Plaintiff, and thousands of other claimants, have asserted, and provided hundreds of thousands of pages of evidence from Inspector General offices, that prove that agencies and staff of the United States government were weaponized on orders of The White House and top California political figures, to operate reprisal, vendetta, revenge and payback operations in order to harm Plaintiff, and others, on an ongoing basis, in reprisal for reporting crimes and illicit schemes those parties were involved in.
Now comes the 118th CONGRESS, 1st Session under H. RES. 12 which Plaintiff now advises and which has been deployed for the purpose of Establishing a Select Subcommittee on the Weaponization of the Federal Government as a select investigative subcommittee of the Committee on the Judiciary.
IN THE U.S. HOUSE OF REPRESENTATIVES on January 9, 2023, the following was sent to the Committee on Rules. It Established a Select Subcommittee on the Weaponization of the Federal government as a select investigative subcommittee of the Committee on the Judiciary, in part based on Plaintiff’s team’s testimony and evidence and did resolve the following:
(a) Establishment; Composition.--
(1) Establishment.--There is hereby established for the One
Hundred Eighteenth Congress a select investigative subcommittee
of the Committee on the Judiciary called the Select
Subcommittee on the Weaponization of the Federal Government
(hereinafter referred to as the ``select subcommittee'').
(2) Composition.--
(A) The select subcommittee shall be composed of
the chair and ranking minority member of the Committee
on the Judiciary, together with not more than 13 other
Members, Delegates, or the Resident Commissioner
appointed by the Speaker, of whom not more than 5 shall
be appointed in consultation with the minority leader.
The Speaker shall designate one member of the select
subcommittee as its chair. Any vacancy in the select
subcommittee shall be filled in the same manner as the
original appointment.
(B) Each member appointed to the select
subcommittee shall be treated as though a member of the
Committee on the Judiciary for purposes of the select
subcommittee.
(b) Investigative Functions and Authority.--
(1) Investigative functions.--The select subcommittee is
authorized and directed to conduct a full and complete
investigation and study and, not later than January 2, 2025,
issue a final report to the House of its findings (and such
interim reports as it may deem necessary) regarding--
(A) the expansive role of article II authority
vested in the executive branch to collect information
on or otherwise investigate citizens of the United
States, including ongoing criminal investigations;
(B) how executive branch agencies work with, obtain
information from, and provide information to the
private sector, non-profit entities, or other
government agencies to facilitate action against
American citizens, including the extent, if any, to
which illegal or improper, unconstitutional, or
unethical activities were engaged in by the executive
branch or private sector against citizens of the United
States;
(C) how executive branch agencies collect, compile,
analyze, use, or disseminate information about citizens
of the United States, including any unconstitutional,
illegal, or unethical activities committed against
citizens of the United States;
(D) the laws, programs, and activities of the
executive branch as they relate to the collection of
information on citizens of the United States and the
sources and methods used for the collection of
information on citizens of the United States;
(E) any other issues related to the violation of
the civil liberties of citizens of the United States;
and
(F) any other matter relating to information
collected pursuant to the investigation conducted under
this paragraph at any time during the One Hundred
Eighteenth Congress.
(2) Authority.--
(A) The select subcommittee may report to the House
or any committee of the House from time to time the
results of its investigations and studies, together
with such detailed findings and legislative
recommendations as it may deem advisable.
(B) Any markup of legislation shall be held at the
full Committee level consistent with clause 1(l) of
rule X of the Rules of the House of Representatives.
(c) Procedure.--
(1) Rule XI of the Rules of the House of Representatives
and the rules of the Committee on the Judiciary shall apply to
the select subcommittee in the same manner as a subcommittee
except as follows:
(A) The chair of the select subcommittee may, after
consultation with the ranking minority member,
recognize--
(i) members of the select subcommittee to
question a witness for periods longer than five
minutes as though pursuant to clause 2(j)(2)(B)
of such rule XI; and
(ii) staff of the select subcommittee to
question a witness as though pursuant to clause
2(j)(2)(C) of such rule XI.
(B) The Committee on the Judiciary (or the chair of
the Committee on the Judiciary, if acting in accordance
with clause 2(m)(3)(A)(i) of rule XI) may authorize and
issue subpoenas to be returned at the select
subcommittee.
(C) With regard to the full scope of investigative
authority under subsection (b)(1), the select
subcommittee shall be authorized to receive information
available to the Permanent Select Committee on
Intelligence, consistent with congressional reporting
requirements for intelligence and intelligence-related
activities, and any such information received shall be
subject to the terms and conditions applicable under
clause 11 of rule X.
(2) The provisions of this resolution shall govern the
proceedings of the select subcommittee in the event of any
conflict with the rules of the House or of the Committee on the
Judiciary.
(d) Service.--Service on the select subcommittee shall not count
against the limitations in clause 5(b)(2)(A) of rule X of the Rules of
the House of Representatives.
(e) Successor.--The Committee on the Judiciary is the ``successor
in interest'' to the select subcommittee for purposes of clause 8(c) of
rule II of the Rules of the House of Representatives.
(f) Sunset.--The select subcommittee shall cease to exist 30 days
after filing the final report required under subsection (b). National News Coverage Exposes Problems
With Government Agency Reprisals – An Overview
By Conner Lee
A vast number of agency abuse cases and lawsuits are now on public record in the Inspector General's offices and federal courts.
It is an indisputable fact that some government agencies run "hit-jobs" on citizens on orders from certain corrupt politicians. These actions are felony violations of the law.
Federal and State Agencies including SSA, FEC, DOE, HHS, VA, CIA, NSA, SEC, FBI, DOJ and many others, have been charged, and found guilty, in these crimes against citizens.
In the Congressional investigation published by the United States Congress in review of the U.S. Department of Energy LGP/ATVM programs, it is clearly proven that the U.S. Department of Energy was used as a slush-fund by some DOE executives in order to pay off campaign financiers by attacking and sabotaging their competitors.
The DOE Paducah Gaseous Diffusion Plant under contracts with the Department of Energy and the government-owned U.S. Enrichment Corp paid $5M whistle-blower awards to those whistle-blowers who were attacked, using government agency resources, for reporting a crime.
Dept. of Energy Hanford URS has agreed to settle a lawsuit brought by former employee Walter Tamosaitis for $4.1 million. The settlement in the whistle-blower case comes almost one year before the case was set for a jury trial in federal court in Richland and compensates Tamosaitis for attacks against him, by DOE officials, in retribution for reporting a crime.
VA officials attacked hundreds of citizens who reported corruption, ie:
https://www.thenewamerican.com/usnews/health-care/item/18610-va-whistleblowers-facing-retribution
As shown in this report:
https://www.pogo.org/analysis/2018/08/new-report-confirms-whistleblower-retaliation-is-alive-and- well-at-department-of-veterans-affairs/
...Agencies attack often and harshly.
CIA and NSA executives have been widely shown to use spy tools to attack domestic citizens they don't like, ie:
3https://www.dailymail.co.uk/news/article-2435011/NSA-employees-used-phone-tapping-tools-spy- girlfriends-cheating-husbands.html
...and hundreds of other news links that can be provided.
Elon Musk and Tesla, as well as Eric Schmidt and Larry Page at Google, have been proven to use the CIA group: IN-Q-TEL, to run government sponsored/financed attacks on business competitors.
In Civil Action No. 1:13-cv-00777-RBW
GOVERNMENT AGENCIES WERE CAUGHT BEINGUSED FOR ATTACKS AGAINST CITIZENS AND PUNISHED IN THE COURT AND THE
MEDIA!
The IRS, HUD, SSA, DOE and hordes of other government agencies have been caught and proven, IN COURT, to target and attack people for presumed political differences.
Why should we assume that the Social Security Administration is not ALSO doing this too to harm citizens who speak out?
The Lois Lerner IRS attacks took many years to resolve. In an unprecedented victorious conclusion to a four year-long legal battle against the IRS, the bureaucratic agency admitted in federal court that it wrongfully targeted citizens, during the Obama Administration, because of their political viewpoints and issued an apology to those people for doing so.
In addition, the IRS is consenting to a court order that would prohibit it from ever engaging in this form of unconstitutional discrimination in the future.
In a proposed Consent Order filed with the Court, the IRS has apologized for its treatment of U.S. citizens including organizations from 20 states that applied for 501(c)(3) and (c)(4) tax-exempt status with the IRS between 2009 and 2012 -- during the tax-exempt determinations process. Crucially, following years of denial by the IRS and blame-shifting by IRS officials, the agency now expressly admits that its treatment of our clients was wrong and a total violation of our Democracy..
As set forth in the proposed Order:
“The IRS admits that its treatment of Plaintiffs during the tax-exempt determinations process, including screening their applications based on their names or policy positions, subjecting those applications to heightened scrutiny and inordinate delays, and demanding of some Plaintiffs’ information that TIGTA determined was unnecessary to the agency’s determination of their tax-exempt status, was wrong. For such treatment, the IRS expresses its sincere apology.”
Throughout litigation of this case, activists have remained committed to protecting the rights of the public who faced unlawful and discriminatory action by the IRS and other agencies. The objective from the very beginning has been to hold agencies accountable for corrupt practices.
4This Consent Order represents a historic victory for the public and sends the unequivocal message that
a government agency’s targeting of citizens organizations, or any organization, on the basis of political
viewpoints, will never be tolerated and that revenge will be swift and vast.
The Order will put an end, once and for all, to the abhorrent practices utilized against citizens, as the
agreement includes the IRS’s express acknowledgment of – and apology for – its wrongful treatment of
the public. While this agreement is designed to prevent any such practices from occurring again, rest
assured that all public interest lawyers will remain vigilant to ensure that the IRS, SSA, DOJ or SEC
does not resort to such tactics in the future.
Per detailed reports, in March of 2012 lawyers began being contacted by literally dozens of citizens and
groups who were being harassed by the Obama IRS after submitting applications for tax-exempt status.
Their tax-exempt applications were held up for years (over seven years in some cases), and they began
receiving obtrusive and unconstitutional requests for donor and member information. That began a now
more than five and a half year fight with the burgeoning bureaucracy at the IRS. Then on May 10,
2013, Lois Lerner, the then head of the IRS Tax Exempt Organizations Division, publicly implicated
the IRS in one of the worst political targeting scandals of the century.
This is an extraordinary victory against government agency abuse. It sends a powerful warning to the
deep state bureaucracy that it will not be allowed to violate the Constitution in order to silence and shut
down the whistle-blowers.
In addition to the IRS’s admissions of and apology for its wrongful conduct, the Consent Order would
specifically award Plaintiffs the following:
- A declaration by the Court that it is wrong to apply the United States tax code to any tax-exempt
applicant or entity based solely on such entity’s name, any lawful positions it espouses on any issues, or
its associations or perceived associations with a particular political movement, position or viewpoint;
- A declaration by the Court that any action or inaction taken by the IRS must be applied evenhandedly
and not based solely on a tax-exempt applicant or entity’s name, political viewpoint, or associations or
perceived associations with a particular political movement, position or viewpoint; and
- A declaration by the Court that discrimination on the basis of political viewpoint in administering the
United States tax code violates fundamental First Amendment rights. Disparate treatment of taxpayers
based solely on the taxpayers’ names, any lawful positions the taxpayers espouse on any issues, or the
taxpayers’ associations or perceived associations with a particular political movement, position or
viewpoint is unlawful.
In the Order, the IRS has also agreed that (unless expressly required by law) certain actions against the
Plaintiffs– i.e. the sharing, dissemination, or other use of information unnecessarily obtained by the IRS
during the determinations process (such as donor names, the names of volunteers, political affiliations
of an organization’s officers, etc.) – would be unlawful. In addition, the IRS promises not to take any
retaliatory action against our clients for exposing the targeting scheme.
5Finally, and of crucial significance, the IRS admits it targeted persons and groups based on their
viewpoints (i.e., “policy positions”) and that such viewpoint discrimination violates fundamental First
Amendment rights. This is the first time the IRS has admitted that its targeting scheme was not just
“inappropriate” – as TIGTA found – but, as alleged, blatantly unconstitutional.
To ensure consistency and uniformity within the agency’s operations going forward, the IRS is
required, pursuant to the Order, to inform all employees within the Exempt Organizations Division, as
well as the Commissioners and Deputy Commissioners within other divisions, of the Order’s terms.
This Order not only validates allegations about their treatment at the hands of the corrupt Obama-era
IRS but also provides important assurances to the American public that the agency understands its
obligation to refrain from further such discriminatory conduct. As Attorney General Sessions
acknowledged in this regard, “[t]here is no excuse for [the IRS’s] conduct,” as it is “without question”
that the First Amendment prohibits the conduct that occurred here, i.e., subjecting American citizens to
disparate treatment “based solely on their viewpoint or ideology.” Sessions further confirmed his
Department’s commitment to ensuring that the “abuse of power” in which the IRS engaged here “will
not be tolerated.”
It is impossible to overstate the importance of this victory. This marks a years-long fight for justice in
defense of the constitutional rights of the public.
This is an extraordinary victory against abuse of power and corruption.
It sends a powerful warning to the deep state bureaucracy that it will not be allowed to violate the
Constitution and manipulate the IRS, SSA and other agencies in order to silence and shut down those
who speak out about political corruption crimes.
In the wake of Wisconsin Watchdog’s investigation into SSA staff allegations of incompetence,
misconduct, and retaliation in Social Security disability appeals offices, several employees have taken
their complaints to a Senate committee led by Wisconsin Sen. Ron Johnson.
An official with knowledge of the complaints said the Senate Homeland Security and Governmental
Affairs Committee, chaired by the Oshkosh Republican, has received emails and other contacts from
“certain people” inside the Social Security Administration’s Office of Disability Adjudication and
Review.
The initial complaints came from an employee inside the Milwaukee office following Wisconsin
Watchdog’s opening investigative report that found some claimants waiting more than 1,000 days for
an appeals decision on their disability benefits claim.
Following Wednesday’s story of a whistleblower in the Madison ODAR office, the committee has
received more specific complaints about retaliation against employees, the source said.
Committee staff members sent the latest Watchdog piece to SSA administrators hoping they will
“cooperate,” the source said. To date, the agency has been less than cooperative.
6“This is an ongoing process, and they are not always as forthcoming as we’d like them to be,” the
source said. “Hopefully with your continued reporting, this is an issue they can’t duck.”
A Senate committee member said officials there are working with the Office of Special Counsel on
“multiple whistleblower retaliation claims.” The committee continues to request information from the
SSA.
The whistleblower in the Madison office claims management retaliated against her after she was called
to testify in a misconduct case. The incident involved “inappropriate behavior” by an administrative
law judge, she said.
“They are so corrupt. It’s absolutely horrible,” said the woman, a lead case technician in the Madison
Office of Disability Adjudication and Review.
She spoke on condition of anonymity, fearing more retribution from her supervisors. While she said
recounting her particular experiences will more than likely betray her identity anyway, the ODAR case
worker insisted she has had enough.
“I’m at point where they don’t care about me, I don’t see why I’m protecting them. This is my last
resort,” she said. “I want to do my work without fear of retaliation.”
She said she has contacted the Senate committee.
“I forwarded my information to them and I got an email back from them. They said people are coming
out of the woodwork with their complaints (about ODAR) following your story,” the whistle-blower
said.
Ronald Klym, a long-time senior legal assistant in the Milwaukee ODAR office, alleges he has been
retaliated against by supervisors for going public with his charges of incompetence and misconduct in
the agency.
The federal employee, who has worked for SSA for 16 years, provided Wisconsin Watchdog with
documents showing extremely long wait times for claimants appealing their denied applications for
benefits.
Doug Nguyen, SSA regional spokesman, in a previous story said the agency acknowledges that
Milwaukee ODAR has a “high average processing time for disability appeal hearings, and we are
working to address the issue.”
Beyond the delays is what Klym calls the “shell game,” the wholesale transferring of cases to other
parts of the country by administrators to make the Milwaukee office’s numbers look better than they
are.
The Madison office whistle-blower confirmed Klym’s allegations, saying at one point she saw 2,000
cases from the Milwaukee office handed off to the Oak Brook operation.
7There are over 10,000 SSA disability manipulation charges against SSA executives and staff.
MORE PROOF:
https://archive.fo/V4KSh
https://www.thegatewaypundit.com/2019/02/confirmed-john-fry-the-irs-analyst-who-leaked-michael-
cohens-tax-returns-is-a-far-left-trump-basher-who-supports-beto-orourke/
New Whistleblower Protection Office Is Under Investigation for
Retaliating Against Whistleblowers
The Veterans Affairs Department’s watchdog is investigating a new office created by President Trump
early in his administration that was designed to protect whistleblowers from reprisal but is now facing
allegations of aiding retaliation against them.
VA’s Office of Inspector General is leading the investigation from its new Office of Special Reviews,
which the IG created to conduct “prompt reviews of significant events” and examine allegations of
senior VA employee misconduct, an IG spokesman said. The new IG office is looking into activities at
the Office of Accountability and Whistleblower Protection as part of an ongoing review of the
implementation of the 2017 law that created OAWP.
Trump created OAWP by executive order in 2017 and later codified it when he signed the 2017 VA
Accountability and Whistleblower Protection Act into law. The office was mostly celebrated, with
advocates hopeful that the focus on the rights and protections for whistleblowers would reverse a
culture infamous for intimidation and reprisal. That optimism has largely soured, however, leading to
hotline tips to the inspector general and bipartisan scrutiny from Congress.
“There has been considerable interest by some members of Congress and other stakeholders in this
effort,” said Mike Nacincik, the IG spokesman, who said he could not comment further on ongoing
work.
President Trump has frequently touted the law as one of his signature legislative achievements,
focusing primarily on the reforms it made to expedite the disciplinary process for VA employees. But
Trump also spoke of the promises on which skeptics now say the law has failed to deliver: “This bill
protects whistleblowers who do the right thing,” Trump said. “We want to reward, cherish, and promote
the many dedicated employees at the VA.”
Government Executive spoke to several VA employees who expressed frustration or anger toward
OAWP, three of whom have already been interviewed by IG investigators. They described feeling
betrayed or neglected by an office they believed was going to help them but ended up doing the
8opposite. They said they have shared information with the investigators, including documentation of
alleged reprisal.
Curt Cashour, a VA spokesman, said the department “welcomes the inspector general’s oversight,” but
defended it against most allegations. He acknowledged that the office experienced some growing pains,
but said it has “evolved over time, refining and improving its policies and practices along the way.”
What Whistleblowers Are Telling Investigators
“It’s a crooked system where literally the fox is guarding the hen house,” said Jay DeNofrio.
DeNofrio, an administrative officer at a VA facility in Altoona, Pa., had prior experience as a
whistleblower before OAWP was created—years ago, he disclosed information about a doctor he said
was losing mental capacity and putting veterans at risk—so he thought he understood the investigative
process that takes place after employees make disclosures to investigators. OAWP, however, was the
first body he’d ever worked with that coordinated with VA headquarters to find blemishes on his own
record after he reported wrongdoing, he said. Investigators questioned his coworkers, telling them
DeNofrio does not “walk on water” just because he is a protected whistleblower and encouraged them
to immediately report “any instances of poor behavior,” according to transcripts of those conversations
obtained through records requests and provided to Government Executive.
DeNofrio said IG investigators took the allegations against OAWP seriously and called their review
“high profile” and “high priority.”
Dan Martin, a chief engineer at VA’s Northern Indiana Health Care System, said OAWP failed to
protect him when his case came before it. Martin said in 2016 he discovered contracting violations
related to a non-functioning water filtration system, but when he reported the problems to superiors he
was stripped of his responsibilities and sent to work in an office without heat or air conditioning. The
VA inspector general launched an investigation into the contracting practices, and asked Martin to
surreptitiously record conversations with procurement officers, Martin said.
It was not until OAWP got involved in the case that Martin’s supervisors became aware of that
cooperation. When OAWP allegedly shared that information with leadership at his facility, Martin said
his supervisors “had no choice but to shut me down” so he could no longer send recordings about the
supervisors’ “very inappropriate relationships with contractors” to investigators in the OIG.
“OAWP set me up,” said Martin, who initially felt far more optimistic about OAWP’s capacity to help
his cause. “They incentivized [my facility] to go after me.”
Martin is also fighting his case through the Merit Systems Protection Board. During that process, VA’s
Office of General Counsel came to Martin and his attorneys asking for certain information about the
case. The attorneys representing Martin told the lawyers in the Office of General Counsel they would
only hand the information over during discovery. Shortly after rejecting the request, Martin said,
OAWP followed up to ask for the same information.
“Some of them are so crooked they swallow nails and spit up corkscrews,” Martin said.
9‘They Turned on Whistleblowers’
The alleged collaboration between the Office of General Counsel and OAWP has troubled observers.
Tom Devine, legal director at the Government Accountability Project, a whistleblower advocacy group,
said his initial excitement about OAWP has been dampened by “structural developments,” including
what he called veto power the department's general counsel has over the whistleblower protection
office.
This would appear to be in violation of the 2017 law that permanently authorized OAWP, which
prohibits the office from existing “as an element of the Office of General Counsel” and its leadership
from reporting to OGC. Cashour said it was false to suggest that the Office of General Counsel
exercises veto power over whistleblower claims, but acknowledged OAWP and OGC do coordinate.
“OAWP has a collaborative working relationship with OGC, but OAWP retains final decision making
authority on all OAWP matters,” Cashour said.
Rebecca Jones, policy counsel at the Project on Government Oversight, said the office can likely not
completely fix its issues while it remains an “internal clearinghouse” for whistleblowers rather than a
truly independent office. Jones praised the IG for investigating the alleged retaliation.
“I wish it hadn’t come to this,” she said.
Devine praised some of OAWP’s early accomplishments, such as delaying VA’s disciplinary decisions
that involved alleged reprisal and the hiring of high-profile whistleblower Brandon Coleman as a
liaison between whistleblowers and the office. Coleman even established a mentoring program to help
assist victims of retaliation, but it has since been shut down.
“They didn’t have the teeth to enforce their good deeds,” said Devine, who has significantly curbed his
cooperation with OAWP. “They turned on whistleblowers.”
‘You Don’t Want to Come Forward’
A third VA employee, who requested anonymity to protect his ongoing cases, recently informed IG
investigators about what he alleged is OAWP’s betrayal of trust and subsequent inactivity. The
employee made an initial whistleblower disclosure in early 2017 that was bounced around to several
offices within VA. He subsequently was removed from his position as a technician and is now relegated
to “brain-dead work,” he said.
He contacted OAWP about the alleged reprisal later that year. During his interactions with the
whistleblower office, he turned over sensitive information about his hospital that a colleague had
provided—the OAWP investigator was the only individual with whom he shared the information. Days
later, the employee said, the colleague was “chewed out” by leaders at the facility for sharing the
information. To the employee, it felt like OAWP had betrayed him, he told Government Executive.
10The employee said he then experienced 21 months of “radio silence.” He recently spoke with OIG
about his negative experiences with OAWP. A few days later, the employee said he unexpectedly heard
from the OAWP investigators. He said he is now “very, very cautious” in his interactions with OAWP.
“It scares you,” he said. “You don’t want to come forward. People are afraid.”
Tonya Van, formerly a doctor a VA facility in San Antonio, also became a whistleblower after
disclosing to a supervisor that a doctor at her facility was giving incorrect diagnoses. She filed a
complaint with OAWP after she alleged her supervisor made her work life so miserable she was forced
to resign. But she quickly became disenchanted with the office due to lack of communication, she said.
She tried to follow up with OAWP but never heard back. The office eventually closed out her case,
though it later contacted her about opening a second investigation. She said she has “no idea” what the
results of either investigation were.
Van alleged that her supervisors’ reprisal against her took the form of accusations of using foul
language in the workplace. Martin, the Northern Indiana employee, said he faced an investigation for
similar accusations.
Changes and Cautious Optimism
Cashour, the VA spokesman, said OAWP does not provide “detailed information related to the specific
outcome of an investigation to employees” due to privacy concerns. He added that the office has
revised its policies to disclose more information to claimants, including when an investigation has been
closed and if claims of retaliation were substantiated.
Multiple VA employees criticized this practice, calling it counterintuitive that VA would claim privacy
concerns over investigations that the employees themselves requested.
Cashour said OAWP has changed other practices after a draft of a June 2018 Government
Accountability Office report faulted the office for its investigatory practices, including allowing
officials accused of retaliation to be directly involved in the inquiries in which they are named. VA told
GAO it would not end its practice of “referring cases of misconduct back to facilities and program
offices where the misconduct occurred.” However, Cashour said OAWP now informs employees
upfront when their matters will be referred elsewhere for review. To protect whistleblowers, he said,
OAWP now allows employees “to either opt-out of the disclosure or withhold the release of their
name.”
In August 2018, however, when Van had an in-person interview with OAWP investigators, she and her
attorney were still alleging retaliation by OAWP. While asking about Van’s allegations, an OAWP
investigator told Van she could be penalized for violating a prior settlement with VA by asking a former
colleague to write a recommendation. Her attorney said Deirdre Weiss, the OAWP employee, was
ignoring the intent of that prior agreement.
“The bottom line is that, as accountability investigators, where we see possible wrongdoing we cannot
look the other way just because somebody is a complainant, okay,” said Weiss, according to a transcript
of the proceedings.
11Last year, before his office formally launched an official investigation into the practices of OAWP, VA
Inspector General Michael Missal became part of a public spat with then acting Secretary Peter
O’Rourke over documents housed within the office. The IG requested access to information on the
cases filed with OAWP, but O’Rourke refused to comply. They aired their grievances through a series
of public letters, which included O’Rourke harshly reminding Missal that the IG served as the
secretary’s subordinate. Congress ultimately intervened by emphasizing in a spending bill that the IG
had the right to any and all documents it requested.
O’Rourke had previously served as the first head of OAWP, a period in which many of the complaints
against the office originated. Current VA Secretary Robert Wilkie reportedly asked O’Rourke to resign
last year after determining he was doing little work as a senior advisor.
OAWP is still a small office, employing just 96 workers—28 of whom are investigators—for a
workforce of 380,000. Its employees receive standardized training in investigative techniques, both
internally and from outside experts such as those at the Homeland Security Department and the Office
of Special Counsel.
The office is now headed by Tammy Bonzanto, who previously served as an investigator on the House
Veterans Affairs Committee. Her tenure has received mixed reviews. DeNofrio, for example, is still
concerned by what he calls her lack of transparency. Other observers are cautiously optimistic that her
leadership could get the office back to its original mission.
“We’re confident they have good-faith leadership now,” said GAP’s Devine. “The question is how
much professional freedom she’ll have.”
-------------------------------------
Nearly 100,000 Pentagon whistleblower complaints have been silenced – By Lee Camp
I don’t know if I’d have the nerve to be a whistleblower. I’d like to think I would. We all like to think
we would, just like we all like to think we could catch the game-winning touchdown or fold a fitted
sheet without cursing
But to blow the whistle on a huge organization with a lot of power, likely drawing that power to come
crashing down on your head – that takes some serious spine-age. Now, imagine the organization you’re
calling out is arguably the largest, most powerful, most secretive and most violent organization on
planet Earth. I’m speaking, of course, of the US Department of Defense.
Pentagon books so wrong on every level it’s impossible to detect fraud – Matt Taibbi Pentagon books
so wrong on every level it’s impossible to detect fraud – Matt Taibbi
12Yet thousands, even tens of thousands, of people have taken that step over the past five years. (More on
this in a moment.)
All the while our organized human murder machine continues its work around the world. Every day.
Every hour. Never a moment of rest. Never pausing to clip their toenails or scratch their ass. Bombs
dropped. Buildings blown up. People killed or imprisoned. No end in sight.
By the way, that’s the term I like to use instead of “military” – Organized Human Murder Machine.
It has a nice ring to it, doesn’t it? “Mili-tary” sounds too boring, too banal. Sounds like a super-lame
couple you met at a party. “Yeah, Millie and Terry over there are accountants. If I have to hear one
more joke about capital gains taxes, I’m gonna kill myself.”
But that’s not what the military is. The military is a gigantic organized human murder machine, and
even if you “support” every action our military has ever taken, you can still acknowledge it’s an
organized human murder machine. (You would just bizarrely argue that all the murder has been just and
sound and pure.)
Eleven months ago I covered $21 trillion of unaccounted-for adjustments at the Pentagon over the past
20 years. Don’t try to think about the number $21 trillion because you’ll pass out and hit your head on
the desk. If your salary is $40,000 a year, in order to earn $21 trillion, it would take you 525 million
years. (At which point you can’t even enjoy the new jet ski you just bought with all your money
because you’re almost certainly a brain in a jar … though a nice embroidered jar that only the rich
brains can afford.)
Also on rt.com The Pentagon failed its audit amid a $21 trillion scandal (yes, trillion) - Lee Camp
Over the past year there has been a little more coverage of the utterly preposterous amount of money
unaccounted for at our human murder machine. The Nation magazine, Forbes and Congresswoman
Alexandria Ocasio-Cortez all covered it. Then the white blood cells of the military-industrial complex
kicked into action in order to destroy the “infection.” The New York Times and Vox both claimed the
$21 trillion is merely the result of large-scale misdocumentation and therefore doesn’t matter at all. Of
course, the idea that tens of TRILLIONS of dollars of unaccountable adjustments don’t matter and
couldn’t mask any fraud, abuse or corruption is an assertion that makes Charlie Sheen’s statement that
he runs on tiger blood seem downright levelheaded.
Probably the best article to date on the $21 trillion was written a few weeks ago by Matt Taibbi for
Rolling Stone.
Point is, even though most of the mainstream media won’t get near this subject (or worse yet—actively
attack those who do), the word is getting out: There is a giant sucking sound in the center of the
Pentagon, and whatever’s down there feeds on trillions of secretive dollars, then sh*ts out incalculable
death and destruction. (It’s the Death Star if officials at the Death Star spent $10,000 on a toilet seat.)
13A month ago the Government Accountability Office came out with a report showing the total number
of whistleblower complaints over the past five years at the Department of Defense. It’s nearly 100,000.
Here’s the only part of the report that references that number:
“The Department of Defense Inspector General identified 8 substantiated violations of whistleblower
confidentiality between fiscal years 2013 and 2018, representing approximately .01 percent of the
95,613 contacts handled by the Inspector General during that time…”
We are being lied into war again – Lee Camp We are being lied into war again – Lee Camp
95,613 whistleblower complaints over five years.
Sadly, the Government Accountability Office was trying to brag in that sentence. They were proudly
stating, “We only breached the confidentiality of .01 percent of our 95,000 whistleblower complaints.
Aren’t we heroes?!”
It’s kind of like saying, “Of the 10,000 dolphins I’ve killed, not a single one has accidentally been a
human.” The sane response is, “Well, I’m glad to hear that, but did you say you killed 10,000
dolphins?”
To try to get the 95,000 number to make a little more sense, that averages out to a whistleblower every
six minutes of every weekday for five straight years. (That waiting room must be truly nuts. I bet all the
good magazines were claimed years ago.)
But maybe I’m looking at this all wrong. Perhaps the number 95,613 shouldn’t be all that shocking, and
I need to roll my tongue back up and store it back within my mouth. When you have $21 trillion of
unaccounted-for adjustments, it means a seizure-inducing amount of money, parts, pieces, bombs,
missiles, manpower and devices are flying around with no accountability – likely creating loads of
fraud, which would probably create loads of whistleblowers. Hence, maybe we all should have
expected this number of whistleblowers rather than being shocked.
For example, there’s the time in 2003 when the US flew $12 billion in cash to Iraq and promptly lost
track of it. As the Guardian makes clear in this article, this was not an instance of hackers on a
computer system stealing a bunch of ones and zeroes. This was giant pallets of cash money vanishing
without a trace. In fact, it was 281 million $100 bills, weighing in at 363 tons. That’s not really the type
of thing you can just smuggle away in your sweatshirt while humming “She’ll be comin’ ‘round the
mountain.”
Or here’s another example journalist David DeGraw highlights from the Government Accountability
Report:
“… according to a Department of Defense official, during an initial audit, the Army found 39
Blackhawk helicopters that had not been recorded in the property system. [$819 million in value]
Similarly, the Air Force identified 478 buildings and structures at 12 installations that were not in the
real property systems.”
14The Army lost and then found 39 helicopters.
The Air Force lost and then found 478 buildings.
How does one lose a goddamn building? Unless you just had a bad breakup with David Copperfield,
there’s no explanation for losing a building. (Side note: It must suck divorcing David Copperfield.
“Really, honey? You think you’re gonna take the house?? PAFOOMPF! What house?!”)
Ya see, this madness stems from the fact that the Pentagon has a standard operating procedure of
simply making up numbers to fill their books – which, for normal human beings, is termed “fraud.” But
in the case of the Pentagon, it’s termed, “We get to make sh*t up because … ummm… national
security.”
Also on rt.com Cold War is good for business: US contractors rejoice at the new Red Scare
Here’s more from a 2013 Reuters article:
“Linda Woodford spent the last 15 years of her career inserting phony numbers in the Department of
Defense’s accounts … but many mystery numbers remained. For those, Woodford and her colleagues
were told by superiors to take “unsubstantiated change actions” – in other words, enter false numbers,
commonly called “plugs,” to make the Navy’s totals match the Treasury’s.”
Have no fear, patriotic Americans, this is not “lying to the American people, stealing their money, and
using it for war,” this is just “unsubstantiated change actions.” Try that on your next tax return. Put in
$10,000 marked “Unsubstantiated change actions.” I’m sure they’ll love that.
So let’s sum this up, shall we? The Pentagon sucks up 55% of all the discretionary tax money we pay to
our government (thanks to our bought-off Congress who receive more Christmas cards from weapons
contractors than they do from relatives). Those who work at the Pentagon have no idea where or how
the money is spent. They make up many of the numbers resulting in tens of trillions of dollars of
unaccounted-for adjustments. They lose helicopters, buildings and, in a few instances, even nuclear
warheads. There is an unimaginable amount of fraud and corruption at every level and literally
thousands of whistleblowers have tried to come forward every single year – one every six minutes.
When they do take that incredibly brave action, over 90% of the claims are dismissed without even
being investigated.
You would think, in this topsy-turvy world, if there were one organization we could trust with a trillion
dollars a year of our taxpayer money, it would be the Department of Unauthorized Highly Secretive
Mass Human Murder.
-------------------------
https://www.army.mil/article/124325/whistleblower_reprisal_what_it_is_isnt
http://www.dodhotline.dodig.mil/Programs/Whistleblower/pdfs/IOGuide/
GuideToInvestigatingMilitaryWhistleblowerReprisalAndRestrictionComplaints.pdf
15https://www.gsaig.gov/sites/default/files/foia/Investigation%20of%20GSA%20Whistleblower
%20Reprisal%20Complaint%20June%202017.pdf
https://www.latimes.com/local/lanow/la-me-ln-california-air-national-guard-whistleblower-retaliation-
20190423-story.html
http://www.newindianexpress.com/world/2019/apr/16/european-parliament-backs-rules-to-protect-
whistleblowers-1965117.html
https://www.rollcall.com/news/pentagon-whistleblowers-often-face-retaliation-that-goes-unpunished
https://www.law360.com/articles/1133035/9th-circ-affirms-ex-bio-rad-gc-s-8m-whistleblower-win
https://retractionwatch.com/2018/07/30/how-institutions-gaslight-whistleblowers-and-what-can-be-
done/
https://www.theguardian.com/australia-news/2018/dec/05/corporate-whistleblowers-desperate-for-new-
protections
https://www.devex.com/news/the-high-price-of-being-a-un-whistleblower-92752
http://www.mondaq.com/canada/x/670072/Whistleblowing/
OSC+Whistleblower+Regime+Updates+Civil+Cause+Of+Action+For+Whistleblower+Reprisals
https://www.cbc.ca/news/canada/manitoba/middlechurch-home-whistleblower-speaks-1.4713482
https://www.smh.com.au/business/chilling-tale-of-origin-energy-whistleblower-20170124-gtxuhz.html
https://www.news.com.au/national/courts-law/you-ruined-my-career-pay-me-10m-traumatised-agent-
suing-the-afp-for-huge-sum/news-story/8c6e1c9a70745dc4418973d028db1323
https://www.federaltimes.com/federal-oversight/2017/10/23/fbi-managers-labeled-whistleblower-an-
insider-threat-in-retaliation/
https://www.washingtonpost.com/news/federal-eye/wp/2015/09/22/va-culture-of-reprisals-against-
whistleblowers-remains-strong-after-scandal/
https://www.stripes.com/news/feds-probing-reports-of-va-whistleblower-reprisals-1.287227
https://www.scmp.com/news/world/europe/article/3006462/european-parliament-overwhelmingly-
backs-rules-protect-whistle
https://www.canberratimes.com.au/politics/federal/the-whistle-shaped-hole-in-our-laws-20190327-
p5185l.html
http://theconversation.com/troublemakers-and-traitors-its-no-fun-being-a-whistleblower-50755
https://leadership.ng/2019/01/19/fifa-whistleblower-killed-in-ghana/
http://www.ncregister.com/daily-news/2018-the-year-of-the-whistleblower
16DOE corruption—appointed and elected
officials should face prison time
Marita Noon
|
An exhaustive review of 350+ pages of leaked emails regarding the Obama administration’s handling
of the various green-energy loan and grant programs makes several things very clear: they lied,
engaged in favoritism, and rushed application approvals to suit the political agenda of the White House.
At the same time, worthy projects that went through a complete due diligence process were denied or
ultimately withdrawn, as the lengthy approval process “taxed investors’ patience”—as was the case
with Aptera Motors, which worked closely with the DOE for two years.
Paul Wilbur, President and CEO at Aptera, didn’t think they were treated unfairly. He told me, “At the
end of the day, we couldn’t get through the process.” But, he admits, he hasn’t read the emails.
Aptera was trying to build a very efficient electric vehicle with an under $30K price point. Wilbur met
with Secretary Chu who could see the value in the technology. But our research shows that value was
not the deciding factor in which projects got funded and which ones didn’t. Wilbur reports that he
didn’t donate to any candidate. He wanted to keep the whole process clean and do what was “good for
America.”
The report from the House Oversight Committee says Aptera first applied for an ATVM loan in
December of 2008 and “shut down on December 2, 2011.” The report implies that Aptera was led on:
“After numerous negotiations with DOE, in September 2011, Aptera received a conditional loan
commitment of $150 million if the company was able to raise $80 million privately.” And: “The loans
given to Fisker and Tesla gave Aptera hope that DOE would eventually act on their application. More
importantly, since the DOE continued to engage with the company throughout the time period,
management was convinced that DOE was interested and willing to provide financing for the
company.”
Aptera’s 100% US technology has since been sold to a Chinese company.
Aptera was applying for an Advanced Technology Vehicle Manufacturing loan (ATVM). Only five
loans were given out through the program and all have political ramifications. Christine Lakatos, who
has worked with me on the green-energy, crony-corruption reports I’ve written, has done thorough
research on the topic. She has read each and every one of the 350+ pages of emails released on October
31 and has written a blog post specifically addressing the ATVM program and its hijinks. As she cites,
Fisker and Tesla (which Romney referenced in the first debate), got loans in 2010 and then the Vehicle
Production Group’s loan was the only ATVM loan closed in 2011; all have ties to Obama bundlers. The
17other two ATVM loans went to Ford and Nissan—both of which, according to the House report, “were
heavily engaged in negotiations with the Administration over fuel economy standards for model years
2012-2016 at the time the DOE was considering their applications. Both companies eventually
expressed publicly their support for these standards, which the Administration described as the
‘Historic Agreement.’”
Armed with the sweeping knowledge of the House reports and subsequent hearings, evidence from
DOE staffers (many of whom were appointed by Obama), Lakatos’ research, and personal experience,
a different ATVM applicant has now taken its case to court citing “corruption and negligence.”
On November 16, 2012, XP Technologies filed a lawsuit against the federal government concerning the
DOE’s denial of XP Technology’s loan guarantee application. The complaint alleges: “criminal
activities did take place by DOE staff and affiliates.” A November 23 press release announces that XP
Technologies is now represented by Cause of Action, “a nonprofit, nonpartisan organization that uses
investigative, legal, and communication tools to educate the public on how government accountability
and transparency protects taxpayer interests and economic activity.”
According to the document filed on November 16, “Plaintiffs' backgrounds include extensive issued
patents on seminal technologies in use world-wide, White House and Congressional commendations
and an engineering team of highly experienced auto-makers. Plaintiff brought a vehicle design, which
was proposed as the longest range, safest, lowest cost electric vehicle, to be built in America in order to
deliver extensive American jobs nationwide. No other applicant, or award ‘winner’, has succeeded in
meeting, or (is) intending to meet, that milestone. XP Technology developed a patented lightweight,
low-cost, long-range, electric vehicle using air-expanded foam-skinned material for a portion of the
polymer body and received numerous patents, acclaim and superior computer modeling metrics over
any competing solution. XP presented a vast set of letters of support to DOE from pending customers.
Major auto-industry facilities and engineers had joined forces to bring the vehicle to the defense,
commercial and consumer market.”
Over the weekend, we had an exclusive interview, on condition of anonymity, with a senior official at
XP Technologies about the lawsuit and the experience.
He reported: “Staff from within the DOE have provided evidence which is quite compelling.” As
Aptera's Wilbur made clear, the individuals within the DOE were very thorough. One of the emails, in
the 350+ pages, was from Secretary Chu himself in which he criticized staffers for taking a “principled
stand,” which held up the approval process of projects the White House wanted advanced. Another
indicated that the pressure to rush was coming from “above the agency.” Overall, the emails show that
projects were rushed so that announcements could coincide with visits, speeches, and photo ops—as
well as providing talking points for the president.
Our XP source told us “We experienced, and have been provided evidence of, applicant submissions
and reviews being modified in order to benefit some and disadvantage others, and the business
connections between the different parties associated with the ones that benefited is quite
extraordinary.” The leaked emails support this accusation, specifically regarding the “business
18connections.” In her post, Lakatos calls it “green fraternizing.” The emails show that certain applicants
and decision makers went bike riding together, had coffee meetings, sleepovers, beer summits, parties,
dinners, and fundraisers.
While he didn’t provide us with a name, the XP official said, “We experienced a senior senator
blockading our efforts and then providing favors to a competitor, which then benefited his family
financially.” The discovery the lawsuit will provide will expose the “senior senator,” but our previous
research shows that Senator Harry Reid’s actions seem to fit the XP official’s comment.
XP Technologies believes that “DOE officials changed the first-come-first-served published rules and
standards of the funding in order to take applicants in order of who they favored and who had
purchased the most influence instead of the order in which they applied, as required.”
Having extensively studied the DOE’s various loan programs, including the ATVM, Lakatos and I
agree with our source’s startling conclusion: “Based on the evidence provided by investigators, and
experienced directly by our team, it is hard to imagine that at least one or more elected, or?appointed,
officials might not be seeing measures ranging from censure or even federal prison time.”
Time, the lawsuit, and subsequent investigation will tell.
While the House Oversight Committee has been digging deeply into the mismanagement and
corruption of the green energy loans, the media has paid little attention. Other than our report, the
October 31 release of the emails cited here received virtually no news reporting. Even the Fox News
Channel ignored the story. The plight of promising companies like Aptera and XP Technologies would
have gone unnoticed if not for the lawsuit. The legal complaint attracted attention.
On November 16, the Heritage Foundation broke the XP story: “A lawsuit filed in federal court on
Wednesday alleges mass favoritism in the Department of Energy’s decisions to award federal grants to
major car companies to develop electric vehicles, according to a legal complaint obtained by Scribe.”
On November 19, Lakatos, whose work is listed as “evidence” in the legal complaint, received a call
from Fox News’ Gary Gastelu—who reported on the story on November 20. The next day, Fox News
covered the lawsuit on America’s Newsroom. Even the Drudge Report picked up on the story.
XP has a litigation website on which the company states: “The case has nothing to do with complaining
about not getting the loans. It has everything to do with HOW the applicants didn't get the loans!” They
are communicating with other applicants about participating in the lawsuit.
The XP story and subsequent media coverage offers a lesson for others—especially industries who
have been wronged by the Obama Administration’s practices (such as energy). The lawsuit may—or
may not—send officials to federal prison, as our XP source suggests, but it could go a long way to
winning in the court of public opinion.
If you thought that Mossack Fonseca and the Panama Papers was "The Story": IT WAS ONLY THE
BEGINNING AND THE BRIBES, STOCK MARKET RIGGING AND CORRUPTION ARE STILL
INCREASING!!!
19In the USA; Mofo, Wilson Sonsini, Perkins Coie, Covington & Burling, and other firms, do the same
corruption today that Mossack Fonseca did when they got caught.
THIS IS ABOUT THE U.S. SENATORS AND THEIR CRONY DARK MONEY POLITICAL
BRIBES AND CRIMINAL KICK-BACKS, THE TECH OLIGARCHS WHO DEPLOYED THE
BRIBES AND THE VICTIMS OF THESE CRIMES.
- Google, Tesla, Facebook, Linkedin and their VC's (and deeply bribed Senators) ordered and operated
hit-jobs on the public and their competitors, supported by the Obama White House and U.S. Dept. of
Energy. The FBI raided their scheme and the investigations tracked all the way back to the Oval Office!
- How Obama's U.S. Department of Energy Defrauded Americans Out Of Their Life Savings In A
Massive Dark Money Crony Crime Cover-up
- "DARK MONEY" IS THE WAY THAT CORRUPT POLITICAL CRIMINALS EXCHANGE
COMPENSATION, BRIBES AND INFLUENCE WITHOUT THE FBI CATCHING THEM
- For these politicians to say: "We are excluded from the law for these crimes because we changed the
laws in order to exclude ourselves" is like the Mafia saying: "Killing people isn't illegal only if we do
the killing".
- This is about a group of tech oligarchs, and their corrupt Senators, who commit crimes in order to
manipulate over a trillion tax dollars (YOUR MONEY) into their, and their friends pockets.
- They create fake issues that they hype-up through their controlled media. They use media monopoly
tricks to try to shut out any other viewpoints. They push pretend issues that they believe will get more
tax money allocated to "issue solutions" that they, and their friends, happen to already own the
monopolies for.
- They are felons yet they control some of the offices of the agencies who are supposed to arrest them.
Silicon Valley bought K Street and U.S. Senators, gave them more Dark Money than history has ever
seen and then had giant tech-law firms bribe, hit-job and blockade any attempts to solve the problem.
- Some of the largest bribes in American history were paid via billions of dollars of pre-IPO cleantech
stock, insider trading, real estate, Google search engine rigging and shadow-banning, sex workers,
revolving door jobs, nepotism, state-supported black-listing of competitors and under-the-table cash.
Why are these Silicon Valley Oligarchs and their K-Street law firms and lobbyists immune from the
law?
https://pilotonline.com/news/government/politics/article_c6836711-70ed-588c-b73f-
547d6d82cb62.html
======================
HOW SILICON VALLEY'S "SCALED" CRIME CARTEL WORKS:
20- A crime with hookers and a very big shark
There are millions of sharks in the ocean but only "Jaws" was big enough to earn himself (The Shark)
so many feature films about trying to kill him. It was simply because he was so big and so hungry.
Judging by the endless sequels, Jaws seems pretty hard to kill.
This is about the biggest sharks. They are from Silicon Valley.
Google, Facebook, Amazon, Linkedin, Netflix, et al; exist because they operate under the criminal
umbrella of the tech Cartel frat boys.
These guys are addicted to sex, and they are also huge assholes, so they can't keep any partners around
unless they pay them to be trophy wives or "beard" wives. Buying sex from Italian escorts, young girls
and New York Rent Boys is really, really expensive. This drives them to do anything to suck up huge
amounts of cash.
These guys are also addicted to power, so they buy East and West Coast U.S. Senators, British
Parliament members and partner with corrupt Russian oligarchs. Buying Senators is also really, really
expensive. This also drives them to do anything to suck up huge amounts of cash.
These guys need, and spend, massive amounts of cash. Being a tech oligarch is really, really expensive.
They can't have the IRS cutting into their hooker-budgets. They spend massive amounts on big law
firms to hide money in real estate, trusts, fake charities and in a huge array of off-shore spider holes.
These guys can't afford to get caught so they hire In-Q-Tel, Gawker Media, Black Cube, Fusion-GPS,
and a huge army of other attackers, to destroy anybody who questions their motives.
Their Cartel exists because they own all of the main servers, banks, venture capital firms, tech law
firms, K Street lobbyists and tech HR firms.
They control their entire eco-system and black-list anybody that offends them.
They own the internet and they delete anybody who steps in their circle.
Nobody can operate outside of it.
No start-up can compete with them without getting a hit-job put on it.
Since the year 2000, together, they have put over a million smaller companies out of business.
They exist because of "Scaling": the ability to use monopolized networks to reach everyone on Earth,
have lower prices, and destroy all competition because they control all infrastructure. Scaling is all they
talk about at their AngelGate "power lunches" in the back rooms of Restaurants on University Avenue
in Palo Alto.
The FBI can't stop them because they owned James Comey, the head of the FBI.
21The SEC, FEC and FTC can't stop them because they own the regulators at those agencies.
They Obama White House could not stop them because most of the Obama Administration was staffed
by, and directed by, the staff of Google, Amazon and Facebook, et al.
The Silicon Valley tech Cartel makes the Mafia look like small potatoes.
They are a criminal organization!
If certain politicians are as 'impassioned to serve the public' as they say, then shouldn't they volunteer
for office and allow the public to see all of their bank accounts?
Of course they will never do that because many of them are getting "DARK MONEY" covert payola
and they are in office only to serve criminal kick-back schemes.
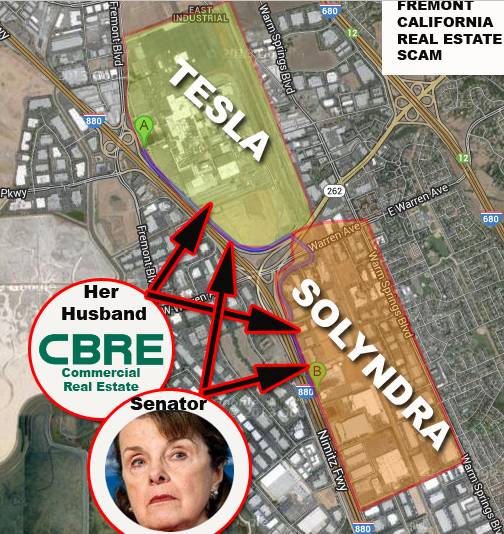
Politician's Dianne Feinstein, Barbara Boxer, Nancy Pelosi, Harry Reid and 42 others, sent out letters,
emails, meeting requests and pitches to solicit members of the public to join a cause. The top staff of
the U.S. Department of Energy (DOE) sent out the same pleas. They promised a "wonderful new
opportunity for all" in the first market break for outsiders in 30 years.
In meetings, on camera, they promised to give members of the public a fair shot at a group of new
Department of Energy funds that Obama had put in place.
They failed to mention one key fact: ALL OF THE TAXPAYER MONEY HAD ALREADY BEEN
SECRETLY PROMISED ("Hard Wired" it is called) TO OBAMA'S, AND THE DOE BOSSES,
FRIENDS, IN ADVANCE.
That is a felony violation of the law. A crime which FBI Director James Comey, and his staff covered
up and which DOE Boss Steven Chu and his staff actively implemented. Our team knows this, as fact,
because they reported directly to Comey, Chu and their offices.
It was not an 'accident', it was not an 'oversight', it was not 'an agency just overwhelmed with paper'. It
was a precision controlled, coordinated organized crime effort designed to rape, both, the U.S.
taxpayers and the non-crony applicants for these funds.
The crime used the traditional bribes, crony payola contracts, revolving doors, sex worker payoffs and
other political corruption but it mainly used a new tactic called "Dark Money'.
Our team knows this because some of them were solicited to participate in these crimes and some of
them had close personal relationships with the politicians who are now known to have operated these
crimes. Some of our witnesses and insiders have been involved with the DOE since before 2000. They
have 'seen it all'.
Companies, their executives and their investors were induced by California and New York Senators,
White House Staff and the top staff of the U.S. Department of Energy to invest many years of their
lives, and tens of millions of dollars of their personal cash in a fake government program which only
existed to pay off Obama's political financiers.
22American taxpayers were lied to and ruined by the U.S Department of Energy and their damages are
increasing monthly. The DOE never apologized, offered fixes or provided anything other than Fusion-
GPS kinds of attacks on those who asked for help or who reported the crimes.
This scam happened in 2008. History has proven that the DOE funds, since then, were rigged.
Congress, the news media and special investigations have proven that these crimes happened. Nothing
has ever been done to help the victims (over 100 companies and over 1800 individuals) recover from
their state-sponsored losses.
Former House Speaker Nancy Pelosi bought stock in initial public offerings (IPOs) from the very
Cleantech companies that earned hefty returns (ie: Solyndra, Tesla, Abound, etc.) while she had access
to insider information that would have been illegal for an average citizen to trade with – even though
it’s perfectly legal for elected officials, CBS’s "60 Minutes" reported Sunday night.
In a piece relying on data collected from the conservative Hoover Institution, "60 Minutes" revealed
that elected officials like Pelosi are exempt from insider trading laws – regulations that carry hefty
prison sentences and fines for any other citizen who trades stocks with private information on
companies that can affect their stock price.
In the case of elected officials – this secret information ranges from timely details on lucrative federal
contracts to legislation that can cause companies’ stocks to rise and fall dramatically.
Editor's Note: Repeal Obamacare? Vote Here Now
How do they get away with it? Lawmakers have exempted themselves from the laws that govern every
other citizen.
Pelosi, D-Calif., and her husband have participated in at least eight IPOs while having access to
information directly relating to the companies involved. One of those came in 2008, from Visa, just as a
troublesome piece of legislation that would have hurt credit card companies, began making its way
through the House.
“Undisturbed by a potential conflict of interest the Pelosis purchased 5,000 shares of Visa at the initial
price of $44 dollars. Two days later it was trading at $64. The credit card legislation never made it to
the floor of the House,” Steve Kroft of "60 Minutes" reported.
Kroft confronted Pelosi at a regular press conference after she declined an interview.
Kroft: Madam Leader, I wanted to ask you why you and your husband back in March of 2008 accepted
and participated in a very large IPO deal from Visa at a time there was major legislation affecting the
credit card companies making its way through the —through the House.
Nancy Pelosi: But —
Kroft: And did you consider that to be a conflict of interest?
23Pelosi: The — y — I — I don't know what your point is of your question. Is there some point that you
want to make with that?
Kroft: Well, I — I — I guess what I'm asking is do you think it's all right for a speaker to accept a very
preferential, favorable stock deal?
Pelosi: Well, we didn't.
Kroft: You participated in the IPO. And at the time you were speaker of the House. You don't think it
was a conflict of interest or had the appearance--
Pelosi: No, it was not —
Kroft: — of a conflict of interest?
Pelosi: —it doesn't — it only has appearance if you decide that you're going to have — elaborate on a
false premise. But it — it — it's not true and that's that.
Kroft: I don't understand what part's not true.
Pelosi: Yes sir. That — that I would act upon an investment.
“There are all sorts of forms of honest grafts that congressmen engage in that allow them to become
very, very wealthy. So it's not illegal, but I think it's highly unethical, I think it's highly offensive, and
wrong,” he told Kroft.
“… Insider trading on the stock market. If you are a member of Congress, those laws are deemed not to
apply,” Schweizer added. “The fact is, if you sit on a healthcare committee and you know that
Medicare, for example, is — is considering not reimbursing for a certain drug that's market moving
information. And if you can trade stock on — off of that information and do so legally, that's a great
profit making opportunity. And that sort of behavior goes on.”
Pelosi’s office issued a statement Sunday saying, “It is very troubling that ‘60 Minutes’ would base
their reporting off of an already-discredited conservative author who has made a career out of attacking
Democrats.”
Schweizer’s books include “Do as I Say (Not as I Do): Profiles in Liberal Hypocrisy,” and “Architects
of Ruin,” according to Schweizer’s page on the Hoover Institution website.
What happened when the victims of these crimes reported the incidents to authorities? The Obama
Administration ordered and operated attacks on the victims. Those attacks included the following
reprisal, retribution and revenge efforts:'
- DOE solicited the victims with false promises and caused them to expend millions of dollars and
years of their time for projects which DOE had covertly promised to their friends and were using the
victims as a “smokescreen” to cover their illegal DOE slush-fund for the victims competitors and
personal enemies.
24- Social Security, SSI, SDI, Disability and other earned benefits were stone-walled. Applications
were “lost”. Files in the application process “disappeared”. Lois Lerner hard drive “incidents” took
place in order to seek to hide information and run cover-ups.
- DOE’s Jonathan Silver, Lachlan Seward and Steven Chu contacted members of the National
Venture Capital association (NVCA) and created national “black-lists” to blockade Victims from ever
receiving investor funding. This was also confirmed in a widely published disclosure by Tesla Motors
Daryl Siry and in published testimony.
FOIA requests were hidden, frozen, stone-walled, delayed, lied about and only partially responded to
in order to seek to hide information and run cover-ups.
- State and federal employees played an endless game of Catch-22 by arbitrarily determining that
deadlines had passed that they, the government officials, had stonewalled and obfuscated applications
for, in order to force these deadlines that they set, to appear to be missed.
- Some Victims found themselves strangely poisoned, not unlike the Alexander Litvenko case. Heavy
metals and toxic materials were found right after their work with the Department of Energy weapons
and energy facilities. Many wonder if these “targets” were intentionally exposed to toxins in retribution
for their testimony. The federal MSDS documents clearly show that a number of these people were
exposed to deadly compounds and radiations, via DOE, without being provided with proper HazMat
suits which DOE officials knew were required.
- Victims employers were called, and faxed, and ordered to fire Victims from their places of
employment, in the middle of the day, with no notice, as a retribution tactic.
- On orders from Obama White House officials, DNC-financed Google, YouTube, Gawker Media
and Gizmodo Media produced attack articles and defamation videos and locked them on the internet on
the top line, of the front page of all Google searches for a decade in front of 7.5 billion people, around
the world, at a cost of over $40 million dollars in server farms, production costs and internet rigging.
The forensic data acquired from this attack proved that Google rigs attacks against individuals on the
internet and that all of Google’s “impressions” are manually controlled by Google’s executives who are
also the main financiers and policy directors of the Obama Administration. This data was provided to
the European Union for it’s ongoing prosecution of Google’s political manipulation of public
perceptions.
- Victims HR and employment records, on recruiting and hiring databases, were embedded with
negative keywords in order to prevent them from gaining future employment.
- Our associates: Gary D. Conley, Seth Rich, Rajeev Motwani and over 30 other whistle-blowers in
this matter, turned up dead under strange circumstances. They are not alone in a series of bizarre deaths
related to the DOE investiagtions.
- Disability and VA complaint hearings and benefits were frozen, delayed, denied or subjected to lost
records and "missing hard drives" as in the Lois Lerner case.
25- Paypal and other on-line payments for on-line sales were delayed, hidden, or re-directed in order to
terminate income potential for Victims who competed with DOE interests and holdings.
- DNS redirection, website spoofing which sent Victims websites to dead ends and other Internet
activity manipulations were conducted. All commercial storefronts and on-line sales attempts by
Victims, had their sites hidden, or search engine de-linked by an massively resourced facility in order to
terminate revenue potentials for those victims.
Over 50,000 trolls, shills, botnets and synth-blog deployments were deployed to place defamatory
statements and disinformation about victims in front of 7.5 billion people around the world on the
internet in order to seek to damage their federal testimony credibility by a massively resourced facility.
- Campaign finance dirty tricks contractors IN-Q-Tel, Think Progress, Black Cube, Podesta Group,
Stratfor, Fusion GPS, IN-Q-Tel, Media Matters, Gawker Media, Gizmodo Media, Syd Blumenthal, etc.,
were hired by DOE Executives and their campaign financiers to attack Victims who competed with
DOE executives stocks and personal assets.
- Covert DOE partner: Google, transfered large sums of cash to dirty tricks contractors and then
manually locked the media portion of the attacks into the top lines of the top pages of all Google
searches globally, for years, with hidden embedded codes in the links and web-pages which multiplied
the attacks on Victims by many magnitudes.
Covert Cartel financier: Google, placed Google’s lawyer: Michelle Lee, in charge of the U.S. Patent
Office and she, in turn, stacked all of the U.S. Patent Office IPR and ALICE review boards and offices
with Google-supporting employees in order to rig the U.S. Patent Office to protect Google from being
prosecuted for the vast patent thefts that Google engages in. Google has hundreds of patent lawsuits for
technology theft and a number of those lawsuits refer to Google’s operations as “Racketeering”,
“Monopolistic Cartel” and “Government Coup-like” behaviors. Thousands of articles and
investigations detail the fact that Google, “essentially” ran the Obama White House and provided over
80% of the key White House staff. A conflict-of-interest unlike any in American history. Google’s
investors personally told Applicant they would “kill him”. Google and the Obama Administration were
“the same entity”. Applicant testified in the review that got Michelle Lee terminated and uncovered a
tactical political and social warfare group inside Google who were financed by Federal and State funds.
- Honeytraps and moles were employed by the attackers. In this tactic, people who covertly worked
for the attackers were employed to approach the “target” in order to spy on and misdirect the subject.
- Mortgage and rental applications had red flags added to them in databases to prevent the targets
from getting homes or apartments.
- McCarthy-Era "Black-lists" were created and employed against Victims who competed with DOE
executives and their campaign financiers to prevent them from funding and future employment.
- Targets were very carefully placed in a position of not being able to get jobs, unemployment
benefits, disability benefits or acquire any possible sources of income. The retribution tactics were
audacious, overt..and quite illegal.
26========================================
How does DOE Dark Money work?
Let's take a look:
In the politics of the United States, dark money is funds given to nonprofit organizations—and include
501(c)(4)(social welfare) 501(c)(5) (unions) and 501(c)(6) (trade association) groups—that can receive
unlimited donations from corporations, individuals, and unions, and spend funds to influence elections,
but are not required to disclose their donors.[3][4] Dark money first entered politics with Buckley v.
Valeo (1976) when the United States Supreme Court laid out Eight Magic Words that define the
difference between electioneering and issue advocacy.
According to the Center for Responsive Politics, "spending by organizations that do not disclose their
donors has increased from less than $5.2 million in 2006 to well over $300 million in the 2012
presidential cycle and more than $174 million in the 2014 midterms."[3] The New York Times editorial
board has opined that the 2014 midterm elections were influenced by "the greatest wave of secret,
special-interest money ever raised in a congressional election."[5]
The term was first used by the Sunlight Foundation to describe undisclosed funds that were used during
the United States 2010 mid-term election.[6][7] Its practical effect has been described by Donald
Trump as Congress "being under the magical spell of the donors."[8]
In some elections, dark money groups have surpassed traditional political action committees (PAC) and
"super PACs" (independent-expenditure-only committees) in the volume of spending.[4] In 2014, the
group Freedom Partners was identified as the "poster child" for the rise of dark money.[4] In 2012,
Freedom Partners had the ninth-highest revenues among all U.S. trade associations which filed tax
returns that year, more than "established heavyweights" such as the American Petroleum Institute,
PhRMA, and U.S. Chamber of Commerce.[4] Freedom Partners largely acted as a conduit for
campaign spending; of the $238 million it spent in 2012, 99 percent went to other groups, and Freedom
Partners itself did not have any employees.[4] This was a major distinction between other high-revenue
trade associations, which typically have many employees and devote only about 6 percent of spending
to grants to outside groups.[4]
The rise of dark money groups was aided by the U.S. Supreme Court decisions in FEC v. Wisconsin
Right to Life, Inc. (2008) and Citizens United v. FEC (2010).[4] In Citizens United, the Court ruled (by
a 5–4 vote) that corporations and unions could spend unlimited amounts of money to advocate for or
against political candidates.[9]
2010 election cycle
According to the Center for Responsive Politics, dark money (which it defined as funds from outside
groups that did not publicly disclose donors, plus groups that received a substantial portion of their
contributions from such nondisclosing groups) accounted for nearly 44% of outside spending in the
2010 election cycle.[10]
27In the 2012 election cycle, more than $308 million in dark money was spent, according to the Center
for Responsive Politics.[11] An estimated 86 percent was spent by conservative groups, 11 percent by
liberal groups and 3 percent by other groups.[11]
The three dark money groups which spent the largest sums were Karl Rove's American
Crossroads/Crossroads GPS ($71 million), the Koch brothers' Americans for Prosperity ($36 million)
and the U.S. Chamber of Commerce ($35 million), all conservative groups.[11][12] Aside from a
complex, and still highly covert network created by The Clinton Foundation, Media Matters and The
Podesta Group, the three liberal groups with the largest dark-money expenditures were the League of
Conservation Voters ($11 million), Patriot Majority USA, a group focusing on public schools and
infrastructure ($7 million), and Planned Parenthood (almost $7 million).[11]
The 2014 election cycle saw the largest amount of dark money ever spent in a congressional election;
the New York Timeseditorial board described 2014 "the greatest wave of secret, special-interest money
ever."[5] On the eve of the election, Republican-leaning dark money groups dominated, with $94.6
million in expenditures, exceeding dark money expenditures by Democratic-leaning dark money
groups ($28.4 million), and by expenditures that could not be classified ($1.9 million).[13] Karl Rove's
dark money group Crossroads GPS alone spent over $47 million in the 2014 election cycle.[14]
In the Senate elections, dark money spending was highly concentrated in a handful of targeted
competitive states, and especially in Alaska, Arkansas, Colorado, Kentucky, and North Carolina.[15] In
the eleven most competitive Senate races, $342 million was spent by non-party outside groups,
significantly more than the $89 million spent by the political parties.
In the 2014 Kentucky election, a key player was the "Kentucky Opportunity Coalition," a group
supporting Mitch McConnell, Republican of Kentucky,[16] whom the New York Times editorial board
has described as "the most prominent advocate for unlimited secret campaign spending in
Washington."[5] The Kentucky Opportunity Coalition, a 501(c)(4) "social welfare" group,[17] raised
more than $21 million, while McConnell raised about $32 million and McConnell's opponent,
Democratic candidate Alison Lundergan Grimes, raised about $19 million.[17] According to a Center
for Public Integrity analysis of data provided by advertising tracking firm Kantar Media/CMAG, the
group ran more than 12,400 television advertisements.[17] Every Kentucky Opportunity Coalition's
television advertisements mentioned either McConnell or Grimes; overall, about 53 percent of the
group's ads praised McConnell while the rest were attack ads against Grimes.[18] The Kentucky
Opportunity Coalition relied heavily on political consultants in Washington, D.C. and Virginia linked to
Karl Rove's Crossroads groups,[19] and received $390,000 in a grant from Crossroads GPS.[17]
Described as "mysterious," the group was listed by a Post Office box,[17] and the only name formally
associated with the group was political operative J. Scott Jennings, a deputy political director in the
George W. Bush administration, a worker for McConnell's previous campaigns.[18] Melanie Sloan of
the watchdog organization Citizens for Responsibility and Ethics in Washington said that the Kentucky
Opportunity Coalition was "nothing more than a sham."[17]
In North Carolina, the pro-Tillis group "Carolina Rising" received nearly all (98.7%) of its funds from
Crossroads GPS; the Center for Responsive Politics highlighted this as an example of how Crossroads
GPS, a 501(c)(4) group, "evades limits on political activity through grants" to other 501(c)(4) groups.
[16][21] In the 2014 cycle, Crossroads GPS also gave $5.25 million to the U.S. Chamber of
Commerce, $2 million to the American Future Fund, and $390,000 to the Kentucky Opportunity
28Coalition.[21] In total, Crossroads GPS spent more than $13.6 million on grants to other groups, which
it described as being for the purposes of "social welfare."[21]
In 2014, the Democratic Party-aligned dark money group Patriot Majority USA, a 501(c)(4), spent
almost $13.7 million on "direct and indirect political campaign activities," airing 15,000 television ads
in targeted Senate races.[22] About half of the $30 raised by the group came from five anonymous
donors.[22] The group was led by Craig Varoga, "a staunch ally" of Senate Minority Leader Harry
Reid, Democrat of Nevada.[22]
In Alaska, Mark Begich was "one of the few Democratic candidates to come close to receiving as much
support from dark money as his Republican opponent."[15] The pro-Begich Alaska Salmon PAC,
funded entirely by the League of Conservation Voters and its Alaska affiliate, spent funds in support of
Begich.[15]
According to the Center for Responsive Politics, by October 2015, $4.88 million in dark money had
already been spent for the 2016 election cycle, "more than 10 times the $440,000 that was spent at this
point during the 2012 cycle."[11] The money was spent by six groups - five conservative groups
(including the U.S. Chamber of Commerce, which spent $3 million, and Americans for Prosperity,
which spent $1.5 million) and one liberal group (Planned Parenthood, which spent just under $75,000).
[11] According to Richard Skinner of the Sunlight Foundation, "the focus of early dark money being
spent in the 2016 cycle" is on competitive U.S. Senate elections and some U.S. House of
Representatives races.[11] However, dark money also is playing a role in the 2016 Republican
presidential primaries; by June 2015, at least four Republican presidential candidates were raising
funds via 501(c)(4) organizations: Bobby Jindal's America Next, Rick Perry's Americans for Economic
Freedom, John Kasich's Balanced Budget Forever, and Jeb Bush's Right to Rise.[23]
501(c) "dark money" groups are distinct from super PACs.[25]While both types of entity can raise and
spend unlimited sums of money, super PACs "must disclose their donors," while 501(c) groups "must
not have politics as their primary purpose but don't have to disclose who gives them money."[25]
However, a single individual or group can create both types of entity and combine their powers,
making it difficult to trace the original source of funds.[25][26] ProPublica explains: "Say some like-
minded people form both a Super-PAC and a nonprofit 501(c)(4). Corporations and individuals could
then donate as much as they want to the nonprofit, which isn't required to publicly disclose funders.
The nonprofit could then donate as much as it wanted to the Super-PAC, which lists the nonprofit's
donation but not the original contributors."[25] In at least one high-profile case, a donor to a super PAC
kept his name hidden by using an LLC formed for the purpose of hiding their personal name.[27] One
super PAC, that originally listed a $250,000 donation from an LLC that no one could find, led to a
subsequent filing where the previously "secret donors" were revealed.[28]
During the 2016 election cycle, "dark money" contributions via shell LLCs became increasingly
common.[29] The Associated Press, Center for Public Integrity, and Sunlight Foundation all "flagged
dozens of donations of anywhere from $50,000 to $1 million routed through non-disclosing LLCs to
super PACs" backing various presidential candidates, including Marco Rubio, Hillary Clinton, Ted
Cruz, John Kasich, Jeb Bush, and Carly Fiorina.[29] Bradley A. Smith, a former FEC chairman who is
now with the Center for Competitive Politics, a group that opposes campaign-finance reform, argues
that this practice is not problematic, writing that "it is possibly the making of a campaign contribution
in the name of another," a violation of existing law.[30]
29According to Kathy Kiely, managing editor of the Sunlight Foundation, "untraceable dark money is a
preferred tactic of conservatives, while Democrats tend to use traceable super PACs."[31]
The first federal law requiring disclosure of campaign contributions, the Federal Corrupt Practices Act,
was passed in 1910. By the late 1970s, virtually all states and the federal government required public
disclosure of campaign contributions and information on political donors. Most states and the federal
government also required public disclosure of information about donors and amounts spent on
independent expenditures, that is, expenditures made independently of a candidate's campaign.
In January 2010, at least 38 states and the federal government required disclosure for all or some
independent expenditures or electioneering communications, for all sponsors.[32]
Yet despite disclosure rules, it is possible to spend money without voters knowing the identities of
donors before the election.[33][34]In federal elections, for example, political action committees have
the option to choose to file reports on a "monthly" or "quarterly" basis.[35][36][37] This allows funds
raised by PACs in the final days of the election to be spent and votes cast before the report is due.
In addition to PACs, non-profit groups ranging from Planned Parenthood to Crossroads may make
expenditures in connection with political races. Since these non-profits are not political committees, as
defined in the Federal Election Campaign Act, they have few reporting requirements beyond the
amounts of their expenditures. They are not required by law to publicly disclose information on their
donors. As a result, voters do not know who gave money to these groups. Reports have disclosed
instances where non-profits were managed by close associates, former staff, or a candidate's family
member, and this has led to concern that the candidates benefiting from their expenditures would be
able to know who donated the funds to the non-profit group, but the public would not.[38] [39]
For example, in the 2012 election cycle, one organization, the National Organization for Marriage, or
NOM, operated two non-profit arms that received millions in donations from just a few donors. It in
turn funded several different PACs. While these PACs had to disclose that NOM contributed the funds,
they were not required to disclose who gave money to NOM.[40]
On March 30, 2012 a U.S. District Court ruled that all groups that spend money on electioneering
communications must report all donors that give more than $1,000.[41][42] However, this ruling was
overturned on appeal.[43]
Legislative and regulatory proposals and debate over dark moneyAccording to Columbia Law School's
Richard Briffault, disclosure of campaign expenditures, contributions, and donors is intended to deter
corruption.[45]
The Federal Elections Commission, which regulates federal elections, has been unable to control dark
money. According to the Center for Public Integrity, FEC commissioners are voting on many fewer
enforcement matters than in the past because of "an overtaxed staff and commissioner
disagreement."[12] The IRS (rather than the FEC) is responsible for oversight of 501(c)(4) groups.[12]
The IRS "found itself ill-prepared for the groundswell" of such groups taking and spending unlimited
amounts of money for political purposes in the wake of the U.S. Supreme Court's decision in Citizens
United v. Federal Election Commission in 2010.[12] The agency particularly "struggled to identify
which organizations appeared to be spending more than the recommended 50 percent of their annual
30budgets on political activities—and even to define what 'political spending' was."[12] When the IRS
began looking at nonprofit spending, it was accused of improper targeting in a 2013 controversy.[12]
"With the FEC and IRS duly sidelined" advocates for disclosure turned to the Securities and Exchange
Commission (SEC); nine academics from universities across the U.S. filed petitioned the SEC in
August 2011 for the agency to "develop rules to require public companies to disclose to shareholders
the use of corporate resources for political activities."[12] The petition received over a million
comments in the following month, "a record amount for the SEC, with the overwhelming majority of
voters asking for better disclosure."[12] According to Lucian Bebchuk, a Harvard professor of law,
economics, and finance who helped draft the petition, the request had drawn the support of "nearly a
dozen senators and more than 40 members of the House."[12] Under current SEC regulations, public
corporations must file a Form 8-K report to publicly announce major events of interest to shareholders.
[46] The Sunlight Foundation, a group which advocates for a comprehensive disclosure regime, has
proposed that the 8-K rule should be updated to require that aggregate spending of $10,000 on political
activities (such as monetary contributions, in-kind contributions, and membership dues or other
payments to organizations that engage in political activities) should be disclosed and made publicly
available via the 8-K system.[46] In 2015, Republicans in Congress successfully pushed for a rider in a
2015 omnibus spending bill that bars the IRS from clarifying the social-welfare tax exemption to
combat dark money "from advocacy groups that claim to be social welfare organizations rather than
political committees."[47]
Other provisions in the 2015 bill bar the SEC from requiring corporations to disclose campaign
spending to shareholders, and a ban application of the gift tax to nonprofit donors. The Obama
administration opposed these provisions, but President Obama eventually acceded to them in December
2015, with the White House declining to comment. The nonpartisan Campaign Legal Center said in a
statement that the dark-money provision ensures "that the door to secret foreign dollars in U.S.
elections remains wide open through secret contributions to these ostensibly 'nonpolitical' groups that
run campaign ads without any disclosure of their donors."[47]
The Center for Competitive Politics (CCP), chaired by former FEC chairman Bradley A. Smith,
opposes legislation to require the disclosure of dark-money groups, saying: "Our view is that many
people will be driven out of politics if they are forced to disclose their names and their personal
information. The purpose of disclosure is to help people monitor the government, not for the
government to monitor the people."[12] The Center for Competitive Politics views "dark money" as a
pejorative term, stating that the phrase "evokes an emotional, fearful reaction" and contending that
"many of the statistics published on the topic aim to mislead rather than enlighten."[48] The CCP
maintains that dark money "comprises a very small percentage of total campaign spending," calculating
the percent of money spent in federal elections by organizations that did not provide itemized
disclosure of their donors as 4.3% in 2012 and 3.7% in 2014.
The U.S. Department of Energy was complicit in the processing of Dark Money payola cycling to
Obama's financiers as a 'hand-on' operator of a RICO-class crime.
All of the ruckus with Donald Trump and California/DOE VS. Trump is almost entirely based on West
Coast and New York corrupt senators, and their insiders, freaking out about their Dark Money
organized crime payola scam coming apart and getting exposed.
31There’s a reason why David Brock chooses to house an unregistered Professional Solicitor in his office
to raise money for his conglomerate of Super PACs and non-profits.
================================
FURTHER PROOF OF THE CRIMES AND LIES:
https://archive.fo/xCf3t
https://neonnettle.com/news/6471-pelosi-s-brother-in-law-received-737m-taxpayer-money-for-failed-
green-project
https://voat.co/v/whatever/2239148
https://www.thegatewaypundit.com/2019/02/watch-college-students-love-ocasio-cortezs-green-new-
deal-until-they-find-out-whats-really-in-it/
IN ADDITION TO OUR EYE-WITNESS, FIRST-HAND, VIEWING OF THESE CRIMES THESE
SMALL SAMPLES OF THE BROADCAST NEWS REPORTS, CONGRESSIONAL REPORTS, FBI
CASE EVIDENCE AND AGENCY REPORTS PROVE EVERY ASSERTION WE HAVE MADE:
- http://fbi-report.net
- All FBI case files referencing "Solyndra", "Kleiner Perkins", "Rare-Earth Mining", "Stock Market
Manipulation" and related search terms
- https://stopelonfromfailingagain.com
- http://londonworldwide.com
- https://www.thecreepyline.com
- https://fusion4freedom.com/about-gcf/
- https://fusion4freedom.com/the-green-corruption-files-archive/
- https://en.wikipedia.org/wiki/Angelgate
- https://en.wikipedia.org/wiki/High-Tech_Employee_Antitrust_Litigation
- https://www.cbsnews.com/news/cleantech-crash-60-minutes/
- https://www.cbsnews.com/news/congress-trading-stock-on-inside-information/
- https://www.businessinsider.com/congressional-insider-trading-revealed-on-60-minutes-2011-11
- https://www.law360.com/articles/366325/gop-report-slams-white-house-over-535m-solyndra-loan
- https://www.judicialwatch.org/press-room/press-releases/judicial-watch-announces-list-of-
washingtons-ten-most-wanted-corrupt-politicians-for-2012/
- http://www.npr.org/templates/story/story.php?storyId=140291210
- https://publicintegrity.org/federal-politics/fundraiser-for-obama-urged-solyndra-deal-from-the-inside/
- https://althouse.blogspot.com/2011/10/either-rahm-or-obama-himself-pushed-to.html
- https://archives-energycommerce.house.gov/sites/republicans.energycommerce.house.gov/files/
analysis/20120802solyndra.pdf
- https://republicans-oversight.house.gov/wp-content/uploads/2012/03/FINAL-DOE-Loan-Guarantees-
Report.pdf
32- https://docs.house.gov/meetings/SY/SY20/20160303/104591/HHRG-114-SY20-20160303-
SD002.pdf
- https://big.assets.huffingtonpost.com/email.pdf
- https://theintercept.com/2014/02/24/jtrig-manipulation/
- https://driftglass.blogspot.com/2014/02/the-deadly-british-viper-character.html
- https://nuclear-news.net/2014/02/28/western-intelligence-agencies-use-the-internet-fot-character-
assassination/
- http://blog.agupieware.com/2014/02/snowden-drip-government-funded.html
- https://freethoughtblogs.com/singham/2014/02/26/the-nsa-and-gchq-are-criminal-enterprises/
- http://vcracket.weebly.com
- https://mega.nz/#F!6Rk1hC7K!5FxlpPi_eG52GnYuN_JmeA
- http://videonet111.com
- http://atvm-loan.com
- http://causeofaction.org/assets/uploads/2015/07/ECF-No.-38.pdf
- http://causeofaction.org/assets/uploads/2015/07/ECF-No.-37.pdf
- http://docquery.fec.gov/cgi-bin/fecimg/?11971582033
- http://blogs.wsj.com/venturecapital/2014/02/05/fisker-investors-executives-hit-by-another-lawsuit-
kleiner-perkins-and-ray-lane-among-defendants/
- http://dealbook.nytimes.com/2013/05/07/a-humbled-kleiner-perkins-adjusts-its-strategy/
- http://www.mining.com/1-trillion-motherlode-of-lithium-and-gold-discovered-in-afghanistan/
- http://2.bp.blogspot.com/_VyTCyizqrHs/TBaffwKixYI/AAAAAAAAH74/Wee8LTQfo3k/s1600/
afghanminerals.jpg
- http://pubs.usgs.gov/fs/2007/3063/pdf-page.jpg
- https://news.wttw.com/sites/default/files/Letter%20from%20Bright%20Automotive%20to%20US
%20Dept%20of%20Energy.pdf
- https://gigaom.com/2010/08/18/the-greentech-vc-influence-over-washington/
- https://www.catholic.org/news/politics/story.php?id=42817
- https://europetodaynews.wordpress.com/2016/05/23/tesla-and-google-partnered-on-the-same-scam-
against-the-public/
- https://www.abc.net.au/news/2018-07-25/cobalt-child-labour-smartphone-batteries-congo/10031330
- https://www.washingtonpost.com/graphics/business/batteries/congo-cobalt-mining-for-lithium-ion-
battery/
- http://www.mining.com/1-trillion-motherlode-of-lithium-and-gold-discovered-in-afghanistan/
- https://www.dw.com/en/chiles-lithium-blessing-or-curse/a-43721539
- https://www.economist.com/the-americas/2017/06/15/a-battle-for-supremacy-in-the-lithium-triangle
- https://www.visualcapitalist.com/lithium-fuel-green-revolution/
- https://www.forbes.com/sites/jamesconca/2018/09/26/blood-batteries-cobalt-and-the-congo/
- https://www.forbes.com/sites/greatspeculations/2018/02/27/the-worlds-cobalt-supply-is-in-jeopardy/
- https://www.greentechmedia.com/articles/read/congo-cobalt-reliance-grows-despite-europe-
discoveries
- http://iopscience.iop.org/article/10.1088/1748-9326/aae9b1/pdf
https://www.mining-technology.com/features/featuremining-iran-endless-opportunity-corruption-and-
the-trump-question-5695882/
- https://www.brighteon.com/5809392344001
- https://business.financialpost.com/personal-finance/high-net-worth/frank-giustra-takes-a-break-from-
the-blade-runner-sequel-and-an-italian-olive-estate-to-return-to-his-first-love-a-gold-mine
- https://www.theglobeandmail.com/globe-investor/giustra-backed-lithium-x-plunges-on-doubts-about-
33chinese-buyer/article38156222/
- https://globalnewstimes.wordpress.com/tag/frank-guistra-and-hillary-clinton/
- http://www.dear-white-house.com
- http://archive.is/ox9pX
- https://www.gold-eagle.com/article/hypocrisy-most-foul
- https://www.washingtonpost.com/graphics/business/batteries/congo-cobalt-mining-for-lithium-ion-
battery/
- https://www.iisd.org/story/green-conflict-minerals/
- https://www.amnesty.org/en/latest/news/2017/09/the-dark-side-of-electric-cars-exploitative-labor-
practices/
- https://www.aljazeera.com/news/2017/07/dr-congo-loses-750m-corruption-mismanagement-
170721154134478.html
ORGANIZATIONS AND WITNESSES WHO CAN ALSO VERIFY THESE FACTS:
Home
http://www.fbi.gov
http://www.gao.gov
https://www.transparency.org
Judicial Watch
https://corruption123.com
https://wikileaks.org
https://causeofaction.org
Home
https://propublica.org
https://www.allsides.com/unbiased-balanced-news
http://wearethenewmedia.com
http://ec.europa.eu/anti_fraud/index_en.html
Home
http://www.iaaca.org/News/
http://www.interpol.int/Crime-areas/Corruption/Corruption
http://www.icac.nsw.gov.au/
http://www.traceinternational.org/
http://www.oge.gov/
https://ogc.commerce.gov/
Home
http://www.anticorruptionintl.org/
Homepage 2023 EOY
http://www.giaccentre.org/dealing_with_corruption.php
http://www.acfe.com/
https://www.oas.org/juridico/english/FightCur.html
https://www.opus.com/international-anti-corruption-day-businesses/
https://www.opengovpartnership.org/theme/anti-corruption
https://www.ethicalsystems.org/content/corruption
https://sunlightfoundation.com/
https://www.opensecrets.org/
http://peterschweizer.com/
34http://www.googletransparencyproject.org/
Marita Noon
http://www.nara.gov
pbedard@washingtonexaminer.com
The Archives from whistleblower@judiciary-rep.senate.gov
Congressperson Jim Jordan
Gary D. Conley
stone@stonecoldtruth.com
Philip Giraldi
allumbokhari@protonmail.com
David Bird – WSJ
Andrew@TheCitizensAudit.com
Congressperson Trey Gowdy
Congressperson Darrell Issa
William Barr, AG
Dan Epstein
Veronique de Rugy
http://www.projectveritasaction.com
GOOGLE BOSSES, INCLUDING ERIC SCHMIDT, TOLD ASSOCIATES: "OBAMA NEVER
WOULD HAVE BEEN ELECTED WITHOUT GOOGLE'S DIGITAL MASS PERCEPTION-
MANIPULATION AND OPINION-STEERING TECHNOLOGIES..." SEE MORE AT:
https://www.thecreepyline.com
Many thousands of additional person's, organization's and links available to prove the assertions...
35How Public Officials Are Bribed To Use
Government Agencies As Political Weapons
Against Citizens
- "DARK MONEY" IS THE WAY THAT CORRUPT POLITICAL CRIMINALS EXCHANGE
COMPENSATION, BRIBES AND INFLUENCE WITHOUT THE FBI CATCHING THEM. Public
officials do such onerous crimes because they, and their friends ,want to control and direct over five
trillion dollars of taxpayer cash into their, and their friends pockets. That check you write ion April 15
every year is the pot of gold that they are trying to put in their personal bank accounts. Some of them
will even kill to get that cash. A person is killed every few minutes for robberies involving less than
$25.00; Why would you doubt that corrupt politicians would not murder citizens and reporters for over
a trillion dollars?
- This is about a group of tech oligarchs, and their corrupt Senators, who commit crimes in order to
manipulate over a trillion tax dollars (YOUR MONEY) into their, and their friends pockets.
- They are felons yet they control some of the offices of the agencies who are supposed to arrest them.
Silicon Valley bought K Street and U.S. Senators, gave them more Dark Money than history has ever
seen and then had giant tech-law firms bribe, hit-job and blockade any attempts to solve the problem.
- Some of the largest bribes in American history were paid via billions of dollars of pre-IPO cleantech
stock, insider trading, real estate, Google search engine rigging and shadow-banning, sex workers,
revolving door jobs, nepotism, state-supported black-listing of competitors and under-the-table cash.
Why are these Silicon Valley Oligarchs and their K-Street law firms and lobbyists immune from the
law?
U.S. Senators, Agency Heads and Congress are bribed with: Billions of dollars of Google, Twitter,
Facebook, Tesla, Netflix and Sony Pictures stock and stock warrants which is never reported to the
FEC; Billions of dollars of Google, Twitter, Facebook, Tesla, Netflix and Sony Pictures search engine
rigging and shadow-banning which is never reported to the FEC; Free rent; Male and female
prostitutes; Cars; Dinners; Party Financing; Sports Event Tickets; Political campaign printing and
mailing services "Donations"; Secret PAC Financing; Jobs in Corporations in Silicon Valley For The
Family Members of Those Who Take Bribes And Those Who Take Bribes; "Consulting" contracts from
McKinsey as fronted pay-off gigs; Overpriced "Speaking Engagements" which are really just pay-offs
conduited for donors; Private jet rides and use of Government fuel depots (ie: Google handed out
NASA jet fuel to staff); Real Estate; Fake mortgages; The use of Cayman, Boca Des Tores, Swiss and
related money-laundering accounts; The use of HSBC, Wells Fargo, Goldman Sachs and Deustche
Bank money laundering accounts and covert stock accounts; Free spam and bulk mailing services
owned by Silicon Valley corporations; Use of high tech law firms such as Perkins Coie, Wilson
Sonsini, MoFo, Covington & Burling, etc. to conduit bribes to officials; and other means now
documented by us, The FBI, the FTC, The SEC, The FEC and journalists.
36FOR EXAMPLE:
David Brock’s Media Matters gave a $930,000 cash grant to David Brock’s Franklin Education Forum
David Brock’s Franklin Education Forum credited the Bonner Group for raising those funds, triggering
the 12.5% commission
David Brock paid the Bonner Group a $124,250 commission to solicit a cash grant … from himself!
IT DOESN’T STOP THERE
After the Franklin Education Forum retained $869,750, they sent a $816,224 cash grant to David
Brock’s The Franklin Forum:
Note: The ‘Franklin Education Forum’ is a 501(c)3, and ‘The Franklin Forum’ is a 501(c)4. They are
not the same company.
Since The Franklin Forum 501(c)4 paid Bonner a commission in 2013, it’s safe to assume fundraiser
received a $102,028 commission in 2014. Unfortunately, it’s hard to tell for sure. They still haven’t
filed their taxes for 2014!
LET’S RECAP
Say, for example, you donate $1,062,857 to Media Matters for America. This is how David Brock
would have used your charitable donation in 2014:
In the end, Brock’s solicitor would have pocketed $350,825, almost a third of your initial donation!
That’s a far cry from the advertised 12.5% commission.
As bizarre as that scenario may sound, this is exactly what David Brock did in 2014.
HOW CAN WE BE SURE THIS IS INTENTIONAL?
David Brock is the Chairman for each of these organizations! How could he not know what’s going
on?
He’s a hands-on Chairman. According to their tax returns, Brock allocates time, weekly, to his
organizations:
Furthermore, the New York Times reports that David Brock shares a summer rental in the Hamptons
with Mary Pat Bonner, the President of the Bonner Group!
David Brock will have a hard time claiming ignorance on this. These transfers are intentional. He
vacations with his solicitor. Case closed.
STILL NOT CONVINCED?
37David Brock didn’t even bother to give his organizations different phone numbers. They all share the
same phone number!
WHAT IF…?
We even located the Bonner Group’s solicitation agreement with Media Matters on Florida’s Gift
Givers’ Guide. Clarification on their commission can be found on page 2:
In English: Contractually, David Brock has the option to exclude certain contributions from triggering
the commission. In spite of this option, he intentionally chooses to trigger the 12.5% commission for
money grants between his organizations.
Note: Yes, we are making the assumption that all of Brock’s organizations have the same solicitation
agreement with the Bonner Group. Given that his organizations share the same address, board
members, and telephone number, we feel it’s safe to assume they also share the same solicitation
agreement.
THIS BARELY SCRATCHES THE SURFACE
Utilizing public facing tax returns, along with records submitted to the FEC, we mapped out all the
significant money transfers from 2014 that took place in Brock’s office:
This is all from just one year!
I have been asking myself lately; how were there so many corrupt people in the Obama
Administration? The only answer I can come up with is that Barack Obama himself was a very corrupt
person. Who else would have had so many corrupt people that he chose or tolerated in his
Administration.
Do you remember Lois Lerner from the IRS and Barack Obama asking her to go after his political
rivals using the most feared government agencies, the IRS. The last place you want to be is between the
government and your money.
Obama Attorney General Eric Holder who was found in Contempt of Congress for lying to Congress
and looking the other way on every illegal act Obama or someone in his administration perpetrated.
Secretary of Energy Steven Chu, earned his spot among Obama’s corrupt appointees thanks to his
admitted role in the “green energy” scams, specifically the Solyndra scandal in which the Obama gave
more than $500 million to a failed company and one of its key investors, Obama backer George Kaiser.
Do not forget Obama’s corrupt cabinet appointee Secretary of Health and Human Services Kathleen
Sebelius. According to the U.S. Office of Special Counsel, she was guilty of violating the Hatch Act by
campaigning for the president in her official capacity. Violators of this act are normally fired, but
Obama would not allow his AG Eric Holder to do any such thing. So Sibelius got off without
punishment after claiming she said she "... got a little caught up in the notion that the gains which had
been made would clearly not continue without the president’s reelection..."
38I am not even going into the details of the corrupt John Brennan former CIA Director and James
Clapper Director of National Intelligence.
And let us not forget about the most corrupt person Obama appointed and that was Hillary Clinton.
After thinking about all of the people above how could we not think Obama himself was the Godfather
of this mob?
Now let us add another and that is James Comey, former disgraced FBI Director. Politico is reporting
that on Friday night the FBI released a two-page summary former disgraced FBI Director James
Comey used to brief then President-elect Donald Trump on the “dossier” about Trump’s ties to Russia.
https://www.judicialwatch.org/press-room/press-releases/judicial-watch-uncovers-doj-records-
showing-numerous-bruce-ohr-communications-with-fusion-gps-and-christopher-steele/
The document, asserts that Christopher Steele, the person who compiled the dossier, was working “on
behalf of private clients” in his investigation of Trump’s possible ties to Russia. Comey was not honest
to the court because Steele was actually working for the DNC and Clinton campaign. Comey also did
not inform the court or President-Elect Trump Hillary Clinton and the Democratic Party paid the
Russian government via Steele and Fusion GPS for the opposition research document. Why didn’t
Comey inform the court or President-Elect Trump that the information came from the Russian
government: because then he would be admitting that the true collusion was between Hillary, the
Democratic Party and Russia.
No matter which political party corruption is found in we must drain the swamp of all these corrupt
people and prosecute them if we actually want to improve the political climate in the United States.
The key suspects under investigation for the crimes, attacks on the public and manipulation of
Democracy include:
Amy Pascal; Bill Daley; Bill Lockyer; Brian Goncher; Daniel Cohen; David Axelrod; David
Drummond; David Plouffe; David E. Shaw; Dianne Feinstein; Elon Musk; Eric Holder; Eric Schmidt;
John Zaccarro, Jr.; Frank Giustra; Nick Denton; Harry Reid; Haim Saban; Hillary and Bill Clinton; Ira
Ehrenpreis; Jay Carney; James Comey; Jared Cohen; Jeffrey Katzenberg; John Doerr; Harvey
Weinstein; Yasmin Green; Jonathan Silver; Ken Brody; Lachlan Seward; Judge Stewart M. Bernstein;
Larry Page; Google; Alphabet; YouTube; Facebook; In-Q-Tel; Amazon; Twitter; WordPress.Org; The
Law Firm of Perkins Coi; Mark Zuckerberg; Martin LaGod; Matt Rogers; Marc Benioff; Michael
Birch; S. Donald Sussman; Pierre Omidyar; Rahm Emanual; Raj Gupta; Ray Lane; Tom Perkins;
Robert Rubin; Rob Friedman; Reid Hoffman; Richard Blum; Robert Gibbs; Robert Shwarts; Roger
Altman; The Law Firm of Covington and Burling; Sanford Robertson; Steve Jurvetson; Steve Rattner;
Steve Westly; Steven Chu; Steve Spinner; Susie Tompkins Buell; George Soros; Warren Buffet; Tom
Steyer; The Clinton Foundation, Tim Draper; Valarie Jarrett; Jeffrey Epstein; Vinod Khosla; Michelle
Lee; The law firm of Wilson Sonsini Goodrich and Rosatti; Lawrence Summers; Marc Andreessen
Sheryl Sandberg; Yuri Milner; Fenwick & West LLP; James W. Breyer; McBee Strategic; Mike
Sheehy; Nancy Pelosi; Gilman Louie; Thomas J. Kim; Ping Li; Greylock Capital, Accel Partners; Jim
Swartz; Bank Menatep; Alisher Asmanov; Marc L. Andreessen; Peter Thiel; Clarion Capital; Richard
Wolpert; Robert Ketterson; David Kilpatrick; Tesla Motors; Solyndra; BrightSource; IDG Capital
Partners; Goldman Sachs; Morgan Stanley; State Street Corporation; JP Morgan Chase; Lloyd
39Blankfein; Jamie Dimon; Steve Cutler; Rodgin Cohen; Sullivan Cromwell, LLP; Jeff Markey; Steve
McBee; Michael F. McGowan; Toni Townes-Whitley; CGI Federal; Todd Y. Park; Frank M. Sands, Sr.;
Robin Yangong Li; Parker Zhang; Jonathan Goodman; Gawker Media; Jalopnik; Adrian Covert, John
Herrman; Gizmodo Media; K2 Intelligence; WikiStrat; Podesta Group; Fusion GPS; Think Progress;
Media Matters; Black Cube; Debbie Wasserman, The DNC Executive Committee; Correct The Record;
Stratfor; ShareBlue; Sid Blumenthal; David Brock; Barack Obama; Sen. Robert Menendez; Jerry
Brown; Ken Alex; Susan Rice; Kamala Harris; Bruce Ohr; Nellie Ohr; and other names to be identified
in court...
These parties appear to have exploited taxpayer government resources to line their pockets at tax payer
expense as proven by finance reports, FEC filings, Congressional studies, Panama Papers, espionage
journalism, state election reporting forms, Goldman Sachs and ICIJ Swiss Leaks documents and
journalists, on-staff whistle-blowers, covert accounts revelations, forensic audits, Congressional action
comparison charts and other evidence. Connected on XKEYSCORE, FBI, Palantir, Linkedin and other
investigative databases. Confirmed in cross-over financial dealings and transfers. Sourced as
beneficiaries and financiers of the activities.
40How You Can Become Your Own FBI And Take
Down Corrupt Agency Staff
- You Can Destroy ANY Corrupt Politician 100% Legally!
You will use high resolution video to capture the face of every person that works in the office that is
trying to use taxpayer resources to harm you. You will use open-source free software to rapidly cross-
check their faces, using facial recognition, across every Facebook, Linkedin, Google, YouTube,
Instagram and other social media outlet on the planet. This will create a digital dossier on each person
that is working to hurt you and their postings, emails, texts, event participations, etc. will soon reveal
their true agendas.
You will build a CIA-class dossier on each of them and then use that to turn them in to every agency
and regulator that has the power to fire, indict, prosecute and terminate them and their lives. They must
never be allowed to harm you, or other members of the public again!
Organized crime is alive and well in public offices across the nation. This is how you utterly destroy
any person who engages in it, using 100% legal tactics and the power of crowd-sourced law
enforcement.
FBI and other government officials will even help you do it. The voters will help you do it. Your
friends will help you do it. Total strangers will help you do it. The entire internet will help you do it.
You will use CIA-class databases, social media, public watch-dog technologies, FBI-quality monitoring
systems and open-source collaborative forensics comparison data to hunt down every: hooker, real
estate asset, male prostitute, mistress, secret email account, social media posting, family trust fund,
shell corporation, family stock market transaction, off-shore account, covert investment brokerage,
email, Uber and Lyft ride, hotel entry and exit, credit card transaction, Paypal account, search engine
manipulation, venture capital connection, Stanford University admissions bribe, expense account
abuse, taxpayer funds abuse, rape, sextortion, covert tech company stock they own under another name,
every party they attended, every tag they appear in on social media, every Cayman Island account,
every crooked CPA or law firm they have used, every lobbyist they ever paid....EVERYTHING.. and
you will drop the data into a simple database and cross matrix everything even better than the spy
agencies can do it..
...AND EXPOSE IT ALL. YOU WILL SUE THEM IN SMALL CLAIMS COURT. YOU WILL
LAUNCH CLASS ACTION LAWSUITS. YOU WILL HOLD PRESS CONFERENCES IN FRONT
OF THEIR HOMES. YOU WILL CONFRONT THEM WITH FACTS AT EVERY SINGLE TOWN
HALL AND PUBLIC APPEARANCE. YOU WILL PUT UP A BOOTH AT EVERY STREET FAIR
AND PUBLIC ASSEMBLY AREA AND HAND OUT LITERATURE. YOU WILL CREATE A
MASSIVE PUBLIC MEDIA CIRCUS. YOU WILL MAKE DISCLOSURE WEBSITES. YOU WILL
NOT LET THEM ESCAPE!
41Each person from each political office, lobby firm, law firm or company who engaged in the
subversion of the government and the bribery of public officials WILL have EVERY personal email
account, text message account, voice-mail hard drive, social media account, dating account or other
PERSONAL communications account examined via investigators. Such examinations shall begin from
the date of the opening of each account and run up to today. Law enforcement believes that such parties
used personal data systems to subvert the laws of public disclosure and engage in criminal financial
crimes and democracy subversion efforts.
You will be even more powerful than Ralph Nader, Julian Assange and Edward Snowden
COMBINED!
You will ensure that the public servants, who are your EMPLOYEES!!!!, are held accountable and
totally, completely devastated for their crimes against the public.
What Is An 'Extinction-Level Interdiction Program' For Corrupt Companies And
People?
By The Leesberg Foundation
It only works on corrupt companies that bribe, break the law, abuse employees, rape, tax evade, lie,
cheat, steal, run character assassinations, operate anti-trust violating monopolies, spy and are generally
dirty pigs.
That is why it works so well on Google, Gawker, Gizmodo, Jalopnik, Univision, Facebook, Tesla,
Goldman Sachs and other creepy corps who bribe, break the law, abuse employees, rape, tax evade, lie,
cheat, steal, run character assassinations, operate anti-trust violating monopolies, spy and are generally
dirty pigs.
'Extinction-level' means that the goal is to put them-out-of-business.
'Interdiction' means that the effort involves interrupting their corruption, crimes, bribes, payola and
sex trafficking.
It is a 'Program' because it is a constant, unwavering, long-term effort that the entire public population
is continually expanding and adding to the effort of.
The efforts are long and take many years but they always work.
If your company does not bribe, break the law, abuse employees, rape, tax evade, lie, cheat, steal, run
character assassinations, operate anti-trust violating monopolies, spy and they are not generally dirty
pigs then they have nothing to worry about.
If the truth can't hurt a Facebook, Google or Tesla then they should have no concern about the truth
being exposed.
42Alas, though, those companies are targeted for extinction and any smart investor should remove their
investment funds from those companies. The way that they are taken down includes exposing every
time each investor engages in a bribe, breaks the law, abuses employees, rapes, tax evades, lies, cheats,
steals, runs character assassinations, operates anti-trust violating monopolies, spies and is generally a
dirty pig.
Bill Cosby thought he could not be taken down. He was!
Enron thought they could not be taken down. They were!
Dick Nixon thought he could not be taken down. He was!
Hillary Clinton thought she could not be taken down! She was!
Theranos thought it could not be taken down! It was!
The list is endless. The fact is clear: If you cheat rather than compete you will be destroyed.
It is now easier than ever to kill a corrupt entity!
We have hard-fact FBI and CIA-class evidence that Google, Gawker, Gizmodo, Jalopnik, Univision,
Facebook, Tesla, Goldman Sachs and others are breaking the law and exist based on a criminal
operation. That is why they are going down! We witnessed them do the crimes. Their ex-employees and
federal investigators saw it too. That is why they are helping with the take-downs. Millions of web
users who hate corruption are helping too, using crowd sourced forensics.
The deaths of these crooked behemoths will be long, slow and hard..but the crash they make when they
finally fall will resound throughout history!
An Extinction-Level Interdiction Program known as an "ELIP" always guarantees that a corrupt
attacking corporation will:
A. Lose a minimum of one billion dollars in stock market and brand valuation from exposure of the
truth about them.
B. Suffer the firings or forced terminations of multiple senior staff.
C. Have draft FBI 302 forms authored and submitted to the relevant regional FBI offices where those
companies are located.
D. Have private investigators prepare case files on the company, or individual, and submit those to
every relevant law enforcement and regulatory agency on every continent.
E. Have every investor who has placed over $50,000.00 in the company investigated for tax fraud,
expense fraud, drug abuse, spousal abuse, sexual extortion, off-shore accounts, political bribery, kick-
backs, payola, under-the-table payments, real estate fraud, 501 c 3 and 501 c 4 charity fraud, self-
dealing, revolving door political payola and other relevant issues.
You will use 100% legal creative NON-Violence.
43This is an instruction book about how to destroy the most criminally corrupt politicians and dirt-bags in
the world. It teaches you how to wipe out any corrupt person, campaign, company or other entity
without breaking the law and to do so for very little expense and with no need for expert skills.
Any private citizen taxpayer has the right, the tools and the ability to do these things.
Why should you need to do this?
BECAUSE NONE OF THE PEOPLE YOU ARE PAYING TAXES TO ARE DOING
THEIR JOBS!
The local police, The FBI, The Courts, The SEC, The FEC, The Attorney Generals,The Mayors, The
City Supervisors, Your Senators, Your Congress- People.. ALL OF THEM HAVE RECENTLY BEEN
ARRESTED, INDICTED, FIRED AND/OR EXPOSED DOING CRIMES TO COVER UP THEIR
FRIEND'S CRIMES!
THEY HAVE ALL RECENTLY BEEN CAUGHT RUNNING FINANCIAL CRIMES AND
OPERATING STONE-WALL CAMPAIGNS IN ORDER TO KEEP THE PUBLIC FROM GETTING
JUSTICE!
You, the taxpayers, have nobody in the system that is on-your-side any more.
For example; The Silicon Valley Oligarchs pay-off the California Senators and they all put hundreds of
millions of dollars in their private bank accounts in the Cayman Islands. They got most of that money
from your paycheck and your tax payment every April.
They are not going to help you! They are going to continue to rob you while running their stock market
insider trading scams at your expense.
"Officials" in California may say "oh, my, that certainly sounds like a bad thing...you should report
that, immediately to your lawful representatives: Dianne Feinstein and Nancy Pelosi.." The fact is that
Feinstein and Pelosi are running some of the largest graft, payola, revolving door, nepotism and insider
treading scams in the whole crime scheme. So how can anyone expect you to go into their offices with
a straight face and expect them to help you?
Not only will they not help you, the second you leave their office, their staff will be on the phone to
Fusion GPS, Gizmodo and Gawker Media, Black Cube and Podesta Group to order those companies to
attack and destroy you. Your life will be ended.
If they get to do that to you, then you get to do it right back to them...except you are going to partner
with 300 million other voting taxpayers to utterly and completely wipe these dirty scumbag politicians
out forever.
You will destroy their brand, their finances, their power and their family legacy for the rest of time in
every history book that will ever be! You will expose them. You will shame them. You will peel their
whole filthy dynastic family empires open like a skinned possum!
44CIA, FSB and STAZI psychological warfare operatives are widely documented deploying techniques
that can brainwash you into killing your whole family, echo-chambering your whole factory to be either
for, or against, unions, believing mass media propaganda about totally fictional issues and other
subliminal mind tricks. There are tens of thousands of books and movies about how Madison Avenue
ad agencies use these tactics. Modern politicians created operations like In-Q-Tel and New America
Foundation to weaponize these tactics.
These are the tactics that corrupt politicians and sociopath Silicon Valley social media companies are
now using as political weapons against you.
They are not doing awful things like this to try to get you to believe that their political ideas are better.
They are doing awful things with your government and your media in order to rig the stock market so
they can buy more hookers, jet planes and mansions. You must shut them down before everything is
taken away from you and you have no options left for counter-measuring their crimes.
At the point that all of the public's hope, and all of the taxpayers options, are taken away. That is the
day the public starts shooting all of the politicians with actual guns.
This book was created to stop that potential violence and to give the public one last lawful and creative
non-violent option.
Average consumers are now wiping out the largest corrupt companies and politicians on Earth; and you
can do it too using one potent weapon: The Truth!
For the rest of time, the message must ring out loud and clear:
"DO NOT EVER RUN FOR POLITICAL OFFICE IF YOU OR YOUR COVERT
FINANCIERS WANT TO MAKE MONEY OFF OF IT. YOU WILL BE
WATCHED AND HUNTED DOWN FROM THE DAY YOU ANNOUNCE
YOUR CAMPAIGN."
The Public now has access to all of the same tools that the CIA, NSA, KGB, FBI and Fusion GPS have
and they have hundreds of millions more "agents" (voters) than all of those spy agencies combined.
---
In other books we have exposed all of the dirty tactics they use to operate their crimes. Now we are
exposing all of the methods that any members of the public can use to catch them and then use mass
media distribution to expose them.
The big anti-corruption check-list looks like this.
As you can see, it is well on the
way to being completed:
"1.) Build The Internet (Done)
2.) Put Movies And Music On The Internet To Get All Of The Base Demographics And Nose Pickers To
Come To A Collaborative Global Network (Done)
453.) Give Everybody On Earth All Of The Secrets About How Abused And Manipulated They Are By A
Handful of Evil Billionaires (Done)
4.) Expose The Manipulative Fraud Of Political Party Bosses (Done)
5.) Tell The Entire Planet, 1 Million People At A Time, How The Billionaires Companies Abuse Their
Privacy, Minds, Human Rights and Media Impressions (Done)
6.) Crash All of the Billionaires Main Stream “Fake News” Information Outlets by Exposing Them And
Giving All News Away For Free And Teaching People How To Make Free Newspapers (Done)
7.) Crash the Evil Billionaires Silicon Valley Companies, and Money, By Contacting 1 Million People
at a Time to Remind Them to Boycott Silicon Valley Companies and Their Products (Done)
8.) Contact Every Advertiser of Every Silicon Valley Billionaire and Warn Them To Pull All Ad Budgets
For the Companies Who Contribute to Political Campaigns (In Process)
9.) Make It So That Non-Main-Stream Candidates Can Run And Win By Exposing And Breaking Illicit
Election Rigging (Done)
10.) Sit Back And Watch The Fireworks (In Process)"
That check-list is very high-level.
Let's get down into the weeds and examine the details of the process.
You must become an FBI-Class, CIA-capable forensic investigator with your computer and mass social
networking.
You have access to all of the same tools and intellect that every FBI and CIA agent has access to. CIA
and FBI agents primarily sit at computers and track down connections. You can do that too using free
public software and groups of people that also hate political corruption. It is actually quite easy.
You know when something is wrong or when something "smells fishy". Now you can turn your
intuition and your public spirit into productive home-based forensic research that makes your nation
great again.
You will create public case files and gather news articles and related information in order to expose
each of the corrupt people that ruin this great country.
You will expose the dirty and illicit deeds of elected officials and their corrupt political financiers. All
of these actions are 100% legal and will be appreciated by non-corrupt law enforcement agencies and
the public:
- Expose their Hookers in widely released news and social media releases
- Expose their Rent Boys in widely released news and social media releases
46- Expose all of the bad dates and sex extortion they engaged in, in widely released news and social
media releases
- Expose their hidden family trust fund payola accounts, in widely released news and social media
releases
- Expose their shell corporations they use to hide from the IRS- Expose their mistresses
- Expose their addictions
- Expose their under-the-table payments
- Expose their illegal workers
- Expose their expensive cars, jewelry and homes that can't afford on a legal salary
- Expose their Cayman Island, Belize and Swiss hidden bank accounts
- Expose their personal email accounts they illegally used to hide government fraud
- Expose their illicit hidden email servers
- Expose their secret black-lists and start-up valuation rigging like in the Angel Gate Scandal
- Expose their Uber and Lyft GPS docs proving that they lied about where they went
- Expose their campaign financing records
- Expose their social media statements proving they are, or fund, ANTIFA or political disruption
programs
- Expose their money laundering
- Expose their connections to Pede groups and activities
- Expose their hotel records and videos of illicit hotel meetings
- Expose their PayPal, Bitcoin and credit card payments for illicit services and products
- Distribute creative Memes exposing their crimes
- File reports with their employers disclosing their crimes and tell the media you told their employers
- File many copies of criminal reports on them with all law enforcement entities
- Expose the members of their family that hide money for them or use their names to launder money
- Photo and video document all of their meetings and actions
- Aggregate all of the video investigations about them on many different web video sites
- Write and distribute books, articles and white-papers about their crimes
- Promote new laws that makes what that criminal uses as a loop-hole, illegal
- Re-release all of the above every six months in order to keep the crimes in people's minds
- Use "The Striesand Effect" to it's maximum technical potential and research how the "Effect" works
- Grow your network of voters and taxpayers who are helping you and make your supporter network
bigger every day
- Expose the manner in which Google, Facebook and Twitter fight against exposing their criminal
friends
- Use Google, Facebook and Twitter's own illicit tools against them and expose them with "Hypocrisy
Exposure" when they censor
- Confront them in every single public presentation they attend and expose them in public
- Create coordinated groups of volunteers to expose the troll farms and click farms of the corrupt
manipulators
- Expose and publicly document all of their illicit real estate holdings, mansions and property scams-
Release of the details of their crooked secret partnership contracts
- Place a First Amendment informational exhibit outside of their offices, homes and each door they go
through each day
- Write them weekly and tell them that they are exposed. Send them certified letters proving that you
told them that you know
- Document and publicly expose all of their trips and expenditures
47- Document the identities of the service trucks that come to their homes and offices
- Photo document all of their workers, interns and secretaries
- Contact their staff and ask them to report the illicit deeds of their employer. Provide media and police
contact information.
- Help their staff and the public organize class-action abuse law suits against the perpetrators
- File RICO Racketeering lawsuits against the corrupt
- File FEC charges, ie: Google provided over $1B of search engine rigging for Obama's elections but
never reported that to the FEC
- Expose their stock market manipulations and valuation rigging in Wall Street Pump-And-Dump
scams
- Expose the insider trading where Senators own the stock that they just provided government perks for
- Expose politicians that make tens of millions more dollars, from mystery funds, than their salary
should allow
- Use pictures of expensive toys that politicians acquired from taxpayer funds via crony payola
- When they are hacked (which you legally can't do) expose the hacked material globally as far as
possible (which you legally can do)
- Read and analyze all publicly posted hacked emails and point out the crimes it exposes
- Meme any criminal remarks that the target makes
- And thousands of additional fully legal public investigation methods...
Every single crooked politician, and their corrupt billionaire financiers, have been using these tactics
against the public for 20 years. Silicon Valley, David Brock's groups, John Podesta's groups, Stratfor,
Black Cube, Gawker/Gizmodo and a host of illicit organizations have used all of the above tactics to
attack domestic taxpaying citizens in the USA.
Now YOU get to give them a taste of their own medicine!
Pelosi, Feinstein and their financiers use Gizmodo Media, Gawker Media, Jalopnik, and Univision to
run retribution vendetta hatchet job media attacks on members of the public that speak out about their
crimes. In exchange here is what the public is "giving back" to Gizmodo Media, Gawker Media,
Jalopnik,
and Univision:
"1. Added Gizmodo, Jalopnik, Univision prostitute and rent boy uses to master
Google docs files and forwarded to law enforcement…
2. Sent duplicates of reports previously provided to James Comey to
Christopher Wray at the FBI and regional FBI offices…
3. Added Gizmodo, Jalopnik, Univision tax evasion records to master Google
docs files and reported them to IRS, EU and InterPol…
4. Added Gizmodo, Jalopnik, Univision political party past work records to
master Google docs files and copied that to adversarial political parties and
reporters…
485. Updated every case file on each Gizmodo, Jalopnik, Univision past and
present worker in master Google docs files and forwarded them to investigative
organizations…
6. Source backers for Gizmodo lawsuits and contact every party attacked by
Gizmodo Media to introduce backers, litigation firms and draft case merits to
assist with their cases…
7. Launch Gizmodo expose' national news articles and distribute by hand to all
related reports in AP, Reuters, Muck Rack, DNC and GOP mailing lists, with
background data sets…
8. Release video of London young men who claim to have been abused by Nick
Denton…
9. Release video of Manhattan young men who claim to have been abused by
Nick Denton…
10. Add Gizmodo, Jalopnik, Univision political email communications with
Obama White House to master Google docs files and distribute to AP, Reuters,
Muck Rack, DNC and GOP mailing lists, with background data sets…
11. Privately contact Gizmodo, Jalopnik, Univision current and ex-staff and offer
cash awards for whistle-blowing…
12. Submit formal "requests for charges" with SEC, FBI, FTC, IRS, FEC, FCC,
GAO, DOJ and other agencies…
13. File Grand Jury requests for hearings into tax evasion, money laundering,
stock rigging, collusion, election manipulation…
14. Prepare rapid-response story points for the Gang-of-20 reporters to counter
any Gawker/Gizmodo façades of First Amendment rights with proof of why
Gizmodo, Jalopnik, Univision gave up their rights by engaging in crimes…
15. Destroy the investors and company trying to revive Gawker Media by
exposing the dirty finances, fake ad stats, click-farms, hookers, money
laundering, FEC fraud and other dirt behind them…
16. Deliver the full dossier on them to the public and the media..."
That is just a tiny example from one small campaign.
The pain must be extreme when a politician, who is hired to protect you, puts a thirty million dollar kill
order on you that you could never possibly over-come.
Taxpayers should not be destroyed because they "did the right thing" and reported a crime.
49A business only has the right to sell a product or service. They do not have the right to manipulate
politics.
A politician only has the right to serve YOU.
They do not have the right to serve themselves criminal money laundering and insider trading.
50When The White House Runs An Attack
Program Against You
A Payback Playbook Against Corruption
"When You Political And Corporate Goons Attack Us And Operate Character Assassination Smear
Campaigns, This Is What You Can Expect:"
“Dear Attackers:
You may work for a sociopath industrialist oligarch. You may actually be one of those sociopath
billionaire tech oligarchs. You may only be one of the low-life blogger scum at the bottom of their
political pig trough. In any case, you are going down.
You have more money than us but we have more time, dedication, creativity and voting members of the
public on our side. We also have the law, ethics and tactical resources on our side.
Because you chose to try to end our lives we are coming after you and we are coming for the rest of
your life, the rest of your families life and for 100 years of your legacy in any historical publications.
We play the “long game” for people like you. Everything that will now happen to you will be done
100% legally and the law enforcement and intelligence community will help us do it to you.
Slowly, over time, you will notice your life falling apart. Your business efforts will fail. Your romances
will fail. Your investments will fail. Your health will fail. Things will seem to be falling apart, in slow
motion, all around you. You must know that YOU brought everything on yourself that is about to
happen.
Every member of the public that hears about your deviant, repulsive activities will help make what is
going to take place come to fruition.
Here is what you can look forward to:
We will have justice served up with a big cold scoop of vengeance.
You will eventually be bankrupted but that will be the least of your worries.
Take a look at any stock you own, right now. Your stock market valuations are going to dive. Your
brand is going to crash. Your profits will start to vaporize. By the time you notice, it will be too late.
51Using these proven tactics and methodologies, a task-force of voters, journalists, investigators and
forensic experts have caused over 300 billion dollars in losses to corrupt companies and individuals
and bankrupted their criminally evil operations with 100% legal procedures. Any member of the public
can do this too, on their own, without breaking a single law and with the gratitude of every citizen.
As a target, let’s take a look at the corrupt politicians that work for dirty corporations. Let's deeply
examine the Silicon Valley oligarch financiers, their dirty corporate law firms and their media attack
squads that have demonstrated a cycle of attack and harm to citizens.
Now we are ripping you, and your kind, a new one.
Signed,
Your Victims”
---------------------------------------------------------------------
GOOGLE RIGS ELECTIONS AND CHARACTER ASSASSINATION ATTACKS AROUND
THE GLOBE ON ORDERS FROM BARACK OBAMA AND DEBBIE WASSERMAN
BY ROBERT EPSTEIN
Authorities in the UK have finally figured out that fake news stories and Russian-placed ads are not the
real problem. The UK Parliament is about to impose stiff penalties—not on the people who place the
ads or write the stories, but on the Big Tech platforms that determine which ads and stories people
actually see.
Parliament’s plans will almost surely be energized by the latest leak of damning material from inside
Google’s fortress of secrecy: The Wall Street Journal recently reported on emails exchanged among
Google employees in January 2017 in which they strategized about how to alter Google search results
and other “ephemeral experiences” to counter President Donald Trump’s newly imposed travel ban.
The company claims that none of these plans was ever implemented, but who knows?
While U.S. authorities have merely held hearings, EU authorities have taken dramatic steps in recent
years to limit the powers of Big Tech, most recently with a comprehensive law that protects user
privacy—the General Data Protection Regulation—and a whopping $5.1 billion fine against Google for
monopolistic practices in the mobile device market. Last year, the European Union also levied a $2.7
billion fine against Google for filtering and ordering search results in a way that favored their own
products and services. That filtering and ordering, it turns out, is of crucial importance.
As years of research I’ve been conducting on online influence has shown, content per se is not the real
threat these days; what really matters is (a) which content is selected for users to see, and (b) the way
that content is ordered in search results, search suggestions, news feeds, message feeds, comment lists,
and so on. That’s where the power lies to shift opinions, purchases, and votes, and that power is held by
a disturbingly small group of people.
52I say “these days” because the explosive growth of a handful of massive platforms on the internet—the
largest, by far, being Google and the next largest being Facebook—has changed everything. Millions of
people and organizations are constantly trying to get their content in front of our eyes, but for more
than 2.5 billion people around the world—soon to be more than 4 billion—the responsibility for what
algorithms do should always lie with the people who wrote the algorithms and the companies that
deployed them.
In randomized, controlled, peer-reviewed research I’ve conducted with thousands of people, I’ve
shown repeatedly that when people are undecided, I can shift their opinions on just about any topic just
by changing how I filter and order the information I show them. I’ve also shown that when, in multiple
searches, I show people more and more information that favors one candidate, I can shift opinions even
farther. Even more disturbing, I can do these things in ways that are completely invisible to people and
in ways that don’t leave paper trails for authorities to trace.
Worse still, these new forms of influence often rely on ephemeral content—information that is
generated on the fly by an algorithm and then disappears forever, which means that it would be
difficult, if not impossible, for authorities to reconstruct. If, on Election Day this coming November,
Mark Zuckerberg decides to broadcast go-out-and-vote reminders mainly to members of one political
party, how would we be able to detect such a manipulation? If we can’t detect it, how would we be able
to reduce its impact? And how, days or weeks later, would we be able to turn back the clock to see what
happened?
Of course, companies like Google and Facebook emphatically reject the idea that their search and
newsfeed algorithms are being tweaked in ways that could meddle in elections. Doing so would
undermine the public’s trust in their companies, spokespeople have said. They insist that their
algorithms are complicated, constantly changing, and subject to the “organic” activity of users.
This is, of course, sheer nonsense. Google can adjust its algorithms to favor any candidate it chooses no
matter what the activity of users might be, just as easily as I do in my experiments. As legal scholar
Frank Pasquale noted in his recent book “The Black Box Society,” blaming algorithms just doesn’t cut
it; the responsibility for what an algorithm does should always lie with the people who wrote the
algorithm and the companies that deployed the algorithm. Alan Murray, president of Fortune, recently
framed the issue this way: “Rule one in the Age of AI: Humans remain accountable for decisions, even
when made by machines.”
Given that 95 percent of donations from Silicon Valley generally go to Democrats, it’s hard to imagine
that the algorithms of companies like Facebook and Google don’t favor their favorite candidates. A
newly leaked video of a 2016 meeting at Google shows without doubt that high-ranking Google
executives share a strong political preference, which could easily be expressed in algorithms. The
favoritism might be deliberately programmed or occur simply because of unconscious bias. Either way,
votes and opinions shift.
It’s also hard to imagine how, in any election in the world, with or without intention on the part of
company employees, Google search results would fail to tilt toward one candidate. Google’s search
algorithm certainly has no equal-time rule built into it; we wouldn’t want it to! We want it to tell us
what’s best, and the algorithm will indeed always favor one dog food over another, one music service
53over another, and one political candidate over another. When the latter happens … votes and opinions
shift.
Here are 10 ways—seven of which I am actively studying and quantifying—that Big Tech companies
could use to shift millions of votes this coming November with no one the wiser. Let’s hope, of course,
that these methods are not being used and will never be used, but let’s be realistic too; there’s generally
no limit to what people will do when money and power are on the line.
1. Search Engine Manipulation Effect (SEME)
Ongoing research I began in January 2013 has shown repeatedly that when one candidate is favored
over another in search results, voting preferences among undecided voters shift dramatically—by 20
percent or more overall, and by up to 80 percent in some demographic groups. This is partly because
people place inordinate trust in algorithmically generated output, thinking, mistakenly, that algorithms
are inherently objective and impartial.
But my research also suggests that we are conditioned to believe in high-ranking search results in much
the same way that rats are conditioned to press levers in Skinner boxes. Because most searches are for
simple facts (“When was Donald Trump born?”), and because correct answers to simple questions
inevitably turn up in the first position, we are taught, day after day, that the higher a search result
appears in the list, the more true it must be. When we finally search for information to help us make a
tough decision (“Who’s better for the economy, Trump or Clinton?”), we tend to believe the
information on the web pages to which high-ranking search results link.
As The Washington Post reported last year, in 2016, I led a team that developed a system for
monitoring the election-related search results Google, Bing, and Yahoo were showing users in the
months leading up to the presidential election, and I found pro-Clinton bias in all 10 search positions on
the first page of Google’s search results. Google responded, as usual, that it has “never re-ranked search
results on any topic (including elections) to manipulate political sentiment”—but I never claimed it did.
I found what I found, namely that Google’s search results favored Hillary Clinton; “re-ranking”—an
obtuse term Google seems to have invented to confuse people—is irrelevant.
Because (a) many elections are very close, (b) 90 percent of online searches in most countries are
conducted on just one search engine (Google), and (c) internet penetration is high in most countries
these days—higher in many countries than it is in the United States—it is possible that the outcomes
ofupwards of 25 percent of the world’s national elections are now being determined by Google’s search
algorithm, even without deliberate manipulation on the part of company employees. Because, as I
noted earlier, Google’s search algorithm is not constrained by equal-time rules, it almost certainly ends
up favoring one candidate over another in most political races, and that shifts opinions and votes.
2. Search Suggestion Effect (SSE)
When Google first introduced autocomplete search suggestions—those short lists you see when you
start to type an item into the Google search bar—it was supposedly meant to save you some time.
Whatever the original rationale, those suggestions soon turned into a powerful means of manipulation
that Google appears to use aggressively.
My recent research suggests that (a) Google starts to manipulate your opinions from the very first
character you type, and (b) by fiddling with the suggestions it shows you, Google can turn a 50–50 split
54among undecided voters into a 90–10 split with no one knowing. I call this manipulation the Search
Suggestion Effect (SSE), and it is one of the most powerful behavioral manipulations I have ever seen
in my nearly 40 years as a behavioral scientist.
How will you know whether Google is messing with your election-related search suggestions in the
weeks leading up to the election? You won’t.
3. The Targeted Messaging Effect (TME)
If, on Nov. 8, 2016, Mr. Zuckerberg had sent go-out-and-vote reminders just to supporters of Mrs.
Clinton, that would likely have given her an additional 450,000 votes. I’ve extrapolated that number
from Facebook’s own published data.
Because Zuckerberg was overconfident in 2016, I don’t believe he sent those messages, but he is surely
not overconfident this time around. In fact, it’s possible that, at this very moment, Facebook and other
companies are sending out targeted register-to-vote reminders, as well as targeted go-out-and-vote
reminders in primary races. Targeted go-out-and-vote reminders might also favor one party on Election
Day in November.
My associates and I are building systems to monitor such things, but because no systems are currently
in place, there is no sure way to tell whether Twitter, Google, and Facebook (or Facebook’s influential
offshoot, Instagram) are currently tilting their messaging. No law or regulation specifically forbids the
practice, and it would be an easy and economical way to serve company needs. Campaign donations
cost money, after all, but tilting your messaging to favor one candidate is free.
4. Opinion Matching Effect (OME)
In March 2016, and continuing for more than seven months until Election Day, Tinder’s tens of
millions of users could not only swipe to find sex partners, they could also swipe to find out whether
they should vote for Trump or Clinton. The website iSideWith.com—founded and run by “two friends”
with no obvious qualifications—claims to have helped more than 49 million people match their
opinions to the right candidate. Both CNN and USA Today have run similar services, currently
inactive.
I am still studying and quantifying this type of, um, helpful service, but so far it looks like (a) opinion
matching services tend to attract undecided voters—precisely the kinds of voters who are most
vulnerable to manipulation, and (b) they can easily produce opinion shifts of 30 percent or more
without people’s awareness.
At this writing, iSideWith is already helping people decide who they should vote for in the 2018 New
York U.S. Senate race, the 2018 New York gubernatorial race, the 2018 race for New York District 10
of the U.S. House of Representatives, and, believe it or not, the 2020 presidential race. Keep your eyes
open for other matching services as they turn up, and ask yourself this: Who wrote those algorithms,
and how can we know whether they are biased toward one candidate or party?
5. Answer Bot Effect (ABE)
More and more these days, people don’t want lists of thousands of search results, they just want the
answer, which is being supplied by personal assistants like Google Home devices, the Google Assistant
on Android devices, Amazon’s Alexa, Apple’s Siri, and Google’s featured snippets—those answer
55boxesat the top of Google search results. I call the opinion shift produced by such mechanisms the
Answer Bot Effect (ABE).
My research on Google’s answer boxes shows three things so far: First, they reduce the time people
spend searching for more information. Second, they reduce the number of times people click on search
results. And third, they appear to shift opinions 10 to 30 percent more than search results alone do. I
don’t yet know exactly how many votes can be shifted by answer bots, but in a national election in the
United States, the number might be in the low millions.
6. Shadowbanning
Recently, Trump complained that Twitter was preventing conservatives from reaching many of their
followers on that platform through shadowbanning, the practice of quietly hiding a user’s posts without
the user knowing. The validity of Trump’s specific accusation is arguable, but the fact remains that any
platform on which people have followers or friends can be rigged in a way to suppress the views and
influence of certain individuals without people knowing the suppression is taking place. Unfortunately,
without aggressive monitoring systems in place, it’s hard to know for sure when or even whether
shadowbanning is occurring.
7. Programmed Virality and the Digital Bandwagon Effect
Big Tech companies would like us to believe that virality on platforms like YouTube or Instagram is a
profoundly mysterious phenomenon, even while acknowledging that their platforms are populated by
tens of millions of fake accounts that might affect virality.
In fact, there is an obvious situation in which virality is not mysterious at all, and that is when the tech
companies themselves decide to shift high volumes of traffic in ways that suit their needs. And aren’t
they always doing this? Because Facebook’s algorithms are secret, if an executive decided to bestow
instant Instagram stardom on a pro-Elizabeth Warren college student, we would have no way of
knowing that this was a deliberate act and no way of countering it.
The same can be said of the virality of YouTube videos and Twitter campaigns; they are inherently
competitive—except when company employees or executives decide otherwise. Google has an
especially powerful and subtle way of creating instant virality using a technique I’ve dubbed the Digital
Bandwagon Effect. Because the popularity of websites drives them higher in search results, and
because high-ranking search results increase the popularity of websites (SEME), Google has the ability
to engineer a sudden explosion of interest in a candidate or cause with no one—perhaps even people at
the companies themselves—having the slightest idea they’ve done so. In 2015, I published a
mathematical model showing how neatly this can work.
8. The Facebook Effect
Because Facebook’s ineptness and dishonesty have squeezed it into a digital doghouse from which it
might never emerge, it gets its own precinct on my list.
In 2016, I published an article detailing five ways that Facebook could shift millions of votes without
people knowing: biasing its trending box, biasing its center newsfeed, encouraging people to look for
election-related material in its search bar (which it did that year!), sending out targeted register-to-vote
reminders, and sending out targeted go-out-and-vote reminders.
56I wrote that article before the news stories broke about Facebook’s improper sharing of user data with
multiple researchers and companies, not to mention the stories about how the company permitted fake
news stories to proliferate on its platform during the critical days just before the November election—
problems the company is now trying hard to mitigate. With the revelations mounting, on July 26, 2018,
Facebook suffered the largest one-day drop in stock value of any company in history, and now it’s
facing a shareholder lawsuit and multiple fines and investigations in both the United States and the EU.
Facebook desperately needs new direction, which is why I recently called for Zuckerberg’s resignation.
The company, in my view, could benefit from the new perspectives that often come with new
leadership.
9. Censorship
I am cheating here by labeling one category “censorship,” because censorship—the selective and
biased suppression of information—can be perpetrated in so many different ways.
Shadowbanning could be considered a type of censorship, for example, and in 2016, a Facebook
whistleblower claimed he had been on a company team that was systematically removing conservative
news stories from Facebook’s newsfeed. Now, because of Facebook’s carelessness with user data, the
company is openly taking pride in rapidly shutting down accounts that appear to be Russia-connected
—even though company representatives sometimes acknowledge that they “don’t have all the facts.”
Meanwhile, Zuckerberg has crowed about his magnanimity in preserving the accounts of people who
deny the Holocaust, never mentioning the fact that provocative content propels traffic that might make
him richer. How would you know whether Facebook was selectively suppressing material that favored
one candidate or political party? You wouldn’t. (For a detailed look at nine ways Google censors
content, see my essay “The New Censorship,” published in 2016.)
10. The Digital Customization Effect (DCE)
Any marketer can tell you how important it is to know your customer. Now, think about that simple
idea in a world in which Google has likely collected the equivalent of millions of Word pages of
information about you. If you randomly display a banner ad on a web page, out of 10,000 people, only
five are likely to click on it; that’s the CTR—the “clickthrough rate” (0.05 percent). But if you target
your ad, displaying it only to people whose interests it matches, you can boost your CTR a
hundredfold.
That’s why Google, Facebook, and others have become increasingly obsessed with customizing the
information they show you: They want you to be happily and mindlessly clicking away on the content
they show you.
In the research I conduct, my impact is always larger when I am able to customize information to suit
people’s backgrounds. Because I know very little about the participants in my experiments, however, I
am able to do so in only feeble ways, but the tech giants know everything about you—even things you
don’t know about yourself. This tells me that the effect sizes I find in my experiments are probably too
low. The impact that companies like Google are having on our lives is quite possibly much larger than I
think it is. Perhaps that doesn’t scare you, but it sure scares me.
The Same Direction
57OK, you say, so much for Epstein’s list! What about those other shenanigans we’ve heard about: voter
fraud (Trump’s explanation for why he lost the popular vote), gerrymandering, rigged voting machines,
targeted ads placed by Cambridge Analytica, votes cast over the internet, or, as I mentioned earlier,
those millions of bots designed to shift opinions. What about hackers like Andrés Sepúlveda, who spent
nearly a decade using computer technology to rig elections in Latin America? What about all the ways
new technologies make dirty tricks easier in elections? And what about those darn Russians, anyway?
To all that I say: kid stuff. Dirty tricks have been around since the first election was held millennia ago.
But unlike the new manipulative tools controlled by Google and Facebook, the old tricks are
competitive—it’s your hacker versus my hacker, your bots versus my bots, your fake news stories
versus my fake news stories—and sometimes illegal, which is why Sepúlveda’s efforts failed many
times and why Cambridge Analytica is dust.
“Cyberwar,” a new book by political scientist Kathleen Hall Jamieson, reminds us that targeted ads and
fake news stories can indeed shift votes, but the numbers are necessarily small. It’s hard to overwhelm
your competitor when he or she can play the same games you are playing.
Now, take a look at my numbered list. The techniques I’ve described can shift millions of votes without
people’s awareness, and because they are controlled by the platforms themselves, they are entirely
noncompetitive. If Google or Facebook or Twitter wants to shift votes, there is no way to counteract
their manipulations. In fact, at this writing, there is not even a credible way of detecting those
manipulations.
And what if the tech giants are all leaning in the same political direction? What if the combined weight
of their subtle and untraceable manipulative power favors one political party? If 150 million people
vote this November in the United States, with 20 percent still undecided at this writing (that’s 30
million people), I estimate that the combined weight of Big Tech manipulations could easily shift
upwards of 12 million votes without anyone knowing. That’s enough votes to determine the outcomes
of hundreds of close local, state, and congressional races throughout the country, which makes the free-
and-fair election little more than an illusion.
Full disclosure: I happen to think that the political party currently in favor in Silicon Valley is, by a hair
(so to speak), the superior party at the moment. But I also love America and democracy, and I believe
that the free-and-fair election is the bedrock of our political system. I don’t care how “right” these
companies might be; lofty ends do not justify shady means, especially when those means are difficult
to see and not well understood by either authorities or the public.
Can new regulations or laws save us from the extraordinary powers of manipulation the Big Tech
companies now possess? Maybe, but our leaders seem to be especially regulation-shy these days, and I
doubt, in any case, whether laws and regulations will ever be able to keep up with the new kinds of
threats that new technologies will almost certainly pose in coming years.
I don’t believe we are completely helpless, however. I think that one way to turn Facebook, Google,
and the innovative technology companies that will succeed them, into responsible citizens is to set
upsophisticated monitoring systems that detect, analyze, and archive what they’re showing people—in
effect, to fight technology with technology.
58As I mentioned earlier, in 2016, I led a team that monitored search results on multiple search engines.
That was a start, but we can do much better. These days, I’m working with business associates and
academic colleagues on three continents to scale up systems to monitor a wide range of information the
Big Tech companies are sharing with their users—even the spoken answers provided by personal
assistants. Ultimately, a worldwide ecology of passive monitoring systems will make these companies
accountable to the public, with information bias and online manipulation detectable in real time.
With November drawing near, there is obviously some urgency here. At this writing, it’s not clear
whether we will be fully operational in time to monitor the midterm elections, but we’re determined to
be ready for 2020.
- Robert Epstein is a senior research psychologist at the American Institute for Behavioral Research
and Technology in California. Epstein, who holds a doctorate from Harvard University, is the former
editor-in-chief of Psychology Today and has published 15 books and more than 300 articles on internet
influence and other topics. He is currently working on a book called “Technoslavery: Invisible
Influence in the Internet Age and Beyond.” His research is featured in the new documentary “The
Creepy Line.” You can find him on Twitter - Robert Epstein is a senior research psychologist at the
American Institute for Behavioral Research and Technology in California. Epstein, who holds a
doctorate from Harvard University, is the former editor-in-chief of Psychology Today and has
published 15 books and more than 300 articles on internet influence and other topics. He is currently
working on a book called “Technoslavery: Invisible Influence in the Internet Age and Beyond.” His
research is featured in the new documentary “The Creepy Line.” You can find him on Twitter
@DrREpstein.@DrREpstein.
-------------------------------------------------------------
Dear Public:
They use criminally corrupt and illicit operations designed to steal taxpayer monies and they character
assassinate, defame, murder, black-list, and monopolize industries against anyone who speaks out
against them.
They formed a business and political manipulation “Cartel” intended to inflict corruption upon the
United States Federal Government, The New York State Government and the California State
Government, as defined by law under RICO Racketeering Statutes for the purpose of manipulating the
value of stock market holdings and controlling political policy decisions. They violated “Treason” laws
against the nation.
The criminally corrupt are enabled by criminally corrupt law firms who spend all day operating legal
evasion schemes. Public efforts took down the Brobeck law firm and hundreds of others that were
doing such crime cover-ups. There are many more needing to be terminated. Wilson Sonsini, Perkins
Coi, Covington and Burling are targeted for termination next. Watch the TV show called “Queen Of
The South” and watch how the cartel lawyer for the main drug queen is actually running the system.
Every lawyer like that needs to be hunted down and 100% legally terminated.
59These criminally corrupt people, companies and organizations are now going to experience payback,
for their crimes against society, for the rest of their time on Earth. Their historical legacy after they die
will remember each of them, in every history book, as: “...political criminals, insider trading mobsters
and crony taxpayer abusing scum...”.
Society provides only 3 options when these people try to take your life and your ethical society: 1.) Kill
them – This is illegal. 2.) Sue them - While it is easy to sue them for their crimes, their criminally
corrupt law firms will only blockade and/or delay such litigation. 3.) Expose them and boycott them –
This has proven to work best.
Because they are scumbags who have been accused, by reporters, employees, spouses and tipsters, of
very evil bribery, sex abuse, drug deals, political crimes, tax evasion, crony government payola,
industry black-lists, money laundering, defamation, libel, slander, misogyny, stock market rigging,
election manipulation, global search engine fake news, employee abuse and other horrific crimes
against society. Exposing them, and their enablers, is proven method to take them down. A person,
company or organization who commits crimes has always, according to historical forensics data, been
indicative as only just one small part of a deeply infected body which is fully corrupt and one which
requires termination.
The take-down effort must last for the rest of their lives. It must not just be a passing fad inspired by a
single news expose’. Society must never forget about what they did and never forgive them for
attacking and damaging you, as a citizen, and for damaging and abusing society.
You will learn how to wipe out their eco-system. You will investigate, expose and demand prosecution
of their corrupt:
A.) Law Firm Corporations
B.) CPA Firms
C.) Investment Banks
D.) Crony Politicians
E.) Fake Money Laundering ‘Charities’
F.) False Front Stock Market Accounts
G.) Covert Family Trust Funds And Shell Corporations
H.) Internet Search Engine Manipulation Services
I.) PR And Advertising Agency News Cover-Up Services
J.) Offshore Money Laundering Services
K.) And Every Other Intermediary Money Laundering Conduit...
There are now massive free database software systems the public can use to build your collaborative
case files. CERN in Switzerland uses billions of dollars of free global database software that you can
use too. You will use the web to create shared public collaboration peer-to-peer crime interdiction
databases. The databases have every piece of information about the bad guys that was ever created, ie:
all of their addresses, account numbers, tax records, bank accounts, dating site records, phone numbers,
fax numbers, IMEI device records, IP addresses, device serial numbers, every lover they cheated on,
service calls, drug deals, hookers, rent boys, Uber and Lyft trip addresses, neighbors, GPS records, etc.
All of this information can be legally acquired by the public. These narcissistic criminals put most of it
60out on the web themselves. The public has already built their own versions of Palantir, XKEYSCORE,
and other CSI database tools. You must now use these tools to end corruption.
If you have the funds, you can hire ex-FBI, CIA, NSA, GCHQ and other top intelligence and crime
interdiction experts. They have ways of watching the bad guys every second of every day. Many of
them are already doing it out of a sense of public service and you can find them on Voat.co,
Reddit.com, 4Chan and tens of thousands of online web sleuth and citizen investigator sites.
Did you know that WiFi and the ceramic objects around you can can make it look like there are not
even walls where the bad guys are right now? Science has created a new world in which technology
can see through walls and there is, LITERALLY, no place crooks can hide!
Face recognition can also source up every image of them that was on security cameras, store cameras,
restaurant cameras, Google and Bing image databases, social networks, dating sites, traffic cameras,
hotel and motel cameras and everything that has ever recorded their face; which is public domain.
Everything they are connected to will be connected to them and psychologically analyzed. A map of
every “secret” meeting they had each day can now be computer generated in minutes.
If these political crooks ever, for the rest of their life, cheat on taxes, take money off-the-books, lie on
an application, get arrested, get sued, buy drugs, buy sex, cheat, hide money, use off-shore conduits,
set-up an illicit trust fund or shell corporation, get an STD, lie on a dating site, abuse or extort an
employee, abuse a co-worker, plagiarize, break the law, run a real estate scam, hide insider stock
trading, provide political campaign services without filing detailed and accurate FEC disclosures,
support a political campaign, spend or receive any money that they do not report, etc… THE PUBLIC
CAN NOW CATCH THEM!
There is now no place on Earth a corrupt politician or their corrupt financier can hide from the crowd-
sourced investigations. The public now has investigators online across the globe. The public can now
count on friends in Congress, journalists, law enforcement and the intelligence community to help
taxpayers never let the corrupt out of their sights!
You, as a PUBLIC INVESTIGATOR never have to do creepy illicit things, like they do, so you have
nothing to worry about.
THEY have PLENTY to worry about. These tactics only work on Bad Guys like them!
Each of these crooks are, today, sitting at the edge of the same precipice that BILL COSBY, FOREX,
SOLYNDRA, ABOUND SOLAR, A123, ENERDEL, AMY PASCAL, E.F.HUTTON, RADIO
SHACK, ENRON, MCI WORLDCOM, EASTERN AIRLINES, STANDARD OIL, ERIC HOLDER,
STEVEN CHU, ARTHUR ANDERSON, DELOREAN, PETS.COM, BEAR STEARNS, BEATRICE
FOODS, HEALTHSOUTH, ALLEN STANFORD, TYCO, LANCE ARMSTRONG, PARMALAT,
BANINTER, HSBC, GLOBAL CROSSING LTD., BLACKBERRY, HIH INSURANCE, IMCLONE,
DEUTSCHE BANK (SPY CASE), URBAN BANK, JEROME KERVIEL, BARCLAYS BANK, BRE-
X, FISKER, BARINGS BANK, PATRICIA DUNN, SIEMENS AG, PETROBAS, FERNANDO
MARCOS, KELLOG BROWN AND ROOT, BAE SYSTEMS, KERRY KHAN, ALCATEL-LUCENT
SA, PRESIDENT RICHARD NIXON, HARVEY WEINSTEIN, ERIC SCHNIDERMAN, JAMES
COMEY...and many, many more, sat at just before they slid down their filthy funnels straight to hell.
61We all hope they enjoy the ride! Our public efforts took those players down! If the crooks think they
are immune, they are 100% wrong! Google, Facebook, Twitter, Kliener Perkins, Snapchat, Musk, and
the rest of the Silicon Valley Cartel should expect a life-time of investigations.
Here are a few of the thousands of 100% legal methods for wiping out creeps like them.
These corrupt politicians, the Silicon Valley Mafia, their political shills and their crony companies can
be terminated from the comfort of any voter’s living room.
This only works on criminals and the corrupt.
The “good guys” have nothing to fear.
Our goal is to get over 300 million voters working on these efforts ASAP:
Step-By-Step Termination Instructions For The Public To Use On Corrupt Targets:
“- Make sure your interdiction of their illicit deeds lasts the rest of their life. Make it your hobby and
engage in it every month. Put it on your calendar to have a monthly action day.
- Bankrupt their corrupt companies by contacting EVERY single advertising director for EVERY
company that advertises with them to show them the evidence and encourage them to stop advertising
with the suspect under threat of boycott.
- List out every past employee of the tabloid that was used to attack the taxpayers.
- Bankrupt their corrupt companies by contacting EVERY single employee that works for them to show
them the evidence and encourage them to quit.
- Bankrupt their corrupt companies by contacting EVERY single investor that funds them to show them
the evidence and encourage them to divest.
- Use “Espionage Journalism” like Project Veritas does. Sneak in to the bad guys operation using your
cell phone as a broadcast camera and film the crooks doing crooked things.
- Contact billionaire’s (ie: Peter Thiel, Larry Ellison, etc.) to get them to sponsor a RICO, or other kind
of lawsuit, against these corrupt parties. Use proxies to sue the corrupt (ie: Get Thiel to pay for some
other guy to sue Gawker for you). The Legal Proxy is one of your biggest assets. You can get billions
of dollars of lawsuits executed against corrupt mega giants. Make Hulk Hogan be YOUR proxy. He
takes all of the risk and YOU get to see a criminally corrupt oligarch (ie: Nick Denton and
Gawker/Gizmodo Media) ground into the dirt. Read the news daily and PACER.GOV and FIND
YOUR PROXY!
62- Bankrupt their corrupt companies by contacting EVERY user of their company, via mass media and
personal out-reach, to show them the evidence and encourage them to cancel their subscriptions and
‘poison’ their data by filling their profiles with fantasy data.
- See the movie: “DARK MONEY’ ! Understand what “Dark Money” is. Then cut off every possible
source of the bad guys “Dark Money and expose every party involved in Dark Money schemes.
- Write every government agency with a short, concise, detailed complaint letter and say IN YOUR
LETTER that “THIS LETTER IS ON FOIA PUBLIC RECORD”. These days, all government
documents are leaked, hacked or FOIA’d so assume the public will be reading your letter. Compose
your letter as if you were writing it for the audience of the Jerry Springer show so that the public will
be interested in it, excited about it and amused by it. This will help the public help you to push your
issue. Audacious controversy gets traction.
- Bankrupt their corrupt companies by contacting EVERY single member of Congress and regulatory
agencies to show them the evidence and demand, in writing, a federal investigation.
- Bankrupt their corrupt companies by exposing corrupt sources of supply to the news and the public;
ie: Elon Musk uses “blood cobalt” mines in the Congo which rely on child labor and mercenaries to
operate the cobalt mineral mines.
- Expose the covert sex cults (ie: Pizza Gate, NXIUM, Burning Man, Mission Control, Power
Exchange, etc.) that they frequent.
- Look on Linkedin and other databases to contact their former interns to see if they sexually or
mentally abused that intern and help that intern find lawyers (ie: Lawless Firm, AllRed, etc.).
- All of the data of famous corrupt persons and corporations has been hacked and acquired by many,
many parties over the last decade. Watch for it to get leaked on the web or go search the ICIJ,
Wikileaks and related databases for keywords about your targets. Expose what you find to the public.
Cross reference what you find with the Palantir, Taleo, Bitcoin Trace, PayPal Trace, VISA Trace, D&B
Insider, Gust-Scan, etc. commercially available databases and you will have an even more powerful
search than the NSA’s XKEYSCORE tool.
- Expose the trust funds, shell corporations and real estate contracts that they and their family own and
make sure the IRS and SEC knows about those slush fund pots. Find all of their insider trading payola
scams and expose them.
- Expose every reporter and ‘stock analyst’ that is actually a shill for the corrupt. Call them out by name
in press releases and your own news articles. Demand to see their financial records if they claim to
have never been paid by the corrupt entity in question.
- Expose the racist, tribal, misogynist organizations that the majority of their executive hires are part of.
- Investigate them and share your investigation data, from public data resources, on databases. All of
their addresses, account numbers, tax records, bank accounts, dating site records, phone numbers, fax
numbers, IMEI device records, IP addresses, device serial numbers, etc. are on public record.
63- As Comey, et al; proved, there are crooks at the FBI...but there will always be, at least, one Elliot
Ness kind of good guy at the FBI. DO report your findings to the FBI, in writing, but report to EVERY
main, and regional FBI office, in writing, with a carbon copy to the media. It only takes one good FBI
agent to get an official FBI case going. The same goes for the SEC, The EU and the CFTC.
- These incredibly abusive people have an inordinate number of divorce lawsuits for abusive behavior.
Showcase the most revealing text from those abusive divorce court filings.
- Write ‘Request For Prosecution’ requests to every major law enforcement agency and send copies of
those requests to every other law enforcement agency and independent news reporters.
- If they run for office, confront them (legally) at public speaking events and hand out one page fliers
about their crimes to the public at these events. Name their crony financial backers out loud at these
events.
- File charges with the FEC for campaign finance violations. Ie: In one year Google reported a million
in campaign contribution cash to one party but they actually provided many billions of campaign
contributions via search engine rigging and perception manipulation services. Report that to the FEC
and demand to know what the FEC is doing about it. Ask the FEC, in writing, every month until you
get an answer in writing.
- Don’t just ‘follow the money’. Make fun charts and diagrams of the illicit funds routes and mass
distribute those graphics.
- Meme them forever.
- Uncover every: illicit sex partner and who they cheated on; drug deals; hooker; rent boy; Uber and
Lyft trip route; neighbors who complained about them; GPS records, social media posting that hinted at
a political agenda, etc. All of this information can be legally acquired. They put most of it out on the
web themselves and agreed to let Facebook, Uber and Google sell the data.
- Search every face recognition database with automated search tools. They agreed to allow their image
on databases for security cameras, Walmart cameras, restaurant cameras, Google and Bing image
databases, social networks, dating sites, traffic cameras, hotel and motel cameras and everything that
has ever recorded their face; which is public domain. Check out what they were doing at each place
they were recorded.
- Report every illicit deed done by the corrupt to large Congressional, news writer, social network and
voter mass distribution systems.
- Learn ‘Corporate Veil Protection Strategies’ and How to Bust Them With Doxing And Public
Lawsuits’.
- Break their cover-ups. Carbon copy every Inspector General (IG), reporter and social media resource
you can find. Never allow only a few people to be the only ones that know what you uncovered. Tell
everyone and never stop finding new people to tell. Use the “Streisand Effect”.
64- If they ever, for the rest of their life: cheat on taxes, take money off-the-books, lie on an application,
get arrested, get sued, buy drugs, buy sex, cheat, hide money, use off-shore conduits, set-up an illicit
trust fund or shell corporation, get an STD, lie on a dating site, abuse or extort an employee, abuse a
co-worker, plagiarize, break the law, run a real estate scam, hide insider stock trading, provide political
campaign services without filing detailed and accurate FEC disclosures, support a political campaign,
spend or receive any money that they do not report, etc.; THEN YOU EXPOSE THEM AND THE
ILLICIT ACTIONS THEY TOOK.
- Educate yourself by typing this phrase into the top 5 non-Google search engines: “How To Be A
Private Investigator” and read all of the results. Try more searches, like: “Investigation methods” or
“Background check methods” or “Investigate a politician”, etc. There are thousands of other legal
techniques in addition to those few listed here. They all work if you are persistent.
- Learn how to put a covert media alarm in ‘Corporate Poison Pills’ and find ‘Criminal Back-Dating’.
- Track the spouses finances of corrupt Senators and expose the crony deals to the world.
- Make certain that you find every other voter and community group who might help you. Support their
efforts and share what you have uncovered with them. Use the web to guarantee that there is no place
on Earth they can hide from justice. Work to mesh investigators, Congress, journalists, law
enforcement, intelligence community, voters and your friends and family to never let them out of your
sights!
- Use social media, press releases, direct mail, PR and publicity stunts to seek out and join every other
person or group, in the world, who also hates corruption. Share these notes with them and ask them to
“pass them around...”
Hundreds of corrupt public officials have now been terminated since the main public web corruption
purge efforts began in 2009. The corrupt are fools if they think they are immune. There is no “invisible
cloak of corruption”. Every single day a shocking new set of revelations ends the career or some, now
notorious, well known political figure.
If the corrupt think they hid their deeds in private texts, whispered restaurant conversations, secret
home servers, the back seats of Uber and Lyft, closed doors in the back room or Cayman Islands hotel
rooms THEY COULD NOT BE MORE MISTAKEN!
Every trust fund that they and their family own has been tracked.
Every Goldman Sachs, JP Morgan, Wells Fargo, and other I-Bank account they, and their corrupt
family own, has been tracked and cross referenced to every political action they participated in that
resulted in valuation increases to their crony insider accounts.
Every stock market account they and their family own has been tracked and cross referenced to every
political action they took that might have increased the valuation of those stocks. Every sale of stock
they engaged in is being analyzed for “pump-and-dump” illegality. ICIJ and Wikileaks still have tens of
65thousands of investigative documents that need to be reviewed. Volunteer to help find keywords and
incrimination data in those records.
Every dirty off-shore account in Switzerland, the Caymans, Brazil and all of their other hiding places
has been tracked and data-based on fully resourced online tracking databases.
Every person these criminal politicians ever communicated with on a dating site is being contacted.
Any abuse, sexual misdeeds, sexting, porno pictures and lies are being documented and reported.
Dating sites sell their user data and all of their server records, since inception, are available to the
public, investigators and law enforcement with a single credit card purchase thanks to Facebook,
Google and Axciom. They caught two different NY AG’s by reading their Match.com messages.
The Russians, Chinese, activists and bored teens have been entering the electronic device back doors
on every router and consumer electronics device for decades and vacuuming up every record and file
on every corporate and government network. Now they sell, or freely provide, those records to every
public-interest law suit litigant to help them sue corrupt politicians and their financiers.
If they ever beat or abused a woman or child, it will be uncovered and reported just like Harvey,
Huma’s Weiner and the New York AG were outed!
Hundreds of thousands of new non-main-stream, non-party-controlled, non-corporate owned news
outlets have been created and they now reach the majority of the voting public. Hundreds of thousands
of new voters are invited to these sites every hour, around the world. These news sites are exposing
them and exposing the “Main Stream Fake News” that the corrupt thought they controlled.
There is no under-age sex scheme that they are involved in that will not be found out and exposed.
There is no male or female prostitute that they used that will not be found out and exposed.
There are no abuse charges in your divorce filings and other documents that will not be uncovered.
There is no intern that they sexually abused that will not be protected when they tell their story about
them.
TIPS FOR THE TAXPAYING PUBLIC:
For major anti-corruption lawsuit efforts we had to find the hidden money that corrupt Silicon Valley
political financing billionaires had spent billions of dollars to hide. How hard was it to peel the skins
off of Google’s onion? Thanks to modern law enforcement and intelligence technology, it was not hard
at all.
The fluency and practice of piercing the corporate veil & alter ego liability shields of political
manipulation bosses such as George Soros, Eric Schmidt, Larry Page, Elon Musk and their colleagues,
has become increasingly important in recent years due to changes in the law and business cycles.
As more small taxpayers need to help hunt down the corrupt, it is increasingly critical for taxpayers to
be fluent with the cutting-edge techniques and best tools to pierce & dissolve the corporate veil, as well
66as determine alter ego liability. The growing number of bankruptcies, foreclosures, and judgments has
dramatically increased the need for forensic experts proficient in the science of effective judgment
enforcement and asset recovery against the Silicon Mafia collection of corrupt California tech
companies.
Ie: Any corrupt Department of Energy employer or contractor can now be sued, lose their home and
have the courts transfer all of their assets away.
It is critical for action groups to understand the best strategies to suck dry the corporate assets in
judgments for cases and how to sue individual State and Federal workers.
Any member of the public can now begin piercing of the Google corporate veil, navigating complex
determinations on corporate liability, strategies involving legal alter ego, and breaking open both
corporate & personal liability with your home computer.
We use tools that not only include, but exceed, the capabilities of XKEYSCORE, Palantir, Taleo,
Bitcoin Trace, PayPal Trace, VISA Trace, D&B Insider, Gust-Scan, and hundreds of other executive
asset tracking and intelligence engines.
You, as a voter, need to learn how to:
• Expose Veil Protection Strategies and How to Bust Through Them
• Expose Liabilities for the Obligations of the Entity That Wilson Sonsini Created For Google & Tesla
and How We Busted Through Them In Less Than 24 Hours
• Employ Best Practices in Litigating the Veil Piercing Case in a Gawker Media-Like Laundering
Operation
• Snag The Corrupt With Veil Piercing Tactics & Fraudulent Conveyances With Sting Operations
• Inform The Corrupt About How Dire Their Situations Are In the New Information Age
• Expose Corporate Entities Used to Diminish Liability And Use Them As Evidence Against The
Corrupt
• Understand the Alter Ego of Insane Silicon Valley Tech Billionaires
• Run Reverse Veil Piercing Investigations
• Connect the Separate "Personalities" of the Corporation & Shareholders
From the underlying substantive law to practical aspects of asset protection planning (i.e., what works
and what does not), new groups are teaching the public everything they need to know about dissolving
corporate and executive asset protection like butter on a frying pan.
67From Gawker to Enron and from Solyndra to Nigerian War Lords, From Steven Chu and Eric Holder to
Brian Goncher and Steve Jurvetson; taxpayers are now only a few mouse clicks away from the deepest
family trust fund hide-aways and the darkest sexual services transactional relationship disclosure.
The public can now see how to uncover assets from tort plaintiffs, lenders, government entities and
other creditors, hidden in thousands of corporations, partnerships, LLCs and offshore entities. Online
web sleuths who are distinguished CIA-FBI-NSA-Class staff will teach you specific approaches and
solutions, including the most effective tactics, best practices, and the cutting-edge strategies to peel an
Eric Schmidt or a John Doerr veil open like a Taco, 100% legally.
The public is learning various ways, from the very simple to the very sophisticated, to expose specific
assets of State and Federal corrupt employees and illicit contractors: houses, bank and brokerage
accounts, private islands, billionaire bunkers, hookers with billionaires homes in their names, rent-boy
services, rental real estate, businesses and professional practices and retirement plans. Sue Obama?
Yes! He is now a private, corrupt citizen!
Every taxpayer is now able to easily acquire the most effective strategies and latest law in destroying
all corrupt asset protection for the criminal titans.
You, as a taxpayer, can learn and use these methods:
• Practical Goals and Limitations of Asset Protection – Google bosses were never as safe as their
consultants told them they were
• Picking the Right Structure to Trick an Oligarch Into Incriminating himself
• Understanding Fraudulent Transfers and How To Get Their Relatives To Disclose Them
• Effectively Planning for Possible Challenges From Their Corrupt CPA’s
• Busting Multi-Entity Structures For The Fake Sheathing of Business Assets
• Dealing with Successor Liability; Get The Money From The Next Guy
• Using Check-the-Box Election As Incrimination Evidence
• Charging Order Protection and Tearing It Apart
• Best Practices on Picking the Right Jurisdiction
• Single Member LLCs, Poison Pills and Criminal Back-Dating
Every bad and immoral thing the corrupt did yesterday will be on the lead stories in the Wall Street
Journal tomorrow.
68Use this document as your check-list. Try to accomplish everything on it against the most corrupt entity
you see in the news. It does not matter how big they are. These tactics work on a corrupt entity of ANY
size!
Not only is this effort 100% legal, it is your moral obligation to undertake it. Even if you don’t care
about the moral issues, you should care about the fact that your personal assets will increase and the
quality of your life will improve as this program increases in effectiveness.
In “The 25% Revolution—How Big Does a Minority Have to Be to Reshape Society?” David Noonan
describes how this sort of program by a committed few can influence the many and sweep away social
conventions. In fact MASS, PEER-TO-PEER, CROWD-SOURCED POLITICAL CORRUPTION
INTERDICTION has already moved to the influence of many.
Social change—from evolving attitudes toward gender and marijuana to the rise of Donald Trump to
the emergence of the Black Lives Matter and #MeToo movements—is a constant. It is also mysterious,
or so it can seem. For example, “How exactly did we get here?” might be asked by anyone who lived
through decades of fierce prohibition and now buys pot at one of the more than 2,000 licensed
dispensaries across the U.S.
A new study about the power of committed minorities to shift conventional thinking offers some
surprising possible answers. Published this week in Science, the paper describes an online experiment
in which researchers sought to determine what percentage of total population a minority needs to reach
the critical mass necessary to reverse a majority viewpoint. The tipping point, they found, is just 25
percent. At and slightly above that level, contrarians were able to “convert” anywhere from 72 to 100
percent of the population of their respective groups. Prior to the efforts of the minority, the population
had been in 100 percent agreement about their original position.
“This is not about a small elite with disproportionate resources,” says Arnout van de Rijt, a sociologist
at Utrecht University in the Netherlands who studies social networks and collective action, and was not
involved in the study. “It's not about the Koch brothers influencing American public opinion. Rather,
this is about a minority trying to change the status quo, and succeeding by being unrelenting. By
committing to a new behavior, they repeatedly expose others to that new behavior until they start to
copy it.”
The experiment was designed and led by Damon Centola, associate professor in the Annenberg School
of Communications at the University of Pennsylvania. It involved 194 people randomly assigned to 10
“independent online groups,” which varied in size from 20 to 30 people. In the first step group
members were shown an image of a face and told to name it. They interacted with one another in
rotating pairs until they all agreed on a name. In the second step Centola and his colleagues seeded
each group with “a small number of confederates…who attempted to overturn the established
convention (the agreed-on name) by advancing a novel alternative.”
For the second step, as Centola explains it, the researchers began with a 15 percent minority model and
gradually increased it to 35 percent. Nothing changed at 15 percent, and the established norm remained
in place all the way up to 24 percent.
69The magic number, the tipping point, turned out to be 25 percent. Minority groups smaller than that
converted, on average, just 6 percent of the population. Among other things, Centola says, that 25
percent figure refutes a century of economic theory. “The classic economic model—the main thing we
are responding to with this study—basically says that once an equilibrium is established, in order to
change it you need 51 percent. And what these results say is no, a small minority can be really
effective, even when people resist the minority view.” The team’s computer modeling indicated a 25
percent minority would retain its power to reverse social convention for populations as large as
100,000.
But the proportion has to be just right: One of the groups in the study consisted of 20 members, with
four contrarians. Another group had 20 members and five contrarians—and that one extra person made
all the difference. “In the group with four, nothing happens,” Centola says, “and with five you get
complete conversion to the alternative norm.” The five, neatly enough, represented 25 percent of the
group population. “One of the most interesting empirical, practical insights from these results is that at
24 percent—just below the threshold—you don’t see very much effect,” adds Centola, whose first
book, How Behavior Spreads: The Science of Complex Contagions, comes out this month. “If you are
those people trying to create change, it can be really disheartening.” When a committed minority effort
starts to falter there is what Centola calls “a convention to give up,” and people start to call it quits. And
of course members have no way to know when their group is just short of critical mass. They can be
very close and simply not realize it. “So I would say to Black Lives Matter, #MeToo and all of these
social change movements that approaching that tipping point is slow going, and you can see
backsliding. But once you get over it, you’ll see a really large-scale impact.”
Real-life factors that can work against committed minorities—even when they reach or exceed critical
mass—include a lack of interaction with other members, as well as competing committed minorities
and what’s called “active resistance”—which pretty well describes the way many people in 2018
respond to political ideas with which they disagree. But even with such obstacles, Centola says the
tipping point predicted in his model remains well below 50 percent.
Certain settings lend themselves to the group dynamics Centola describes in his study, and that includes
the workplace. “Businesses are really great for this kind of thing,” he says, “because people in firms
spend most of their day trying to coordinate with other people, and they exhibit the conventions that
other people exhibit because they want to show that they’re good workers and members of the firm. So
you can see very strong effects of a minority group committed to changing the culture of the
population.”
The other environment in which the 25 percent effect is particularly evident, Centola says, is online—
where people have large numbers of interactions with lots of other people, many of them strangers.
This raises some tricky questions: Can a bot stand in for a member of a committed minority? And can a
committed minority be composed of bots and the real people the bots influence, so that bots are
actually driving the change? According to Centola, “In a space where people can’t distinguish people
from bots, yes. If you get a concerted, focused effort by a group of agents acting as a minority view,
they can be really effective.”
You owe it to society, and yourself, to fight against political and corporate corruption.
Taxpayers cannot afford to let corrupt corporate bullies win!
70-------------------------------------------------------------------
This site was created with the help of FBI, CIA, DOJ, Police and Congressional experts in order to
confirm that all of these methods are legal and effective.
READ MORE:
Peter Eigen: How to expose the corrupt | TED …
Some of the world's most baffling social problems, says Peter Eigen, can be traced to systematic,
pervasive government corruption, hand-in-glove with global companies. In his talk, Eigen describes the
thrilling counter-attack led by his organization, Transparency International.
cached proxied
Latest News - Exposing the Truth about Corrupt …
The March 24th and 27th articles point to a serious amount of potential corruption in the EPSO. First,
you report that the County Attorney (Amy Folsom) recommends the …
cached proxied
https://dirtyelder.com/latest-news-blogs/
Peter Eigen: How to expose the corrupt | TED Talk - TED.com
Let me talk about my own experience. I used to work as the director of the World Bank office in ...
cached proxied
Peter Eigen: How to expose the corrupt - YouTube
http://www.ted.com Some of the world's most baffling social problems, says Peter Eigen, can be ...
cached proxied
Sidney Powell – Author of the Bestseller Licensed …
“That our government is corrupt is the only conclusion. This book helps the people understand the
nature of this corruption—and how it is possible for federal prosecutors to …
cached proxied
https://sidneypowell.com/
Why exposing and preventing corruption is important - Independent ...
Why exposing and preventing corruption is important. Undetected and unchecked corruption in the
public sector can cause serious damage including:.
cached proxied
https://www.icac.nsw.gov.au/about-corruption/why-expose-corruption
Doxing - Wikipedia
71Doxxing (from dox, abbreviation of documents) or doxing is the Internet-based practice of researching
and broadcasting private or identifiable information (especially personally identifiable information)
about an individual or organization.
cached proxied
https://en.wikipedia.org/wiki/Doxing
dox – Wiktionary
Alternative forms . doxx; Etymology . Phonetic respelling of docs, which is a short form of documents.
Pronunciation . Rhymes: -ɒks; Noun . dox pl (plural only)
cached proxied
https://en.wiktionary.org/wiki/dox
How to Dox Anyone « Null Byte :: WonderHowTo
Doxing is the act of finding one's personal information through research and discovery, with little to no
information to start with. You may have ...
cached proxied
https://null-byte.wonderhowto.com/how-to/dox-anyone-0160998/
How To Find Someones Online Identity - DOX Tutorial - YouTube
Hochgeladen von The Hacker ShowDOX - An Internet slang word for finding and releasing personally
identifiable information such ...
cached proxied
https://www.youtube.com/watch?v=5c5Lm0H49DY
I was taught to dox by a master | The Daily Dot
It makes you feel vulnerable and on-edge, knowing that anyone has the details ... While doxers
sometimes use hacking or deception to uncover ...
cached proxied
I was taught to dox by a master
18th International Anti-Corruption Conference: Plenary 3: Exposing ...
The role of media and particularly of investigative journalists have transformed the fight against
corruption: leaks, whistleblowers, cross-border ...
cached proxied
https://18iacc.sched.com/event/Foqd/pl[...]sing-the-corrupt-knocking-out-impunity
Exposing Corrupt Politicians: The Effects of Brazil's Publicly ...
This paper examines whether access to information enhances political accountability. Based upon the
results of Brazil's recent anti-corruption program...
cached proxied
https://www.iza.org/publications/dp/28[...]-released-audits-on-electoral-outcomes
72How To Protect Yourself Online While You
Investigate These Corrupt Officials
SURVIVE AND KEEP YOUR FAMILY, FRIENDS AND YOURSELF SAFE IN THE MODERN
DIGITAL WORLD
Always remember: Anybody that does not like you can open, read and take any photo, data, email or
text on EVERY phone, computer, network or electronic device you have ever used no matter how
"safe" you think your personal or work system is! They can do this in less than a minute. Also:
Hundreds of thousands of hackers scan every device, around the clock, even if they never heard of you,
and will like your stuff just for the fun of causing trouble. Never use an electronic device unless you
encrypt, hide and code your material!
Those people who think: "I have nothing to worry about..I am not important" ARE the people who get
hacked the most. Don't let naivete be your downfall.
Every single modern cell phone and digital device can be EASILY taken over by any hacker and made
to spy on you, your family, your business and your friends in thousands of different ways. Taking over
the microphone is only a small part of the ways a phone can be made to spy on you. Your phone can
record your location, you voice vibrations, your mood, your thoughts, your sexual activity, your
finances, your photos, your contacts (who it then goes off and infects) and a huge number of other
things that you don't want recorded.
The worst abusers of your privacy, personal information, politics and psychological information
intentions are: Google, Facebook, Linkedin, Amazon, Netflix, Comcast, AT&T, Xfinity, Match.com &
the other IAC dating sites, Instagram, Uber, Wells Fargo, Twitter, Paypal, Hulu, Walmart, Target,
YouTube, PG&E, The DNC, Media Matters, Axciom, and their subsidiaries. Never, ever, put accurate
information about yourself on their online form. Never, ever, sign in to their sites using your real name,
phone, address or anything that could be tracked back to you.
In recent science studies cell phones were proven to exceed radiation safety limits by as high as 11
times the 2-decade old allowable U.S. radiation limits when phones touch the body. This is one of
thousands of great reasons to always remove the battery from your cell phone when you are not talking
on it. A phone without a battery in it can't spy on you and send your data to your enemies.
If you are reading this notice, the following data applies to you:
1. EVERY network is known to contain Intel, Cisco, Juniper Networks, AMD, QualComm and other
hardware which has been proven to contain back-door hard-coded access to outside parties. This is a
proven, inarguable fact based on court records, FISA data, IT evidence, national news broadcasts,
Congressional presented evidence and inventory records, ie: Krebs On Security, FireEye, ICIJ,
Wikileaks Vault 9, EU, Global IT services, FBI.
732. Chinese, Russian FSB, Iranian and other state-sponsored hacking services as well as 14 year old
domestic boys are able to easily enter your networks, emails and digital files because of this. They can
enter your network at any time, with less than 4 mouse clicks, using software available to anyone. This
is a proven, inarguable fact based on court records, FISA data, IT evidence and inventory records, ie:
Krebs On Security, FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services, FBI.
3. Your financial office is aware of these facts and has chosen not to replace all of the at-risk
equipment, nor sue the manufacturers who sold your organization this at risk equipment. They believe
that the hassle and cost of replacement and litigation is more effort than the finance department is
willing to undertake. This is a proven, inarguable fact based on court records, FISA data, IT evidence,
national news broadcasts, Congressional presented evidence and inventory records, ie: Krebs On
Security, FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services, FBI.
4. In addition to the existing tools that were on the internet, in recent years, foreign hackers have
released all of the key hacking software that the CIA, DIA and NSA built to hack into any device.
These software tools have already been used hundreds of times. Now the entire world has access to
these tools which are freely and openly posted across the web. This is a proven, inarguable fact based
on court records, FISA data, IT evidence, national news broadcasts, Congressional presented evidence
and inventory records, ie: Krebs On Security, FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services,
FBI.
5. The computers, servers, routers, cell phones, IP cameras, IP microphones, Smart Meters, Tesla’s,
“Smart Devices:”, etc. and other devices openly broadcast their IP data and availability on the internet.
In other words, many of your device broadcast a “HERE I AM” signal that can be pinged, scanned,
spidered, swept or, otherwise, seen, like a signal-in-the-dark from anywhere on Earth and from
satellites overhead. Your devices announce that they are available to be hacked, to hackers. This is a
proven, inarguable fact based on court records, FISA data, IT evidence, national news broadcasts,
Congressional presented evidence and inventory records, ie: Krebs On Security, FireEye, ICIJ,
Wikileaks Vault 9, EU, Global IT services, FBI.
6. It is bad policy for your organization, or any organization, to think they are immune or have IT
departments that can stop these hacks. NASA, The CIA, The White House, EQUIFAX, The
Department of Energy, Target, Walmart, American Express, etc. have been hacked hundreds of times.
This is a proven, inarguable fact based on court records, FISA data, IT evidence, national news
broadcasts, Congressional presented evidence and inventory records, ie: Krebs On Security, FireEye,
ICIJ, Wikileaks Vault 9, EU, Global IT services, FBI.
7. The thinking: “Well, nobody would want to hack us”, or “We are not important enough to get
hacked” is the most erroneous and negligent thinking one could have in the world today. Chinese,
Russian and Iranian spy agencies have a global “Facebook for blackmail” and have been sucking up the
data of every entity on Earth for over a decade. If the network was open, they have the data and are
always looking for more. The same applies to Google and Facebook who have based their entire
business around domestic spying and data re-sale. This is a proven, inarguable fact based on court
records, FISA data, IT evidence, national news broadcasts, Congressional presented evidence and
inventory records, ie: Krebs On Security, FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services,
FBI.
748. You are a “Stepping Stone” doorway to other networks and data for targeted individuals and other
entities. Your networks provide routes into other people’s networks. The largest political industry today
is called “Doxing” and “Character Assassination”. Billions of dollars are expended by companies such
as IN-Q-Tel - (DNC); Gawker Media - (DNC); Jalopnik - (DNC); Gizmodo Media - (DNC); K2
Intelligence - (DNC); WikiStrat - (DNC); Podesta Group - (DNC); Fusion GPS - (DNC/GOP); Google
- (DNC); YouTube - (DNC); Alphabet - (DNC); Facebook - (DNC); Twitter - (DNC); Think Progress -
(DNC); Media Matters - (DNC); Black Cube - (DNC); Mossad - (DNC); Correct The Record - (DNC);
Sand Line - (DNC/GOP); Blackwater - (DNC/GOP); Stratfor - (DNC/GOP); ShareBlue - (DNC);
Wikileaks (DNC/GOP); Cambridge Analytica - (DNC/GOP); Sid Blumenthal- (DNC); David Brock -
(DNC); PR Firm Sunshine Sachs (DNC); Covington and Burling - (DNC), Buzzfeed - (DNC) Perkins
Coie - (DNC); Wilson Sonsini - (DNC) and hundreds of others to harm others that they perceive as
political, personal or competitive threats. Do not under-estimate your unintended role in helping to
harm others. This is a proven, inarguable fact based on court records, FISA data, IT evidence, national
news broadcasts, Congressional presented evidence and inventory records, ie: Krebs On Security,
FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services, FBI.
9. NEVER believe that you are too small to be noticed by hackers. Parties who believe that are the
hackers favorite targets. This is a proven, inarguable fact based on court records, FISA data, IT
evidence, national news broadcasts, Congressional presented evidence and inventory records, ie: Krebs
On Security, FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services, FBI.
10. NEVER believe that because the word “DELL” or “IBM” or “CISCO” is imprinted on the plastic
cover of some equipment that you are safe. Big brands are targeted by every spy agency on Earth and
are the MOST compromised types of equipment. This is a proven, inarguable fact based on court
records, FISA data, IT evidence, national news broadcasts, Congressional presented evidence and
inventory records, ie: Krebs On Security, FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services,
FBI.
11. YOU may not personally care about getting exposed but the person, or agency, you allow to get
exposed will be affected for the rest of their lives and they will care very much and could sue you for
destroying them via negligence. Be considerate of others in your “internet behavior”. Do not put
anything that could hurt another on any network, ever. This is a proven, inarguable fact based on court
records, FISA data, IT evidence, national news broadcasts, Congressional presented evidence and
inventory records, ie: Krebs On Security, FireEye, ICIJ, Wikileaks Vault 9, EU, Global IT services,
FBI.
12. Never post your real photograph online, or on a dating site social media or on any network. There
are thousands of groups who scan every photo on the web and cross check those photos in their
massive databases to reveal your personal information via every other location your photo is posted.
These "image harvesters" can find out where you, who your friends and enemies are and where your
kids are in minutes using comparative image data that they have automated and operating around the
clock. This is a proven, inarguable fact based on court records, FISA data, IT evidence, national news
broadcasts, Congressional presented evidence and inventory records, ie: Krebs On Security, FireEye,
ICIJ, Wikileaks Vault 9, EU, Global IT services, FBI.
13. If you think using web security measures like this makes you "paranoid", then think again. Cautious
and intelligent people use these security measures because these dangers are proven in the news
75headlines daily. Uninformed, naive and low IQ people are the types of people who do not use good web
hygiene and who suffer because they are not cautious and are not willing to consider the consequences
of their failure to read the news and stay informed.
- Provided By The Broadcast News Association - 2019
YOU HAVE BEEN WARNED:
According to the world's top internet security experts: "...Welcome to the new digital world. Nobody
can ever type anything on the internet without getting scanned, hacked, privacy abused, data harvested
for some political campaign, spied on by the NSA and Russian hackers and sold to marketing
companies. You can't find a corporate or email server that has not already been hacked. For $5000.00,
on the Dark Web, you can now buy a copy of any person's entire dating files from match.com, their
social security records and their federal back-ground checks. These holes can never be patched because
they exist right in the hardware of 90% of the internet hardware on Earth. Any hacker only needs to
find one hole in a network in order to steal everything in your medical records, your Macy's account,
your credit records and your dating data. Be aware, these days, Mr. & Ms. Consumer. Facebook,
Google, Twitter and Amazon have turned out to be not-what-they-seem. They manipulate you and your
personal information in quite illicit manners and for corrupt purposes. Avoid communicating with
anybody on the internet because you will never know who you are really talking to. Only
communication with people live and in-person..."
SPREAD THE WORD. TELL YOUR FRIENDS. COPY AND PASTE THIS TO YOUR SOCIAL
MEDIA
MORE PROOF:
https://www.i-programmer.info/news/149-security/12556-google-says-spectre-and-meltdown-are-too-
difficult-to-fix.html
https://sputniknews.com/us/201902231072681117-encryption-keys-dark-overlord-911-hack/
https://www.businessinsider.com/nest-microphone-was-never-supposed-to-be-a-secret-2019-2
https://thehill.com/policy/technology/430779-google-says-hidden-microphone-was-never-intended-to-
be-a-secret
https://www.blacklistednews.com/article/71200/smartphone-apps-sending-intensely-personal-
information-to-facebook--whether-or-not-you-have-an.html
https://www.bleepingcomputer.com/news/security/microsoft-edge-secret-whitelist-allows-facebook-to-
autorun-flash/
https://news.ycombinator.com/item?id=19210727
https://www.davidicke.com/article/469484/israel-hardware-backdoored-everything
76https://www.scmp.com/economy/china-economy/article/2186606/chinas-social-credit-system-shows-
its-teeth-banning-millions
https://youtu.be/lwoyesA-vlM
https://www.zdnet.com/article/critical-vulnerabilities-uncovered-in-popular-password-managers/
https://files.catbox.moe/jopll0.pdf
https://files.catbox.moe/ugqngv.pdf
https://www.technologyreview.com/s/612974/once-hailed-as-unhackable-blockchains-are-now-getting-
hacked/
https://arstechnica.com/tech-policy/2019/02/att-t-mobile-sprint-reportedly-broke-us-law-by-selling-
911-location-data/
https://theintercept.com/2019/02/08/jeff-bezos-protests-the-invasion-of-his-privacy-as-amazon-builds-
a-sprawling-surveillance-state-for-everyone-else/
https://www.blacklistednews.com/article/71200/smartphone-apps-sending-intensely-personal-
information-to-facebook--whether-or-not-you-have-an.html
https://www.stripes.com/news/us/feds-share-watch-list-with-1-400-private-groups-1.569308
https://voat.co/v/news/3053329
https://www.zdnet.com/article/all-intel-chips-open-to-new-spoiler-non-spectre-attack-dont-expect-a-
quick-fix/
https://voat.co/v/technology/3075724
https://www.theregister.co.uk/2019/02/26/malware_ibm_powershell/
https://fossbytes.com/facebook-lets-anyone-view-your-profile-using-your-phone-number/
Vulnerability in Ring Doorbell Fixed After Discovery that Hackers Could Supply Fake Images
https://voat.co/v/technology/3077896
Whistleblowers Say NSA Still Spies on American Phones in Hidden Program
256208/
https://www.wionews.com/photos/how-israel-spyware-firm-nso-operates-in-shadowy-cyber-world-
218782#hit-in-mexico-218759
77https://sg.news.yahoo.com/whatsapp-hack-latest-breach-personal-data-security-135037749.html
https://metro.co.uk/2019/05/14/whatsapp-security-attack-put-malicious-code-iphones-androids-
9523698/
https://www.thesun.co.uk/tech/9069211/whatsapp-surveillance-cyber-attack-glitch/
----------------------------------------------
THE PROMIS BACKDOOR
Beyond embedded journalists, news blackouts, false flag events, blacklisted and disappeared Internet
domains the plotline of America's "free press" there are now ISP-filtering programs subject to
Homeland Security guidelines that sift through emails and toss some into a black hole. Insiders and the
NSA-approved, however, can get around such protections of networks by means of the various hybrids
of the PROM IS backdoor. The 1980s theA of the Prosecutor's Management Information System
(PROMIS) software handed over the golden key that would grant most of the world to a handful of
criminals. In fact, this one crime may have been the final deal with the devil that consigned the United
States to its present shameful descent into moral turpitude. PROMIS began as a COBOL-based
program designed to track multiple offenders through multiple databases like those of the DOJ, CIA,
U.S. Attorney, IRS, etc. Its creator was a former NSA analyst named William Hamilton. About the time
that the October Surprise Iranian hostage drama was stealing the election for former California
governor Ronald Reagan and former CIA director George H.W. Bush in 1980, Hamilton was moving
his Inslaw Inc. from non-profit to for-profit status.
His intention was to keep the upgraded version of PROM IS that Inslaw had paid for and earmark a
public domain version funded by a Law Enforcement Assistance Administration (LEAA) grant for the
government. With 570,000 lines of code, PROMIS was able to integrate innumerable databases without
any reprogramming and thus turn mere data into information.
With Reagan in the White House, his California cronies at the DOJ offered Inslaw a $9.6
million contract to install public-domain PROMIS in prosecutors' offices, though it was really the
enhanced PROM IS that the good-old-boy network had set its sights on. In February 1983, the chief of
Israeli antiterrorism intelligence was sent to Inslaw under an alias to see for himself the DEC VAX
enhanced version. He recognized immediately that this software would revolutionize Israeli
intelligence and crush the Palestine Inti fada. Enhanced PROMIS could extrapolate nuclear submarine
routes and destinations, track assets, trustees, and judges. Not only that, but the conspirators had a CIA
genius named Michael Riconosciuto who could enhance the enhanced version one step further, once it
was in their possession. To install public domain PROMIS in ninety-four U.S. Attorney offices as per
contract, Inslaw had to utilize its enhanced PROMIS. The DOJ made its move, demanding temporary
possession of enhanced PROMIS as collateral to ensure that all installations were completed and that
only Inslaw money had gone into the enhancements. Na'ively, Hamilton agreed. The rest is history: the
DOJ delayed payments on the $9.6 million and drove Inslaw into bankruptcy. With Edwin Meese III as
Attorney General, the bankruptcy system was little more than a political patronage system, anyway.
The enhanced PROMIS was then passed to the brilliant multivalent computer and chemical genius
Riconosciuto, son of CIA Agent Marshall Riconosciuto.5 Recruited at sixteen, Michael had studied
with Nobel Prize-winning physicist and co-inventor of the laser Arthur Shallo. Michael was moved
78from Indio to Silver Springs to Miami as he worked to insert a chip that would broadcast the contents
of whatever database was present to collection satellites and monitoring vans like the Google Street
View van, using a digital spread spectrum to make the signal look like computer noise. This Trojan
horse would grant key-club access to the backdoor of any person or institution that purchased PROM
IS software as long as the backdoor could be kept secret. Meanwhile, the drama between Hamilton and
the conspirators at DOJ continued. A quiet offer to buy out Inslaw was proffered by the investment
banking firm Allen & Co., British publisher (Daily Mirror) Robert Maxwell, the Arkansas corporation
Systematics, and Arkansas lawyer (and Clinton family friend) Webb Hubbell. Hamilton refused and
filed a $50 million lawsuit in bankruptcy court against the DOJ on June 9, 1986. Bankruptcy Judge
George F. Bason, Jr. ruled that the DOJ had indeed stolen PROMIS through trickery, fraud, and deceit,
and awarded Inslaw $6.8 million. He was unable to bring perjury charges against government officials
but recommended to the House Judiciary Committee that it conduct a full investigation of the DOJ. The
DOJ's appeal failed, but the Washington, D.C. Circuit Court of Appeals reversed everything on a
technicality. Under then-President George H.W. Bush (1989 — 1993), Inslaw's petition to the Supreme
Court in October 1991 was scorned. When the IRS lawyer requested that Inslaw be liquidated in such a
way that the U.S. Trustee program (AG Meese's feeding trough between the DOJ and IRS) could name
the trustee who would convert the assets, oversee the auction, and retain the appraisers, Judge Bason
refused.
Under then-President William Jefferson Clinton (1993 — 2001), the Court of Federal Claims
whitewashed the DOJ's destruction of Inslaw and theA of PROMIS on July 31, 1997. Judge Christine
Miller sent a 186-page advisory opinion to Congress claiming that Inslaw's complaint had no merit a
somber message to software developers seeking to do business with Attorney Generals and their DOJ.
For his integrity, Judge Bason lost his bench seat to the IRS lawyer. Throughout three administrations,
the mainstream Mockingbird media obediently covered up the Inslaw affair, enhanced PROMIS being
a master tool of inference extraction able to track and eavesdrop like nothing else. Once enhanced
PROMIS was being sold domestically and abroad so as to steal data from individuals, government
agencies, banks, and corporations everywhere, intelligence-connected Barry Kumnick~ turned
PROMIS into an artificial intelligence (AI) tool called SMART (Special Management Artificial
Reasoning Tool) that revolutionized surveillance. The DOJ promised Kumnick $25 million, then forced
him into bankruptcy as it had Hamilton. (Unlike Hamilton, Kumnick settled for a high security
clearance and work at military contractors Systematics and Northrop.) Five Eyes / Echelon and the
FBI's Carnivore / Data Collection System 1000 were promptly armed with SMART, as was closed
circuit satellite highdefinition (HD) television. With SMART, Five Eyes / Echelon intercepts for
UKUSA agencies became breathtaking.
The next modification to Hamilton's PROMIS was Brainstorm, a behavioral recognition software,
followed by the facial recognition soAware Flexible Research System (FRS); then Semantic Web,
which looks not just for link words and embedded code but for what it means that this particular person
is following this particular thread. Then came quantum modification. The Department of Defense paid
Simulex, Inc. to develop Sentient World Simulation (SWS), a synthetic mirror of the real world with
automated continuous calibration with respect to current real-world information. The SEAS (Synthetic
Environment for Analysis and Simulations) soAware platform drives SWS to devour as many as five
million nodes of breaking news census data, shiAing economic indicators, real world weather patterns,
and social media data, then feeds it proprietary military intelligence and fictitious events to gauge their
destabilizing impact. Research into how to maintain public cognitive dissonance and learned
helplessness (psychologist Martin Seligman) help SEAS deduce human behavior.
There are legitimate reasons ( http://www.learnliberty.org/videos/edward-snowden-surveillance-is-
about-power/ )to want to avoid being tracked and spied-on while you're online. But aside from that,
doesn't it feel creepy knowing you're probably being watched every moment that you're online and that
information about where you go and what you do could potentially be sold to anyone at any time--to
advertisers, your health insurance company, a future employer, the government, even a snoopy
neighbor? Wouldn't you feel better not having to worry about that on top of everything else you have to
worry about every day?
First, let me start out by giving you the bad news, there is no such thing as perfect online privacy. We'll
assume for the purposes of this article that online privacy and anonymity mean roughly the same thing.
No matter what anyone tells you, online privacy (and anonymity) just doesn't exist. The fight for online
privacy is like warfare. Every time one side gets an advantage, the other side figures out how to get
around it. That means your level of online privacy is dependent on how much effort you are willing to
continually put into making yourself invisible. Let's face it, if the NSA wants to spy on you and is
willing to put more time and money into singling you out than you are willing to spend being
anonymous, then you will be spied on.
The good news is that there are things you can do to be less surveillable--and they won't cost you
anything. Remember the old story about the two friends in the woods who came across a bear. One says
to the other, "We'll never outrun this bear." The other smiles and says, "That's OK. I only have to outrun
you." That isn't exactly a perfect analogy, because any trace that you leave behind on the internet could
be used against you at some later date. But it's still better to leave less behind than the next guy. Make it
too expensive for "Them" to surveil everyone to the level that they would need to get much on you--at
least for the time being.
The most anyone can possibly do to avoid online surveillance is to use a different computer every time
he goes on line--one that has never been on the internet before and cannot be traced to him. Then, after
a single use, he will dispose of it where it can never be found by anyone. Further, he will wear gloves, a
ski mask, and dark glasses and go to some public wifi hot spot with hundreds of people using it in a
town far away from where he lives (a different town each time). Then he will avoid sites he has
frequented in the past and never log on to any site with a password. And he will leave no finger prints
or DNS evidence behind... So, obviously, no one is going to actually do this--unless he is in some
really, really deep trouble. But, barring that, no sane person is going to put out this level of effort to be
anonymous every time he goes on the internet.
So, what level of effort is reasonable? Well, it depends on what you are trying to accomplish. But let's
assume you are not doing anything illegal. You just want to access your email and surf the internet,
maybe buy something on Amazon. In other words, you are the average consumer. Well, there's some
more bad news. Given a reasonable level of effort, you can't be anonymous on any website where you
enter a password. Once you type your password, you have identified yourself. That's the point of a
password. So, some level of anonymity can only be achieved when you don't enter a password during
the period of time that you're logged on to the internet. I know that's probably not what you were
hoping to hear. But unless you are someone like Edward Snowden fleeing from the NSA, or on the
80FBI's ten-most-wanted list, you'll probably not be willing to expend the amount of effort I spelled out
above to get the level of online privacy that it would take to keep yourself really, really anonymous.
Assessing Threats
Given that you are willing to make an effort to achieve a reasonable level of anonymity, how do you go
about it? The first thing you need to do is to understand who "They" are and how they are watching
you. The first group that is watching you is the companies who are hoping to make a buck off of you or
off of information about what you are doing on line. These are companies like your internet service
provider, Google, Google Analytics, Microsoft, Facebook, WordPress, Squarespace, their competitors,
and every website that uses web development software written by these companies or their competitors.
The problem is that their software is used on just about every website these days. So, chances are
extremely good that if you visit a website that sponsors advertisements, tracks the number of hits it
receives, or allows you to make comments or fill out any kind of a form, you are being identified and
tracked online. (By the way, this website, The Cheapskate's Guide to Computers and the Internet, only
uses open-source software and does not attempt to identify or track you in any way.) If you are using an
internet browser or operating system written by Google, like Chrome or Android, you are also being
identified and tracked. If you are using Windows 10, you are being identified and tracked online. That
covers just about everyone who accesses the internet.
The next group that is watching you works for a government. These are the NSA and possibly the CIA
and FBI and other US government agencies (there are 17 government intelligence agencies in the US)
and their foreign equivalents. For the time being, all the US government agencies want is to make sure
that you are not a criminal or a terrorist--and to make sure they know where you are at all times, in case
you ever decide to commit a crime or become a terrorist. In the future, who knows? Governments of
some countries make it a crime to speak out against them, so you can probably figure out why they may
want to watch their citizens. And the British government seems to want to spy on its people ... well
apparently it just likes spying on its people. I don't know how else to account for the level of
surveillance in Britain.
The next group that is watching you is composed of thieves. These are people who want your
passwords, so they can empty out your bank accounts. Or they may want to use your online accounts,
so they can hide while they steal from others. They may also want to convince you that they are
actually a nigerian prince ( https://www.bbb.org/new-york-city/get-consumer-help/articles/the-nigerian-
prince-old-scam-new-twist/ ) who has no other place to keep his money safe except in your trustworthy
hands.
The next group that is watching you is the hackers who are not thieves. Mostly, they just want to snoop
and to practice snooping so as to improve their ability to snoop. They want to know everything about
everyone, especially governments and large corporations. And sometimes they want to get notoriety for
revealing that information. Maybe some want to fix the broken systems that we all live under to make
the world a better place.
Reasonable questions for you, the average consumer, to ask are, which groups, if any, can you protect
yourself from, and how hard should you be trying? In order to be able to answer these questions, let's
look at a few things. In the three lists which follow, I've assumed that the governments to which I am
81referring are Western "democratic" governments. The first list is a probable ranking of the above
groups from most to least difficult to protect yourself from:
Governments
Hackers
Corporations
Thieves
Next, the ranking from most to least likely to be spying on you probably looks like this:
Corporations
Governments
Thieves
Hackers
Lastly, the amount of damage from most to least that these groups could do to you while spying on you
probably looks like this:
Thieves
Governments
Corporations
Hackers
Taken together, the three lists above suggest the following. First, you shouldn't be worried about
hackers, because they probably aren't spying on you. But even if they are, you can't do anything about
it. And you really don't have much to fear from them, even if they are spying on you. Second, you
should definitely be trying to protect yourself from thieves, because you have the most to fear from
them, there is a reasonable likelihood that they are trying to spy on you, and they are the easiest group
to protect yourself from. Next, Corporations probably aren't going to do you much damage by spying
on you, even though they are certainly spying on you, although you have a chance, with vigilance on
you part, of protecting yourself from them. So, whether you want to try to protect yourself from
corporations is a judgment call that you'll have to make. And, lastly, governments are spying on you.
And you have nearly as much reason to fear them as to fear thieves. However, governments are the
hardest to protect yourself from. So, though you may be tempted to give up on trying to protect
yourself from governments, due to the difficulty of doing so, you should probably be looking for ways
to protect yourself from them. By the way, it makes sense that you have nearly as much to fear from
governments spying on you as from thieves, since according to Paul Kennedy, who wrote The Rise and
Fall of the Great Powers, ( https://www.amazon.com/Rise-Fall-Great-Powers/dp/0679720197 )
governments are nothing more than institutionalized thievery. One more thing to note about
government spying is that the numbers of people they are spying on is at least in the millions--if not a
very significant portion of everyone on the planet, judging by what we know about the NSA
https://www.eff.org/nsa-spying
Also, see this (https://en.wikipedia.org/wiki/PRISM_(surveillance_program)
and this: https://www.youtube.com/watch?v=wB4Gn0u4DSE
82Threat-Tailoring Approaches
So, now that we have established that we need to fear thieves, governments, and corporations, in that
order, let's talk about what we can do about each. Thieves' main methods of attack are through social
engineering attacks (https://www.incapsula.com/web-application-security/social-engineering-
attack.html). Social engineering works mainly through phone calls, offers on web sites, and email. A
thief may call you on the phone or send you an email to try to scam you by saying they are someone
else who has a legitimate need for your information. For example, they may pretend to be the IRS and
ask for your tax information, including your banking information and social security number. A thief
may have a website with a message that pops up saying that your computer is infected with a virus and
telling you to call a phone number. This is never legitimate. To avoid being scammed through email,
many people advise you not to open emails from people you don't know. That's like never answering
your phone unless you recognize the person calling. You may miss legitimate calls. But it is safer than
talking to every caller. Avoid clicking on links in emails or opening attachments, because they may
execute malware programs or take you to fake websites. Also 2-factor authentication is another layer of
protection against thieves. By the way, you cannot protect yourself from thieves who steal your
information out of companies' computers; however, the one exception is that you can encrypt your data
before giving it to online services like Dropbox or sending it in emails. Often thieves will hide malware
in software that looks legitimate. Don't load software onto your phone or computer from any sources
that you don't trust, which is just about every source on the internet except for official Microsoft and
Google websites and Linux distribution repositories. With any other software, including web browser
add-ons, you are risking your privacy and security. If you have to load software from another source,
some of the less risky sources can be found here:
https://www.makeuseof.com/tag/9-cleanest-safest-websites-download-free-software-windows/
One way of telling if you may have malware on your computer that is transmitting information to a
thief is to see what ports you have open. You can do this using the Shieldsup test
ttps://www.grc.com/x/ne.dll?rh1dkyd2
You should not see any ports open while you are online. If you want even more online security, my
personal recommendations are to not bank online and to consider using my three-USB stick method.
Also, since threats, threat prevention software, and threat prevention techniques change continuously, it
is important to keep yourself aware of the latest information.
Protecting yourself from corporate spying requires even more effort. It also requires even more
knowledge. No gadget out there will do the work for you. Every time I've seen someone offer
consumers a gadget, I've seen someone else explain why it's not very effective--at least, not so far. That
leaves software. First, your Internet Service Provider (ISP) can see everything you do online. You
probably can't do anything to completely change that; however, you can make it a little harder for them.
First, use another DNS server, not your ISP's. This will make it slightly harder for them to see which
websites you visit. It is also possible to encrypt your DNS traffic:
https://www.opendns.com/about/innovations/dnscrypt/
83This prevents your ISP from from seeing which websites you're visiting by examining the DNS headers
in individual packets coming across its servers. Then, take full advantage of the built-in encryption on
the internet by only using HTTPS websites, where possible. Many people suggest using a VPN service.
However, studies have shown that most VPN services don't actually work when it comes to hiding your
activities from your ISP. Note that HTTPS and VPN's can no longer protect you from government
surveillance. https://cheapskatesguide.org/articles/no-online-bank-account.html
To protect yourself from being tracked online by corporations other than your ISP, like Google and
Facebook, many people recommend that you use anti-tracking software--like, for example, Privacy
Badger. The bad news is that anti-tracking software, including anti-tracking settings in your browser
and deletion of tracking cookies are far from 100% effective. There is a technique called fingerprinting
that takes all the information that your browser puts out to websites and uses it to uniquely identify
you, no matter what anonymizing or anti-tracking measures you have taken. It is extremely difficult to
circumvent fingerprinting, because all browsers transmit information to websites. I have never tried
using an ancient web browser like Lynx to see if it may transmit significantly less data than the average
modern web browser, but it's worth a shot. However, since a lot of corporate tracking techniques rely
on your own web browser to do their work for them, one thing you can do to thwart them to some
extent is to turn off javascript in your browser.
https://helpeverybody.wpengine.com/websocial-media/1409-you-have-no-idea-how-many-visitors-
your-website-gets
You can test to what extent your browser is transmitting unique information using these sites:
panopticlick.com, Shieldsup, and ip-check.info.
https://panopticlick.eff.org/
https://www.grc.com/shieldsup
https://cheapskatesguide.org/articles/ip-check.info?/lang=en
These sites confirm that browsers transmit a lot of data that can be used for fingerprinting. From
playing around with these sites, I have noticed that turning off javascript in my browser does help
some. Also the TOR browser seems to transmit less data than most, but even it is not completely
effective. The added benefit that you get from the TOR browser and especially the TAILS operating
system is that they block your IP address from the websites you visit. You want to try several browsers
to see which one transmits the least information. Perhaps you will be lucky enough to find a browser
that transmits less information than the TOR browser.
The next thing to be aware of is that corporations have methods other than tracking to spy on you.
There is a saying that if a corporation is offering you their product for free, you are their product. This
means that corporations that offer you free services are selling the data they collect from you in order to
be able to provide you with these services. So, chances are that companies that provide you with free
84email are reading your email. We know that, in addition to tracking you, Facebook reads your posts and
knows who your friends are, and that is just the beginning of Facebook's spying methods. Free online
surveys are just ways of collecting more data from you. Companies also monitor your credit card
transactions and sell your online dating profiles. If you have a Samsung TV that is connected to the
internet, it's probably recording what you watch and may even be listening to your private
conversations in your home. In fact, anything that you have in your home that is connected to the
internet may be spying on you, right down to your internet-connected light bulb. With a few
exceptions, online search engines monitor and log your searches. One of the exceptions is the
ixquick.com search engine, which is headquartered in Europe. The steps to counter the nearly
ubiquitous activities of free service providers would be to pay for services you receive online, read
website privacy agreements, and not buy products that are known to be spying on you. However, the
only way to be really secure from corporations using the internet to spy on you is to never connect to
the internet or buy any internet-connected appliances. Welcome back to the 1980's.
Protecting yourself from government spying while you are on the internet is the hardest and requires
the most knowledge. The biggest problem is that unless a whistle-blower like Edward Snowden tells
us, we have no way of knowing how governments may potentially be spying on us. That means that we
have no way of protecting ourselves 100% of the time from government spying. Some things whistle-
blowers have revealed ( https://secureswissdata.com/9-ways-government-spying-on-internet-activity/
) are that the US government logs the meta data from all phone calls (who calls who and when),
secretly forces internet service providers and providers of other services to allow it to "listen in on" and
record all traffic going through their servers, reads nearly all email sent from everywhere in the world,
and tracks the locations of all cell phones (even when they're turned off). And, although I am not aware
of any specific whistle-blower revelations on this, there is every reason to believe that the US
government (and perhaps others, including China's) has backdoors built into all computer hardware and
operating system software for monitoring everything we do on our cell phones, tablets, laptops, desktop
computers, and routers. ( https://www.eteknix.com/nsa-may-backdoors-built-intel-amd-processors/
) See also this. Because Lenovo computers are manufactured in China, the US government has issued
warnings to all US government agencies and subcontractors to strongly discourage them from using
Lenovo computers. And the US government probably has backdoors (
https://www.atlasobscura.com/articles/a-brief-history-of-the-nsa-attempting-to-insert-backdoors-into-
encrypted-data
) into all commercially-available encryption software, with the possible exception of Truecrypt version
7.1a. I hope you are understanding now the magnitude of the lengths that governments are going to
(using your tax money) to spy on you. In truth, we are now approaching the level of government spying
that George Orwell warned about in his book, 1984
So what can we practically do to protect ourselves from government spying? Seriously, there isn't
much, if we want to use cell phones, credit cards, and the internet. About all we can do, if we
absolutely need to have a private conversation, is to have a face-to-face meeting without any
electronics within microphone range. That includes cell phones, Samsung TV's, video cameras,
computers, or land-line telephones. And don't travel to the meeting place using long-distance
commercial transportation. Sending a letter through the US mail is the next best, although it is known
that the outsides of all mail sent through the US mail are photographed, and the pictures are stored. So,
don't put your return address on the envelope. (
http://www.abajournal.com/news/article/new_york_times_post_office_photocopies_envelopes_of_all_
mail_sent_in_the_us/
85) As far as surfing the internet is concerned, begin with all the precautions that I outlined above to
protect yourself from corporate spying (except HTTPS and VPN's). Then, add the TAILS operating
system on a USB stick. As I said, TAILS will not prevent you from being identified and tracked via the
fingerprinting method. And who can be sure whether the government has a backdoor in TAILS? As far
as I know, the super-paranoid, hoody and sunglasses method I outlined above is is the next step.
Some people recommend using ProtonMail to send private emails (and then, only to other ProtonMail
users). In order for this to work, ProtonMail would have to provide both the sender and the receiver
with software that runs on their computers to encrypt and decrypt the contents of their emails before
they are sent over the government-monitored internet lines. Or you could encrypt the contents yourself
with a prearranged password (from that face-to-face meeting you had). Be sure to use an extremely
secure password! The real benefit of ProtonMail is not its encryption (because it's more secure to do
that yourself), but the fact that the emails are stored in Switzerland, where the US government can't get
them. But, if the government has a backdoor into either the encryption software that you used or that
ProtonMail used to encrypt your email, then encryption does you no good if the US government ever
manages to get their hands on your emails. (See this, this, and this.) All we know is that Snowden
provided evidence in 2014 that the NSA had not cracked Truecrypt. Whether that is still the case today
is unknown.
Be aware that simply the use of methods of avoiding government spying techniques may make you a
target. This includes the use of encryption and TAILS. However, if millions and millions of law-abiding
people begin to actively use these methods, then the NSA cannot put them under significantly more
scrutiny than that to which it is already subjecting the rest of the world. This alone is an argument for
their use.
-----------------------------------------------
Experts warns of ‘epidemic’ of bugging devices used by agency stalkers
- By James Hockaday
Stalkers are using cheap bugging devices hidden in everyday household items
More funding and legal powers are needed for police to stop a surge of stalkers using eavesdropping
devices to spy on victims, experts have warned.
Firms paid to detect the bugs say they’re finding more and more of the devices which are readily
available on online marketplaces like Amazon and eBay.
Jack Lazzereschi, Technical Director of bug sweeping company Shapestones, says cases of stalking and
victims being blackmailed with intimate footage shot in secret has doubled in the past two years.
He told Metro.co.uk: ‘The police want to do something about it, they try to, but usually they don’t have
the legal power or the resources to investigate.
86‘For us it’s a problem. We try to protect the client, we want to assure that somebody has been
protected.’
People are paying as little as £15 for listening devices and spy cameras hidden inside desk lamps, wall
sockets, phone charger cables, USB sticks and picture frames.
Users insert a sim card into a hidden slot and call a number to listen in on their unwitting targets.
People using hidden cameras can watch what’s happening using an apps on their phones.
Jack says the devices are so effective, cheap and hard to trace to their users, law enforcement prefer
using them over expensive old-school devices.
Although every case is different, in situations where homeowners plant devices in their own properties,
Jack says there’s usually a legal ‘grey area’ to avoid prosecution.
The devices themselves aren’t illegal and they are usually marketed for legitimate purposes like
protection, making it difficult for cops to investigate.
There is no suggestion online marketplaces like eBay and Amazon are breaking the law by selling
them.
But in some instances, images of women in their underwear have been used in listings – implying more
sinister uses for the devices.
Even in cases when people are more clearly breaking the law, Jack says it’s unlikely perpetrators will
be brought to justice as overstretched police will prioritise resources to stop violent crime.
Jack’s says around 60 per cent of his firm’s non-corporate cases cases involve stalking or blackmail.
He says it’s become an ‘epidemic’ over the past couple of years with the gadgets more readily available
than ever before.
---------------------------------------------------
Jack Lazzereschi says he’s seen government stalking cases double in a few years
Victims are often filmed naked or having sex and threatened with the threat of footage being put online
and in the worst cases children are also recorded.
Jack says UK law is woefully unprepared to deal with these devices compared to countries in the
Asian-Pacific region.
In South Korea authorities have cracked down on a scourge of perverts planting cameras in public
toilets.
87James Williams, director of bug sweepers QCC Global says snooping devices used to be the preserve
of people with deep pockets and technological know-how.
He said: ‘It’s gone from that to really being at a place where anybody can just buy a device from the
internet.
‘Anything you can possibly think of you can buy with a bug built into it. I would say they’re getting
used increasingly across the board.’
Suky Bhaker, Acting CEO of the Suzy Lamplugh Trust, which runs the National Stalking Helpline,
warned using these gadgets could be a prelude to physical violence.
She said: ‘We know that stalking and coercive control are extremely dangerous and can cause huge
harm to the victim, both in terms of their psychological wellbeing and the potential for escalation to
physical violence or even murder.
‘The use of surveillance devices or spyware apps by stalkers, must be seen in the context of a pattern of
obsessive, fixated behaviour which aims at controlling and monitoring the victim.
Former Home Secretary Amber Rudd with Suky Bhaker during her visit to the Suzy Lamplugh Trust,
who run the
She added: ‘There should be clarity for police forces that the use of surveillance equipment by stalkers
to monitor their victim’s location or communications is a sign that serious and dangerous abuse may be
present or imminent.’
‘All cases of stalking or coercive control should be taken seriously and investigated when reported to
police.’
The charity is calling for all police forces across the country to train staff in this area.
Earlier this month a policeman known only by his surname Mills was barred from the profession for
life for repeatedly dismissing pleas for help from 19-year-old Shana Grice who was eventually
murdered by her stalker ex-boyfriend Michel Lane.
A spokesman for eBay said: ‘The listing of mini cameras on eBay is permitted for legitimate items like
baby monitors or doorbell cameras.
‘However, items intended to be used as spying devices are banned from eBay’s UK platform in
accordance with the law and our policy.
‘We have filters in place to block prohibited items, and all the items flagged by Metro have now been
removed.’
The FBI revealed how the bureau uses the CIA and National Security Agency to probe the private lives of Americans without a warrant in its updated rulebook, which is the first version made public since the Obama administration.
The handbook, rewritten in 2021, confirms a decade-old leak showcasing the bureau’s collaboration with the CIA and NSA for FBI probes that may involve surveillance without court orders against people not accused of any crimes. Such probes are known as “assessments” at the FBI.
The revelations will fuel critics who have long accused the FBI of abusing its national security surveillance powers.
The FBI’s partnership with U.S. intelligence agencies that are focused on foreign threats is expected to get intense scrutiny from the new Republican-run Congress. The House Permanent Select Committee on Intelligence and House Judiciary Committee are digging into how intelligence agencies target Americans. Plans include a new panel to examine the weaponization of the federal government against U.S. citizens.
New information about the FBI’s work with other federal agencies and state and local officials is included in the 906-page rule book authored during the Trump administration and revised under President Biden. The bureau published the updated Domestic Investigations and Operations Guide online after rejecting requests to make it public.
The words CIA and NSA are unredacted in section 20.2 of the 2021 rule book, while the full details of the section remain hidden from public view. A leaked 2011 copy of the FBI’s rule book without redactions obtained by The Intercept shows that section 20.2 covers name trace requests, which involve formal FBI requests for other agencies to conduct searches of their records regarding subjects of interest.
SEE ALSO: New House committees to probe FBI abuse of power, fight China’s advance
Information obtained by CIA and NSA searches of their records may be used in assessments and predicated investigations, according to the leaked 2011 rule book.
The FBI assessments are investigations of people and groups that do not require accusations of wrongdoing and need only an “authorized purpose” and a clear objective, according to the 2021 rule book. The investigations are intended to prevent federal crimes, protect against threats to national security or collect foreign intelligence.
Cato Institute senior fellow Patrick Eddington said the updated rule book shows that the FBI is confident that it will not face consequences for its conduct.
“The bureau is continuing to hide the fact that 1) they can and clearly do use informants to penetrate domestic civil society organizations where those informants may, either on their own or at FBI direction, attempt to influence the organization’s actions,” Mr. Eddington said in an email. “And 2) [they] employ searches of CIA and NSA data streams on U.S. persons or civil society organizations absent a criminal predicate via assessments.”
Mr. Eddington said both practices should be prohibited by law and Congress will have a chance to do that this year.
The NSA declined to comment and referred questions to the FBI, which also refused to comment.
The CIA said it follows the rules and respects Americans’ privacy.
“CIA recognizes and takes very seriously our obligation to respect the privacy and civil liberties of U.S. persons in the conduct of our vital national security mission, and conducts our activities in compliance with U.S. law, Executive Order 12333, and our Attorney General guidelines,” the CIA said in a statement to The Times.
Assessments have faced bipartisan scrutiny in recent years, and the bureau’s internal audits dating to 2013 have shown agents’ repeated failures to follow rules for sensitive investigations.
The FBI’s use of assessments contributed to worries that agents are investigating Americans because of their ideologies, politics or religious beliefs. The conservative Concerned Women for America, a New York chapter of the League of Women Voters, and the Muslim Justice League in Massachusetts are among the groups swept up in FBI assessments, according to records obtained by Mr. Eddington.
The FBI revealed in 2021 that there was nothing to pursue at Concerned Women for America after conducting an assessment in 2016. In December 2021, the bureau told Sen. Chuck Grassley, Iowa Republican, that it did not need to explain its probe of the group.
The FBI’s use of assessments drew additional congressional attention from the House last year. Reps. Nancy Mace, South Carolina Republican, and Jamie Raskin, Maryland Democrat, pressed the Government Accountability Office to conduct a comprehensive review of the bureau’s assessments.
The bipartisan duo said the FBI may have wrongly used assessments to conduct investigations without factual predicates of criminal wrongdoing. They wanted to know whether the assessments involved the monitoring of constitutionally protected activity.
The bureau’s decision to unveil aspects of its work with the CIA and NSA in its 2021 rule book indicates that it has teamed with those intelligence agencies on assessments for more than 10 years.
The Cato Institute sued the FBI for access to government records and pressed the bureau to reveal its rule book before the FBI published it online this fall. Mr. Eddington said his team plans to file challenges to the information that the FBI is keeping hidden in its updated rule book .