, Jay Carney, Robert Gibbs, Adrian Covert, Eric Schmidt, Larry Page, Perkins Coie, John Cook, Elon Musk, The Secretary of Energy Jennifer Granholm, et. al; and those other parties listed within the main complaint..
The FBI ‘302’ reports on those attackers is hereby requested, and a request for the Court to demand those reports is hereby requested for review by all parties concerned.
(G) Court ordered back payments from SSA from 2007 to today because public officials ordered blockade of Victims’s SSDI payments as political reprisal for whistle-blowing in 2007 as proven by Inspector General and attached Exhibits:
Victims hereby places a plea before the Court for the Court to order the Social Security Administration to pay Victims back payments from SSA for SSDI from 2007 to today because, as proven in the Master Complaint, public officials, including White House staff and California Senators with intelligence agency access to government ‘dirty tricks’ teams, ordered the blockade of Victims’s SSDI payments as political reprisal for whistle-blowing in 2007 as proven by Inspector General and attached Exhibits in the Master Complaint. Some SSA officials now work for the charged Defendants. This illicit federal reprisal circumvention of Victims’s income cost him his house and all many of the damages listed, in detail, in the Master Complaint. It has been proven, in the evidence, that Senator’s Pelosi, Harris, Reid, Feinstein, and other senior public officials regularly order hacking, data manipulation and de-funding of political whistle-blowers. Dianne Feinstein’s staffer: Daniel Jones, is world known as the ‘CIA Master of Dirty Tricks’. In fact, Victims and his peers, previously won federal lawsuits, as detailed in the Master Complaint, proving that, “government agencies infected by corruption use their resources to put reprisal hit-jobs on citizens”. Any Senate aide can hack or manipulate SSA, DOE, HUD and other agency decision files within minutes and order ANY citizen to have their funds cut-off with a single phone call. That happened in this case, as Victims, and federal evidence has sworn, certified and verified as to the veracity of such dirty tricks operations within the Government. Senator’s staff and family cohabited with Victims and revealed such tactics.