A massive set of documents and internal reports being collected by Senator Ron Johnson, along with Jim Jordan, Trey Gowdy and their associates, reveals a shocking abuse of the Democratic process by “The Silicon Valley Political Collusion Cartel”. “Some of these tech oligarchs deserve prison”, they say!
Google, Facebook, Netflix, Linkedin, Twitter and the NVCA (National Venture Capital Association aligned with IN-Q-TEL) election-colluded to put Obama and Biden In the White House And Then Get Stock Market Kick Backs
First, they colluded to attack and destroy political and business competitors with global digital character assassination attacks.
- Jonathan Turley: “Fool Me Once . . . ” Why The Public Is Not Buying The Latest Media Campaign Against Twitter…
- Julie Kelly: Obama-Biden Government In Exile Ran Hunter Laptop Suppression Operation…
- Calls For Investigations Grow Over Katie Hobbs’ Alleged Use Of Twitter Censorship, 1A Issues…
- Comedy Hosts Think Twitter Censoring Hunter Story Is About Nude Photos…
- Deposition Reveals Fauci’s Interesting Connection To Twitter…
- White House Dismisses Hunter Biden Laptop ‘Twitter Files’ As ‘Distraction’…
- Miranda Devine: FBI Warned Twitter During ‘Weekly’ Meetings Of Hunter Biden ‘Hack-And-Leak Operation’ Before Censoring The NY Post…
- Propaganda Czar: Soros Bankrolls 253 Groups To Influence Global Media
Every Time We Shave Billions Of Dollars Off Of The Bad Guys Stock Market Valuations: We All Win!
Our Single Most Deadly Weapon Is: THE TRUTH!
Help expose the employee abuse, hookers, tax evasion, female sextortion, character assassination attacks by Black Cube and Fusion GPS, sex cults, cheating and other illicit deeds of these dirty politicians and their Big Tech oligarch financiers!
Put dirty Google, Facebook, Tesla, Linkedin, Kleiner Perkins, Greylock, Netflix, Twitter and Their Silicon Valley Corruption Cartel OUT OF BUSINESS!
Someone has to say it: Elon Musk has lied for 27 years about his credentials. He does not have a BS in Physics, or any technical field. Did not get into a PhD program. Dropped out in 1995 & was illegal. Later, investors quietly arranged a diploma – but not in science.
1/ pic.twitter.com/ziuOMblwLJ
— capitolhunters (@capitolhunters) November 17, 2022
Hunter Biden laptop whistleblower says he’s ‘not surprised’ the NYTimes and other liberal media have failed to cover Elon Musk’s ‘Twitter Files’ – because they are in thrall to Biden’s White House
John Paul Mac Isaac delivered the comment to DailyMail.com in an interview Sunday, two days after Musk published a trove of emails that looked to show Twitter execs attempting to suppress reporting on the story in the run up to the 2020 election – at the behest of the Biden campaign. The barrage of tweets , tauntingly titled the ‘Twitter Files’, saw the site’s new CEO accuse his predecessors of engaging in collusion with Biden’s team – publishing internal emails from the company that supported those claims. At the time, The Times refused to report on the scandal, calling the claims ‘unsubstantiated’ – a stance it has since maintained even after’s Musk’s massive evidence dump. On Saturday, Musk blasted paper for its refusal to cover the ongoing firestorm, branding it an ‘unregistered lobbying firm for far-left politicians.’ Now, 45-year-old Mac Isaac, the owner of the since-shuttered Delaware Mac Shop where an ‘inebriated’ Hunter brought the laptop in 2019, says the paper’s decision to abstain from filing a story is likely ‘its master’s bidding’ – with the master being the Biden Administration.
- Leaked Email Alleges Arizona Gov-Elect Katie Hobbs, Twitter Employees Colluded To Censor ‘Election Related Misinformation’…
- Miranda Devine: FBI Warned Twitter During ‘Weekly’ Meetings Of Hunter Biden ‘Hack-And-Leak Operation’ Before Censoring The NY Post…
- New York Times Falsely Claims Hunter Biden Laptop ‘Stolen’…
- Former Head Of Twitter’s ‘Trust And Safety’ Team Whines About ‘Dangerous’ Babylon Bee Joke…
- Musk Vows ‘More Smoking Guns’ To Come In Twitter Exposé…
- Censorship By Surrogate: Why Musk’s Document Dump Could Be A Game Changer…
- Nicholas Sandmann Asks Musk To Release ‘Hidden’ Twitter Files On Death Threats Permitted Against Him…
- Victor Davis Hanson: How Corrupt Is A Corrupt Media?
- Margot Cleveland: If A Legitimate Free Press Existed, The Twitter Files Wouldn’t
- Reversal Of Long-Standing Policy Keeps Key Docs On Hunter Biden’s Business From Congress
Meta’s own oversight board slams Facebook’s ‘unequal’ program that gives celebs, business partners and politicians preferential treatment
The dictionary defines a “Character Assassination Attack”, ie: https://en.wikipedia.org/wiki/Character_assassination , as “…The state-sponsored destruction of reputations, fostered by political propaganda and cultural mechanisms, can have more far-reaching consequences. One of the earliest signs of a society’s compliance to loosening the reins on the perpetration of crimes (and even massacres) with total impunity is when a government favors or directly encourages a campaign aimed at destroying the dignity and reputation of its adversaries, and the public accepts its allegations without question. The mobilisation toward ruining the reputation of adversaries is the prelude to the mobilisation of violence in order to annihilate them. Generally, official dehumanisation has preceded the physical assault of the victims.[8]…”
DON’T read all about it! America’s inbred, partisan media are Biden lapdogs – and their refusal to report the Twittergate scandal is all the proof you need, writes RICH MINITER
MINITER: It’s time for a media reckoning. On Monday, the White House blew off bombshell revelations of a direct pipeline from DC insiders to social media censors at Twitter. Press Secretary Karine Jean-Pierre called the report ‘old news’ and a ‘distraction.’ That’s easy to say when mainstream reporters don’t ask any new questions. But there’s plenty to investigate if they only did their jobs. These are the same journalists, who shrugged off the Hunter Biden laptop story in 2020, admitted that was a mistake just a few months ago, and are now turning a blind eye to another scandal involving – none other than – Hunter’s laptop. With these guys, it’s always Groundhog Day, except they never have the Bill Murray epiphany at the end of the movie.
The organized use of “The Silicon Valley Cartel” RICO and Antitrust violating racketeering organization to operate a global charactar assassination attack on anybody they opposed, put them in control of public perceptions. The media group of the Cartel is widely known to consist of Google, Alphabet, YouTube, Gizmodo/Gawker Media, Black Cube, Twitter and the like, which are COVERTLY owned by the government figures involved in these corruption matters. To use an 8 Billion person global media Silicon Valley attack engine is to end someone’s life, to permanently destroy them. The White House and the Department of Energy have been exposed in investigations doing this thousands of times!
It’s All Making Sense – Elon Musk Has No Idea What He Purchased with Jack’s Magic Coffee Shop…
… And if he does, the outlook is worse.
According to both the Senate Intelligence Committee (SSCI), via Chairman Mark Warner, and the House Intelligence Committee (HPSCI) via Mike Turner, the Chinese social media platform TikTok represents a “national security risk” to the United States. South Dakota Governor Kristi Noem, soon to be the vice-presidential candidate for the DeSantis-Noem 2024 ticket, has also called TikTok a national security threat and banned it in the state. Now, think about that carefully.
What is it about a social media app allowing short video sharing that would constitute a national security risk? The answer is not about dog and cat videos, or dancing diatribes or funny, weird or goofy content; nor is the national security risk attached to any data of the app users or content providers. The national security risk is found in the ability to influence public opinion that is not under the control of the United States government, or more specifically the Dept of Homeland Security (DHS).
The need for control is a reaction to fear. TikTok, as a social media platform, is not considered a national security threat because the Chinese government can control it. TikTok is considered a national security threat because the United States government does not control it.
For several years CTH has been outlining the relationship between DHS and social media. Currently, the headlines are filled with stories about Twitter and revelations of censorship and government influence coming from the purchase of the platform by Elon Musk. I promise you things are not what they seem.
Let me put some context to the dynamic that will hopefully clarify what is going on, and perhaps the context will help explain what you are seeing and what you are not seeing as this unfolds. There are going to be a lot of citations to fill in the details and understanding the modern Fourth Branch of Government is critical. The bigger picture also explains why SSCI Chairman Mark Warner said “people will die” if the seized Trump Mar-a-Lago documents become public.
♦ Elevator Speech: Twitter is to the U.S. government as TikTok is to China. The overarching dynamic is the need to control public perceptions and opinions. DHS has been in ever increasing control of Twitter since the public-private partnership was formed in 2011/2012. Jack Dorsey lost control and became owner emeritus; arguably, Elon Musk has no idea (you’ll see proof toward the end).
 To explain the background activity of Twitter in a way that readers could understand, I used the metaphor of Twitter as Jack’s Magic Coffee Shop.
To explain the background activity of Twitter in a way that readers could understand, I used the metaphor of Twitter as Jack’s Magic Coffee Shop.
…”The metaphorical Jack had a great idea, open a coffee shop where the beverages were free and use internal advertising as the income subsidy to operate the business. Crowds came for the free coffee, comfy couches, fellowship, conversation and enjoyment.
It didn’t matter where Jack got the coffee, how he paid for it, or didn’t, or what product advertising the customers would be exposed to while there. Few people thought about such things. Curiously, it didn’t matter what size the crowd was; in the backroom of Jack’s Coffee Shop they were able to generate massive amounts of never-ending free coffee at extreme scales.
Over time, using the justification of parking lot capacity and township regulations, not everyone would be able to park and enter. Guards were placed at the entrance to pre-screen customers. Some were denied. A debate began.”…
Here’s what happened….
In/around 2011 and 2012 the U.S. Government, Obama administration and the U.S. State Dept., came into Jack’s Coffee Shop and asked him for help.
The govt officials needed to deliver massive amounts of coffee to their allies in Egypt, Libya and the middle east to support the Arab Spring party. Jack told the officials he was willing to help but didn’t have the capacity to deliver on that scale. The officials told Jack not to worry, they would handle that aspect – he just needed to agree to the partnership and let them utilize his business. Jack agreed.
[Note, the timing here is not accidental. The operational agreement happened at the same time DHS was fine tuning the domestic surveillance systems to monitor social media platforms and target political opposition. See The Fourth Branch.]
Over the next several weeks, months and eventually years, Jack watched as hundreds of new employees flooded into the business to facilitate the rapid expansion. Along with a myriad of new faces, new equipment was delivered and soon Jack found himself looking at heavy industrial equipment erecting large buildings in the back lots of the property. Coffee urns were replaced with massive industrial coffee delivery systems that far exceeded anything Jack ever imagined.
Business was booming, but slowly Jack realized he had lost control. Jack was riding a dragon.
As the years progressed, thousands of new employees moved into the offices of the new buildings and massive pipelines were producing incredible scales of coffee. Jack noted offices of the United Nations Human Rights Commission were now creating unique blends of coffee for international distribution, and the European Commission had an entire suite of specially trained coffee production engineers creating alternate combinations and flavors.
By 2018 Jack had essentially become an “owner emeritus,” his name was on the shingle, but the day-to-day operation of Jack’s Magic Coffee Shop had turned into an industrial park complex.
Jack saw his personal wealth attached to the success of the business, but operationally his only responsibility was traveling to symposiums and venues where he would stand on stage and wax philosophically about the future of a coffee delivery organization he no longer controlled. Day-to-day operations were now controlled by experts in the scale of massive industrial coffee. Those experts came from the Dept of Homeland Security.
[The Intercept] – […] Behind closed doors, and through pressure on private platforms, the U.S. government has used its power to try to shape online discourse. According to meeting minutes and other records appended to a lawsuit filed by Missouri Attorney General Eric Schmitt, a Republican who is also running for Senate, discussions have ranged from the scale and scope of government intervention in online discourse to the mechanics of streamlining takedown requests for false or intentionally misleading information.
“Platforms have got to get comfortable with gov’t. It’s really interesting how hesitant they remain,” Microsoft executive Matt Masterson, a former DHS official, texted Jen Easterly, a DHS director, in February.
In a March meeting, Laura Dehmlow, an FBI official, warned that the threat of subversive information on social media could undermine support for the U.S. government. Dehmlow, according to notes of the discussion attended by senior executives from Twitter and JPMorgan Chase, stressed that “we need a media infrastructure that is held accountable.” (read more)
 To streamline the operational efficiencies as the industrial coffee system grew, direct portals between the Washington DC government offices and Jack’s Magic Coffee shop were created. Officials no longer needed to travel to the location of Jack’s Coffee Shop in order to operate the valves, mixers, grinders and systems to generate the scale of blends being produced.
To streamline the operational efficiencies as the industrial coffee system grew, direct portals between the Washington DC government offices and Jack’s Magic Coffee shop were created. Officials no longer needed to travel to the location of Jack’s Coffee Shop in order to operate the valves, mixers, grinders and systems to generate the scale of blends being produced.
Experts could now use direct portals to the facility to operate the coffee production systems remotely, with a limited number of specially trained (FBI) coffee engineers doing the laborious tasks and maintenance at the facility.
The badges were intimidating to Jack who went to sleep every night under the realization he no longer had any clue about how the coffee shop communication business was operating.
[…] The extent to which the DHS initiatives affect Americans’ daily social feeds is unclear. During the 2020 election, the government flagged numerous posts as suspicious, many of which were then taken down, documents cited in the Missouri attorney general’s lawsuit disclosed. And a 2021 report by the Election Integrity Partnership at Stanford University found that of nearly 4,800 flagged items, technology platforms took action on 35 percent — either removing, labeling, or soft-blocking speech, meaning the users were only able to view content after bypassing a warning screen. The research was done “in consultation with CISA,” the Cybersecurity and Infrastructure Security Agency.
Prior to the 2020 election, tech companies including Twitter, Facebook, Reddit, Discord, Wikipedia, Microsoft, LinkedIn, and Verizon Media met on a monthly basis with the FBI, CISA, and other government representatives. According to NBC News, the meetings were part of an initiative, still ongoing, between the private sector and government to discuss how firms would handle misinformation during the election. (keep reading)
After several years of increasing distance from the Coffee Shop operation he initially started, eventually Jack decided it was silly to own an industrial coffee delivery system that he didn’t control. So, Jack decided to sell his shingle to someone else.
Enter, Elon Musk.
Billionaire Elon Musk, a man intimately familiar with large industrial systems and government, had been watching the disgruntled visitors to Jack’s Coffee Shop who were no longer permitted to enter. Musk saw an inequity between the amount of coffee that was available, and the scarcity of the coffee amid a community blacklisted by the operational executives and managers of the shop.
With expressions of both interest and fellowship, Mr. Elon Musk told Mr. Jack Dorsey he would take ownership of Jack’s Magic Coffee Shop and remove any discriminatory guards that were now controlling permitted entry. Jack had no aversion to Elon and eventually a deal was brokered.
After the transfer of sale was complete, Mr. Musk fired many of the guards and then set about checking the payroll to identify which group of shop employees were actually involved in the generation of coffee, and which employees were involved in promotion of the industrial coffee delivery system that were no longer needed.
Within this process Elon Musk begins to discover the complex nature of what, at least at the surface, appeared to be an uncomplicated coffee shop. Why is there a 500-room glass walled office building on the backside of the coffee shop? What is going on in that building that has anything to do with selling coffee?
If you’ve read this far, you might think my metaphor is a little over the top. Perhaps you thought that when I originally started saying there was much more to Jack’s Magic Coffee Shop a long time ago.
Well, thankfully, someone of reasonably intelligent curiosity finally asked Elon Musk the right question about this direct portal from DHS into the coffee shop. How Mr. Musk replied might surprise you. You see, the Jack’s Magic Coffee Shop metaphor is evidenced in the Musk response.
Twitter owner Elon Musk has no idea what the DHS portal into the coffee shop is for. WATCH:
.
To put it in brutally honest terms, The United States Dept of Homeland Security is the operating system running in the background of Twitter.
You can debate whether Elon Musk honestly didn’t know all this before purchasing Twitter from his good friend Jack Dorsey, and/or what the scenario of owner/operator motive actually is. Decide for yourself.
For me, I feel confident that all of the conflicting and odd datapoints only reconcile in one direction. DHS, via CISA, controls Twitter.
Wittingly or unwittingly (you decide) Elon Musk is now the face of that govt controlled enterprise.
If you concur with my researched assessment, then what you see being released by Elon Musk in the Twitter Files is actually a filtered outcome as a result of this new ownership dynamic.
Put simply, DHS stakeholders, to include the DOJ, FBI and Office of the Director of National Intelligence (ODNI), are mitigating any consequential public exposure of their domestic surveillance activity by controlling and feeding Mr. Musk selected information about their prior Twitter operations.
If TikTok is a national security threat, then TikTok is to Beijing as Twitter is to Washington DC.
The larger objective of U.S. involvement in social media has always been monitoring and surveillance of the public conversation, and then ultimately controlling and influencing public opinion.
.
Resources:
Large Numbers of FBI Agents Work Inside Twitter
Govt Structured Cloud Computing is Social Media operating System
Tech Platforms Connected to DHS Portals
Examples of Govt Influence of Social Media Content
[…] “Intelligence agencies backed new startups designed to monitor the vast flow of information across social networks to better understand emerging narratives and risks.” [HERE]
Understanding Jack’s Magic Coffee Shop
Some online articles list an example set of the Silicon Valley Cartel members in a manner such as this:
“THE SILICON VALLEY CARTEL MEMBERS
The Worst Ones – Rev 2.2
You would be shocked to learn how many people are killed, every day, for less than $50.00. ISIS and the Taliban will saw your head off for just an ideology. If people would commit murder over that small an amount of money, imagine what they would do to control the trillions of dollars of money that is always moving through the stock market.These are the people that will stop at nothing for power, mansions, hookers, private jets and greed!
### THE BRIBED INSIDER TRADING POLITICIANS – Tracked via financial records and email leaks to quid pro quo:
– Aneesh Chopra – White House Tech Exec
– Arnold Schwarzenegger – Governor (Accused of political bribery and kickbacks; tax evasion, illicit deal organization with Russians and more…)
– Barack Obama – Chicago politician
-Bill Daley – White House strong-arm (Forced to resign)(he is now under investigation)
– Bill Lockyer – Calif State finance head (Under investigation and sex scandal conflicts, charged with corruption by media. Assets and ownerships under investigation)
– Daniel Cohen – DOE Legal counsel who assisted in the Steven Chuscam (Sent packing/fired/forced to resign)
– David Axelrod – White House strategist who helped stage the quid-pro-quo (Sent packing/fired/forced to resign)(he is now under investigation)(accused of political bribery and kickbacks; tax evasion, and more…)
– Hunter Biden
– David Plouffe – White House money packager. Arranged deals between VC campaign Donors (Forced to Resign. Under investigation)
– Debbie Wasserman Schultz
– Denis McDonough – White House adviser
– Dianne Feinstein – California politician
– Eric Holder – Attorney General- DOJ (Forced to resign) (Charged with staff & VC Protections and blockade of FBI and Special Prosecutor deployments in order to run the cover-up)
– Eric Strickland – Head of Auto Safety agency under DOT (Sent packing/fired/forced to resign)(he is now under investigation. Charged with cover-up of Tesla and GM auto dangers he had known about)
– Gabriel Burt
– Harry Reid – Senator- Solar factory guru, Congress lead (Accused of political bribery and kickbacks; tax evasion, and more…Forced out of Congress in shame)
– Hillary Clinton – Dynastic politician
– Jack Lew
– Jay Carney – White House press lead (Forced to resign)
– Jeff Berman – Bryan Cave. Berman, the former delegate counter for President Obama’s 2008 campaign
– Jeff Peck, Peck, Madigan, Jones & Stewart. Aide to then-Sen. JoeBiden (D-Del.) on the Senate Judiciary Committee
– Jeffrey Zients
– Jerry Brown – California politician
– Joe Rhodes – White House shill
– Joe Biden – Politican who created Solyndra funds
– John Podesta – White House adviser
– Jonathan Silver – DOE VC (Sent packing/fired/forced to resign)(he is now under investigation. Shamed in media for epic failures)
– Joshua Wright – FTC
– Kamala Harris– Stock favoritism Insider with her husband
– Katherine Feinstein
– Kathy Zoi
– Ken Alex – Scheme Adviser to Jerry Brown
– Ken Duberstein and Marti Thomas, The Duberstein Group. Duberstein was floated as a candidate for Obama’s chief of staff before the president chose Bill Daley, while Thomas is a Democratic vet who worked in the Clinton Treasury Department.
– Lachlan Seward – Energy Department insider gatekeeper
– Melanie Nutter – Pelosi Top Aide
– Matt Rogers – VC and quid pro quo pass-through conduit
– Megan Smith – U.S. CTO
– Mikey Dickerson
– Nancy Pelosi – California politician
– Robert Gibbs – White press office head
– Steven Chu – Secretary of Energy – The most corrupt in US history
– Todd Park – IT manipulator inside White House
– Plus others to be named…
### THE OLIGARCH FINANCIER/BENEFICIARIES OF THE CRIMES – Tracked via financial records and email leaks to quid pro quo:
– Andy Bechtolsheim – VC- Insider campaign backer (He is now under investigation)(accused of political bribery and kickbacks; tax evasion, and more…)
– Bill Gurley
– Carl Gordon
– Chad Hurley – YouTube
– Cheryl Sandberg – Facebook boss, reports to Larry Summers
– Dave McClure – VC
– David Danielson
– David Drummond – Lawyer/Lobbyist– Google, bribes expert for DC and EU regions (Under investigation. Quail Road, Woodside, CA home bugged)
– David Mott
– David Prend
– David Sacks
– Draper – Fisher – VC firm (Campaign funder who received massive windfalls from Russian mining & tech start-up rigging)
– Elon Musk – CEO – Tesla (He is now under investigation & in multiple lawsuits for fraud)(accused of political bribery and kickbacks; tax evasion, and more…) ( All of his personal assets,investments and portfolio holdings are under investigation )
– Emerson Collective -Steve Jobs wife, has one of the largest and stealthiest election data combines
– Eric Paley
– Eric Schmidt – Owner- Google (He is now under investigation)(accused of political bribery and kickbacks; tax evasion, and more…)
– Gilman Louie – VC, founder on IN-Q-Tel
– Goldman Sachs – Financial packager (Suspected of staging most ofthe TARP/DOE deals for personal gain & insider payouts)
– Greylock Capital – Silicon Valley Insider trading operator (Underi nvestigation)
– Ira Ehrenpreis – VC Campaign backer (He is now underinvestigation)(accused of political bribery and kickbacks; tax evasion, and more…) ( All of his personal assets, investments andportfolio holdings are under investigation)
– Jacque Littlefield – VC, Dead
– James Bronkema – West Coast Money Man for David Rockefeller andFeinstein financier (Dead)
– Jared Cohen – Google boss and international political manipulator
– Wilson Sonsini Partner Club
– Wilson, Sonsini, Goodrich and Rosatti
– Jim Breyer – VC and CIA intermediary
– Joe Lonsdale – VC, famous for rape and abuse scandal and domesticspying via Palantir
– Johanna Shelton – Google Lobbyist
– John Doerr – Owner – Kleiner Perkins. “Godfather” – SiliconValley Cartel (He is now under investigation)(accused of political bribery and kickbacks; tax evasion, and more…)( All of his personalassets, investments and portfolio holdings are under investigation )
– John Lindfors
– Josh Kopelman
– JP Gan
– Keith Rabois -VC
– Ken Howery – VC
– Kleiner Perkins – Campaign funding VC who (Received massivewindfalls from Russian mining & tech start-up rigging. Sued. Under investigation. All assets being tracked )
– Larry Page – Google Boss
– Larry Summers – VC
– Lloyd Craig Blankfein – VC and Sachs boss
– Luke Nosek
– Marc Andreessen -VC
– Mario Rosatti – VC
– Mark Zuckerberg – Facebook Boss
– Martin LaGod -VC Firelake Cap
– Mary Meeker – VC
– Max Levchin -VC
– Mckinsey Consulting – The firm you hire to rig white papers andinsider hires in government positions for the Palo Alto Mafia
– Michael Moritz -VC
– Neerag Agrawal – VC
– Peter Thiel – VC
– Pierre Omidyar– VC
– Raj Gupta – VC, arrested
– Rakesh Saxeena – Canadian in-house arrest, arms dealer, westernpolitical packager
– Ray Lane – VC
– Reid Hoffman – VC and sex.com partner with Gary Kremen, alsomatch.com
– Richard Blum – VC and director/husband of Dianne Feinstein -Finally dead!
– Roelof Botha
– Sanjay Wagle – VC
– Scott Shleiffer
– Sergy Brin – Google boss
– Steve Chen
– Steve Jurvetson – VC embroiled in sex abuse charges
– Steve Rattner – White House car czar, indicted for fraud
– Steve Spinner – Energy Department manipulation expert, Wife wasSolyndra’s lawyer
– Steve Westly – VC
– Ted Schlein – IN-Q-Tel
– Tim Draper – VC
– Tom Perkins – Dead KPCB Palo Alto Mafia founder
– Tom Steyer – VC
– Tomorrow Ventures – Social manipulation group
– Tony Podesta, Podesta Group. The prolific Democratic fundraiser hasseen his firm rocket to the echelons of the top five lobby shops.
– Viktor Vekselberg – Russian business entity
– Vinod Khosla -VC
– Plus others to be named…
### THEIR OPERATIVES AND HIRED MEDIA ASSASSINS – Tracked via financialrecords, quid pro quo perks and email leaks to payola. The people in the two lists, above, hired these people to harm citizens:
– A.J. Delaurio– Defamation-for-sale blogger
– Adam Dachis– Defamation-for-sale blogger
– Adam Weinstein– Defamation-for-sale blogger
– Adrian Covert– Defamation-for-sale blogger
– Adrien Chen– Defamation-for-sale blogger
– Al D’Amato, Park Strategies. The former GOP New York senator hasbeen a big advocate for online gambling as a lobbyist for the Poker Players Alliance.
– Al Mottur and Manuel Ortiz, Brownstein Hyatt Farber Schreck. Motturheads up lobbying operations at the K Street giant. Ortiz, one of Brownstein’s newest hires, is a rising star in Democratic circles.
– Alan Henry– Defamation-for-sale blogger
– Albert Burneko– Defamation-for-sale blogger
– Alex Balk– Defamation-for-sale blogger
– Alexander Pareene– Defamation-for-sale blogger
Alexander Sternhell, Sternhell Group. Previously a Senate Banking Committeestaffer, Sternhell’s two-year-old venture is in the big leagues with clients such as Citigroup Management and PricewaterhouseCoopers.
– Alexandra Philippides– Defamation-for-sale blogger
– Allison Spinner – Wife of Steve Spinner and lawyer at WSGR andSolyndra who helped Feinstein rig the Solyndra cash ((Under investigation. All assets being tracked and terminated.)
– Allison Wentz– Defamation-for-sale blogger
– Andrew Collins– Defamation-for-sale blogger
– Andrew Magary– Defamation-for-sale blogger
– Andrew McCormack
– Andrew Orin– Defamation-for-sale blogger
– Andy Barbour, Smith-Free Group. Smith lobbies for several financialand insurance companies but is best known for his work as the lead Democratic lobbyist for the Financial Services Roundtable.
– Angelica Alzona– Defamation-for-sale blogger
– Anna Merlan– Defamation-for-sale blogger
– Ariana Cohen– Defamation-for-sale blogger
– Ashley Feinberg– Defamation-for-sale blogger
– Ashley Vance – Elon Musk suck-up and Musk hype monger
– Austin Lau
– Ava Gyurina– Defamation-for-sale blogger
– Barry Petchesky– Defamation-for-sale blogger
– Black Cube – An attack service providing hit jobs on competitors
– Brendan I. Koerner– Defamation-for-sale blogger
– Brendan O’Connor– Defamation-for-sale blogger
– Brent Rose– Defamation-for-sale blogger
– Brian Goncher – Deloitte VC intermediary in the stock marketrigging (He is now under investigation)(accused of political bribery and kickbacks; tax evasion, and more…)
Brobeck Law Firm
– Brian Hickey– Defamation-for-sale blogger
– Camila Cabrer– Defamation-for-sale blogger
– Carr & Ferrell – Sony and Facebook’s law firm that helps toblockade inventors
– Choire Sicha– Defamation-for-sale blogger
– Chris Jennings, Jennings Policy Strategies
– Chris Mohney– Defamation-for-sale blogger
– Chuck Brain, Capitol Hill Strategies Inc. Once a Clinton White Houseaide and longtime House Ways and Means Committee staffer
– Civis Analytics – Social manipulation group
– Clover Hope– Defamation-for-sale blogger
– Covington & Burling
– Dan Tate Jr., Capitol Solutions. Tate delivers stellar clientrelations while harnessing 10 years of upper-level Hill and administration experience.
– Daniel Morgan– Defamation-for-sale blogger
– Covington & Burling – corrupt law firm that puts appointees inoffice for VC’s
– David Sandalow
– Diana Moskovitz– Defamation-for-sale blogger
– Doyle Bartlett, Eris Group. Bartlett has years of Capitol Hillexperience and a busy lobbying practice
– Eleanor Shechet– Defamation-for-sale blogger
– Elizabeth Spiers– Defamation-for-sale blogger
– Elizabeth Starkey– Defamation-for-sale blogger
– Emily Gould– Defamation-for-sale blogger
– Emily Herzig– Defamation-for-sale blogger
– Emma Carmichael– Defamation-for-sale blogger
– Erin Ryan– Defamation-for-sale blogger
– Ethan Sommer– Defamation-for-sale blogger
– Eyal Ebel– Defamation-for-sale blogger
– Fred Graefe, Law Offices of Frederick H. Graefe
– Fusion GPS – Defamation and journalist bribery service
– Gabrielle Bluestone– Defamation-for-sale blogger
– Gabrielle Darbyshire– Defamation-for-sale blogger and attackservices director
– Gawker Media – DNC/Clinton/Obama character assassination media tool(In Mid-Termination)
– Georgina K. Faircloth– Defamation-for-sale blogger
– Gerald Cassidy and Gregg Hartley, Cassidy & Associates
– Gizmodo – DNC/Clinton/Obama character assassination media tool (Failing, rapidly decreasing users and increasing fake ad stats disclosures )
– Gregory Howard– Defamation-for-sale blogger
– Hamilton Nolan– Defamation-for-sale blogger
– Hannah Keyser– Defamation-for-sale blogger
– Heather Deitrich– Defamation-for-sale blogger
– Heather Podesta, Heather Podesta + Partners. The former congressionalaide has built a solid lobbying practice and helps fundraise for Democrats with her husband, Tony Podesta
– Hudson Hongo– Defamation-for-sale blogger
– Hugo Schwyzer– Defamation-for-sale blogger
– Hunter Slaton– Defamation-for-sale blogger
– Ian Fette– Defamation-for-sale blogger and Google, Gawker,Jalopnik, Gizmodo media assassin
– Irin Carmon– Defamation-for-sale blogger
– Jalopnik – Online defamation facade political publication. Pretendsto be about cars but is DNC hit job rag
– James Brown Jr – HHS Programming lead in California (Arrested forcorruption)
– James J. Cooke– Defamation-for-sale blogger
– James King– Defamation-for-sale blogger
– Jawed Karim – YouTube
– Jeff Lieberman
– Jennifer Ouellette– Defamation-for-sale blogger
– Jesse Oxfeld– Defamation-for-sale blogger
– Jessica Cohen– Defamation-for-sale blogger
– Jesus Diaz– Defamation-for-sale blogger
– Jillian Schulz– Defamation-for-sale blogger
– Joanna Rothkopf– Defamation-for-sale blogger
– Joel Johnson, The Glover Park Group
– John Cook– Defamation-for-sale blogger and director of mediaassassins group
– John Herrman– Defamation-for-sale blogger
– John Raffaelli, Capitol Counsel
– Jordan Sargent– Defamation-for-sale blogger
– Joseph Keenan Trotter– Defamation-for-sale blogger
– Josh Stein– Defamation-for-sale blogger
– Julia Allison– Defamation-for-sale blogger
– Julianne E. Shepherd– Defamation-for-sale blogger
– Julie Domenick, Multiple Strategies LLC
– Justin Hyde– Defamation-for-sale blogger
– Kate Dries– Defamation-for-sale blogger
– Katharine Trendacosta– Defamation-for-sale blogger
– Katherine Drummond– Defamation-for-sale blogger
– Kelly Stout– Defamation-for-sale blogger
– Kerrie Uthoff– Defamation-for-sale blogger
– Kevin Draper– Defamation-for-sale blogger
– Lacey Donohue– Defamation-for-sale blogger
– Larry O’Brien, OB-C Group
– Lucy Haller– Defamation-for-sale blogger
– Luke Malone– Defamation-for-sale blogger
– Madeleine Davies– Defamation-for-sale blogger
– Madeline Davis– Defamation-for-sale blogger
– Mario Aguilar– Defamation-for-sale blogger
– Mark Isakowitz, Fierce, Isakowitz and Blalock. Isakowitz and his GOPlobby shop scored a coup this year when Apple and Facebook both signed up as clients in a two-week span.
– Mark Kadesh, Kadesh & Associates. Kadesh, once chief of staff toSen. Dianne Feinstein (D-Calif.), has an A-list of California clients
– Matt Hardigree– Defamation-for-sale blogger
– Matt Novak– Defamation-for-sale blogger
– Michael Ballaban– Defamation-for-sale blogger
– Michael Dobbs– Defamation-for-sale blogger
– Michael Spinelli– Defamation-for-sale blogger
– Morrison and Foerster
– Neal Ungerleider– Defamation-for-sale blogger
– Nicholas Aster– Defamation-for-sale blogger
– Nicholas Guido Denton– Defamation-for-sale blogger and head of theGawker, Gizmodo, Jalopnik sleaze tabloid empire
– Omar Kardoudi– Defamation-for-sale blogger
– Owen Thomas– Defamation-for-sale blogger
– Patrick George– Defamation-for-sale blogger and CharacterAssassination expert
– Patrick Laffoon– Defamation-for-sale blogger
– Patrick Redford– Defamation-for-sale blogger
– Perkins Coie – Campaign conduit law firm
– Rich Juzwiak– Defamation-for-sale blogger
– Richard Blakely– Defamation-for-sale blogger
– Richard Rushfield– Defamation-for-sale blogger
– Robert Finger– Defamation-for-sale blogger
– Robert Sorokanich– Defamation-for-sale blogger
– Rory Waltzer– Defamation-for-sale blogger
– Rosa Golijan– Defamation-for-sale blogger
– Ryan Brown– Defamation-for-sale blogger
– Ryan Goldberg– Defamation-for-sale blogger
– Sam Faulkner Biddle– Defamation-for-sale blogger, Runs a large partof the Anti-GOP blog programs
– Sam Woolley– Defamation-for-sale blogger
– Samar Kalaf– Defamation-for-sale blogger
– Sarah Ramey– Defamation-for-sale blogger
– Shannon Marie Donnelly– Defamation-for-sale blogger
– Shep McAllister– Defamation-for-sale blogger
– Sophie Kleeman– Defamation-for-sale blogger
– Stephen Totilo– Defamation-for-sale blogger
– Steve Elmendorf and Jimmy Ryan, Elmendorf | Ryan. A former aide toex-House Democratic Leader Richard Gephardt (Mo.), Elmendorf brought in Ryan to help expand the Senate ties of his firm.
– Steve McBee, McBee Strategic. A former aide to Rep. Norm Dicks(D-Wash.), McBee has seen his lobby firm take off.
– Steve Perry and Andy Wright, Dutko Grayling. Perry and Wright man theroster for one of the top 20 lobby shops in Washington.
– Tamar Winberg– Defamation-for-sale blogger
– Taryn Schweitzer– Defamation-for-sale blogger
– Taylor McKnight– Defamation-for-sale blogger
– The Groundwork– Social manipulation group
– Thomas Jolly, Jolly/Rissler. Jolly is founding chairman of theWashington Caucus, a group that hosts dinners with lawmakers, and a mainstay among lobbyists.
– Thorin Klosowski– Defamation-for-sale blogger
– Tim Marchman– Defamation-for-sale blogger
– Timothy Burke– Defamation-for-sale blogger
– Tobey Grumet Segal– Defamation-for-sale blogger
– Tom Ley– Defamation-for-sale blogger
– Tom Scocca– Defamation-for-sale blogger
– Veronica de Souza– Defamation-for-sale blogger
– Wes Siler– Defamation-for-sale blogger
– William Haisley– Defamation-for-sale blogger
– William Turton– Defamation-for-sale blogger
– Plus others to be named…
### THEIR CORPORATE STOCK MANIPULATION FRONT FACADES- Tracked viafinancial records and email leaks to RICO, Anti-trust and Money Laundering violations:
– Abound Solar – Criminally corrupt crony campaign finance frontoperation. (Terminated)
– Alphabet – Privacy abuse, spy-on-the-public, Fake News electionrigger, Clinton/DNC scheme financier (Under Federal and EU investigation)
– Facebook/Meta – Privacy abuse, spy-on-the-public, Fake News electionrigger, Clinton/DNC scheme financier ( Failing, rapidly decreasing users and increasing fake ad stats disclosures )
– Fisker – Criminally corrupt crony campaign finance front operation.(Terminated)
– Google, Inc. – Data harvesting company(Ran media attacks, stockmarket pump and dump PR hype and character assassinations)(accused of political bribery and kickbacks; tax evasion, and more…) (chargedby EU, and most nations, with multiple abuses of the public. Has totally lost the trust of the public. Revenue loss increasinggeometrically.)
– In-Q-Tel, Inc. – CIA off-shoot associated with Eric Schmidt,Google, Elon Musk and the Cartel leaders. Ran “hit-jobs” on Silicon Valley VC adversaries and reporters (Sued, underinvestigation, exposed in multiple documentaries, under investigation for Cocaine trafficking. Removal of charity status demanded)
– Ivanpah Solar – Criminally corrupt crony Google campaign financefront operation. (In failure mode)
– Linkedin – Election manipulation networking site
– Netflix – Propaganda Site that also conduits jobs as politicalrevolving door payola to politicians
– Solyndra Solar Company – FBI-raided corrupt Clean Tech company
– SpaceX – Elon Musk company that Obama gave part of NASA to inexchange for campaign conduits
– Tesla Motors – Car Company that conduits money to campaigns
– The NVCA – National Venture Capital Association collusion group
-Plus others to be named…
Any issues re: culpability can be easily resolved in meetings with theFBI, FINCEN, The SEC, The IRS, The FTC, ICIJ.ORG and open Congressional hearings! Never was the term: “Follow The Money”more appropriate than for these people! Why are these people not yet arrested for election manipulation, RICO and Anti-trust violations,money laundering, bribery and other illicit deeds? Who is protecting them? Who is telling the police not to act? This list also serves asa demand for investigation and prosecution of these individuals who conspired to engage in these illicit acts. This is not the completelist….”
While opposition entities Pooh Pooh the assertion, FINCEN and top forensic investigators, and their XKEY-SCORE type databases provethat they are all financially and politically closely aligned. Their media group set out to “CONTROL THE NEWS AND INFORMAION PERSPECTIVES THAT ARE VIEWED BY OVER 8 BILLION PEOPLE…”, per Google executives and, indeed, that is what they accomplished. The head of the world reknown publication: Psychology Today, Robert Epstein: (born June 19, 1953) is an American psychologist, professor, author, and journalist. He was awarded a Ph.D. in psychology by Harvard University in 1981, was editor in chief of Psychology Today, and has held positions at several universities including Boston University, University of California, San Diego, and Harvard University. He is also the founder and director emeritus of the Cambridge Center for Behavioral Studies in Concord, MA. In 2012, he founded the American Institute for Behavioral Research and Technology (AIBRT), a nonprofit organization thatconducts research to promote the well-being and functioning of people worldwide. Epstein has been a commentator for National Public Radio‘s Marketplace, the Voice of America, and Disney Online. His popular writings have appeared in Reader’s Digest, The Washington Post, The Sunday Times (London), Good Housekeeping, The New York Times, Parenting, and other magazines and newspapers. Epstein is a public figure in theworld of psychology.[1][2][3][4] He has published over 350 articles and 15 books. His onlinecompetency tests are taken by more than a million people a year.[5] . He has testified before Congress to facts herein.
In fact Every one of the insiders who did get government funding got it in the exact same size and order as their covert politicalcampaign funding and stock market bribes to the deciders. Chamath Palihapitiya and other Silicon Valley insiders have now exposed thefact that Greylock, Kleiner, etc. are just a VC Ponzi Scheme! in this whole mess. Musk used crooked Senators to get his funds. ThoseSenators and government agency bosses were financed by, friends with, sleeping with, dating the staff of, holding stock market assets in,promised a revolving door job or government service contracts from, partying with, personal friends with, photographed at private eventswith, making profits by consulting for, exchanging emails with, business associates of or directed by; one of those businessadversaries, or the Senators and politicians that those business adversaries pay campaign finances to, or supply political searchengine manipulation services to. Elon Musk is notorious for getting Department of Energy money by bribing public officials and placinghis friends: Steven Chu, Matt Rogers, Steve Westly, Steve Spinner’s ‘special friend’, etc. on the staff of the Department of Energy andin the White House. We have FBI-class records, financial tracking, emails, stock market relay records and other forensic data thatproves it. We can swear, warrant, certify and prove these assertions in front of Congress in a live Congressional hearing or Civil Jurytrial, given non-compromised legal backing.
While these CIA, FSB and NSA tactics are pooh poohed by media shills as “Hollywood Fare”, The White House is well documented, in Congressional investigations, doing these very things. The CIA’s Democrat led: IN-Q-TEL organization has indisputably funded and advised all of these entities.
Opposition has argued that these “fantastic” assertions are “here-say”and that no citizen “should think that any government official would ever do anything unethical;..”
That argument might have worked…UNTIL THIS WEEKEND:
A MASSIVE TROVE OF HARD PHYSICAL EVIDENCE SHOWING THE WHITEHOUSE AND TOP GOVERNMENT OFFICIALS USING TWITTER, GOOGLE, FACEBOOK, YOUTUBE, GAWKER AND GIZMODO MEDIA TO ATTACK OTHERS AND RIG ELECTIONS HAS BEGUN TO BE RELEASED! NEW CONGRESSIONAL INVESTIGATION HAVE BEEN LAUNCHED BECAUSEOF THESE DISCLOSURES. PLAINTIFF IS A WITNESS IN THESE INVESTIGATIONS. MUCH MORE EVIDENCE WILL BE LEAKED THIS MONTH BY MAJORNEWS OUTLETS.
A SMALL SAMPLE OF THIS BREAKING NEWS FOLLOWS:
This weekend, THE SILICON VALLEY CARTEL LEAKS BEGAN. Part 1 shows the emails between Twitter and White House officials coordinating the rigging of national elections and character assassinations on competitors and political enemies. ICIJ.ORG journalists and European reports say there will be over ten leak sets showing Twitter, Google, Netflix, Facebook, YouTube, Linkedin and other Silicon Valley Big Tech mobsters communicating with The White House to manipulate news, information and elections. Stay tuned. Read the attached book if you want to help accelerate the take-down, and bankrupting of, The Silicon Valley Racketeering Cartel. Multiple federal investigations have now been launched. News Samples: https://never-give.in/shocker-twitter-google-facebook-youtube-instagram-all-found-to-have-manipulated-national-elections/
WE KILLED SILICON VALLEY AND WE LOVE THE LAST GASPS!
Join The Team Ending This Kind Of Political Corruption
AAAA USING SOCIAL MEDIA SITES TO SPY ON CITIZENS
AAAA THE SAN FRANCISCO CRONY CORRUPTION NIGHTMARE
AAAA THE PATENT THEFTS BY THE BIG TECH OLIGARCHS
AAAA THE NETFLIX NEGLIGENCE AND IDEOLOGY PROPAGANDA SCHEMES
AAAA THE LITHIUM BATTERY POLITICAL PROFITEERING LIES
AAAA THE HOUSING CRISIS WAS CREATED BY CORPORATE LOBBYISTS
AAAA THE ELON MUSK AND TESLA MOTORS FRAUD, STOCK RIGGING, BRIBERY AND SAFETY INVESTIGATIONS
AAAA THE CORRUPT SENATORS OWNED BY BIG TECH
AAAA THE CORRUPTION OF FACEBOOK AKA META
AAAA THE AWFUL TRUTH ABOUT GOOGLE
AAAA THE AFGHANISTAN RARE EARTH MINING CORRUPTION
AAAA STANFORD UNIVERSITY HAS A CULTURE OF CORRUPTION AND TEACHES THAT THINKING TO STUDENTS
AAAA SONY PICTURES POLITICAL AND EXECUTIVE CORRUPTION
AAAA SILICON VALLEYS COORDINATED MASS MEDIA MANIPULATION OF THE PUBLIC
AAAA POLITICAL KILL ORDERS AND STATE-SPONSORED CHARACTER ASSASSINATIONS
AAAA FIGHTING POLITICAL CORRUPTION
AAAA ADVANCED TECHNOLOGY VEHICLE MANUFACTURING LOAN CORRUPTION
TWITTER ADMITS THAT IT HAS ALWAYS SPIED ON YOU EVEN WHEN YOU ARE NOT ON TWITTER
HIRED TO KILL – THE CYBER ASSASSINS HIRED BY WHITE HOUSE STAFF
– A Report To Federal Investigators And The Public
A group of companies and individuals sell cyber assassination services designedto end people’s lives. When we spoke with California Senators Speier, Pelosi, Feinstein and Harris; their staff said that theyrefuse to regulate such activities because it would violate “Freedom Of Speech”. We also noticed that THEY hire these cyber assassins to attack political enemies, reporters, competitors andwhistle-blowers. We asked about that conflict-of-interest. They did not respond… We then asked: “If it is OK for these people to engage in the attacks listed herein, (see the ATTACKERS PLAY-BOOK list; Below), are you OK with them doing all of these things to YOU for the next 5 years?”
They did not respond…
The attackers, (ie: The White House and Government agency staff) set-up atentacular, layered, covert payment and command/control system in order to operate and disguise their attacks on citizens, reporters,whistle-blowers and competitors. The problem, for these “Bad Guys” in the post-2000 era, is that nothing can be hidden, any longer, because digital technology monitorseverything. It is said that “DEEDS DONE IN THE DARK, ALWAYS COME TO LIGHT” and, in this case, that turns out to be quite accurate.
“Have you ever wondered who’s pulling the strings?”
Hired cyber assassins hide in the shadows at the tip of the spear ofpolitical and market monopoly wars. … Anything they touch is a weapon. They are government-trained to deceive, persuade, change,influence, and inspire others to their ideology. They come in many forms: from fat gamer neck-beards to attractive business suitcorporate brunettes. They are everywhere that money buys vengeance.
They spy on you to manipulate your politics, ideology and intentions andto report you to bill collectors, tax colletors, investigators and political parties. The spy, on, and harm you and your company if youspeak out about corruption and if your product is better than their bosses product. They help peole who cheat rather than compete.
Google, Netflix, YouTube, Facebook, etc. exist to mass manipulate populationsand run stock market scams for their sociopath owners. Even these big companies covertly sell their services as cyber assassins to certainbuyers for huge amounts of government wire transfers. From INSIDE Google, our team saw Google manipulate the entire internet to hype upLarry Page’s “boyfriend’: Elon Musk and Tesla, which Google execs owned a portion of, while sabotaging Tesla’s competitors.Google illicitly and illegally timed these manipulations with stock market pump-and-dump efforts to exploit insider trading. That is afelony violation of RICO, Antitrust and other laws. Every single thing that Google does is contrived to harm a competitor, apolitician, an employee whistle-blower or some other business adversary.
There are no “bugs”, “operator errors”, “server anomalies” orother media “accidents” at Google, Facebook, Youtube, Twitter, et al

Everything Google, etc, does is contrived, at a psychological warfare kind oflevel, to change a social perception. Google must show its software to FBI, SEC, FTC and our search engine optimisation experts to provethat they did not engage in these crimes. The fact is: We can prove they did the crimes and FBI experts can help us prove it! Google isknown as the “Nazi’s of the Internet”.
In a case unfolding in Britain over whether Google wrongly demoted pricecomparison rival Foundem from its search results in favour of paid-for adverts, Google must now decide which it values more: thealgorithms that rank its search results, or its stance that manually fiddling with those results to promote its own paid-for products overrivals’ sites doesn’t break competition laws.
The integrity of Google’s ranking processes relies upon all webmastersor website owners having the same degree of access to information about Google’s ranking… This will no longer be the case ifinformation of this kind is made available to some individuals offering commercial services to assist companies to improve theirSearch ranking.
Google is a criminal operation. It’s executives have been publicly exposedas participants in horrific sex scandals, money laundering, political bribery and racism. It is time for the bought and paid shillpoliticians to stop protecting them! – Google spies on competitors and steals their technology – Google runs tens of millions ofdollars of defamation attacks against competitors – Google hides all media and news coverage for competitors of Larry Page’sboyfriend: Elon Musk – Google lies to the public about what they really do with the public’s data –
Google promotes illegal immigration in order to get cheap labor and controlvotes – Google runs VC funding back-lists against start-ups that are competitive – Google bribes thousands of politicians – Googleis a criminal RICO-violating monopoly – Google rigs the stock market with Flash-boy, Pump/Dump and Microblast SEC violatingcomputer tricks – Google pays bribes to politicians in Google and YouTube stock – Google manipulates who gets to see what web-sites,globally, for competitor black-lists – Google has a “no poaching” Silicon Valley jobs blacklist –
Google bosses sexually abuse women and young boys – Google bosses run sextrafficking operations in the Epstein and NXVIUM cults – Google bosses control the NVCA financing cartel over start-ups – Googlehas placed the majority of the corporate staff in at least one White House – Google controls national elections for anti-competitivepurposes – The company “Polyhop”, in the HOUSE OF CARDS tv show, does all the crimes that Google actually does in reality –Google’s law firms, like Wilson Sonsini, are corrupt conduits for payola and political conduit-relays –
Google bribes some politicians with revolving door jobs – Google isprimarily responsible for destroying the Bay Area Housing opportunities – Google runs DDoS attacks on competitors bymassively crawling their sites – Google boss Andy Rubin runs a sex slave farm according to his own family – Google boss Eric Schmidtwas a philandering sex-penthouse owner according to vast news articles – Google executives hire so many hookers that one of them,Mr. Hayes, was killed by his hooker –
Google executives sexually abuse so many women that the women staff ofGoogle walked out one day – In the 2009 White House, you could not swing a cat without hitting a Google insider – Google has paidcovert bribes, PAC funds, real estate and search rigging payola to every CA Senator – Google has paid bribes, through its lobbyfronts, to halt FBI, SEC, FEC and FTC investigations of Google crimes – Google was funded by the CIA, via In-Q-Tel, a so called “501 c3charity” which was caught with tons of cocaine – Google gets millions of dollars of taxpayer cash for spying on Americans insidethe USA – Google’s map service was a spy system paid for by taxpayers money that Google now profits off of –
Nancy Pelosi and Dianne Feinstein have promised to “protect” Googlebecause their families profit off Google stocks – Payment receipts prove that Google and Gawker/Gizmodo exchanged cash and staff forCharacter Assassination attacks – Google VC’s and bosses have spent $30M+ rigging the U.S. Patent Office to protect Google and harmGoogle competitors –
Google bribed it’s lawyer into position as head of the U.S. Patent officein order to have her protect Google – To rig insider stock trades, Google hides negative Tesla stories and pumps positive Tesla storieson “push days” – Google and Elon Musk Co-own, co-invest and co-market stocks covertly while running anti-trust schemes – Googlerarely likes, or hires, black employees per federal and news media investigations – Google hired most of the Washington, DC K Streetlobby firms and told them to “do what ever they could” – The film: “Miss Sloane” depicts only 2% of the illicit lobbyingtactics Google employs daily –
Demands for an FTC and FBI raid of Google, for criminal activity, securitieslaw and election felonies have been filed – Google’s David Drummond had his Woodside, CA Quail Road house bugged revealing sexand financial misdeeds – Google, and it’s Cartel (Alphabet, Youtube, and hundreds of other shell-company facades) are a criminalorganization engaged in felony-class crimes. Google’s bosses bribe politicians, regulators and law enforcement officials to hold offprosecution.
At Google: Kent Walker, Andy Rubin, Larry Page, Eric Schmidt, SergyBrin, Jared Cohen, Yasmin Green, David Drummond and Ian Fette are so enmeshed in sex scandals, election manipulation, and White Housebribes that it is hard to comprehend how they can get any legitimate work done. Google executives came from most of the fraternity housesinvolved in the college rape scandals. Google sells covert character assassination services to politicians and fellow oligarchs.Youtube/Google/Alphabet/Deep State are all the same entity. They conspire to hide news about their corruption and they control most ofthe internet.
There are hundreds of millions of people in America. The same 120 of themare all involved in operating the same crimes and corruption including: the Sony Pictures corruption; the Afghanistan rare earthmine scandals operated through The Energy Department political slush fund that involves the lithium battery cover-ups (headed by ElonMusk); the Big Tech Brotopia rape, sex trafficking, bribery, exclusionism, racism and misogyny issues they were taught at StanfordUniversity; The Facebook – Meta – Google – Alphabet – Netflix, et al, coordinated news manipulation and domestic spyingthat they engage in; the hiring of Fusion GPS – Black Cube – Gizmodo/Gawker assassins; the destruction of the housing market bytheir mass real estate manipulations; patent theft and industrial espionage; and the bribery of almost every politician all the way upto the Oval Office.
So, while the categories covered in this investigation may seem diverse.They are connected through an enterprise of criminality and illicit, coordinated operations. We list, by name, the 120 most complicitindividuals organizing these crimes, in the evidence documents already submitted to the FBI, FINCEN, DOJ, FTC, SEC, FEC, Congress,InterPol and other authorities. Digital financial tracking of those persons and all of their family members should be assumed to havebeen under way for some time. Wire-taps and device taps of those persons and all of their family members should be assumed to havebeen under way for some time.
Twitter, Splunk, Google, Facebook, Netflix, YouTube and the Silicon Valleyinternet Cartel serve you custom manipulated content by automatically creating a covert digital dossier on you reflecting the contentconsumption preferences they have spied on about you. They continually evolve their dossier on you in order to steer you towardstheir ideology and their Democrat political party. At these companies, “data mining”, “machine learning” and “AI”means computerized propaganda processing for certain political entities. They began hiring off-shore people (because they would workso cheap) but most of those people turned out to be Muslim. This created conflicts with the entire southern part of the United States(which is anti-Muslim) because those workers steered content to pro-Muslim positions.
Their spy dossier on you uses abstract content-specific features of theconsumed content, such as categories, topic models, and entities, which they automatically extract using natural language processing bycomparing every word you use to a giant computer library of what those words might mean about your psychology. So it’s like you aregetting “mind-raped” without any penis use. Their assessment of what your words might mean is based on what rich, white male,$200K/year, DNC-promoting programmers think they might mean. Their computers scale and expand their tools with algorithmic softwarecreated by those politically and socially biased frat white boys that wrote the code. It is all biased as hell. They never hire blacks orwomen in system creation roles so everything these companies do only supports rich white soyboy snowflake type gamer thinking.
Because the White House told them to spy on billions of people, even forthese web giants, it is impractical to store the entire dynamic history of a user’s interaction features. They, thus, out of greed,use algorithms that selectively decay information in order to generalize users and populations. To them, you are just a generalizeddata point, like cattle on a ranch, to be harvested and fed upon by Silicon Valley.
These cyber assassin attackers are often fired CIA staffers and disgruntledand naive news bloggers from Gawker, Buzzfeed, etc. They conduct influence activities to target psychological vulnerabilities andcreate or intensify fissures, confusion, and doubt in adversaries.
They use all available means of dissemination – from sensitive and hightech, to low-tech, to no-tech, and methods from overt, to clandestine, to deception.
These PSYOPS attackers are trained to confuse, mislead, redirect, andoccupy your mind with thoughts that a targeted candidate, reporter or whistle-blower is “bad” or to be shunned.
They are ghosts in the machine, watching and warping everything to trickyou into hating someone that might tell the truth about them, or their bosses,
A site known as The Vigilant Citizen suggests believes their intent may be darker, and possibly related to the occult. These allusions to magic are notmerely figurative. PSYOPS extensively researched occult and supernatural phenomenons such as ESP (extra-sensory perception) andremote viewing,” Vigilant Citizen reports. “There was always a ‘magical’, supernatural element to PSYOPS. The 4th PsychologicalOperations Group has a Task & Purpose report which is a master class in psychological warfare. A big part of the attackers psychologicaloperations is creating persuasive fake news media. One wonders who Americans should be most afraid of: foreign powers or their own government.
Law enforcement agencies, intelligence agencies and private investigatorshave identified these attackers complicit in this matter.
A lifetime analysis of the published work, payments and who paid them,often via covert payment routes, conducted at an FBI-level of research, reveals some pretty interesting illicit and overt connections between all of them. For example, the following chart shows a typical money-laundering, taxand government survellance evasion system for one of the attackers:

Figure 1: ONE OF A VAST NETWORK OF MONEY LAUNDERING, TAX EVASION, KILL SERVICE OPS NETWORKS

Figure 2: THERE ARE THOUSANDS OF BANKING RECORDS THAT SHOW THAT GAWKER AND GOOGLE TRADED CASH FOR KILLS

Figure 3: THERE ARE TENS OF THOUSANDS OF BANK, SEC, FINCEN, IRS AND OTHER RECORDS PROVING THE CASH MOVING THROUGH THESE EFFORTS WAS HUGE AND CAME FROM GOVERNMENT CONTACTS

Figure 4: THIS SHOWS THAT ONE OF THE ATTACKERS CLEARLY SELLS HIS SERVICES ON FACEBOOK AS AN “ASSASSIN”

Figure 5: ONE ATTACKER PAYMENT SCHEME HAD OVER 980 PASS POINTS VIA SHELLS, TRUSTS AND MONEY DROPS
While the thousands of graphics, that forensic investigators have acquired, provide a good visual tale of the crimes, corruptionand attacks, the following text description of an FBI-level investigation is even more shocking. It is important to keep in mind that U.S. Government officials faxed,emailed, U.S. mailed and delivered the character assassination materials to their target’s employers, family, friends, associates, fiance and others, in orderto maximize the harm to the targeted citizens.
All of the attackers got paid cash, stock perks, job advancements and other compensation.Here are some of the ways they hid the compensation transfers:
– “Based on publicly available FEC records, repeatedly throughout the 2016presidential campaign, HVF would purportedly transfer funds to its constituent political committees, which included between 34 and 40state parties,” the complaint states. “On the very same day each of these transfers supposedly occurred, or occasionally the very nextday, every single one of those state parties purportedly contributed all of those funds to the DNC.”
– In New York City, No. 9 East 71st Street is a well-known sex mansionused to pay off politicians and operatives via sex favors
– On Nov. 8, Craig B. Hulet, a well known and highly respected analyst ongovernment policy, terrorism, and international relations, spoke on Coast to Coast AM regarding the growing scandal involvinga lawsuitagainst the Federal Reserve, major banks, and many members of the Bush andObama administrations. During his one hour interview, Hulet offered the assessment that many members of the Obama cabinet,including Hillary Clinton, Timothy Geithner, and Eric Holder, were resigning their offices dueto their potential roles in the TARP money laundering lawsuit.
– Attorney General Jeff Sessions encouraged the DOJ to reopen the Uranium Onecase. This indictment may be a byproduct of their investigation into the Clinton Foundation and Russia. Fitton doesn’t thinkit’s coincidental that the DOJ under Obama was “hiding this in plain sight from the American people”, and certainly hiding “keyelements” from congress. Then the DOJ under “Jeff Sessions responds by saying we’re going to take another look at this. There’s a new indictment to follow up on the indictment that is already out there, or a conviction… from 2015.” According toFitton, this is a follow-up investigation that started in Little Rock Arkansas. Both the FBI and the Attorney General are lookinginto pay to play allegations on the part of the Clinton Foundation. “One would hope Uranium One is part of it.” He claims therewere tens of millions of dollars that were laundered by the Russians through the Clinton Foundation.
– The Committee to Defend the President, a political action committee,filed its complaint with the FEC on Monday with the allegations that the Hillary Victory Fund (HVF) solicited cash from big-name donors,including Calvin Klein and “Family Guy” creator Seth MacFarlane — money that was allegedly sent through state chapters and back tothe DNC before ending up with the Clinton campaign.
– The FBI and FINCEN found that attacker David Brock, a professional cyber attacker and media assassin, has 7 non-profits, 3 Super PACs, one 527-committee, one LLC, onejoint fundraising committee, and one unregistered solicitor crammed into his office in Washington DC.
Uncovered records expose a constant flow of money between theseorganizations. The Bonner Group, his professional solicitor, works off a commission. Every time money gets passed around, Bonnerreceives a 12.5% cut. It appears that Brock has been passing around donations quite a bit, giving The Bonner Group a handout each time.In 2014, Media Matters for America raised $10,021,188. The Bonner Group was credited for raising these funds. Media Matters paid them a$1,147,882 commission. That same year, Media Matters gave a $930,000 cash grant to David Brock’s Franklin Education Forum, an organization that shares office space with Media Matters. In 2014,the Franklin Education Forum reported $994,000 in total contributions. 93.6% of that total came from Media Matters!Surprisingly, though, the Franklin Education Forum gave full credit to Bonner for raising that money. They paid the fundraiser a$124,250 commission in 2014! As all of these groups exist within Brock’s DC office, it would be difficult for him to claim he had noidea this was going on. The report continues: Furthermore, the New York Times reports that David Brock shares a summer rental in the Hamptons with Mary Pat Bonner, the President of the Bonner Group!
The above quoted sections of investigations are not the exception but,rather, the rule in money-laundering and covert payola to attackers. We have over 200,000.. let me repeat, OVER TWO HUNDRED THOUSAND OTHER EXAMPLES OF THESE ILLICIT PAYMENT SCHEMES TO POLITICAL ANDANTI-COMPETITION ATTACKERS FINANCED, SUPPORTED, ENABLED AND OPERATED BY THE U.S. GOVERNMENT! These payments occer in government offices DAILY! Government officials donot halt these methods, stop stock ownership by politicians, or delay this money laundering because THEY PROFIT FROM IT. That is WRONG,ILLICIT, CRIMINAL and a VIOLATION OF THE BASIC PRECEPTS of AMERICA!
A lifetime analysis of the published work, payments and who paid them,often via covert payment routes, conducted at an FBI-level of research, reveals some pretty interesting illicit and overt connections between all of them.
THE NAMES OF THE ATTACKERS
These are the people that the tech oligarchs, The White House and U.S.Senators hire to end your life if you report their crimes. It should be against the law for these cyber assassination kill services toeven exist, but Congress won’t outlaw them because Senators use them every day. If they can do the things they do, to you, then it must belegal to do the same things back to them. While they spend millions of dollars and get paid millions of dollars to destroy you, theaverage person only has a fraction of that money, if any at all, to fight back with. Since they are hired to destroy you, you have every right to destroy them…as long as you do it legally and in the most creative andinsidious ways possible. In payback for accepting compensation for trying to destroy you and your family, they must be hunted andtracked for the rest of their lives! Criminal referrals and RICO charges appear to have been filed against every party on this list:
-
A.J. Delaurio – Defamation-for-sale blogger
-
Acronym
-
Adam Dachis – Defamation-for-sale blogger
-
Adam Weinstein – Defamation-for-sale blogger
-
Adrian Covert – Defamation-for-sale blogger
-
Adrien Chen – Defamation-for-sale blogger
-
Al Mottur and Manuel Ortiz, Brownstein Hyatt Farber Schreck
-
Alan Henry – Defamation-for-sale blogger
-
Albert Burneko – Defamation-for-sale blogger
-
Alex Balk – Defamation-for-sale blogger
-
Alexander Pareene – Defamation-for-sale blogger
-
Alexandra Philippides – Defamation-for-sale blogger
-
Allison Spinner
-
Allison Wentz – Defamation-for-sale blogger
-
Alphabet – Privacy abuser, spy-on-the-public, Fake News election rigger
-
American Independent Foundation – Attack service
-
American Ledger – Attack service
-
AmpliFire News – News attack media network
-
American Bridge – Spy service and attack service processor
-
American Bridge 21st Century Foundation Group – Experts at separating rich people from their cash to fund attacks
-
Andrew Collins – Defamation-for-sale blogger
-
Andrew Magary – Defamation-for-sale blogger
-
Andrew McCormack
-
Andrew Orin – Defamation-for-sale blogger
-
Andy Barbour, Smith-Free Group
-
Andy Bechtolsheim – VC- Insider campaign backer
-
Aneesh Chopra
-
Angelica Alzona – Defamation-for-sale blogger
-
Anna Merlan – Defamation-for-sale blogger
-
Ariana Cohen – Defamation-for-sale blogger
-
Arnold Schwarzenegger – Outrage media operative
-
Ashley Feinberg – Defamation-for-sale blogger
-
Austin Lau
-
Ava Gyurina – Defamation-for-sale blogger
-
Barack Obama – Chicago politician who hired 70% of the attack services available
-
Barry Petchesky – Defamation-for-sale blogger
-
Bill Daley – White House strong-arm who pushed attack services at White House
-
Bill Gurley
-
Bill Lockyer – Calif State finance head
-
Black Cube – Private Mossad attack service
-
Brendan I. Koerner – Defamation-for-sale blogger
-
Brendan O’Connor – Defamation-for-sale blogger
-
Brent Rose – Defamation-for-sale blogger
-
Brian Goncher – Deloitte VC intermediary that worked Big Tech mafia
-
Brian Hickey – Defamation-for-sale blogger
-
Buzzfeed – Attack service that convinces naive soyboys to write news clips
-
Cambridge Analytica – Attack service, keeps changing name
-
Camila Cabrer – Defamation-for-sale blogger
-
Carl Gordon
-
Cardinal & Pine – Attack service
-
Chad Hurley
-
Cheryl Sandberg – Facebook attack boss, reports to Larry Summers, dates Activision CEO
-
Choire Sicha – Defamation-for-sale blogger
-
Chris Jennings, Jennings Policy Strategies
-
Chris Mohney – Defamation-for-sale blogger
-
Chuck Brain, Capitol Hill Strategies Inc
-
Civis Analytics – Social manipulation attack group
-
Clover Hope – Defamation-for-sale blogger
-
Clearview AI Face Tracking
-
Correct The Record – Attack service
-
Covington & Burling – Policy manipulation & appointee rigging lawyers
-
Courier Newsroom – Attack service
-
Daniel Cohen – DOE Legal maniupulation counsel
-
Daniel Morgan – Defamation-for-sale blogger
-
Daniel Jones – Dianne Feinsteins media “hit man”
-
Dave McClure – VC, Hell magnet
-
David Axelrod – White House attack boss
-
David Brock – Master of character assassination services
-
David Danielson
-
David Drummond – Lawyer/Lobbyist– Google, wife cheater
-
David Matthews – Defamation-for-sale blogger
-
David Mott
-
David Plouffe – White House money packager & election rigger
-
David Prend
-
David Sacks
-
David Sandalow
-
Debbie Wasserman Schultz – Attack politician advisor, election rigger
-
Denis McDonough – White House attack coordinator
-
Diana Moskovitz – Defamation-for-sale blogger
-
Dianne Feinstein – California politician who hired huge numbers of attack services
-
Draper – Fisher – VC firm (Campaign funder who received massive windfalls from Russian mining & tech start-up rigging)
-
Eleanor Shechet – Defamation-for-sale blogger
-
Elizabeth Spiers – Defamation-for-sale blogger
-
Elizabeth Starkey – Defamation-for-sale blogger
-
Elon Musk – Attack boss, has CIA staff and Mercs on payroll to attack others
-
Emerson Collective – Steve Job’s cash deployer for political intrigues
-
Emily Gould – Defamation-for-sale blogger, sounds like an idiot on Jimmel Kimmel interview
-
Emily Herzig – Defamation-for-sale blogger
-
Emma Carmichael – Defamation-for-sale blogger
-
Eric Holder – Attorney General- DOJ, indicted by Congress for contempt, ran cover-ups
-
Eric Paley
-
Eric Schmidt – Owner- Google. Jigsaw Boss, Dr. Strangelove level of sociopathy
-
Erin Ryan – Defamation-for-sale blogger
-
Ethan Sommer – Defamation-for-sale blogger
-
Eyal Ebel – Defamation-for-sale blogger
-
Facebook – Privacy abuse, spy-on-the-public, Fake News election rigger
-
Fusion GPS – Defamation attack and journalist bribery service
-
Gabriel Burt
-
Gabrielle Bluestone – Defamation-for-sale blogger
-
Gabrielle Darbyshire – Defamation-for-sale blogger and attack services director
-
Gawker Media – DNC/Clinton/Obama character assassination media tool
-
Georgina K. Faircloth – Defamation-for-sale blogger
-
Gilman Louie – VC, founder of IN-Q-Tel spy service
-
Gizmodo – DNC/Clinton/Obama character assassination media tool
-
Goldman Sachs – Financial packager (Suspected of staging most of the TARP/DOE deals for personal gain & insider payouts – Elon Musk’s stock manipulation partner
-
Google, Inc. – Data harvesting company(Ran media attacks, stock market pump and dump PR hype and character assassinations – amplifies attacks by the others on this list and locks those attacks at the top of every search result for a fee
-
Gregory Howard – Defamation-for-sale blogger
-
Greylock Capital – Silicon Valley Insider trading operator focused on election manipulation
-
Hamilton Nolan – Defamation-for-sale blogger
-
Hannah Keyser – Defamation-for-sale blogger
-
Heather Deitrich – Defamation-for-sale blogger
-
Heather Podesta, Heather Podesta + Partners
-
Hopewell Fund – Attack service
-
Hudson Hongo – Defamation-for-sale blogger
-
Hugo Schwyzer – Defamation-for-sale blogger
-
Hunter Slaton – Defamation-for-sale blogger
-
Ian Fette – Defamation-for-sale blogger and Google, Gawker, Jalopnik, Gizmodo media assassin
-
In-Q-Tel, Inc. – CIA off-shoot
-
Investing in US
-
Ira Ehrenpreis – VC Campaign backer
-
Irin Carmon – Defamation-for-sale blogger
-
Jalopnik – Online defamation facade political publication. Pretends to be about cars but is hit job rag
-
James Brown Jr – HHS Programming lead in California (Arrested for corruption)
-
James J. Cooke – Defamation-for-sale blogger
-
James King – Defamation-for-sale blogger
-
Jared Cohen – Google boss and international political manipulator
-
Jared Birchell – Elon Musk’s attack dog
-
Jawed Karim
-
JigSaw Operations within the Google Cartel – Attack service
-
Hunter Biden
-
Jay Carney – White House press attack plots coordinator
-
Jeff Berman and David Russell, Bryan Cave
-
Jeff Lieberman
-
Jeff Peck, Peck, Madigan, Jones & Stewart
-
Jeffrey Zients
-
Jennifer Ouellette – Defamation-for-sale blogger
-
Jeremy Stoppelman
-
Jesse Oxfeld – Defamation-for-sale blogger
-
Jessica Cohen – Defamation-for-sale blogger
-
Jesus Diaz – Defamation-for-sale blogger
-
Jillian Schulz – Defamation-for-sale blogger
-
Jim Blanchard and Ilia Rodriguez, DLA Piper
-
Jim Breyer – VC and CIA intermediary
-
Jim Goetz
-
Joanna Rothkopf – Defamation-for-sale blogger
-
Joe Lonsdale – VC, famous for rape and abuse scandal and domestic spying via Palantir
-
Joe Rhodes – White House shill
-
Joel Johnson, The Glover Park Group
-
Johanna Shelton – Google’s White House manipulator
-
John Cook – Defamation-for-sale blogger and director of media assassins group
-
John Doerr – Owner – Kleiner Perkins. Tech Mafia “Godfather”
-
John Herrman – Defamation-for-sale blogger
-
John Lindfors
-
John Podesta – White House attack adviser
-
John Raffaelli, Capitol Counsel
-
Jonathan Silver – DOE VC (Sent packing/fired/forced to resign)
-
Jordan Sargent – Defamation-for-sale blogger
-
Joseph Keenan Trotter – Defamation-for-sale blogger
-
Josh Ackil and Matt Tanielian, Franklin Square Group
-
Josh Kopelman
-
Josh Stein – Defamation-for-sale blogger
-
Joshua Wright
-
JP Gan
-
Julia Allison – Defamation-for-sale blogger
-
Julianne E. Shepherd – Defamation-for-sale blogger
-
Julie Domenick, Multiple Strategies LLC
-
Justin Hyde – Defamation-for-sale blogger
-
Kamala Harris – Defamation-for-sale hiring boss
-
K2 Intelligence – Kill service
-
Kate Dries – Defamation-for-sale blogger
-
Katharine Trendacosta – Defamation-for-sale blogger
-
Katherine Drummond – Defamation-for-sale blogger
-
Kathy Zoi – DOE Quid Pro Quo operator
-
Keith Rabois -VC
-
Kelly Stout – Defamation-for-sale blogger
-
Ken Alex – Adviser to Jerry Brown
-
Ken Duberstein and Marti Thomas, The Duberstein Group
-
Ken Howery – VC
-
Kerrie Uthoff – Defamation-for-sale blogger
-
Kevin Draper – Defamation-for-sale blogger
-
Kleiner Perkins – Campaign funding VC – hires many attack services
-
Kroll – Private CIA and attack services
-
Lacey Donohue – Defamation-for-sale blogger
-
Lachlan Seward – Energy Department gatekeeper for White House insiders
-
Larry O’Brien, OB-C Group
-
Larry Page – Google Boss accused of stealing technology for Google
-
Larry Summers – VC and Facebook covert advisor
-
Licy Do Canto, The DoCanto Group
-
Lisa Kountoupes, Kountoupes Consulting
-
Lloyd Craig Blankfein – VC and Sachs boss
-
Lucy Haller – Defamation-for-sale blogger
-
Luke Malone – Defamation-for-sale blogger
-
Luke Nosek
-
Madeleine Davies – Defamation-for-sale blogger
-
Madeline Davis – Defamation-for-sale blogger
-
Marc Andreessen – VC who has a kill-them-all process towards competitors
-
Mario Aguilar – Defamation-for-sale blogger
-
Mario Rosatti – VC
-
Mark Isakowitz, Fierce, Isakowitz and Blalock
-
Mark Kadesh, Kadesh & Associates
-
Mark Zuckerberg – Facebook Boss
-
Martin LaGod – VC Firelake Cap
-
Marty Paone, Prime Policy Group
-
Mary Meeker – VC
-
Matt Hardigree – Defamation-for-sale blogger
-
Matt Novak – Defamation-for-sale blogger
-
Matt Rogers – VC and pass-through conduit
-
Max Levchin -VC
-
Mckinsey Consulting – The firm you hire to rig white papers and insider hires in government positions for the Palo Alto Mafia
-
Media Matters – Attack service
-
Megan Smith
-
Melissa Schulman, The Bockorny Group
-
Michael Ballaban – Defamation-for-sale blogger
-
Michael Dobbs – Defamation-for-sale blogger
-
Michael Eisenberg
-
Michael Sussmann – attack operative
-
Michael Moritz -VC
-
Michael Spinelli – Defamation-for-sale blogger
-
Mikey Dickerson
-
Mitch Feuer and Robert Griner, Rich Feuer Group
-
Morrison and Foerster
-
MotiveAI – Digital attack and media manipulation service
-
Nancy Pelosi – California politician who hires many attack services
-
Nathan Parker
-
Neal Ungerleider – Defamation-for-sale blogger
-
New America Foundation
-
New Venture Fund – Tricks rich people into financing attack services
-
Neerag Agrawal
-
Nicholas Aster – Defamation-for-sale blogger
-
Nicholas Guido Denton – Defamation-for-sale blogger and head of the Gawker, Gizmodo, Jalopnik sleaze tabloid empire – Takes kill orders directly from White House, Elon Musk and Larry Page
-
Nick Cook – Gawker attack services coordinator
-
Omar Kardoudi – Defamation-for-sale blogger
-
Open Society – George Soros own attack provider service and news manipulation outlet
-
Orbis Business Intelligence – Attack service
-
Owen Thomas – Defamation-for-sale blogger
-
Pacronym – Election manipulation and attack service
-
Pantsuit Nation – Election manipulation service
-
Palantir – Peter Thiel’s spy agency, private CIA
-
Patrick George – Defamation-for-sale blogger and Character Assassination expert
-
Patrick Laffoon – Defamation-for-sale blogger
-
Patrick Redford – Defamation-for-sale blogger
-
Perkins Coie – Campaign conduit law firm, attack and spy service
-
Peter Fenton
-
Peter Thiel – VC and Elon Musk boyfriend
-
Pierre Omidyar – Defamation-for-sale blogger
-
Plouffe Consulting – Talks rich people into funding attacks and election rigging
-
PR Firm Sunshine Sachs – Attack service
-
Priorities USA – Attack service
-
Rahm Emanuel – White House boss, loves attack services
-
Raj Gupta – VC, arrested
-
Rakesh Saxeena – Canadian in-house arrest, arms dealer, western political packager
-
Ray Lane – VC, under IRS investigation
-
Reid Hoffman – VC and sex.com partner with Gary Kremen, also match.com
-
Rhod Shaw, The Alpine Group
-
Rich Juzwiak – Defamation-for-sale blogger
-
Richard Blakely – Defamation-for-sale blogger
-
Richard Rushfield– Defamation-for-sale blogger
-
Robert Finger– Defamation-for-sale blogger
-
Robert Gibbs – White press office head, ordered the hiring of attack services
-
Robert Raben, The Raben Group
-
Robert Sorokanich – Defamation-for-sale blogger
-
Roelof Botha
-
Rory Waltzer – Defamation-for-sale blogger
-
Rosa Golijan – Defamation-for-sale blogger
-
Russel Simmons
-
Ryan Brown – Defamation-for-sale blogger
-
Ryan Goldberg – Defamation-for-sale blogger
-
Sam Faulkner Biddle – Defamation-for-sale blogger, Runs a large part of the Anti-GOP blog programs
-
Sam Woolley – Defamation-for-sale blogger
-
Samar Kalaf – Defamation-for-sale blogger
-
Sanjay Wagle – VC
-
Sarah Ramey – Defamation-for-sale blogger
-
Scott Shleiffer
-
Sergy Brin – Google boss involved in sex scandal
-
Shannon Marie Donnelly– Defamation-for-sale blogger
-
Shadow Inc – Attack Service
-
Shareblue – Attack Service
-
Sid Blumenthal – Creator of Attacks-As-Service concept
-
Shep McAllister – Defamation-for-sale blogger
-
Sixteen Thirty Fund – Tricks rich people into financing attacks
-
Sophie Kleeman – Defamation-for-sale blogger
-
SpaceX – Domestic spy satellites spy on consumers
-
States Newsroom – Media attack network
-
Secondary Infektion – Blogger attack service
-
Stephen Totilo – Defamation-for-sale blogger
-
Steve Chen
-
Steve Elmendorf and Jimmy Ryan, Elmendorf Group
-
Steve Jurvetson – VC embroiled in sex abuse charges
-
Steve McBee, McBee Strategic
-
Steve Perry and Andy Wright, Dutko Grayling
-
Steve Rattner – White House car czar, indicted for fraud
-
Steve Spinner – Energy Department manipulation expert, Wife was Solyndra’s lawyer before the FBI raid
-
Steve Westly – VC that financed Obama campaign
-
Steven Chu – Secretary of Energy – The most corrupt in US history
-
Stratfor Intelligence Services – Spy and attack service
-
Supermajority News – Attack service
-
Tamar Winberg – Defamation-for-sale blogger
-
Taryn Schweitzer – Defamation-for-sale blogger
-
Taylor McKnight – Defamation-for-sale blogger
-
Ted Schlein
-
Tesla Motors – Car Company that conduits money to campaigns
-
The Groundwork – Social manipulation group
-
The Americano
-
The Agency – Massive network of attack bloggers based out of Russia
-
The X – Attack network Elon Musk uses that creates fake fanboys on Twitter, Facebook, Instagram, Google, etc.
-
Think Progress
-
Thomas Jolly, Jolly/Rissler
-
Thorin Klosowski – Defamation-for-sale blogger
-
Tim Draper – VC
-
Tim Marchman – Defamation-for-sale blogger
-
Timothy Burke – Defamation-for-sale blogger
-
Tobey Grumet Segal – Defamation-for-sale blogger
-
Todd Park – IT manipulator inside White House
-
Tom Ley – Defamation-for-sale blogger
-
Tom O’Donnell, Gephardt Government Affairs Group
-
Tom Scocca – Defamation-for-sale blogger
-
Tom Steyer – VC
-
Tomorrow Ventures – Social manipulation group
-
Tony Podesta, Podesta Group
-
Twitter – Biased media manipulation service
-
Tracy Spicer, Avenue Solutions
-
Veronica de Souza – Defamation-for-sale blogger
-
Viktor Vekselberg – Russian man who hires many services
-
Vinod Khosla -VC
-
Wes Siler – Defamation-for-sale blogger
-
WikiStrat – Attack service
-
William Haisley – Defamation-for-sale blogger
-
William Turton – Defamation-for-sale blogger
-
Wilson, Sonsini, Goodrich and Rosatti – Attack lawyers
-
WordPress.org – Censors or deletes any site that speaks against Nancy Pelosi directives, Soros funded
-
Yasmin Green – Google’s Anti-arab
-
YouTube – Media manipulation attack service
-
Undercover Global Ltd – Attack service
-
Versa LLC – Attack service
Congressional and FEC investigators have a big question here. The big question is:If the people, above, are manipulating public elections with information trickery: IS THAT TREASON?
Because almost every one of them coordinated to attack others and their businesses, they broke the RICO Racketeering and anti-trustlaws in America! In an FBI interview, it is believed that every person on this list would be implicated in charges when asked, underoath: “ARE YOU, OR HAVE YOU EVER HIRED, A CYBER ATTACKER?“
These were not just ‘some people’ who wrote something mean on a Facebookpost. They had exclusive publishing resources on a national and global network that they systematically, and in a highly coordinatedmanner, operated on in exchange for compensation, to harm and attack specific targets that they were instructed to harm.
More names will be forthcoming as investigators complete their reviews.
ATTACKERS Daniel Jones, Michael Sussmann, Nicholas Guido Denton, John Herrman, Adrian Covert, Media Matters,John Cook, Ian Fette, Gabrielle Darbyshire, Patrick George, Eric Schmidt, Jay Carney and David Axelrod have already been placed underfederal surveillance for some time. TARGET will request their case records from the FBI, FINCEN, Interpol, The NSA, The IRS, theirbanking and stock market accounts, and other sources, which will prove the assertions about their attacks, who hired them and thetop-level command-and-control authority over their actions.
THE REPRISAL ATTACK TOOLS USED ON AMERICAN CITIZENS – THE ATTACKERSPLAY-BOOK:
HARM #1: MANIPULATION AND BLOCKADE OF TARGET’s EARNED GOVERNMENT FUNDS
In a typical reprisal case a Plaintiff (also known as a “TARGET”) applied for government SSDIand a HUD home certificate. SSA stated that all of TARGET’s disabling conditions existed but that TARGET must confirm they willlast more than a year. TARGET’s SSDI and HUD certificate were blockaded by Pelosi and Feinstein in reprisal for TARGET helping lawenforcement on anti-corruption investigations that involved Pelosi, Feinstein and their political financial backers.
CaliforniaSenators, all of whom have vast documented court and news report records of hiring attackers from spy agencies for reprisal attacks onwhistle-blowers, used their resources to stop all funding in the TARGET’s SSDI funding as reprisal for whistle-blowing. They gotSSA to say that TARGET WAS permanently disabled, but that because he could not work, he lost his SSA credits waiting the one year and oneday that SSA required to prove that his disabilites would last longer than a year. Dianne Feinsteins own staff and family, who hadcohabitated with TARGET, confessed to these ‘dirty-tricks’ actions as reprisal for TARGET’s testimony accidentally cutting off$120 million+ of potential profit the family expected. Her staff have been exposed by CIA staff as “the masters of dirty tricks reprisals…even as good as the ones we (THE CIA) pull off..”
Another time, a TARGET applied for his HUD Mortgage coupon. He was forced towait 15+ years and he still has not received it after over 100 inquiries as to the status. City and County officials have statedthat they have “never seen it take so long”. According to all experts, the only way it could have been stone-walled this long is ifa public official (ie Feinstein, Pelosi, Harris…) had ordered it slow-walked as part of the politial reprisal attacks on TARGET. Threedifferent counties have checked on this and said that TARGET’s records ‘went missing” in a Lois Lerner type of error set.
The cut-off of TARGET’s finances and benefits coincides, exactly, withhis whistle-blower testimony AND to the reprisal threats and promises by THE ONLY PEOPLE IN THE WORLD capable of accomplishing suchstate-sponsored attacks. The ATTACKERS were the only entity with the means, the motivation and the proven history of such actions on aregular historical basis.
Feinstein’s current and former staff members (See the Dossier on Daniel Jones)(See the fact that TARGET lived with, dined with and partied with her family and senior staff) have stated that the Feinstein and Pelosioffices commonly order citizens government funding to be cut off as political reprisal. The White does it almost every other day. In thiscase they did it to TARGET at least three times.
TARGET, had an industry standard pay rate of $10,000.00 per month, based onSalary.com, his high highest recorded salary and accomplishment records in Silicon Valley contrasted with the salaries of lessexperienced executives at Google, Facebook, Netflix and Tesla. The U.S. Government states, via all of its agencies, that the minimumsurvivable cost-of-living in the Bay Area is $3200.00 per month. By intentional actions of government officers, in reprisal, TARGET’sincome was reduced to $300.00 per month for most of the past decades. Two SSA officials confessed to assisting in hit jobs on him includingMario U from the San Mateo SSA office and an official who worked at the San Francisco SSA office and who then went to work for a Senatorwho assisted in the attacks on TARGET. When asked for TARGET’s medical records SSA sent a huge number of medical records for twostrange women in massive violation of federal medical privacy rights. The SSA Inspector General has shown TARGET thousands of cases ofpoliticians using SSA for political reprisal punishments. FBI IT experts and ‘Black Hat’ hackers can hack into every SSA server inminutes and change records, files and decisions. Rahm Emanual, Nancy Pelosi and Dianne Feinstein can do it with a single phone call. Itshould be noted by the Court that EVERY background check file in AMERICA was hacked and stolen by China within a few hours and thatevery hacking tool of the NSA and CIA was hacked by Russia and posted on the internet. It is IMPOSSIBLE for anyone to ever assert that“nobody can hack SSA”. That would be a remarkable lie. In fact, TARGET has agency confimation that 95% of the Silicon Valleyoligarchs entire family tax records, stock accounts, political payments and payola and pretty much everything that would destroythem, has been hacked and is in the hands of ICIJ (Panama Papers investigators), Propublica, FINCEN and pretty much everybody theywould not want to have it.
The TARGET has demanded that the Court order SSA to award TARGET his full SSDI backpay from up to today, with interest, based on the fact that SSA was used to harm Plantiff as a reprisal tool.The Inspector General has proven this happens regularly and hundreds of other whistle-blowers are prepared to confirm this fact.
HARM #2: THREATS OF DEATH AND ACTUAL MURDERS OF PEERS
One TARGET has actually been attacked as enumerated below and has active cases with SFPD, FBI, OSCand other agencies. Twice TARGET’s car was rammed. The first time the attacker performed a PIT maneuver, flipping TARGET’s car onto theconcrete median wall on the Freeway, causing massive damage. The attacker sped away. A car next rammed TARGET’s parked car in front ofhis home and, at the same location, a man tried to drive has car through the fence into TARGET’s cottage. Two other times, strangerspulled up along TARGET, pointed at him and yelled “you are dead”. TARGET has received threats by email and voicemail and had dead animals tossed over his fence. Further proving theat-risk claims of TARGET. TARGET, and his peers, had contact with the following persons in the corruption case: Rajeev Motwani; Gary D. Conley; Seth Rich; Philip Haney; David Bird; Doug Bourn; Misti Epstein; Joshua Brown; Kenneth Bellando; Moritz Erhardt;Imran Aliev; Kate Matrosova; David Drye; Vincent Foster; Kathy Ferguson; Duane Garrett;Eric S. Fox; Judi Gibbs; Berta Caceres; Suzanne Coleman; L.J. Davis; John Hillyer; Stanley Huggins; Sandy Hume; Shawn Lucas; Gary Johnson;John Jones; John F. Kennedy, Jr.; Stephen Ivens; Mary ‘Caity’ Mahoney; Eric Butera; Danny Casolara; John Ashe; Tony Moser; LarryNichols; Joseph Rago; Ron Brown; Bob Simon; Don Adams; Peter Smith; Victor Thorn; Lori Klausutis; Gareth Williams; Daphne CaruanaGalizia; James D Johnston; Dave Goldberg; Loretta Fuddy; Paul Wilcher; Gary Webb; Beranton J. Whisenant Jr; Stanley Meyer; JonParnell Walker; Tyler Drumheller; Barnaby Jack; Dominic Di-Natale; Barbara Wise; Ilya Zhitomirskiy; Jeff Joe Black; Robin Copeland; JohnWheeler; Ashley Turton; Michael Hastings; Antonin Scalia; David Koschman; David Werner; Alex Okrent; Kam Kuwata; Larry Frankel; And hundreds more connected to this case who suddenly, and strangely, turned up dead in this case and, ironically, theirdeaths all benefit the suspects in this case….Rajeev Motwani taught Google how to Google. Suddenly, in perfect health, he was found floatingface-down, dead, in his Silicon Valley swimming pool. It helps certain people that he can no longer talk. Gary D. Conley was the CleanTech competitor to, and whistle-blower on, the suspects. He wassuddenly found with a bullet in his head behind Beale Air Force base. It helps certain people that he can no longer talk. He TOLD TARGET that someone from Google was going to kill him. Google programmer Forrest Hayes, who worked on Google search engine rigging, was suddenly found dead with the storythat “he was overdosed by a Google hooker on his sex yacht”. Google associate and Tesla Investments founder Ravi Kumar was also killed by his hooker. Deep Google investor VC liason and husband of Facebookexecutive Cheryl Sandberg was suddenly found dead with a hole is his head. The “official” story is thathe was the first person in history to be killed by his treadmill. David Bird was the Wall Street Journal energy reporter who was working on astory that involved Cleantech energy connections of some of the suspects. He was working on a story about who controlled the modernenergy industry and cleantech. He went for a walk and was found a long time later, dead, floating in a pond. It helps certain peoplethat he can no longer talk. One Mr. Breitbart was a famous blogger, who railed on the web about the politicalmanipulations of the suspects. Suddenly, he had a “heart attack” in his shower and died. It helps certain people that he can no longertalk on the blogs. Mr. Karl Slym , with Tata Motors was involved in a car deal with some of thesuspects for one of the biggest Indian auto-makers. Suddenly he was a stain on the sidewalk, accomplished by his fall from the top of askyscraper hotel. It helps certain people that he can no longer talk. Doug Bourn, The senior electrical engineer at Tesla (Google’s covert partner),Andrew Ingram of Palo Alto, a top systems electrical engineer at Tesla; and Brian M. Finn the senior manager of interactive electronics, at Tesla, had deep knowledge offinancial misdeeds and technical cover-ups at Tesla Motors. They were key parts of the Tesla operation. For some reason, they all got intoa private airplane, in perfect health, and then the airplane plowed into the ground, killing all three at once. It helps certain peoplethat they can no longer talk. They wrote, and helped describe, in Tesla’s own federal patent filings, the fact that Tesla’s batterieswould kill you, maim you and/or burn your house down. Tesla did not realize this when they paid the federal patent filing fees. WhenTesla, later realized this, they were forced to give all of their patents away for free. These three senior engineers had deep insideknowledge of the Tesla Motors operations. Their aircraft suffered an “Engineering failure”. This case involves potential crimes by two Presidents of The UnitedStates, their staffs, U.S. Senators and the Silicon Valley oligarchs that financed and controlled them, two wars and trillions of dollarsof manipulated U.S. Treasury monies and stock marke monies. How could anyone think this was NOT a life-endanging situation for the TARGET?
HARM #3: THE GOVERNMENT DEFRAUDED A TARGET OVER AND OVER:
Government agency bosses solicited a TARGET with false promises of future loans, carbon credit sales, billions of dollars of stock market valuation profits, contracts and/or grants from their agencies and caused the TARGET and his associates to expend millions of dollars and years of their time for projects which those government bosses had covertly promised to their friends. They used TARGET’s ‘nice guy’ brand as a “smokescreen” to cover their illegal government slush-funds for TARGET’s competitors and personal enemies who were OWNED by government officials. By using this tactic, the attackers drained the TARGET’s funds and forced TARGET into an economic disaster, without the government bosses fearing any reprisal for their scam. The crony insiders made hundreds of billions of dollars in profit in the notorious Solyndra-type scandals as seen in the CBS 60 Minutes episode: “The Cleantech Crash”, thousands of TV news segments and the related GAO and Congressional corruption reports.
HARM #4: THE PLACING OF MOLES AND SPYING ON TARGET:
White House financier Kleiner Perkins placed moles inside of TARGET’s companies in order to sabotage, delay and misdirect operations. The moles were discovered to be staff of Kleiner Perkins. The main offices of Kleiner Perkins were broken into, per San Mateo County police reports, and records of corruption copied or duplicated by a state-sponsored intelligence agency entity, which provided further proof that Kleiner Perkins and the White House were exchanging Quid Pro Quo. Tom Perkins, one of the founders of Kleiner Perkins told TARGET that he was on “A government hit-list” for exposure the corruption of Silicon Valley titans and government executives. John Doerr, another partner, told one TARGET at a VC conference, that he will make sure the government kills off any effort to support fuel cells (which compete with his and Elon Musk’s lithium batteries)
HARM #5: BLOCKADES OF TARGET’S ACCESS TO LEGAL COUNSEL:
The hired cyber assassins used every trick in the book to keep Targets from gaining equitable legal justice or representation because exposure of The ATTACKERS crimes would shame them Government officials and the federal agency: Legal Services Corporation (LSC corporation -A federal agency dedicated to providing legal services to citizens) blockaded TARGET’s rights to legal representation in order to prevent TARGET’s from personally suing the attackers because such a lawsuit would have embarrassed corrupt public officials. High tech law firms that were discussing a services agreement with TARGET’s were threatened and ordered to not help TARGET’s or “they would be black-listed or be cut-off from tens of millions of dollars of Google, Netflix, Facebook and government contracts”. Individual lawyers were threatened with black-listing and getting “flooded with more filings than you could ever respond to in your life-time...” LSC officials, who were almost entirely Obama Administration associates, refused to assist with lawyer referrals. That is a violation of their federal contract with The U.S. Government. Every other possible lawyer had either 1.) been threatened, by the attackers, from representing the Plaintiff, 2.) contracted by the attackers so that they were conflicted from representing the Plaintiff, 3.), or intimidated by the attackers in one of many ways.
HARM #6: HIRED CHARACTER ASSASSINATION AND DEFAMATION SERVICES THAT The ATTACKERS USED TO DESTROY TARGET’S LIFE
In one case the attackers purchased over $30 Million dollars of attacks against the TARGET with Media Matters, The Gawker/Gizmodo Tabloid empire and Google. It was equal in scope and cost the amount of money Bloomberg spent IN ONE WEEK to attack Presidential candidate Trump. A sophisticated animated attack film was produced by Google/Youtube and Nicholas Denton attacking TARGET’s. An animated film is an expensive effort involving considerable time and expense. An attacker must be well financed to undertake such an effort. The film was published on YouTube and locked onto the very top search result line on every YouTube search in front of 7.5 billion internet users for over a decade. The damage to TARGET’s reputation is estimated in the tens of millions of dollars. YouTube steadfastly refused to remove or adjust the search results even though YouTube executives knew TARGET personally and knew that the video represented a character assassination attempt against TARGET. YouTube owners finance the political campaigns of the public officials who ordered the attacks. While Google/YouTube stated to Congress that all of it’s search results are arbitrary, the never-moving search result of this attack video proved that Google’s and YouTube’s search results are manually manipulated by human maintained black-lists. The corrupt officials hired Nicholas Guido Denton and his character-assassination-for-hire sleazy tabloid publication empire known as Gawker Media AKA Gizmodo Media. They own Gawker, Gizmodo, Jalopnik and a number of fake news sites based in the USA and near-Russian regions. The offshore sites are used for money laundering and tax evasion. The FBI has been asked to interview and financially trace the payments and command-and-control orders back and forth between Nicholas Guido Denton and his attacker/operatives: Ian Fette, Adrian Covert, Nick Cook, Gabrielle Darbyshire, John Hermann, Patrick George, et al and Google. Forensic data proves that the attackers transferred payments and communications between each other to conspire, operate, produce and publish the articles, videos, blogs and server manipulations for the attacks against their victims around the world. These attacks resulted in billions of dollars of damages to the victims. The orders for these attacks can be traced back to The White House. This ended the TARGET’s lives but created an enemy for the attackers that has lots of of investigator contacts and nothing to lose. Silicon Valley has caused the deaths of more children than any other entities. Harassment is harassment – whether it happens at school, at the playground, on the job, or on the internet. But online bullying is downplayed. Victims are stigmatized, mocked as oversensitive snowflakes who can’t take a joke. Plenty of people are unwilling to accept that victims can be seriously hurt by this behavior. Internet harassment is not only real and damaging, it represents a threat to the most vulnerable among us: children. The attacker’s Cyberbullying statistics show the high cost of online harassment. From increased depression and suicide rates to social anxiety and alienation, the pain and consequences of online harassment are as severe as they are undeniable. Imagine every new friend, potential date, your fiance’, your bank, anybody.. typing your name on the internet and seeing that Google says that you are a scumbag. Nobody will ever talk to you, hire you or help you ever again. Google, Gawker and Gizmodo are now known to partner together on character assassination efforts. One of their bloggers hired to “kill” TARGET even advertises himself on Facebook, globally, as an assassin-for-hire. TARGET has acquired the banking records of these Co-conspirators showing that they, and the U.S. government wired millions and millions of dollars between each other for these “spy agency” dirty tricks hit jobs.
Google knew one TARGET personally. The TARGET went to school and events with the founders. It was a lie for Google and YouTube to sayover-and-over that they never heard of TARGET so they “can’t remove the attacks because it is ‘just how their algorithm works’…”The founder’s teacher: Rajeev Motwani, revealed to TARGET that Google manually sets all of their key search results BY HAND. Rajeevdied was murdered for telling the truth about Google’s insidious plans and internet manipulations. Investigators suspect shell fish toxin or a reverse taser-like electronic heart-attack inducing defibulator device was used to kill him.
TARGET’s charges proved that Google manually rigs search results based oncronyism and that Google/YouTube lied to Congress about not doing so. This allowed TARGET to drive U.S. agencies and State AG’s to sueGoogle/Alphabet/Youtube for being lying, manipulate, society-abusing, child-killing, monopolistic monsters. Even though theGoogle/Gawker/Gizmodo produced and hosted attack articles and animated videos were completely discredited as a “character assassination hatchet job paid for by politicians”; by every known expert, The ATTACKERS still post them on their servers withhidden “P8” codes covertly embedded in the search engines to trick the public, in front of 7 billion internet readers as“payback”, in order to operate their reprisal attacks. No other servers or publishers in the world host and lock this attack media ontheir search results EXCEPT The ATTACKERS MEDIA COMPANIES. This ALONE would seem to prove that The ATTACKERS did the harms that they arecharged with doing as The ATTACKERS are the only ones running, hosting and operating the attacks on TARGET on all of Earth!
TARGET has, over and over, demanded that the FBI, POLICE, FINCEN and otherenforcement investigators reveal what they discovered when they traced the compensation routes and command-and-control management ofthese attackers. TARGET demands that this Court order the FBI, FINCEN and the NSA to reveal those compensation path records on the attackers from their investigations.
One might wonder why it has been so hard to get this information from theauthorities. If the FBI reveals that the path-of-compensation goes from Adrian Covert, Nicholas Guido Denton and John Herrman right tothe Oval Office in the White House, then the question is asked and answered. White House staff members Jay Carney, David Axelrod andRobert Gibbs have said “maybe”. White House staff insider Jofi Joseph has said “without a doubt”. Rahm Emanual’s White Housestaff say that, while in the White House, Rahm ordered all kinds of hit-jobs on whistle-blowers.
Gawker Media and Gizmodo Mediahave engaged in the origination of, production of and global broadcast of compensated character assassination videos and articlesas a reprisal-service-for-hire (like Fusion GPS, Black Cube, Black Water and other related services) because we were FBI and GAOwitnesses against Gawker and Gizmodo financiers. As 1.) the only publishing group on Earth to have engaged in such attacks and 2.)since the attacks were financed by complainants business competitors and 3.) since adversaries own staff have admitted to the scheme and4.) since communications, FBI records and previous litigation records prove complainants assertions, complainants are justified in theirdemands.
The attacks and broadcast of multiple defamation attack articles andvideos by Gawker Media, Google, YouTube and Gizmodo Media has been operating as recently as this today, thus the statutes of limitationsare not exceeded. Well known U.S. government political figures and political financiers hired Gawker Media, Gizmodo Media and “Nick”Denton to undertake these ongoing attacks and to manipulate web servers to operate those attacks globally and permanently. Theattackers hired Gawker Media, Gizmodo Media, “Nick Guido Denton”, Univision/Unimoda, Google and YouTube (essentially all the samepeople) to engage in reprisals because of the TARGET’s testimony against the Cartel in federal investigations and because the TARGEThad superior technologies that the attackers could not compete with. Transaction documents showing payments between the “bad guys” inthis case, were recently uncovered in other court cases.
Defendant adversaries produced a series of videos and defamation articles andused internet server technology tricks to place those attack materials in front of 7.5+ billion people day after day, year afteryear, refreshing the attack daily. This is, essentially, a “hit-job” service that Univision provides as a side gig through it’s TVnetworks and it’s offensive tabloid brands of: Gizmodo, Jalopnik, Jezebel, Gawker and other Univision/Unimoda assets along with it’spartnership with Google for the operation of such attacks. “Univision uses this service as a political-payback tool for politicians as wellas an anti-trust violating anti- competition tool for its clients”, claim TARGET’s. The TARGET’s are informed and believe and, based onthat information and belief, allege that the named The ATTACKERS herein and each of the parties designated as a “DOE” and everyone of them, are legally responsible jointly and severally for the Federal RICO Statute violating events and happenings referred to inthe within Complaint for Intentional Interference with Contractual Relations, Intentional Interference with Prospective EconomicAdvantage, Cyberstalking, Fraud, Invasion of Privacy, Unfair Competition and Theft of Intellectual Property and RICO statuteviolations. In particular, The ATTACKERS took compensation for, and engaged in, malicious and coordinated tactics to seek to destroy,damage, harm and ruin TARGET’s via an illicit media “hit-job” service which The ATTACKERS regularly offered in covert commerce andengaged in regularly against targets that The ATTACKERS were hired to seek to ruin as part of reprisal, vendetta, retribution programsoperated for business and political competitors of the targets. Historical facts and other history-making lawsuits by third parties,has proven The ATTACKERS to be the single largest core violator of human rights, in this manner, in the world. The ATTACKERS offer theservice of creating and publishing contrived “hatchet job” movies, fake news articles, faked comments and repercussion backlinksdescribing the TARGET’s in horrific descriptors. The ATTACKERS media holdings manipulate national elections.
Let’s be clear on this: TARGET does swear, warrant and certify that Google,Facebook, YouTube, The Elon Musk Group, Twitter and Linkedin plan and operate the conscious and manual manipulation of national Americanelections and international elections.
The attack material is reposted, “impression accelerated”,“click-farm fertilized” and Streisand array cloned over-and-over by The ATTACKERS massive character assassination technology viaservers, algorithms and technical internet manipulation, daily, as recently as yesterday. The ATTACKERS also embed the article in jobhiring databases on Axciom, Palantir, Taleo and other databases used by all hiring and recruiting services in order to prevent TARGET’sfrom ever receiving income for W2 or 1099 work ever again. The ATTACKERS own staff then post thousands of fake comments, below eachattack item, under fake names, designed to make it appear as if a broad consensus of the public agreed with the defamation messages byThe ATTACKERS. Almost all of the fake comments were created by a handful of The ATTACKERS own staff pretending to be a variety ofoutside voices. The ATTACKERS provide the service of delivering “weaponized text and media to corporate clients”. The ATTACKERSreplicated various versions of these attack items across all of their different brands and facade front publications and addedadditionalfake comments to each on a regular basis.
The ATTACKERS have formed a business and political and industrymanipulation “Cartel”. The bosses of the the ATTACKERS intended to inflict corruption upon the United States Federal Government, TheState Government and the California State authorities, as defined by law under RICO Racketeering Statutes for the purpose of manipulatingthe value of stock market holdings and controlling political policy decisions.
In exchange for financing, The ATTACKERS Clients gave The ATTACKERSAssociates business monopolies and government contract monopolies and media distribution exclusives worth trillions of dollars. This was anillegal quid-pro-quo arrangement. TARGET’s designed, produced, received patent awards on, received federal commendations for,received federal funding for and first marketed the very products which The ATTACKERS copied and made billions of dollars on and whichThe ATTACKERS felt might beat them in hundreds of billions of dollars of competitive market positions and stock market trades. Companiesoperated by TARGET’s included automobile design and manufacturing companies, global television broadcasting companies and energycompanies which are commonly known to have generated hundreds of billions of dollars in profits, revenue and stock market transactionsfor The ATTACKERS competing holdings at TARGET’s expense. The ATTACKERS operated a criminal CARTEL as defined by RICO LAWS and thatCartel ran an an anti-trust market rigging and crony political payola operation. The ATTACKERS spent tens of millions of dollars attackingTARGET’s because The ATTACKERS were not clever enough to build better products. The ATTACKERS chose to “CHEAT RATHER THAN COMPETE” andto try to kill TARGET’s lives, careers, brands, revenues, assets, businesses and efforts via malicious and ongoing efforts.
The U.S. Attorney General has been informed, in writing, of these chargesand TARGET’s understand that DOJ officials have an ongoing investigation into these matters.Under investigation for thesecrimes, New York State attorney general Eric Schniderman was recently forcedto quit over corruption and sexual cult charges involving theNXIUM group and related matters.
Due to The ATTACKERS fears of the loss of up a trillion dollars of cronypayola from their illegal abuse of taxpayer funds, The ATTACKERS engaged in felonious actions in order seek to intimidate others.
Just as, over time, the Watergate crimes are now intimately documented anddetailed; over time The “Cleantech Crash Scandal” as featured on CBS News 60 MINUTES TV Show, has
been detailed and exposed in numerous federal, news media and publicinvestigations. Significant barriers to justice were illicitly placed in front of TARGET’s by The ATTACKERS.
The ATTACKERS organized and operated a series of malicious attacks andthefts against TARGET’s as reprisals and competitive vendettas. The ATTACKERS report to the FBI, GAO, FTC, SEC,
Congressional Ethics Committees, The White House and other entities on a regularbasis.
The ATTACKERS and their associates Elon Musk, Jon Doerr, Eric Schmidt,Larry Page, Steve Jurvetson, Vinod Khosla and other members of the “Silicon Valley Cartel” are documented in tens of thousands ofnews reports, federal law enforcement reports and Congressional reports in their attempts to infiltrate and corrupt the U.S.Government in an attempt to route trillions of tax dollars to The ATTACKERS private accounts. The ATTACKERS perceived TARGET’s as athreat to their crimes. Federal investigators, news investigators and whistle-blowers have reported to TARGET’s that The ATTACKERS were thefinanciers and/or beneficiaries and/or command and control operatives for the crimes and corruption disclosed in the CBS NEWS 60 Minutesinvestigative reports entitled: “The Cleantech Crash”, “The Lobbyists Playbook” and “Congress Trading on InsiderInformation”; The Feature Film: “The Car and the Senator” Federal lawsuits with case numbers of: USCA Case #16-5279; and over50 other cases including the ongoing “Solyndra” investigation and federal and Congressional investigations detailed at:
http://greencorruption.blogspot.com
and
https://theintercept.com/2016/04/22/googles-remarkably-close-relationship-with-the-obama-white-house-in-two-charts/
… and thousands of other documentation sites. TARGET’s are chargedwithengaging in these crimes and corruptions against TARGET’s and financing and ordering attacks on TARGET’s. TARGET’s engaged in U.S.commerce and did everything properly and legally. Unlike The ATTACKERS, TARGET’s did not steal technology. Unlike The ATTACKERS,TARGET’s did not bribe elected officials in order to get market exclusives. Unlike The ATTACKERS, TARGET’s did not poach TheATTACKERS staff. Unlike The ATTACKERS, TARGET’s were the original inventors of their products. Unlike The ATTACKERS, TARGET’s did notoperate “AngelGate Collusion” schemes and “High Tech No Poaching Secret Agreements” and a Mafia-like Silicon Valleyexclusionary Cartel. Unlike The ATTACKERS, TARGET’s did not place their employees in the U.S. Government, The California Government,The U.S. Patent Office and The U.S. Department of Energy in order to control government contracts to The ATTACKERS exclusive advantage.Unlike The ATTACKERS, TARGET’s did not place moles inside of competitors companies. Unlike The ATTACKERS, TARGET’s did not hireGawker Media and Think Progress to seek to kill TARGET’s careers, lives and brands. Unlike The ATTACKERS, TARGET’s did not rig thestock market with “pump-and-dump”, “Flash Boy” and “Google-stock/PR-pump” schemes. TARGET’s engaged in hard workevery day of their lives for the time-frame in question under the belief that the good old American work ethic and just rewards foryour creations was still in effect in the U.S.A., and that the thieves and criminals that attempted to interdict TARGET’s would faceJustice. In a number of circumstances The ATTACKERS took advantages of TARGET’s hard work via come-ons; The ATTACKERS then made billionsof dollars from Plainiffs work at TARGET’s expense and attacked TARGET’s in order to reduce TARGET’s competitive and legal recoveryoptions.
The ATTACKERS exchanged payments for services via cash, stock warrants,illicit personal services, media control and a technology known as a “Streisand Effect Massive Server Array” which can control publicimpressions for, or against a person, party, ideology or issue. The ATTACKERS StreisandEffect internet system was used to destroyTARGET’s in reprisal, retribution, and vendetta for TARGET’s help with law enf ment efforts in the case and because TARGET’s companiescompeted with The ATTACKERS companies with superior technologies.
The ATTACKERS have used their Streisand Effect technology to build acharacter assassination ring of bloggers and hired shill “reporters” who engage in a process called a “Shiva”. This process is namedafter a TARGET in a similar case named: Shiva Ayyadurai, the husband of Actress Fran Drescher. Shiva Ayyadurai holds intellectual propertyrights to part of The ATTACKERS email technology. In fact, the people most threatened by the Shiva Ayyadurai patent right claims,ironically turn out to be The ATTACKERS and, in particular, The ATTACKERS associates Elon Musk, Jon Doerr, Eric Schmidt, Larry Page,Steve Jurvetson, Vinod Khosla and other members of the “Silicon Mafia” who own most of the main companies exploiting emailtechnology. Were Shiva Ayyadurai to prevail in his claims, The ATTACKERS would owe him billions of dollars. “Running A Shiva”involves the production of a series of Defamation articles by bloggers who act asif they are independent from The ATTACKERS but arein fact, not. The ATTACKERS used “the Shiva” to attack and seek to destroy Donald Trump, Shiva Ayyadurai, TARGET’s, and numerouspolitical figures. Univision, Unimoda,Jalo pnik, Gawker Media, Gizmodo and over a hundred stealth-ed, and overt, assets of TheATTACKERS have been using “The Shiva” network to attack Donald Trump, Shiva Ayyadurai, TARGET’s, and numerous political figures asrecently as this morning, thus, the time bar restarts every day. TARGET’s have pleaded with The ATTACKERS to cease their attacks butThe ATTACKERS have refused to comply. Even with Fran Drescher’s ongoing royalty payments from her popular television series, friendshave reported that the attacks on the Ayyadurai family have been devastating and have caused massive damages and personal andemotional devastation.
The ATTACKERS produced animated movies, attack articles, fake blog comments, DNS routes, “Shiva”Campaigns, and other attack media against TARGET’s and expended over $30 million dollars in value, as quantified by The ATTACKERS partner:Google, in placing the attack material in front of 7.5 billion people on the planet for the rest of TARGET’s lifetime. No person couldsurvive such an attack and in the case of TARGET’s, lives were destroyed and multiple companies invested into by TARGET’s, which TheATTACKERS made over $50B off of the copies of, were destroyed because they competed with The ATTACKERS.
The TARGET’s are informed and believe, and based on that information andbelief allege that at all times mentioned in the within Complaint, all The ATTACKERS were the agents, owners and employees of theiraffiliated insiders and, in doing the things alleged in this Complaint, were acting within the course and scope of such agency andemployment.
As to any corporate employer specifically named, or named as a “DOE”herein, the TARGET’s are informed and believe and therefore allege that any act, conduct, course of conduct or omission, alleged hereinto have been undertaken with sufficient, malice, fraud and oppression to justify an award of punitive damages, was, in fact, completed withthe advance knowledge and conscious disregard, authorization, or ratification of and by an officer, director, or managing agent ofsuch corporation. The Statute of Limitations and time bar on this case has not expired. TARGET’s only became aware of all of the facts recently due to the FBI, Congressional andhacker-exposed investigation data on The ATTACKERS operating and receiving cash, rewards and assets from an illegal and illicit set ofpolitical slush-funds established to compensate them for financing political campaigns. The Sony, Clinton, DNC, HSBC, Panama Papers andother hacks and publication of all of the relevant files and the Congressional investigation of illicit activities and the continuingissuance of federal documents to TARGET’s confirming TARGET’s intellectual property areall vastly WITHIN the statutes oflimitations to allow this case to proceed to Jury Trial. TARGET’s has had a long, ongoing and high-level interaction with Defendant in boththe work effort and the monetization and collection effort. TARGET’s has been continually interactive with Defendant in order to try tocollect his money. Attacks and interference with TARGET’s has occurred as recently as this week by The ATTACKERS. The TARGET’s,whose multiple businesses ventures had already suffered significant damage as the result of the online attacks of the The ATTACKERS,contacted renowned experts, and especially Search Engine Optimization and forensic internet technology (IT) experts, to clear and clean theinternet of the false, defamatory, misleading and manufactured information belittling the TARGET’s, attacking them and discreditingtheir reputation as an inventor, product developer and project director from their websites.
None of the technology experts hired by the TARGET’s, at substantialexpense, were successful in their attempts to clear, manage or even modify the false, defamatory, misleading and
manufactured information belittling the TARGET’s, attacking him and discreditingtheir reputation as an inventor, product developer and project director which only The ATTACKERS, the controlling entity of theinternet, refused to remove. In fact, those experts were able to even more deeply confirm, via technical forensic internet analysis andcriminology technology examination techniques that The ATTACKERS was rigging internet search results for its own purposes and anti-trustgoals.
All efforts, including efforts to suppress or de-rank the results of aname search for “TARGET’s” failed, and even though tests on other brands and names, for other unrelated parties did achieve balance,the SEO and IT tests clearly proved that The ATTACKERS was consciously, manually, maliciously and intentionally rigging itssearch engine and adjacent results in order to “mood manipulate” an attack on TARGET’s.
In fact, the experts and all of them, instead, informed the TARGET’s,that, not only had The ATTACKERS locked the false, defamatory, misleading and manufactured information belittling the
TARGET’s, attacking them and discrediting their reputation as an inventor,project developer and project director into its search engine so that the information could never be cleared, managed or even modified, TheATTACKERS had assigned the false, defamatory, misleading and manufactured information belittling the TARGET’s, attacking them anddiscrediting their reputation as an inventor, project developer and project director “PR8” algorithmic internet search engine codingembedded in the internet information-set programmed into Defendantsinternet architecture. [See, Information received from oneof over 30 IT, forensic network investigators and forensic SEO test analysts, a true and correct copy of which is attached hereto in theExhibits.]
Per the many world-wide search engine results forensic analysis expertsTARGET hired – They had never seen search engines results that were locked so maliciously, manually and unmovably into Google’s andYouTube’s search results. “It was as if the CIA, or Larry Page himself, was doing this”, said one. TARGET placed associates insideof Google and, among other things, acquired bank records proving Google and the attackers were exchanging millions of dollar with eachother.
TARGET even went to the effort of placing nearly a thousand virtual forensictest servers around the globe, using empty space on third-party existing servers owned by hundreds of other people, in order tomonitor and metricize the manipulations of search results of examples of the
TARGET’s name in comparison to the manipulations for PR hype for The ATTACKERSfinancial partners, for example: the occurrence of the phrase ”Elon Musk”, The ATTACKERS business partner and beneficiary, over a fiveyear period. The EU, China, Russia, and numerous research groups (ie:
http://www.politico.com/magazine/story/2015/08/how-google-could-rig-the-2016-election-121548 By Robert Epstein ) have validated these forensic studies of TheATTACKERS architect-ed character assassination and partner hype system .
The “PR8” codes are hidden codes within the The ATTACKERS softwareand internet architecture which profess to state that a link is a “fact” or is an authoritative factual document per The ATTACKERSresearch. By placing “PR8” codes in the defamatory links that The ATTACKERS was manipulating about TARGET’s, The ATTACKERS was seekingto tell the world that the links pointed to “Facts” and not “Opinions”. The ATTACKERS embedded many covert codes in theirarchitecture which marketing the material in the attack links and video as “facts” according to The ATTACKERS.
The “PR8” codes are a set of codes assigned and programmed into theinternet, by the The ATTACKERS to matters it designates as dependable and true, thereby attributing primary status as the most TheATTACKERS is known to have provided tens of millions of dollars to this tabloid chain per The ATTACKERS financial staff, SEC filings anddisclosures in other legal cases.
TARGET also used CIA technology call “Steganography” to embed text-basedmessages and codes into photos and videos in order track Google and YouTube’s global impression manipulations and create a significantand important link to be viewed by online researchers regarding the subject of their search.
The ATTACKERS were fully aware that all of the information in the attackarticles against TARGET’s was false,The ATTACKERS promo ted these attacks as vindictive vendetta-like retribution against TARGET.
At all times The ATTACKERS maintained it had no subjective control orinput into the rankings of links obtained by online researchers as the result of a search on its search engines and that its searchengine algorithms and the functions of its media assets were entirely “arbitrary” according to the owners and founders of TheATTACKERS.
In or about April 15, 2015, The European Union Commission took directaim at The ATTACKERS charging the their Internet-search giant with skewing and rigging search engine results in order to damage thosewho competed with The ATTACKERS business and ideological interests.
In those proceedings, although The ATTACKERS continued to maintain thatit has no subjective control or input into the rankings of links obtained by online researchers as the result of a search
on its search engines and that its staff had no ability to reset,target, mood manipulate, arrange adjacent text or links, up-rank, down-rank or otherwise engage in human input which would changealgorithm, search results, perceptions or subliminal perspectives of consumers, voters, or any other class of users of the worldwide web,also known as The Internet, the court, in accord with evidence submitted, determined that The ATTACKERS, does in fact have and does in fact exercise, subjective control over theresults of information revealed by searches on its search engine.
The ATTACKERS has a variety of such hidden codes and has various internalnames for such codes besides, and in addition to, “PR8”. The ATTACKERS has been proven to use these fact vs. fiction
rankings to affect elections, competitors rankings, ie: removing the company:NEXTAG from competing with The ATTACKERS on-line; or removing political candidates from superior internet exposure and it isbelieved by investigators and journalists, that The ATTACKERS are being protected
from criminal prosecution by public officials who The ATTACKERS havecompensated with un-reported campaign funding. As a result of receiving this information, the TARGET’s became convinced of thestrength and veracity of their original opinion that the The ATTACKERS, had, in fact posted the false, defamatory, misleading andmanufactured information belittling the TARGET’s, attacking them and discrediting TARGET’s reputation as inventor, project developer andproject designer had been intentionally designed, published, orchestrated and posted by them in retaliation to the true testimonyprovided by the TARGET’s, to the Government Office of Accountability of the United States in May of 2005, and to the Securities andExchange Commission, The Federal Bureau of Investigation, The United States Senate Ethics Committeeand other investigating parties, andhad been disseminated maliciously and intentionally by them in an effort to do damage to their reputation and to their businessprospects and to cause him severe and irremediable emotional distress. In fact, the TARGET’s, has suffered significant andirremediable damage to their reputation and to their financial and business interests. As a natural result of this damage, as intendedby the
The ATTACKERS, Plaintiffs has also suffered severe and irremediableemotional distress.
To this day, despite the age of the false, defamatory, misleading andmanufactured information belittling the TARGET’s, attacking him and discrediting their reputation as an inventor, project developer andproject director, in the event any online researcher searches for information regarding the TARGET’s, the same information appears atthe top of any list of resulting links.
In addition, due to their control of all major internet databaseinterfaces, The ATTACKERS have helped to load negative information about TARGET’s on every major HR and employment database thatTARGET’s might be searched on, thus denying TARGET’s all reasonable rights to income around the globe by linking every internal job,hiring, recruiter, employment, consulting, contracting or other revenue engagement opportunity for TARGET’s back to false “redflag” or negative false background data which is designed to prevent TARGET from future income in retribution for TARGET’sassistance to federal investigators.
HARM #7: The ATTACKERS USED FACTORY-PROCESSED SOCIAL MEDIA ATTACKS AGAINST THEIR TARGETS:
In the book: “ATTACKED”, the Court will see the CIA, FSB and MI6 tactics and techniques that are trained and practiced, illicitly, by political officials. Social networking sites including MeetUp, Match, Facebook, etc. and all other IAC-owned, or similar, sites (IAC is managed by Hillary Clinton’s daughter, whose Mother knew TARGET’s) have had their profiles, texts, and inter-member communications, since those companies were started, hacked or purchased. The financiers of almost everyone of these sites are also the financiers of the suspects. The attack service providers use Palantir, Acronym, In-Q-Tel financed data analysis software to analyze every activity in those services in order to find honey-trap, blackmail and social conflict exploitation opportunities. Your social life will, essentially, end. Every photo on every social site is cross checked with every other photo on the internet in order to cull your Facebook, Linkedin, Snapchat and other social media together to create a total manipulation profile data file on you. New contacts on these sites were contacted by the attackers and told to “avoid” the TARGET’s in order to damage TARGET’s. These attacks were all documented and operated against TARGET as detailed in the EXHIBITS and evidence repositories. The ATTACKERS bought these services from Eastern Bloc nations, China and South America. “The Agency”, in Russia does much of this work. They are hard at work, even as recently as today according to the CIA, pushing a “positive spin” on Russia’s invasion of the Ukraine based on Hunter Biden’s computer leaks.
HARM #8: GOVERNMENT OFFICIALS CAUSED SSA AND HUD BENEFITS BLOCKADES AND MANIPULATIONS AS REPRISAL AGAINST TARGET:
Social Security, SSI, SDI, Disability and other earned benefits were stone-walled. Applications for benefits for the TARGET’s were intentionally “lost” like a “Lois Lerner hard drive”. Files in the application process “disappeared”. A U.S. Senator ordered TARGET’s benefits to “never be approved” even though TARGET’s worked 60 hour+ weeks for decades in service to their nation and their community. A SSA official in the local SSA office, who had a devout expressed hatred against one United States President ordered a benefits blockade against TARGET’s because he found out that TARGET’s ex-lawyer now worked in the White House. Forensic evidence and backgrounders on every person who worked on, or had access to, Applicants files, records, benefits decisions and related data sets shows that a number of those employees and contractors were members, financiers, web promoters or supporters of ANTIFA anarchy groups or KKK or Proud Boys related political activist-type groups. In San Francisco and Marin Counties SSA offices, in employees workspaces and on their Facebook and MySpace sites, many employees proudly display pictures of themselves wearing their pink “pussy hats”, black riot gear and sporting political tattoos. FBI records and IG investigations show that SSA has the highest percentage of political activist employees of any federal agency. Such persons are inclined to become drunk with power when allowed access to the trillions of dollars of government technology on the SSA file and decisions systems. A number of these persons have worked for, or with, U.S. Senators and other politicians who targeted Applicant in political reprisal. At least 3 persons in the San Francisco SSA office, at least 2 persons in the San Mateo SSA office and at least 2 persons in Marin SSA office are known to have engaged in such actions. Applicants funding and benefits were manipulated, so as to harm Applicant, as political reprisal as vendetta for his provision of testimony to federal investigators in a trillion dollar political corruption matter involving famous political figures featured in global news coverage. A vast number of agency abuse cases and lawsuits are now on public record in the Inspector General’s offices and federal courts. It is an indisputable fact that some government agencies run “hit-jobs” on citizens on orders from certain corrupt politicians.
These actions are felony violations of the law. Federal and State Agencies including SSA, FEC, GOVT, HHS, VA, CIA, HUD, SA, SEC, FBI, DOJ and many others, have been charged, and found guilty, in these crimes against citizens. In the Congressional investigation published by the United States Congress in review of the U.S. Department of Energy LGP/ATVM programs, it is clearly proven that the U.S. Department of Energy was used as a slush-fund by some GOVT executives in order to pay off campaign financiers by attacking and sabotaging their competitors. The GOVT Paducah Gaseous Diffusion Plant under contracts with The U.S. Government and the government-owned U.S. Enrichment Corp paid $5M whistle-blower awards to those whistle-blowers who were attacked, using government agency resources, for reporting a crime. Dept. of Energy Hanford URS has agreed to settle a lawsuit brought by former employee Walter Tamosaitis for $4.1 million.
The settlement in the whistle-blower case comes almost one year before the case was set for a jury trial in federal court in Richland and compensates Tamosaitis for attacks against him, by GOVT officials, in retribution for reporting a crime. VA officials attacked hundreds of citizens who reported corruption, ie: https://www.thenewamerican.com/usnews/health-care/item/18610-va-whistleblowers-facing-retribution. As shown in this report: https://www.pogo.org/analysis/2018/08/new-report-confirms-whistleblower-retaliation-is-alive-and-well-at-department-of-veterans-affairs/, Agencies attack often and harshly. CIA and NSA executives have been widely shown to use spy tools to attack domestic citizens they don’t like, ie: https://www.dailymail.co.uk/news/article-2435011/NSA-employees-used-phone-tapping-tools-spy-girlfriends-cheating-husbands.html , and hundreds of other news links that can be provided. Elon Musk and Tesla, as well as Eric Schmidt and Larry Page at Google, have been proven to use the CIA group: IN-Q-TEL, to run government sponsored/financed attacks on business competitors. In Civil Action No. 1:13-cv-00777-RBW GOVERNMENT AGENCIES WERE CAUGHT BEING USED FOR ATTACKS AGAINST CITIZENS AND PUNISHED IN THE COURT AND THE MEDIA! The IRS, and hordes of other government agencies have been caught and proven, IN COURT, to target and attack people for presumed political differences.
Why should we assume that the Social Security Administration is not ALSO doing this too to harm citizens who speak out? The Lois Lerner IRS attacks took many years to resolve. In an unprecedented victorious conclusion to a four year-long legal battle against the IRS, the bureaucratic agency admitted in federal court that it wrongfully targeted citizens, during the Obama Administration, because of their political viewpoints and issued an apology to those people for doing so. In addition, the IRS is consenting to a court order that would prohibit it from ever engaging in this form of unconstitutional discrimination in the future. In a proposed Consent Order filed with the Court, the IRS has apologized for its treatment of U.S. citizens including organizations from 20 states that applied for 501(c)(3) and (c)(4) tax-exempt status with the IRS between 2009 and 2012 — during the tax-exempt determinations process. Crucially, following years of denial by the IRS and blame-shifting by IRS officials, the agency now expressly admits that its treatment of our clients was wrong and a total violation of our Democracy. As set forth in the proposed Order: “The IRS admits that its treatment of TARGET’s during the tax-exempt determinations process, including screening their applications based on their names or policy positions, subjecting those applications to heightened scrutiny and inordinate delays, and demanding of some TARGET’s’ information that TIGTA determined was unnecessary to the agency’s determination of their tax-exempt status, was wrong.
For such treatment, the IRS expresses its sincere apology.” Throughout litigation of this case, activists have remained committed to protecting the rights of the public who faced unlawful and discriminatory action by the IRS and other agencies. The objective from the very beginning has been to hold agencies accountable for corrupt practices.
This Consent Order represents a historic victory for the public and sends the unequivocal message that a government agency’s targeting of citizens organizations, or any organization, on the basis of political viewpoints, will never be tolerated and that revenge will be swift and vast. The Order will put an end, once and for all, to the abhorrent practices utilized against citizens, as the agreement includes the IRS’s express acknowledgment of – and apology for – its wrongful treatment of the public. While this agreement is designed to prevent any such practices from occurring again, rest assured that all public interest lawyers will remain vigilant to ensure that the IRS, SSA, DOJ or SEC does not resort to such tactics in the future. Per detailed reports, in March of 2012 lawyers began being contacted by literally dozens of citizens and groups who were being harassed by the Obama IRS after submitting applications for tax-exempt status. Their tax-exempt applications were held up for years (over seven years in some cases), and they began receiving obtrusive and unconstitutional requests for donor and member information. That began a now more than five and a half year fight with the burgeoning bureaucracy at the IRS. Then on May 10, 2013, Lois Lerner, the then head of the IRS Tax Exempt Organizations Division, publicly implicated the IRS in one of the worst political targeting scandals of the century.
This is an extraordinary victory against government agency abuse. It sends a powerful warning to the deep state bureaucracy that it will not be allowed to violate the Constitution in order to silence and shut down the whistle-blowers. In addition to the IRS’s admissions of and apology for its wrongful conduct, the Consent Order would specifically award TARGET’s the following: – A declaration by the Court that it is wrong to apply the United States tax code to any tax-exempt applicant or entity based solely on such entity’s name, any lawful positions it espouses on any issues, or its associations or perceived associations with a particular political movement, position or viewpoint; – A declaration by the Court that any action or inaction taken by the IRS must be applied evenhandedly and not based solely on a tax-exempt applicant or entity’s name, political viewpoint, or associations or perceived associations with a particular political movement, position or viewpoint; and – A declaration by the Court that discrimination on the basis of political viewpoint in administering the United States tax code violates fundamental First Amendment rights.
Disparate treatment of taxpayers based solely on the taxpayers’ names, any lawful positions the taxpayers espouse on any issues, or the taxpayers’ associations or perceived associations with a particular political movement, position or viewpoint is unlawful. In the Order, the IRS has also agreed that (unless expressly required by law) certain actions against the TARGET’s– i.e. the sharing, dissemination, or other use of information unnecessarily obtained by the IRS during the determinations process (such as donor names, the names of volunteers, political affiliations of an organization’s officers, etc.) – would be unlawful. In addition, the IRS promises not to take any retaliatory action against our clients for exposing the targeting scheme. Finally, and of crucial significance, the IRS admits it targeted persons and groups based on their viewpoints (i.e., “policy positions”) and that such viewpoint discrimination violates fundamental First Amendment rights. This is the first time the IRS has admitted that its targeting scheme was not just “inappropriate” – as TIGTA found – but, as alleged, blatantly unconstitutional. To ensure consistency and uniformity within the agency’s operations going forward, the IRS is required, pursuant to the Order, to inform all employees within the Exempt Organizations Division, as well as the Commissioners and Deputy Commissioners within other divisions, of the Order’s terms. This Order not only validates allegations about their treatment at the hands of the corrupt Obama-era IRS but also provides important assurances to the American public that the agency understands its obligation to refrain from further such discriminatory conduct. As Attorney General Sessions acknowledged in this regard, “[t]here is no excuse for [the IRS’s] conduct,” as it is “without question” that the First Amendment prohibits the conduct that occurred here, i.e., subjecting American citizens to disparate treatment “based solely on their viewpoint or ideology.” Sessions further confirmed his Department’s commitment to ensuring that the “abuse of power” in which the IRS engaged here “will not be tolerated.” It is impossible to overstate the importance of this victory.
This marks a years-long fight for justice in defense of the constitutional rights of the public. This is an extraordinary victory against abuse of power and corruption. It sends a powerful warning to the deep state bureaucracy that it will not be allowed to violate the Constitution and manipulate the IRS, SSA and other agencies in order to silence and shut down those who speak out about political corruption crimes. In the wake of Wisconsin Watchdog’s investigation into SSA staff allegations of incompetence, misconduct, and retaliation in Social Security disability appeals offices, several employees have taken their complaints to a Senate committee led by Wisconsin Sen. Ron Johnson.
An official with knowledge of the complaints said the Senate Homeland Security and Governmental Affairs Committee, chaired by the Oshkosh Republican, has received emails and other contacts from “certain people” inside the Social Security Administration’s Office of Disability Adjudication and Review. The initial complaints came from an employee inside the Milwaukee office following Wisconsin Watchdog’s opening investigative report that found some claimants waiting more than 1,000 days for an appeals decision on their disability benefits claim. Following Wednesday’s story of a whistle-blower in the Madison ODAR office, the committee has received more specific complaints about retaliation against employees, the source said. Committee staff members sent the latest Watchdog piece to SSA administrators hoping they will “cooperate,” the source said. To date, the agency has been less than cooperative. “This is an ongoing process, and they are not always as forthcoming as we’d like them to be,” the source said. “Hopefully with your continued reporting, this is an issue they can’t duck.” A Senate committee member said officials there are working with the Office of Special Counsel on “multiple whistle-blower retaliation claims.” The committee continues to request information from the SSA. The whistle-blower in the Madison office claims management retaliated against her after she was called to testify in a misconduct case.
The incident involved “inappropriate behavior” by an administrative law judge, she said. “They are so corrupt. It’s absolutely horrible,” said the woman, a lead case technician in the Madison Office of Disability Adjudication and Review. She spoke on condition of anonymity, fearing more retribution from her supervisors. While she said recounting her particular experiences will more than likely betray her identity anyway, the ODAR case worker insisted she has had enough. “I’m at point where they don’t care about me, I don’t see why I’m protecting them. This is my last resort,” she said. “I want to do my work without fear of retaliation.” She said she has contacted the Senate committee. “I forwarded my information to them and I got an email back from them. See these reports:
-
WSJ: 131 Federal Judges Broke Law by Hearing Cases Where They Had Financial Interest...
https://www.wsj.com/articles/hidden-interest-judges-financial-conflicts-graphic-11632834079
-
They said people are coming out of the woodwork with their complaints (about ODAR) following your story,” the whistle-blower said. Ronald Klym, a long-time senior legal assistant in the Milwaukee ODAR office, alleges he has been retaliated against by supervisors for going public with his charges of incompetence and misconduct in the agency. The federal employee, who has worked for SSA for 16 years, provided Wisconsin Watchdog with documents showing extremely long wait times for claimants appealing their denied applications for benefits. Doug Nguyen, SSA regional spokesman, in a previous story said the agency acknowledges that Milwaukee ODAR has a “high average processing time for disability appeal hearings, and we are working to address the issue.” Beyond the delays is what Klym calls the “shell game,” the wholesale transferring of cases to other parts of the country by administrators to make the Milwaukee office’s numbers look better than they are. The Madison office whistle-blower confirmed Klym’s allegations, saying at one point she saw 2,000 cases from the Milwaukee office handed off to the Oak Brook operation. There are over 10,000 SSA disability manipulation charges against SSA executives and staff.
HARM #9: The ATTACKERS USED BLACKLISTING AGAINST TARGET:
ie: The U.S. Stops Silicon Valley’s ‘No Poaching’ Deals. . . a …
![]() https://www.aol.com › 2010 › 09 › 26 ›doj-stops-silicon-valleys-no-poaching-deals-a-few-years-t
https://www.aol.com › 2010 › 09 › 26 ›doj-stops-silicon-valleys-no-poaching-deals-a-few-years-t
DOJ Stops Silicon Valley’s ‘No Poaching’ Deals. … But anyone on the ground in Silicon Valley knows that a full-blown war for talent is under way, with checkbooks blazin. Government officials and tech oligarchs contacted members of the National Venture Capital association (NVCA) andcreated national “black-lists” to blockade TARGET’s from receiving investor funding. This was also confirmed in a widelypublished disclosure by Tesla Motors Daryl Siry and in published testimony. If Silicon Valley political campaign finance oligarchsblack-list you (see the “AngelGate” Scandal and the “High Tech No Poaching Class Action Lawsuit” cases) you will never getinvestor funding again.
HARM #10: The ATTACKERS ORDERED FOIA OBFUSCATION OF TARGET’S FOIA AND STILL HAVE NOTRESPONDED TO MANY FOR YEARS BECAUSE THEY SHAME The ATTACKERS:
Federal FOIA requests were hidden, frozen, stone-walled, delayed, lied about and only partially responded to in order to seek to hide information and run cover-ups. In once instance, even though GOVT FOIA staff had the requested FOIA files in their top desk drawers, they delayed handing the FOIA copies over for nearly a decade in order to run a cover-up.
HARM #11: The ATTACKERS ENGAGED IN ARBITRARY DEADLINE MANIPULATION:
Crony state and federal officials play an endless game of Catch-22 by arbitrarily determining that deadlines had passed that they, the government officials, had stonewalled and obfuscated applications for, in order to force these deadlines that they set, to appear to be missed. DOE’s PATTERN OF SUPPORTING WHISTLEBLOWER RETALIATION:
In case # 2:11-cv-05157-LRS ECF; it was proven that when a DOE contractoremployee files a complaint alleging whistleblower retaliation, it is the practice of the DOE to align itself with the contractor and toassert attorney client privilege. For example, in an eleven-TARGET whistleblower retaliation case litigated against Fluor FederalServices, Inc., DOE attorney Robert Carosino refused to disclose evidence relating to meetings between DOE and the offendingcontractors claiming attorney client privilege because DOE and the contractor share a common interest in the litigation. A13-18. Thispractice prevents the DOE from effective oversight of contractor retaliation and creates a culture of fear among the Hanfordworkforce.
Upon Dr. Tamosaitis filing a whistleblower complaint with the DOL in 2010, theDOE, Bechtel and URS asserted attorney client privilege as to their discussions concerning Dr. Tamosaitis’ claim owing to their commoninterest. This fact has been verified by the sworn testimony of Jean Dunkirk in her deposition, which was taken in connection with thestate claim (transcript available).
There is a practice of DOE managers, and most other government agency managers,supporting retaliation against contractor employees who oppose unsafe practices. For example, in 2008, then URS Chief Nuclear Engineer andManager of Nuclear Safety Donna Busche, was terminated from her position at the Waste Isolation Pilot Plant in Carlsbad, New Mexico,with the approval of DOE officials, after she refused to rescind a Technical Safety Violation report that she had filed regarding theimproper handling of a drum from Hanford that contained transuranic waste.
In 2009, Ms. Busche was reassigned to the WTP as Manager of Environmental andNuclear Safety. A155-6. In October 2010, she was berated by Ines Triay, the DOE EM1, after giving truthful testimony at a hearing a bythe DNFSB. A198-199. At a post-hearing meeting with Ms. Triay and numerous URS managers, Triay said, “If your intent was to pisspeople off, you did a very good job. You pissed people off.” A199. Ms. Bushe has suffered retaliation since then,
which has been compounded by her having been a witness in this case. 2.60 In2010, DOE WTP Federal Project Director Dale Knudson submitted a sworn statement to the DOL indicating that he “did not direct BNI or URSto take any specific actions with regards to Dr. Tamosaitis.” A14. In fact, Knudson was directly involved in the decision to terminateDr. Tamosaitis from the WTP. A114. He also participated in the decision that Dr. Tamosaitis not be returned to the WTP after
hearing that Dr. Tamosaitis was a whistleblower. Throughout the Tamosaitisretaliation, DOE managers supported Bechtel and URS efforts to stop necessary design changes to the WTP so that artificial deadlinescould be met, and did nothing to protect, or supported, retaliation by
contractors against employees who opposed those improper decisions.
PLACING A CONTRACTOR EMPLOYEE INTO AN OVERSIGHT POSTION
CREATED AN INHERENT CONELICT OF INTEREST: In 2010, DOE placed PNNL manger DaleKnudson into the position of DOE Federal Project Director of the WTP. A52-3. This created an inherent conflict of interest in that acontractor employee who, on information and belief, is not
motivated by government service and placing the public interest before profit,is placed in a temporary position, overseeing the work of other contractors. On information and belief, after about two years,Knudson will return to his position at PNNL or to another position in the private sector.
HARM #12: POLITICAL POISONING & TOXIC EXPOSURE BY The ATTACKERS HARMED TARGET:
TARGET’s were found to be strangely poisoned, not unlike the Alexander Litvenko case, The Salisbury Case and hundreds of other political poisoning cases. Heavy metals and toxic materials were found right after TARGET’s work with The U.S. Government weapons and energy facilities. Many wonder if TARGET’s was intentionally exposed to toxins in retribution for their testimony. The federal MSDS documents clearly show that a number of TARGET’s were exposed to deadly compounds and radiations, via GOVT, without being provided with proper HazMat suits which GOVT officials knew were required. TARGET was awarded an exceptional number of issued patents on the energy technologies he had developed for the Dept of Energy. 3rd Party outside legal valuation experts appriased the value of these patents at over $200,000.000.00. The patents, clearly visible in full detail, on the US Patent office website, list many of the chemicals and compounds TARGET was working with without adequate hazmat resources of Sandia, Argonne or other National Labs safety oversight.
HARM #13: WORKPLACE SABOTAGE AND OBSTRUCTION OF TARGET’S RIGHT TO WORK:
TARGET’s contacts at ARTECH and KAISER PERMANENTE were called, and faxed, and ordered to fire target TARGET’s from their places of employment, in the middle of the day, with no notice, as a retribution tactic.
HARM #14: MEDIA ASSASSINATION PROGRAMS WERE CONTRACTED BY The ATTACKERS TO HARM TARGET:
On orders from Obama White House officials Google, YouTube, Gawker Media and Gizmodo Media produced attack articles. Google locked these contrived attack articles from the Nicholas Guido Denton tabloid empire on the top line, of the front page of all Google searches for a decade in front of 7.5 billion people, around the world. This attack-type uses over $40 million dollars in server farms, production costs and internet rigging. The forensic data acquired from tracking some of these attacks proves that Google rigged these attacks against TARGET’s on the internet and that all of Google’s “impressions” are manually controlled by Google’s executives who are also the main financiers and policy directors of the Obama Administration. This data was provided to the European Union for it’s ongoing prosecution of Google’s political manipulation of public perceptions. Hired attackers Nicholas Guido Denton, John Herman, Adrian Covert, Ian Fette, Patrick George, Gabrielle Darbyshire and John Cook have been referred to the FBI for surveillance, tracking and interview relative to the command, control and compensation for those attacks.
HARM #15: COMMERCIAL EMPLOYMENT DATABASE POISONING AND RED-FLAGGING OF TARGET’S HRDATABASE REFERENCES WERE CREATED TO HARM TARGET’S INCOME POTENTIAL:
TARGET’s HR and employment records, on Taleo, Palantir and EVERY recruiting and hiring database, was embedded with negative keywords and “flags” in order to prevent the TARGET’s from ever gaining future employment.
HARM #16: ATTEMPTS ON THE LIVES OF WHISTLE-BLOWERS BY THE ATTACKERS WERE MEANT TO FRIGHTEN TARGET:
Gary D. Conley, Seth Rich, Rajeev Motwani who TARGET’s knew, and many other whistle-blowers in these matters, turned up dead under strange circumstances. TARGET’s has received ongoing death threats for his help to federal investigations in the larger organized crime investigation relative to this matter. See the list of over 120 dead victims, lower down in this document, 1/3 of whom worked with TARGET’s and were threatened in advance of their deaths.
HARM #17: THE ATTACKERS ENGAGED IN REVENUE BLOCKADES AND INTERNET INCOME RE-DIRECTION TOMINIMIZE TARGET RESOURCES SO HE COULD NOT FIGHT BACK:
Paypal, and other on-line payments for on-line sales by TARGET’s are de-platformed, delayed, hidden, or re-directed in order to terminate income potential for target who competed with the attackers interests and holdings. This further denied TARGET’s income. As a test, TARGET’s built an online store with hundreds of thousands of products and marketed it globally. Trackers, placed by TARGET’s technicians, on servers, discovered that Paypal and an outside “Virgina-based system” were DNS and payment re-directed all traffic away from the store so that TARGET’s received no traffic and no income. In DNS redirection, “website spoofing” sends target TARGET’s websites to dead ends where no sales orders or customer inquiries actually get back to the target. These internet revenue activity manipulations are conducted using outside covert servers operated by the attackers and revealed in the Snowden Leaks. All commercial storefronts and on-line sales attempts by target TARGET’s, had their sites hidden, or search engine de-linked by a massively resourced facility located in Virginia, Texas or Palo Alto, California in order to terminate revenue potentials for the TARGET’s.
HARM #18: The ATTACKERS USED THE TROLL FARM DEPLOYMENTS AGAINST TARGET THAT THEY USE AGAINST PRESIDENTIAL OPPOSITION CANDIDATES:
Contracted trolls, shills, botnets and synth-blog deployments are deployed to place defamatory statements and disinformation about TARGET’s in front of 7.5 billion people around the world on the internet in order to seek to damage their federal testimony credibility by a massively resourced facility. Some of these troll farms were uncovered in Russia, Ukraine, Israel and Brazil. Renown author Farrow writes about this technique in his book: “Catch And Kill”. FUSION GPS, BLACK CUBE and MEDIA MATTERS Brand, Reputation and Credibiity “KILL” CONTRACTS were executed by The ATTACKERS targeting TARGET. Campaign finance dirty tricks contractors were hired by campaign financiers to attack the friends and family members of the target TARGET’s in order to create low morale for the target TARGET’s psyche and motivation. The Fusion GPS Scandal implicates Gawker and Gizmodo Media In Pay-To-Publish Scheme. A court filing from the U.S. district court for DC shows that Fusion GPS paid several journalist to run hit jobs on political adversaries and was paid by a media organization. All of those players were attackers hired to attack TARGET. FBI interviews can verify this.
HARM #19: MANUAL SEARCH ENGINE LOCK-IN ATTACKS WERE CONTRACTED FROM GOOGLE AND YOUTUBE, BY TheATTACKERS, TO HARM TARGET:
In one case covert political partner: Google, transferred large sums of cash to dirty tricks contractors and then manually locked the media portion of the attacks into the top lines of the top pages of all Google searches globally, for years, with hidden embedded codes in the links and web-pages which multiplied the attacks on TARGET’s by many magnitudes.
HARM #20: THE U.S. PATENT OFFICE MANIPULATION WAS USED TO BLOCKADE REVENUE FROM TARGET’SINVENTIONS:
Facebook and Google executives sit on the boards and run The United States Patent Office. That fact alone says it all. For details see https://www.usinventor.org
Covert Cartel financier: Google, placed Google’s lawyer: Michelle Lee, in charge of the U.S. Patent Office and she, in turn, stacked all of the U.S. Patent Office IPR and ALICE review boards and offices with Google-supporting employees in order to rig the U.S. Patent Office to protect Google from being prosecuted for the vast patent thefts that Google engages in. Google has hundreds of patent lawsuits for technology theft and a number of those lawsuits refer to Google’s operations as “Racketeering”, “Monopolistic Cartel” and “Government Coup-like” behaviors. Thousands of articles and investigations detail the fact that Google, “essentially” ran the Obama White House and provided over 80% of the key White House staff. A conflict-of-interest unlike any in American history. Google’s investors personally told TARGET’s they would “kill him”. Google and the Obama Administration were “the same entity”. TARGET’s testified in the review that got Michelle Lee terminated and uncovered a tactical political and social warfare group inside Google who were financed by Federal and State funds. For additional proof, SEE THE VIDEO at: The_Battle_to_Save_Inventing.m4v
Silicon Valley has taken over the U.S. Patent Office with lobbyists and influence payments. Per Randy Landreneau, the President the U.S. Inventor guild: “ Independence Day is that special time when we Americans remember and celebrate our country’s freedom. While it may mean different things to many people, suffice to say, it is the reason we are Free, we have Liberty. Founder, writer, statesman and inventor Benjamin Franklin wrote, “On Historical occasions, Questions of Right and Wrong, Justice and Injustice, will naturally arise.” Here, on this honored day, we take a quick look at Invention and our Independence. Towards the beginning of the Declaration of Independence, whose principal author was our eventual third president, Thomas Jefferson, the very purpose of our Founders’ quest was established. It is stated: “We hold these truths to be self-evident, that all men are created equal, that they are endowed by their Creator with certain unalienable Rights, that among these are Life, Liberty and the pursuit of Happiness.” These were men and women of incredible vision, of intense courage, and they succeeded in accomplishing their seemingly insurmountable task, rising up and defeating perhaps the most powerful global Empire of the time, Great Britain. The United States of America eventually became the beacon of hope and individual freedom around the world. People from virtually every land came to this country to seek the American Dream, which ideals include individual and property rights, religious freedom, liberty, equality and the opportunity for upward mobility, achieved through dedication and hard work. One of the reasons America became the world leader in nearly all categories is due, in no small part, to how our Founders recognized and encouraged invention and innovation. They understood what builders, creators and designers could mean to a small, fledgling country with such a noble purpose. After declaring our independence and fighting a long and bloody war to establish it, our Founders gathered once again in Philadelphia for the Constitutional Convention to form a government that would embody those ideals embodied in our Declaration of Independence. The Father of our Constitution and eventual fourth President, James Madison wrote, in Federalist 43 (January 23, 1788): “A power ‘to promote the progress of science and useful arts, by securing, for a limited time, to authors and inventors, the exclusive right to their respective writings and discoveries.’ “The utility of this power will scarcely be questioned. The copyright of authors has been solemnly adjudged, in Great Britain, to be a right of common law. The right to useful inventions seems with equal reason to belong to the inventors. The public good fully coincides in both cases with the claims of individuals. The States cannot separately make effectual provisions for either of the cases, and most of them have anticipated the decision of this point, by laws passed at the instance of Congress.” Thus, within our U.S. Constitution is that short item, located in Article I Section 8 as Clause 8: “To promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries.” That clause is, in reality, a significant and powerful part of the American Dream, allowing people from all walks of life who have a bright and useful idea to capitalize on their innovations and creations. For more than two centuries that which our Founders established for inventors and patent holders held true, for the most part. However, the biggest blow to true Independence for Inventors came with passage of the America Invents Act of 2011 (AIA). Due to ambiguous language and loopholes in that piece of legislation, multinational conglomerates and Big Tech have all but wiped out what our Founders had set up, which they hoped would endure – patent holder property rights. When any form of poor legislation is passed and enacted we are reminded of what Samuel Adams, Sons of Liberty founder and a leader of the Boston Tea Party, said; “The grand end of civil government, from the very nature of its institution, is for the support, protection, and defense of those very rights; the principal of which, as is before observed, are Life, Liberty, and Property.”
Indeed, Jefferson states it quite succinctly, “Our legislators are not sufficiently apprized of the rightful limits of their power; that their true office is to declare and enforce only our natural rights and duties, and to take none of them from us.” Madison adds to that, “A Government is instituted to protect property of every sort…This being the end of government, that alone is a just government, which impartially secures to every man, whatever is his own.” As we celebrate Independence Day, and all that our Founders provided for our great country, we at US Inventor are working to correct the wrongs and injustices that have befallen inventors, particularly since the AIA was enacted, by revitalizing the spirit of our Declaration of Independence (“…Life, Liberty and the pursuit of Happiness.”) through restoration of patent rights and protection as guaranteed in Article I Section 8 Clause 8 of our United States Constitution (“securing, for a limited time, to … inventors, the exclusive right to their respective … discoveries.”). We will not rest until the rights of inventors have been restored. We’re gaining ground, but our enemies are powerful. We need your help in forwarding our cause and becoming involved when it matters. This isn’t just for us, it’s for our children, our grandchildren, and the future existence of the American Dream.”
Silcon Valley oligarchs have spent billions of dollars to put their people inside the United States Patent Office and to manipulate patent rulings in order to harm WITNESS and his peers for the purposes of: 1.) cheating instead of competing by stealing technologies and not paying for them and, 2.) operating reprisal, vendetta, retaliation campaigns against competitors and political enemies. TARGET was awarded an exceptional number of issued patents on the energy technologies he had developed for the Dept of Energy. 3rd Party outside legal valuation experts appriased the value of these patents at over $200,000.000.00. By it’s actions, The U.S. Government made TARGET’s patents unusuable for monetization by causing black-listing of those patents with NVCA investors and by using online trolls to make the marketing for those patents close off. TARGET demands that the U.S. Government now purchase ALL of TARGET’s patents at fair market value to partially offset his loss.
HARM #21: HONEY-TRAPS WERE PLACED ON SOCIAL MEDIA SITES BY The ATTACKERS SPY OPERATIVES TO HARMTARGET:
“Honeytraps” and moles were employed by the attackers. In this tactic, people who covertly worked for the attackers were employed to approach the “target” in order to spy on and misdirect the subject. Match.com and other dating sites are owned by famous politicians and election campaign financier involved with Jeffrey Epstein and those sites were used to source girls for Epstein and Honey-traps to lure political adversaries.
HARM #22: A FAKE NEWS TABLOID EMPIRE WAS CREATED JUST FOR DEFAMATION ATTACKS, BY THE ATTACKERS, ANDUSED TO HARM TARGET:
Gawker Media, Gizmodo Media, Snopes, SPLC and other hired media assassins were retained to produce “hatchet job” character assassination articles about TARGET’s. Then those articles were faxed, mailed and emailed to Kaiser Permanente and investors with a note saying: “You don’t want to have anything to do with this person, do you..?” in order to get TARGET’s fired from their job and get TARGET’s loans or financing pulled. The attackers use their round one attack media, that they authored, to create a round two second wave attack designed to end TARGET’s life status via economic warfare. All of the other attack victims received between $100,000.00 to $75,000,000.00 but TARGET received ZERO DOLLARS because the Judge was friends with the The ATTACKERS.
HARM #23: HOUSING BLOCKADES WERE DEPLOYED BY The ATTACKERS TO HARM TARGET:
Mortgage and rental applications had red flags added to them in databases to prevent the targets from getting homes or apartments. HUD applications were manipulated or stalled from 2007 to today, as reprisal.
HARM #24: HACKING OF TARGET’s DEVICES OCCURRED ON ORDERS OF The ATTACKERS:
Krebs On Security, Wired, Ars Technica, The Wall Street Journal and most major IT publications have reported that hundreds of spy “back-doors” have been found on every Intel, AMD, Apple, Xfinity, Cisco, Microsoft, Juniper Networks motherboard, chip-set and hardware component set. This means that the attackers used a “key” code can open any of TARGET’s computer, server, router, cloud-network or other network connected device and read every file, photo, video, your calendar and email on devices at any time from any location on Earth. This has been widely reported on by Glenn Greenwald, Edward Snowden, Scahill, Cheryl K of CBS News and others. TARGET’s was hacked at least 10 times. In a number of instances, people, who TARGET’s had been communicating with online, were mysteriously contacted by a third party who sent them the Gizmodo attack article or phoned them with warnings to avoid TARGET’s. These kinds of Man-In-The-Middle interceptions would only have been possible from hacking and MITM surveillance tactics.
HARM #25: TECH INDUSTRY BLACK-LIST COORDINATION AGAINST TARGET HAD COMMAND-AND-CONTROL OUT OFThe ATTACKERS OFFICES:
McCarthy-Era “Black-lists” were created and employed against target TARGET’s who competed with Obama Administration executives and their campaign financiers to prevent them from getting funding and future employment. This White House process is known as “RatFucking”, a tactic that is documented in a variety of published reports and on Wikipedia. Using Gust, Google Docs, Dropbox and secret meetings, a black-list has been maintained to attack TARGET’s for whistle-blowing. TARGET has named specific individuals to this court and demanded that the Court request the FBI 302 reports on those individuals. Additional, TARGET demands the FINCEN financial mapping records for those Defendant parties. That data, cross referenced in the XKEYSCORE database, provides indisputable, fully incriminating, follow-the-money evidence about every single party mentioned in this complaint.
HARM #26: HUD AND USDA MORTGAGE RIGHTS BLOCKADES TO HARM TARGET HOUSING IN REPRISAL ASDIRECTED BY The ATTACKERS VIA THEIR ‘DIRTY TRICKS’ TEAM:
The housing rights of TARGET’s were stalled in reprisal. Public records show that tens of thousands of other TARGET’s were moved ahead of TARGET’s even though TARGET’s validation metrics exceeded those of almost every other TARGET’s. TARGET’s was “black-listed”.
-
Additional ‘dirty tricks’ efforts were used per:
https://www.justice-integrity.org/634-intelligence-agencies-use-social-media-for-dirty-tricks-propaganda-new-report -
https://www.salon.com/2011/02/11/threats_against_glenn_greenwald_wikileaks/
-
https://www.theguardian.com/commentisfree/2013/jun/24/surveillance-us-national-security
-
http://federal-report.com/public/The_Political_Reprisal_Vendetta_Playbook.pdf
-
https://www.cia.gov/library/readingroom/docs/CIA-RDP89-01258R000100010002-4.pdf
-
…and thousands of additional reports proving the attacker assertions.
TARGET is aware of the FBI procedure of the filing of FBI ‘302’ Reports on subjects.TARGET has, on multiple occasions, via the DC and SFO FBI offices, requested that the FBI interview, observe and track the attackers andconfirm the command and control communications authority authorizing, managing and financing their attacks and the paths of compensation ofthose attacks. The FBI has had the full capacity and resources to easily confirm who ordered and operated the attacks on TARGET via an interview and investigation of the The ATTACKERS hiredattackers, specifically Nicholas Guido Denton, John Herrman, Gabrial Darbyshire, Patrick George, JayCarney, Robert Gibbs, Adrian Covert, Eric Schmidt, Larry Page, Perkins Coie, John Cook, Elon Musk, The Secretary of Energy Jennifer Granholm, et. al; and those other parties listed within the main complaint..
The FBI ‘302’ reports on those attackers is hereby requested, and arequest for the Court to demand those reports is hereby requested for review by all parties concerned.
(G) Court ordered back payments from SSA from 2007 to today becausepublic officials ordered blockade of TARGET’s SSDI payments as political reprisal for whistle-blowing in 2007 as proven by InspectorGeneral and attached Exhibits:
TARGET hereby places a plea before the Court for the Court to order the Social Security Administration to pay TARGETback payments from SSA for SSDI from 2007 to today because, as proven in the Master Complaint, public officials, including White House staff and California Senators with intelligence agencyaccess to government ‘dirty tricks’ teams, ordered the blockade of TARGET’s SSDI payments as political reprisal for whistle-blowingin 2007 as proven by Inspector General and attached Exhibits in the Master Complaint. Some SSA officials now work for the charged The ATTACKERS. This illicit federal reprisal circumvention of TARGET’s income cost himhis house and all many of the damages listed, in detail, in the Master Complaint. It has been proven, in the evidence, that Senator’sPelosi, Harris, Reid, Feinstein, and other senior public officials regularly order hacking, data manipulation and de-funding ofpolitical whistle-blowers. Dianne Feinstein’s staffer: Daniel Jones, is world known as the ‘CIAMaster of Dirty Tricks’. In fact, TARGET and his peers, previously won federal lawsuits, asdetailed in the Master Complaint, proving that, “government agencies infected by corruption use their resources to put reprisalhit-jobs on citizens”. Any Senate aide can hack or manipulate SSA, DOE, HUD and other agencydecision files within minutes and order ANY citizen to have their funds cut-off with a single phone call. That happened in this case,as TARGET, and federal evidence has sworn, certified and verified as to the veracity of such dirty tricks operations within theGovernment. Senator’s staff and family cohabited with TARGET and revealed such tactics.
There are a vast number of other attack tactics. You can find those tacticslisted in the, now public, CIA manuals and British JTRIG manuals.
READ THE REPORT: THE CYBER ASSASSINS
One of 15 platforms with various interactions with the Election Integrity Partnership.
https://purl.stanford.edu/tr171zs0069
See page 12 for government and civil society stakeholders that could issue tickets to flag social media platforms and media content for suppression.
Tick Tock was a cooperating platform. See pages 12 and 17.
The Harvard Kennedy School Belfer Center’s Defending Digital Democracy Project (D3P) is a ticket issuing civil society stakeholder. See pg.12.
Here is the co-director of the Belfer Center addressing the SSCI with a discussion of the Defending Digital Democracy Project:
https://www.belfercenter.org/publication/defending-digital-democracy-four-corners-election-security
…”The Defending Digital Democracy Project, a bipartisan initiative I co-lead at Harvard’s Belfer Center along with Robby Mook and Matt Rhoades, is developing real-world, practical solutions to defend against cyber and information attacks. The team has breadth and depth of talent—including cybersecurity experts from government and the private sector, technologists and political operatives.”…
More on D3P and it’s principals:
…”The Belfer Center for Science and International Affairs at Harvard Kennedy School launched a new, bipartisan initiative today called the “Defending Digital Democracy” (DDD) Project. Co-led by the former campaign managers for Hillary Clinton and Mitt Romney and experts from the national security and technology communities, including Facebook and Google, the project aims to identify and recommend strategies, tools, and technology to protect democratic processes and systems from cyber and information attacks”…
…”Co-sponsored by two other Harvard Kennedy School entities – the Institute of Politics and the Shorenstein Center on Media, Politics, and Public Policy directed by Nicco Mele – the project will be run by Eric Rosenbach, Co-Director of the Belfer Center and former Assistant Secretary of Defense. Prior to his July 2015 appointment as Chief of Staff to Secretary of Defense Ash Carter, Rosenbach served as the Assistant Secretary of Defense for Homeland Defense and Global Security.
Rosenbach recruited Robby Mook, Hillary Clinton’s 2016 campaign manager, and Matt Rhoades, Mitt Romney’s 2012 campaign manager, to join DDD as Fellows and co-leaders.”…
…”The Project has enlisted Marc Elias of Perkins Cole and Ben Ginsberg of Jones Day, two of the top respective Democratic and Republican election lawyers in the country, to advise the project, along with a bipartisan senior advisory group made up of leaders in technology, cyber security, and national security, including:
Heather Adkins, Director, Information Security and Privacy – Google;
Dmitri Alperovich, Co-Founder and CTO – CrowdStrike;
Stuart Holliday, President and CEO – Meridian International Center; former United States Ambassador for Special Political Affairs at the United Nations;
Nicco Mele, Director, Shorenstein Center on Media, Politics, and Public Policy – Harvard Kennedy School;
Debora Plunkett, former Director – National Security Agency’s Information Assurance Directorate;
Suzanne E. Spaulding, former Under Secretary – National Protection and Programs Directorate (NPPD) at the Department of Homeland Security.
Alex Stamos, Chief Security Officer – Facebook.”…
Nearing the truth on the Biden Big Tech racket

It’s been more than two years since The Post published the first article on Hunter Biden’s laptop and for much of that time, the effort to reveal Joe Biden’s role in his son’s dirty deals seemed stalled or even hopeless.
Democratic propaganda outlets circled the wagons around the president they helped elect and never asked him or the White House if Biden is “the big guy” slated to get a secret 10% cut in his son’s deal with a Chinese conglomerate.
Similarly, social media platforms continued to restrict users who didn’t follow the party line that Democrats are the good guys and everybody else is ignorant or evil. Whatever the topic, from COVID to corruption to the transgender agenda, the pattern was gratingly consistent.
Feeling it could always count on this protection, the Biden White House was free to ignore any new evidence against the president. It was proven right when some news outlets that belatedly concluded the laptop was authentic, including the New York Times and the Washington Post, failed to take the logical next step of exploring the evidence that the president shared in the profits of his son’s schemes.
Meanwhile, Attorney General Merrick Garland felt safe enough with Democrats’ control of Congress that he could sit on the 4-year-old probe of the president’s son over taxes and lobbying, even as he raided Donald Trump’s home and launched two probes against the former president.

More recently, several appearances by Hunter Biden at White House events suggest he, too, is emboldened and that an attempt to bring him out of hiding and normalize him is underway. This could indicate that Garland is about to shut down the case, possibly with a no-jail criminal plea or, even more outrageous, a civil settlement.
Catch up on Twitter’s censorship of The Post’s Hunter Biden laptop story
- Happening now: Hunter Biden laptop bombshell: Elon Musk’s Twitter drops Post censorship details
- Our original report: Smoking-gun email reveals how Hunter Biden introduced Ukrainian businessman to VP dad
- Editorial: Twitter is running a blackmail operation — cooperate or no traffic for you
- Dorsey backs down: Twitter CEO admits handling of blocked Post article was ‘unacceptable’
- How tweet it is: Twitter unlocks The Post’s account after two weeks
Here’s the good news: The Biden protection racket is starting to crack and the public is closer than ever to getting the truth about the president.
The hopeful developments are coming from several different directions.
Elon Musk, fresh off his $44 billion purchase of Twitter, is dramatically advancing the cause by pulling back the curtain on the tech partisans who sought to silence criticism of the president. Internal documents released so far also hint at a government role, and as my colleague Miranda Devine reported, a former top official confirmed the FBI secretly warned Twitter to be on the lookout for “hacked” materials in the 2020 campaign.

Yoel Roth, the former head of site security for Twitter, said in a deposition for the Federal Election Commission that “I was told in these meetings that the intelligence community expected that individuals associated with political campaigns would be subject to hacking attacks and that material obtained through those hacking attacks would likely be disseminated over social media platforms, including Twitter.”
Roth added that “there were rumors that a hack-and-leak operation would involve Hunter Biden.”
Mark Zuckerberg has echoed the scenario, saying recently that Facebook got FBI warnings about Russian disinformation and hacking before the 2020 election.
More explicit confirmation about the FBI’s role is coming from a little-noticed lawsuit filed by the attorneys general of Missouri and Louisiana. It alleges the Biden administration violated Americans’ free speech and “colluded with and/or coerced social media companies to suppress disfavored speakers, viewpoints and content on social media platforms” and the case is already paying big dividends.

The suit cites numerous areas of government suppression, including the laptop story, the lab leak theory of COVID-19’s origin, the efficiency of masks and COVID-19 lockdowns and election integrity issues. The consistent charge is that the feds label content they don’t like as “disinformation,” “misinformation” and “mal-information,” then lean on Facebook, Twitter and others to block that content from being shared or seen by users.
In its coverage of the case, taking place in Louisiana, Fox News cites the deposition of FBI Supervisory Special Agent Elvis Chan, who said he organized the meetings with social media companies in San Francisco for as many as “seven DC-based FBI agents ahead of the 2020 presidential election.”
He, too, cited potential “hack and leak” operations, but reportedly could not recall if he mentioned Hunter Biden’s name.

But remember: The FBI had Hunter’s laptop for nearly a year before the election. Leaders had to have known, or should have, that The Post’s stories were legitimate, so any attempt to paint the stories as hacked material cannot be trusted.
Misuse of power
There is no denying that these bombshell developments in recent days all point in the same direction: The Biden administration has been using government powers, including law enforcement, to silence news and viewpoints critical of it.
Amendment is far from won. Musk must continue to release incriminating Twitter documents and the attorneys general case needs to prove beyond doubt there is a government-wide attack on free speech.
But most important is the investigative work the new House majority has promised. Armed with subpoena power, Rep. Jim Jordan (R-Ohio) and other likely committee chairs finally will be able to compel testimony and demand documents about how Joe Biden profited from his family’s influence-peddling schemes.
Even more crucial is the question of whether the president’s involvement has compromised him when dealing with China and other adversaries. As I have noted, Americans are in the dark, but President Xi Jinping certainly knows if there was a quid pro quo for the many millions the Biden family got from China.
Assuming these disparate efforts continue to produce results, the final act in this long drama will begin with growing public outrage, which will cause at least some elements of the mainstream media to finally do their jobs and follow the facts instead of a partisan agenda.

We’re not there yet, but even to imagine the path forward shows how far we have come. It’s been a slow and frustrating slog, but I believe 2023 will produce the truth about a corrupt president.
Legit elex concerns
Count reader Carole Campolo among those drawing big conclusions from the Twitter Files. She writes: “Given what these last 72 hours have proven, it is not beyond the realm of possibility that those of us with legitimate concerns regarding the 2020 and now 2022 elections are not crazy.
“It doesn’t matter which Republican runs in 2024. When elections are not properly investigated, when serious questions are not even allowed to be asked, our democratic republic is done.”
FBI & Big Tech ‘sold their souls’
Martin McGuirk agrees, writing, “It makes me sick how the FBI in 2016 and 2020 was completely dishonest! What in hell does everyone in media and Big Tech see in Hillary and Joe that they would sell out their souls?”










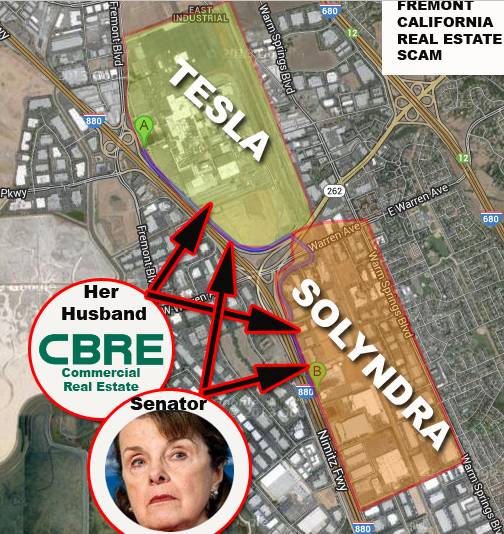



A quick, small connection point…
in his Dec 4 Twitter feed, Matt Tiabbi linked to a Jonathan Turley article on James Baker.
Six Degrees from James Baker: A Familiar Figure Reemerges With the Release of the Twitter Files. In the article, Turley links to familiar players with ties to the Brookings Institute. The articles are a good refresher on some of the actors…
sundance just tweeted a pic of James Baker taken by Ben Wittes (Lawfare/Brookings) in San Francisco (FBI Field office for Elvis Chan, Silicon Valley, etc)
https://t.co/BGULMYq2QS